Introduction
Data posting to the database is common for web applications that store and retrieve information from a server. However, this process can also introduce security risks if not handled properly. This article will discuss some secure data posting methods to the database.
Insecure data posting can lead to serious risks such as identity theft, financial fraud, and reputation damage. When you post sensitive information like your full name, address, phone number, social security number, credit card details, or login credentials, you expose yourself to potential hackers and cybercriminals who can use that information for malicious purposes. Moreover, posting inappropriate or offensive content can also harm your personal or professional image and affect your relationships with others. Thinking twice before sharing everything online and considering the potential consequences is important.
To protect yourself from the risks of insecure data posting, you should always use strong and unique passwords, allow two-factor authentication whenever possible, and be cautious of phishing scams. Additionally, you should avoid sharing sensitive information on public forums or social media platforms and only share it with trusted sources through secure channels.
The Importance Of Security In Data Posting
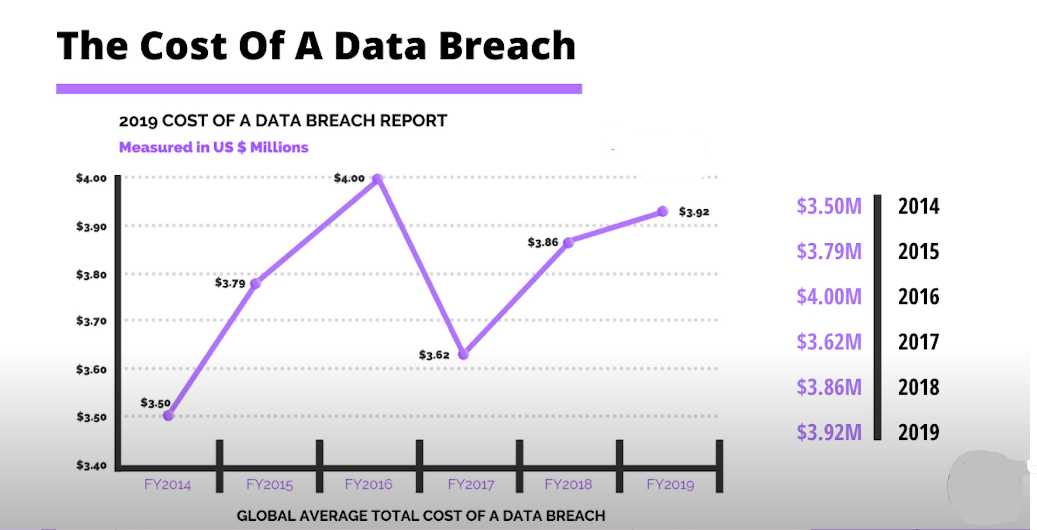
The importance of security in data posting cannot be overstated. In the modern digital age, where information is readily available and accessible, protecting sensitive information from falling into the wrong hands is crucial. Data breaches can result in considerable financial losses, damage to reputation, and even legal consequences. Therefore, taking the necessary actions to protect your personal and business data is essential.
Encryption is one of the most operative ways to ensure data security. Encryption is converting data into a code that only authorized parties can decipher. This ensures that even if the data is intercepted, unauthorized parties cannot read it. Additionally, you should always use secure networks when sharing sensitive information and avoid using public Wi-Fi networks.
Secure Methods Of Posting Data To The Database
When posting data to a database, you can use several secure methods to protect the information. Here are some best practices to follow:
- Use encryption: Encrypting the data before posting it to the database can add an extra layer of security. This makes it more difficult for unauthorized parties to access the information.
- Use parameterized queries: Parameterized queries can help prevent SQL injection attacks. This involves using placeholders for variables in SQL statements, which are then replaced with actual values at runtime.
- Limit access: Only allow authorized users to access the database and limit their access to only the necessary data. This can prevent unauthorized access and reduce the risk of data breaches.
- Regularly update software: Keep your database software up-to-date with modern security patches and updates. This can help prevent vulnerabilities from being exploited by attackers.
Following these best practices ensures your data remains secure when posting to a database.
Different Methods Of Secure Data Posting To The Database
There are several methods of secure data posting to the database, including:
- Parameterized queries: This method uses placeholders for user input and then binds the values to those placeholders. This prevents SQL injection attacks by ensuring user input is treated as data rather than executable code.
