Introduction
What is Data Encryption?
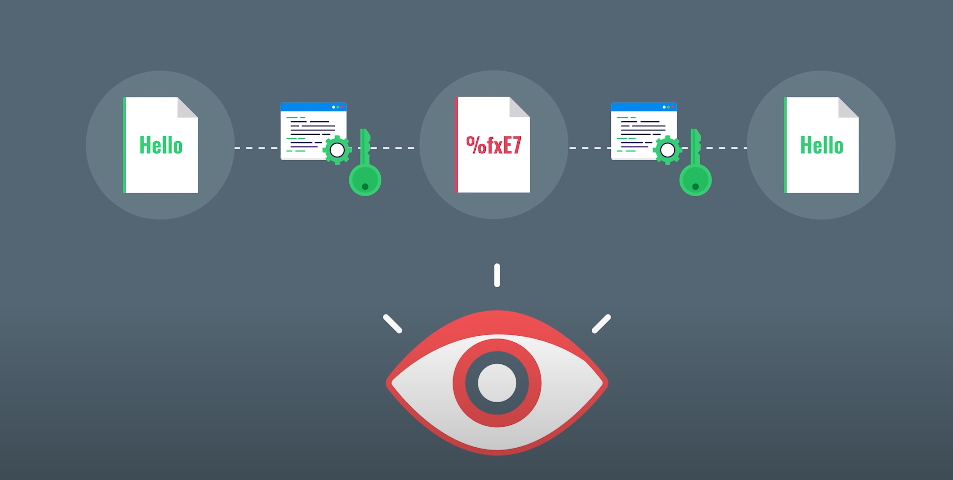
When we send or receive sensitive information, such as financial data or personal details, it’s crucial that the information is protected from prying eyes. That’s where data encryption comes in. Data encryption refers to the process of converting plain text into an unreadable format (known as ciphertext) using an algorithm or key.
Importance of Data Encryption
Data encryption is one of the most crucial aspects of cybersecurity. With an increase in cyber-attacks, data encryption has become a necessity. Data breaches can have severe consequences, including loss of reputation, financial loss, legal action, and even closure of businesses. By using data encryption techniques such as symmetric or asymmetric encryption methods, companies can protect their sensitive information from being accessed by unauthorized individuals or entities, providing peace of mind for both organizations and their customers alike.
Purpose of the Article
The purpose of this article is to help readers understand the two types of encryption and how they work. This article aims to break down the complexities surrounding data encryption into simple terms that can be easily understood by anyone.
By providing clear explanations of two types of data encryptions along with examples that illustrate their workings, readers will gain a deeper understanding of how cryptography technology can protect sensitive information from cyber threats like hacking or identity thefts.
Understanding the Types of Encryption
1. Symmetric Encryption
Definition of Symmetric Encryption
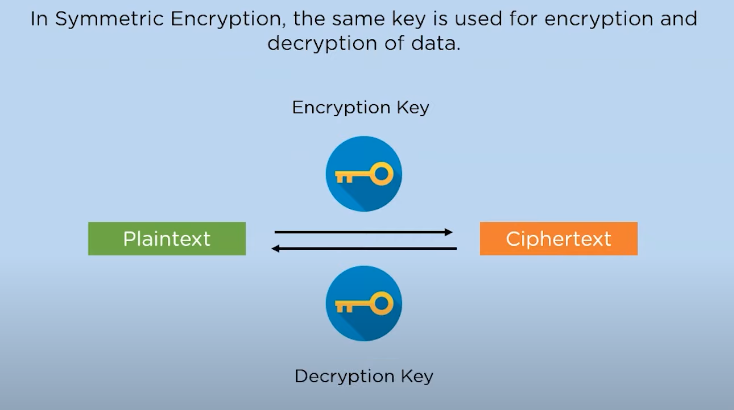
Symmetric encryption is a type of encryption in which the same secret key is used for both encrypting and decrypting the data. This means that whoever has the key can access the encrypted data. The encryption process involves converting plaintext into ciphertext using a cypher algorithm and the secret key. The decrypted message can only be obtained by reversing the process with an identical copy of the secret key.
