End-to-End Encrypted Data on iCloud refers to a security measure implemented by Apple, where data remains encrypted throughout its entire journey, from the sender to the recipient. This means that even Apple, as the service provider, cannot decrypt the contents of the user’s data.
In today’s digital age, the security of our data is of utmost importance. With the rise in cybercrime and hacking incidents, it’s crucial to understand how our sensitive information is protected. One such technology that ensures data security is end-to-end Encryption. I will explore the end-to-end encrypted data on iCloud and how it safeguards our information.
Understanding the Basics of Encryption
To grasp the concept of end-to-end Encryption, it’s essential first to understand what Encryption means. Encryption is a process that transforms plain text into a scrambled form called cipher text, making it unreadable to unauthorized individuals. Using a unique encryption key, the original data can be deciphered only by parties with access to the correct key.
Encryption mainly protects data during transmission over networks or stored on devices or cloud services. It acts as a protective shield, ensuring the information remains secure and inaccessible if it is intercepted or stolen.
What is Encryption?
Encryption is a complex mathematical process that converts legible data into an unreadable format. It involves using algorithms to transform the plain text into cipher text, making it extremely difficult to decipher without the proper decryption key.
The two main types of encryption are symmetric and asymmetric encryption. The first one Symmetric encryption uses a single key for both encryption and decryption, while the second one asymmetric encryption involves a pair of keys: a public key for encryption and a private key for decryption.
Symmetric encryption is faster and more efficient, but requires a secure key exchange. Asymmetric encryption provides a higher level of security but is slower and more resource-intensive.
Both encryption methods rely on complex mathematical algorithms to ensure data confidentiality and integrity. These algorithms are designed to be extremely difficult to reverse-engineer, making it nearly impossible for unauthorized individuals to decrypt the cipher text without the correct key.
The Importance of Encryption in Data Security
- Data security is an essential aspect of our digital lives. Encryption is vital in protecting our sensitive information from cyber threats. Without Encryption, our data, such as passwords, financial details, and personal conversations, would be vulnerable to unauthorized access.
- By employing encryption methods, individuals and organizations can ensure their data’s confidentiality, integrity, and authenticity. It creates a secure environment where only authorized parties can access and decipher the information, significantly reducing the risk of data breaches and identity theft.
- Encryption is crucial in industries that handle sensitive information, such as healthcare, finance, and government. Regulations and compliance standards often mandate Encryption to protect sensitive data from unauthorized disclosure in these sectors.
- Encryption also plays a crucial role in securing online transactions. When you purchase online or enter sensitive information on a website, Encryption ensures that your data is transmitted securely, preventing interception by malicious actors.
- Furthermore, Encryption is not limited to protecting data in transit. It is also essential for securing data at rest, such as data stored on devices or in the cloud. By encrypting stored data, even if a device or cloud service is compromised, the encrypted data remains unreadable without the proper decryption key.
Overall, Encryption is a fundamental tool in the fight against cybercrime and protecting sensitive information. It offers an additional layer of security that helps maintain the privacy and integrity of our digital lives.
The Concept of End-to-End Encryption
While Encryption provides a layer of security, end-to-end Encryption takes it further. End-to-end Encryption is a security method that ensures data remains encrypted throughout its entire journey, from the sender to the recipient. This means that even the service provider, in this case, Apple’s iCloud, cannot decrypt the contents of the user’s data.
End-to-end Encryption is a topic of great importance in today’s digital age. With the growing reliance on technology for communication and data storage, protecting sensitive information has become a paramount concern. End-to-end Encryption addresses this concern by providing a robust solution that safeguards data from unauthorized access.
How Does End-to-End Encryption Work?
End-to-end Encryption involves encrypting the data at the sender’s end, and it can only be decrypted by the intended recipient. To achieve this, both parties must have the necessary encryption keys. When data is sent, it is encrypted using the recipient’s public key. Once the data reaches the recipient, their private key decrypts the information, making it readable again.
The end-to-end Encryption process is complex, involving various cryptographic algorithms and protocols. These algorithms ensure the data remains secure and cannot be easily compromised. By encrypting the data at the sender’s device and decrypting it at the recipient’s device, end-to-end Encryption ensures that the information remains confidential throughout its journey.