Working Principle of Symmetric Encryption
The encryption process starts with the sender encrypting a message using a specific algorithm and a secret key. The encrypted message is then sent to the recipient who uses the same key to decrypt it.
The principle behind symmetric encryption is based on the idea that since both parties share the same key, they can communicate securely without worrying about unauthorized access. However, one of the main challenges with symmetric encryption is how to keep the shared secret key secure during transmission between parties.
To address this issue, various methods have been developed including password-based systems where users can create their own keys that are not shared with anyone else. Another method is using public-key cryptography which involves creating two different keys – one for encrypting data and another for decrypting it – making it harder for attackers to intercept and misuse sensitive information.
Types of Symmetric Encryption
Stream Ciphers
Stream ciphers are one of the two primary types of encryption algorithms, alongside block ciphers. Unlike block ciphers, which encrypt data in fixed-length blocks, stream ciphers encrypt data bit by bit or byte by byte. This type of encryption is commonly used for real-time communication and data transmission since it allows for a continuous flow of encrypted data.
Stream ciphers operate on a key and an initialization vector (IV), which is used to initialize the cipher before encryption begins. The key is combined with the IV to produce a keystream that is XORed with plaintext to create ciphertext. One advantage of stream ciphers over block ciphers is their relative simplicity, making them faster and more efficient for encrypting large amounts of data.
However, one potential drawback of stream ciphers is that they can be vulnerable to attacks if the same keystream is used repeatedly or if the IV and key are not properly protected.
Block Ciphers
Block ciphers are a type of encryption algorithm that operates on fixed-length blocks of data, usually 64 or 128 bits. Each block is transformed into a new block of the same length based on a secret key. The same key is used to encrypt and decrypt messages, and the security of the cipher depends on keeping the key secret. Block ciphers can be used in several modes, such as ECB (Electronic Codebook), CBC (Cipher Block Chaining), CFB (Cipher Feedback), and OFB (Output Feedback).
Block ciphers are widely used in modern cryptography for symmetric-key encryption in applications like secure communication channels and digital signatures. AES (Advanced Encryption Standard) is currently the most popular block cipher algorithm used today because it provides high levels of security while being fast enough for most applications.
While block ciphers are effective at providing confidentiality to encrypted data, they do not provide authentication or integrity checking by themselves. To achieve this, additional cryptographic algorithms like hash functions or message authentication codes must be employed alongside block ciphers.
Pros and Cons of Symmetric Encryption
One significant advantage of symmetric encryption is its speed because it uses a simple algorithm, making it ideal for encrypting large amounts of data. Also, symmetric encryption requires minimal processing power, which makes it efficient and cost-effective.
However, one significant disadvantage of symmetric encryption is its vulnerability to attacks since the same key used for encryption is also used for decryption. If an attacker gains access to the key, they can easily decrypt all encrypted data. Additionally, managing keys in symmetric encryption could be challenging since every individual who needs access to the encrypted data must have knowledge of the secret key.
2. Asymmetric Encryption
Definition of Asymmetric Encryption
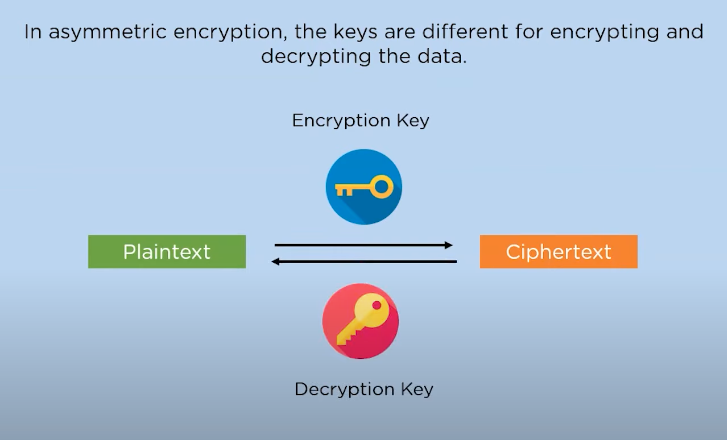
Asymmetric encryption, also known as public-key cryptography, is a cryptographic technique that uses two different but mathematically related keys – a public key and a private key. The public key is used to encrypt the data, while the private key is used for decryption. This means that anyone can encrypt data using the recipient’s public key, but only the recipient possessing the corresponding private key can decrypt it.