Since the encryption and decryption processes occur on the user’s devices, the service provider, such as Apple, cannot access the encryption keys or the decrypted data. This ensures that even if there is a security breach or an attempt to intercept the data, it remains secure and inaccessible.
The Benefits of End-to-End Encryption
- End-to-end Encryption offers several advantages, particularly regarding data privacy and security. By implementing this level of Encryption, iCloud ensures that only the sender and recipient can access the information exchanged. This means that even Apple cannot read or decrypt the data stored on iCloud servers.
- End-to-end Encryption gives users peace of mind, knowing that their sensitive information, such as photos, messages, and documents, remains private and inaccessible to anyone without the necessary decryption keys. It also protects against unauthorized access from hackers, government agencies, or even iCloud employees.
- Furthermore, end-to-end Encryption enhances trust between users and service providers. By implementing this robust security measure, service providers demonstrate their commitment to protecting user data and respecting their privacy. Knowing their information is handled carefully can increase user confidence and loyalty to the service.
In conclusion, end-to-end Encryption is a crucial aspect of data security in today’s digital landscape. By ensuring that data remains encrypted throughout its journey from sender to recipient, end-to-end Encryption provides a strong defense against unauthorized access. It protects sensitive information from falling into the wrong hands. As technology advances, the importance of end-to-end Encryption will only grow as individuals and organizations seek to secure their data and maintain their privacy.
iCloud and End-to-End Encryption

Now that we understand the concept of end-to-end Encryption let’s take a closer look at how Apple implements this technology in iCloud.
But before we delve into the details, let’s first understand why Encryption is crucial for user privacy and data security. In today’s digital age, where sensitive information is constantly being shared and stored online, the need for robust encryption measures has never been more critical. Encryption ensures that data is transformed into an unreadable format, making it virtually impossible for unauthorized individuals to access or decipher the information.
Regarding iCloud, Apple goes above and beyond to protect user data. They use strong encryption methods, ensuring that information remains secure in transit and at rest. This means that whether your data is being transmitted from your device to iCloud or stored on Apple’s servers, it is always encrypted, providing an additional layer of security.
How Apple Implements Encryption in iCloud?
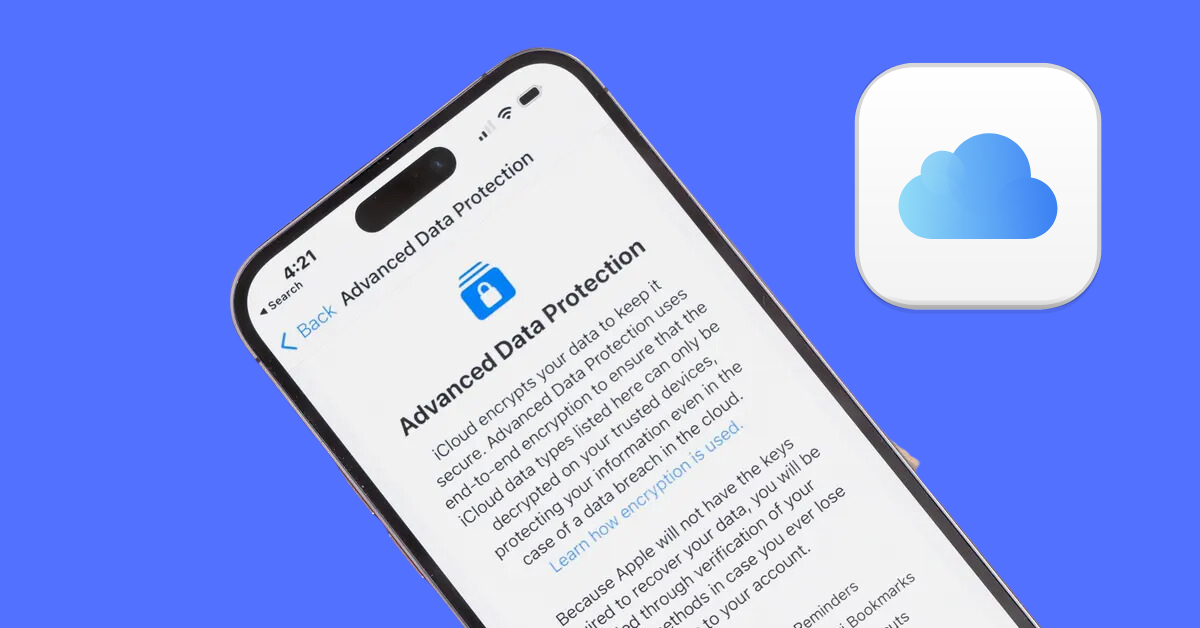
Apple’s commitment to user privacy and data security is evident in how they implement Encryption in iCloud. Let’s explore some of the key aspects of their encryption practices:
- Encryption in Transit: When you upload or download data to and from iCloud, it is protected using secure communication protocols such as HTTPS (Hypertext Transfer Protocol Secure). This ensures your data remains encrypted while it travels between your device and Apple’s servers, safeguarding it from potential eavesdropping or interception.
- Encryption at Rest: Once your data reaches iCloud, it is encrypted on Apple’s servers. This implies that even in the event of unauthorized server access, the intruder would only encounter encrypted data that is nearly dreadful to decipher without the correct decryption keys..
- Strong Encryption Algorithms: Apple employs industry-standard encryption algorithms, such as AES (Advanced Encryption Standard), to protect user data. These algorithms are widely recognized for their strength and reliability, ensuring your information remains secure.
What Data Does iCloud Encrypt?
iCloud encrypts a wide range of user data, providing comprehensive protection for your personal information. Here are some of the types of data that iCloud encrypts:
- Photos and Videos: Any photos or videos you store in iCloud are encrypted, safeguarding your precious memories from unauthorized access.
- Notes: Whether you use the Notes app on your iPhone, iPad, or Mac, any notes you sync with iCloud are encrypted, ensuring that your thoughts and ideas remain private.
- Contacts and Calendars: Your contact information and calendar events are encrypted when stored in iCloud, protecting your schedule and personal connections.
- iCloud Drive: Any files or documents you store in iCloud Drive are encrypted, providing an extra layer of security for your important files.
- iCloud Backup: When you back up your iOS devices to iCloud, the backup data is encrypted, ensuring that your device settings, app data, and other sensitive information are kept safe.
- iCloud Keychain: iCloud Keychain, Apple’s password management system, uses Encryption to protect your passwords, credit card information, and other confidential data.
- iCloud Mail: Even your emails are encrypted when stored in iCloud Mail, safeguarding your communication and ensuring that only you and the intended recipients can access the contents.
Apple demonstrates its unwavering commitment to user privacy and data security by encrypting all these data types. They understand the importance of protecting personal information and work diligently to ensure your data remains confidential and secure.
The Security of iCloud’s End-to-End Encrypted Data
Implementing end-to-end Encryption in iCloud contributes significantly to the overall security of user data.
How Secure is iCloud’s Encryption?
iCloud’s encryption methods are robust and designed to protect user data from unauthorized access. Apple utilizes advanced encryption algorithms and techniques to ensure the confidentiality and integrity of the information stored in iCloud.
The encryption keys used to protect user data in iCloud are unique and designed to resist brute-force attacks. Additionally, Apple regularly updates its encryption protocols and algorithms to avoid emerging threats and vulnerabilities, making iCloud even more secure.
Potential Vulnerabilities in iCloud’s Encryption
While iCloud’s end-to-end Encryption provides a high level of security, no system is entirely immune to vulnerabilities. Awareness of potential weak points that may leave user data susceptible to unauthorized access is essential.
One potential vulnerability is the strength of the user’s password. A weak, easily guessable password could compromise the security of their iCloud account. Choosing a strong, unique password and enabling two-factor authentication to add an extra layer of protection is crucial.
Another vulnerability could arise if the sender or recipient’s device is compromised. If a malicious individual gains access to the user’s device or iCloud account, they could intercept decrypted data before reaching the intended recipient. Therefore, practicing good device security and regularly updating software and apps to mitigate these risks is essential.