Working Principle of Asymmetric Encryption
The working principle of asymmetric encryption involves using complex mathematical algorithms to generate the two keys – one public and one private. When a sender wants to send an encrypted message, they use the recipient’s public key to encrypt it before sending it over a network or storing it on a device. The recipient then uses their private key to decrypt the message.
Types of Asymmetric Encryption
RSA Encryption
RSA algorithm was named after its inventors, Ron Rivest, Adi Shamir, and Leonard Adleman. In RSA encryption, the sender encrypts the message using the receiver’s public key, which can only be decrypted using the receiver’s private key. This ensures that only the intended recipient can read the message.
One of the major advantages of RSA encryption is that it provides secure communication over an insecure channel without requiring any pre-shared secret or symmetric keys. This makes it widely used in online transactions such as banking and e-commerce. However, RSA encryption has some limitations as well. It is computationally intensive and hence slower than symmetric-key algorithms for large data sets. Additionally, if someone gets access to your private key, they could decrypt all encrypted messages meant for you.
Elliptic Curve Cryptography (ECC)
Elliptic Curve Cryptography (ECC) is a type of public key cryptography that uses the algebraic structure of elliptic curves to create keys. ECC is gaining popularity as an alternative to traditional RSA encryption due to its ability to provide strong security with smaller key sizes. This makes it ideal for use in resource-constrained environments like mobile devices and Internet of Things (IoT) devices.
One of the main advantages of ECC is its resistance to attacks from quantum computers, making it a future-proof solution for secure communication. However, this does not mean that ECC is completely impervious to attacks. Like any other cryptographic algorithm, ECC has potential vulnerabilities that can be exploited by attackers who have access to sufficient computing power and resources.
Pros and Cons of Asymmetric Encryption
One of the major advantages of asymmetric encryption over symmetric encryption is its ability to provide secure communication over an insecure channel without any prior exchange of secret keys.
A disadvantage of asymmetric encryption is its relatively slow speed compared to symmetric encryption due to the complexity involved in generating large prime numbers used for creating public and private keys. Additionally, asymmetric encryption requires more computational power than symmetric encryption, which makes it less practical for some applications. Another drawback of using asymmetric encryption is that it may be vulnerable to attacks such as man-in-the-middle (MITM) attacks if not implemented correctly.
Differences Between Symmetric And Asymmetric Encryption
Symmetric encryption uses a single key to encrypt and decrypt data, which means that anyone who has the key can access the encrypted information. This makes it a fast method of encryption, but it’s not very secure as the key must be shared between parties who need to access the encrypted data.
On the other hand, asymmetric or public-key encryption uses two keys: one for encrypting data (public key) and another for decrypting (private key). The public key is available to anyone while the private key is kept secret by its owner. Asymmetric encryption provides better security than symmetric encryption because only those with the private key can decrypt data.
Similarities Between Symmetric And Asymmetric Encryption
Both symmetric and asymmetric encryption are designed to protect data from unauthorized access. They use mathematical algorithms to scramble the original message into an unreadable format that can only be deciphered by the intended recipient with a key or password.
Both methods can be used for secure communication over insecure networks such as the internet. For instance, symmetric encryption is commonly used for encrypting large amounts of data like files while asymmetric encryption is suited for securing small amount of data like emails.
Both encrypting methods have their flaws in terms of security risks. Symmetric encryption’s major drawback stems from the fact that it requires a shared key that can be intercepted by hackers while Asymmetric encryption’s weakness lies in its reliance on public and private keys which could get compromised if not properly secured.
When To Use Symmetric Encryption?
Symmetric encryption is best suited for situations where the same key is used for both encryption and decryption. This makes it ideal for secure communication between two parties who have already established a shared secret, such as in online banking transactions.
When to Use Asymmetric Encryption
Asymmetric encryption is primarily used in situations where secure communication between two parties is needed, but they have not previously shared a secret key. Asymmetric encryption can also be useful in cases where one party wants to send sensitive information securely to multiple recipients without having to create multiple copies of the message or use multiple keys. For instance, when sending an email that contains confidential information, asymmetric encryption can be employed to ensure that only intended recipients can read the message.
3. Hybrid Encryption
Definition of Hybrid Encryption
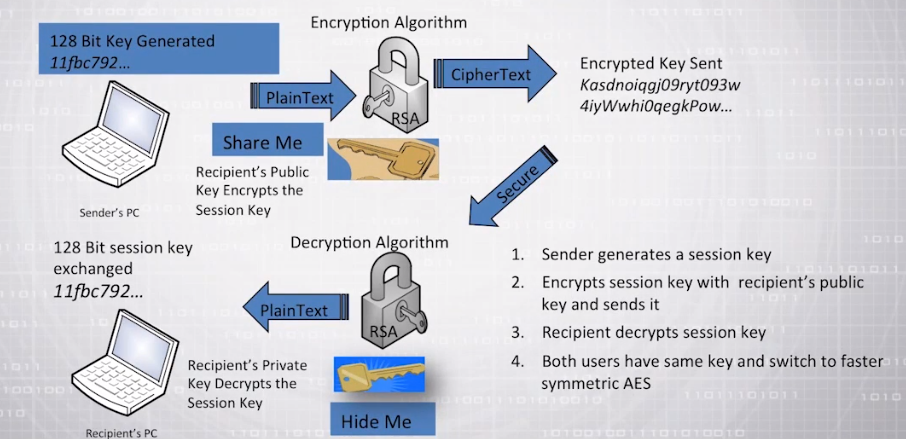
Hybrid encryption is a cryptographic technique that combines symmetric and asymmetric encryption to ensure secure communication. It relies on both public key cryptography and symmetric key cryptography to encrypt data. In this method, the data is encrypted using a symmetric key, which is then encrypted with the recipient’s public key using asymmetric encryption. The recipient can then use their private key to decrypt the symmetric key, which can be used to decrypt the original message.
Hybrid encryption is commonly used in online transactions such as e-commerce sites, banking websites, and email services where security is crucial. It helps protect sensitive information like credit card details, login credentials, and personal messages from unauthorized access by hackers or other malicious entities while in transit over networks vulnerable to interception.
Working Principle of Hybrid Encryption
A message sender uses the recipient’s public key to encrypt data with an asymmetric algorithm, which generates a random symmetric key that encrypts the actual message.
The encrypted message is then sent to the receiver who can decrypt it by first using their private key to extract the symmetric key and then using this key to decrypt the actual message. This process ensures high-grade security as only someone possessing the recipient’s private key can access the encrypted information.
Advantages of Hybrid Encryption
Hybrid encryption has the ability to protect large amounts of data without sacrificing performance. Symmetric encryption used alone can become burdensome when dealing with large volumes of data, while asymmetric encryption can be slow and computationally intensive. Hybrid encryption balances these two methods, ensuring that sensitive information remains secure while maintaining optimal system performance.
Another benefit of hybrid encryption is its flexibility in adapting to changing security requirements. As cyber threats continue to evolve, organizations need an agile and adaptable approach to security. By utilizing hybrid encryption, companies can adjust their security measures by choosing different algorithms or key sizes based on their evolving needs without compromising on performance or scalability.
Challenges And Limitations Of Data Encryption
Key Management
Key management is an essential aspect of data encryption. It refers to the process of creating, storing, and protecting cryptographic keys used for encrypting and decrypting data. Essentially, it involves the secure distribution and administration of keys to authorized users while ensuring that unauthorized individuals do not gain access.
Effective key management is critical for maintaining data confidentiality, integrity, and availability. Therefore proper handling ensures that these two keys remain safe from attackers. Organizations should adopt robust key management policies that define how cryptographic keys are generated, and stored securely in a central repository accessible only by authorized personnel or automated processes.
Computational Power
Computational power refers to the capacity of a computing system to process and analyze large amounts of data at high speeds. The more powerful the system, the easier and faster it is for it to crack encrypted data. As computing power continues to grow exponentially year after year, even asymmetric encryption algorithms can eventually be cracked using brute force attacks with enough computational resources. This highlights the importance of constantly updating and improving cryptographic methods in order to stay ahead of potential threats posed by advances in computing technology.