Comparing iCloud’s Encryption to Other Cloud Services
Lastly, compare iCloud’s Encryption to other popular cloud services like Google Drive and Dropbox.
iCloud vs. Google Drive: Encryption Comparison
Both iCloud and Google Drive offer Encryption to protect user data. However, there are some key differences in their approaches. iCloud employs end-to-end Encryption, meaning the data is encrypted and can only be decrypted by the recipient. On the other hand, while Google Drive encrypts data in transit and at rest, it does not offer end-to-end Encryption, allowing Google to access user data stored on its servers.
iCloud vs. Dropbox: Encryption Comparison
Similar to Google Drive, Dropbox also employs Encryption to safeguard user data. However, like Google Drive, Dropbox does not provide end-to-end Encryption for all user data. While Dropbox encrypts data in transit and at rest, the encryption keys are managed by Dropbox, giving them access to the user’s data.
Ultimately, regarding data privacy and security, end-to-end Encryption, as utilized by iCloud, offers the highest level of protection.
Key Takeaways
- Encryption transforms plain text into unreadable cipher text, protecting personal data from unauthorized access.
- End-to-end Encryption ensures data remains encrypted throughout its journey, and even service providers cannot decrypt it.
- Encryption plays a vital role in data security, reducing the risk of data breaches and identity theft.
- End-to-end Encryption enhances trust between users and service providers, demonstrating a commitment to privacy.
- Apple’s iCloud implements strong encryption methods, encrypting data in transit and at rest.
- iCloud encrypts photos, videos, notes, contacts, calendars, files, backups, keychain data, and emails.
- Weak passwords and compromised devices can be vulnerabilities in iCloud’s Encryption.
- iCloud’s end-to-end Encryption offers higher protection compared to Google Drive and Dropbox.
FAQs
What happens when you reset end-to-end encrypted data on an iPhone?
When you reset end-to-end encrypted data on an iPhone, the encryption keys used to protect the data are deleted, rendering the encrypted data unreadable and inaccessible. This means that even if the data is still stored on the device, it cannot be decrypted and accessed without the original encryption keys.
How do I enable end-to-end encryption in iCloud?
End-to-end encryption in iCloud is automatically enabled for certain data, such as messages and FaceTime calls. However, you cannot directly enable or disable end-to-end encryption for iCloud services. Apple implements end-to-end encryption as a default security measure to protect user data during transmission and storage.
Can you delete end-to-end encryption?
As an end-to-end encryption protocol is implemented at the system level, you cannot delete or disable it selectively. End-to-end encryption is designed to ensure data privacy and security by encrypting data at the sender’s device and decrypting it at the recipient’s device. This encryption cannot be removed or deleted without fundamentally altering the system architecture and compromising data security.
How does end-to-end Encryption protect my data on iCloud?
End-to-end Encryption protects your data by encrypting it with a unique encryption key that is only known to you. This means that even Apple cannot access or decrypt your data without your encryption key, providing an extra layer of privacy and security.
What types of data are end-to-end encrypted on iCloud?
End-to-end Encryption applies to various types of data on iCloud, including your photos, videos, documents, notes, and more. It ensures that your sensitive information remains secure and inaccessible to others.
Can I access my end-to-end encrypted data on multiple devices?
Yes, you can access your end-to-end encrypted data on multiple devices signed into your iCloud account. The encryption key is securely stored on each device, allowing you to seamlessly access and decrypt your data across all your trusted devices.
What should I do if I forget my encryption key for iCloud data?
If you forget your encryption key for iCloud data, Apple cannot recover it for you. It’s important to keep your encryption key in a safe and accessible place, such as a password manager or a secure offline storage method, to ensure you can always access your encrypted data.
Conclusion
In conclusion, end-to-end encrypted data on iCloud provides users with a secure and private environment for storing and exchanging sensitive information. By implementing strong encryption measures, Apple ensures that user data remains inaccessible to unauthorized individuals, including themselves. However, users need to maintain good security practices and be aware of potential vulnerabilities that may compromise the overall security of their iCloud account. Understanding the benefits and limitations of iCloud’s Encryption can empower individuals to make informed decisions about their data privacy and security in the digital realm.