Legal Issues
Legal issues can arise when it comes to using these types of encryption methods. For example, in some countries, it may be illegal to use certain types of encryption methods or to use them without authorization from government agencies. Additionally, businesses that handle sensitive information may be required by law to use certain levels of encryption in order to protect their customers’ personal information.
It’s also important for businesses and individuals alike to understand how their encrypted data will be handled in legal situations such as court cases or investigations. In some cases, law enforcement agencies may have methods for accessing encrypted data even if they don’t have the decryption key, which could potentially compromise sensitive information.
Future Of Data Encryption
Advancements in Encryption Technology
The continuous development of technology has paved the way for more advanced forms of encryption.
One of the most significant advancements in encryption technology is the use of end-to-end encryption. This type of encryption ensures that only authorized parties can access the data being transmitted. End-to-end encryption uses unique keys to encrypt and decrypt messages, making it almost impossible for hackers to intercept and read sensitive information.
Another advancement in encryption technology is homomorphic encryption. Homomorphic encryption allows computations to be performed on encrypted data without having to decrypt it first. This method ensures that data remains confidential, even when being processed or analyzed by third-party applications or services.
Potential Risks of Future Encryption
One of the potential risks of future encryption is that it could become too complicated for the average user to understand. As encryption technology evolves, it may require more technical knowledge and training to implement properly. This could lead to errors or misconfigurations that result in data breaches or other security incidents.
Another risk is the misuse of encrypted communications by criminals or terrorists. As encryption becomes more ubiquitous and robust, it may be used as a tool to conceal illegal activities and communications from law enforcement agencies. This creates a dilemma for governments that must balance the need to protect their citizens’ privacy with the need to prevent crime and terrorism.
There is also concern about “backdoors” being built into encryption systems by governments or other entities. While these backdoors would ostensibly be used only for legitimate purposes such as law enforcement investigations, they could also be exploited by hackers or other malicious actors if discovered.
Future of Quantum Encryption
Quantum encryption is the future of data security. It provides an unbreakable encryption method that leverages the principles of quantum mechanics to secure data transmissions. Unlike classical encryption methods, quantum cryptography relies on the laws of physics to encrypt and transmit information securely. The technology works by encoding messages onto particles of light (photons) and then sending them through a fibre-optic cable from one location to another.
The future of quantum encryption looks bright as researchers continue to explore new ways to improve upon existing technologies. Recent advancements in quantum key distribution have made it possible for multiple parties to communicate securely using shared keys generated through entangled photons.
FAQs
What is Data Encryption Used For?
Data encryption secures online transactions such as credit card payments and bank transfers. In this case, sensitive information such as credit card numbers, account numbers, and personal identification details are encrypted before being transmitted over the Internet. This ensures that only authorized parties can access the information and reduces the risk of fraud or identity theft.
It also secures confidential communications such as email messages and instant messages. Encryption tools like Pretty Good Privacy (PGP) can be used to encrypt emails with a public key that only the recipient can decrypt using their private key. This makes it virtually impossible for anyone else to intercept or read the message without authorization.
How Secure is Data Encryption?
While data encryption provides an added layer of security, it is not foolproof. The strength of the encrypted message relies heavily on the complexity of the password or key used to encrypt it. Weak passwords can easily be cracked by sophisticated hackers using brute force attacks or by exploiting vulnerabilities in software systems that store these keys.
Can Encrypted Data be Hacked?
It is very unlikely for encrypted data to be hacked unless the encryption key or password used to lock it has been compromised. In other words, as long as the encryption key remains secure and uncompromised, hackers will not be able to decrypt the data.
Can Encrypted Data be Decrypted?
If someone has access to the key used for symmetric encryption, they can easily decrypt the encrypted data. Asymmetric encryption, on the other hand, is more secure as only the holder of the private key can decrypt the encrypted data. However, if someone gains access to both keys or finds a vulnerability in the algorithm used for either type of encryption, they may be able to decipher encrypted data.
Conclusion
Data encryption has become an essential aspect of modern-day computing. Its ability to keep sensitive information secure from unauthorized access makes it a vital tool for individuals and businesses alike. The two primary types of encryption – symmetric and asymmetric – provide different levels of security depending on the intended use.