- Stored procedures: This method involves creating pre-defined SQL statements stored on the server and executed when the application calls. This helps to prevent SQL injection attacks by limiting the amount of user input that can be executed as part of a query.
- Input validation: This method involves checking user input to confirm that it achieves certain criteria, such as being of the correct data type and within a certain range of values. This helps to prevent SQL injection attacks by ensuring that only valid input is used in SQL queries.
- Escaping special characters: This method adds escape characters to user input containing special characters, such as quotes or semicolons. This helps prevent SQL injection attacks by ensuring these characters are treated as data rather than executable code.
- Limiting access privileges: This method involves restricting the access privileges of database users to limit the damage that can be done in the event of a SQL injection attack. This includes limiting the ability to execute certain queries and restricting access to sensitive data.
Secure Data Posting With SQL Injection Prevention
Definition Of SQL Injection
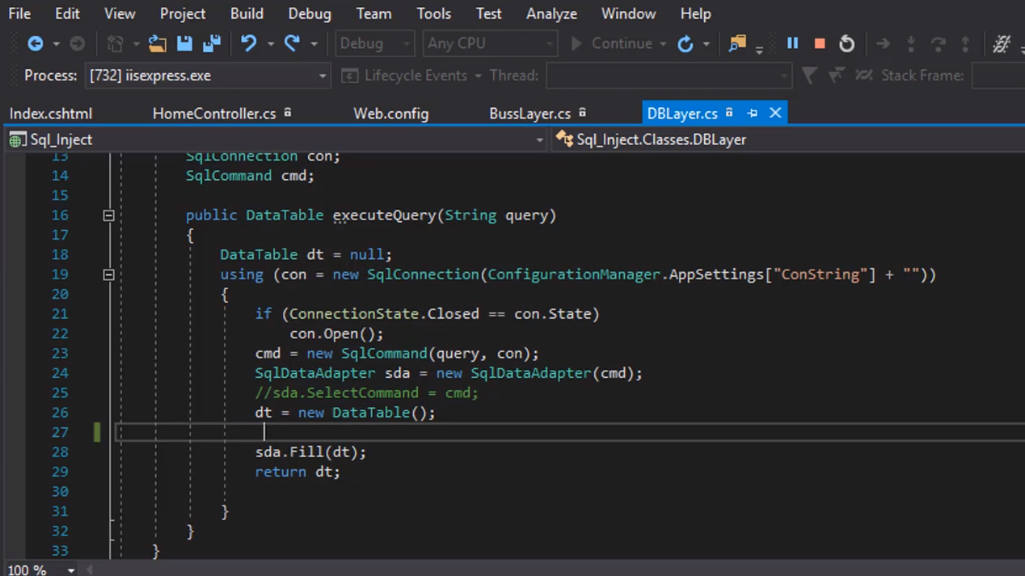
SQL injection is a cyber-attack where an attacker injects harmful code into a database query, allowing them to access or manipulate sensitive data. This can occur when an application fails to validate user input properly, allowing an attacker to insert SQL commands into the input fields. The injected SQL commands can then be executed by the database, potentially giving the attacker access to sensitive information or allowing them to modify or delete data. Implementing proper input validation and using prepared statements or parameterized queries can prevent SQL injection attacks.
Prevention Measures
The prevention measures for SQL injection attacks include:
- Implement proper input validation: This involves validating user input to ensure it only contains the expected data types and formats. This can be done by using regular expressions or other validation techniques.
- Use parameterized queries: This involves using placeholders for user input in SQL statements, which are then replaced with the actual values at runtime. This helps to prevent SQL injection attacks by separating the SQL code from the handler input.
- Use prepared statements: This involves preparing SQL statements before executing them, which helps to prevent SQL injection attacks by separating the SQL code from the user input.
- Limit database permissions: This involves restricting the permissions of database users to only the necessary actions. This helps to prevent SQL injection attacks by limiting the damage that can be done if an attacker gains access to the database.
- Keep software up to date: This involves keeping the software and database systems up to date with modern security patches and updates. This helps to prevent SQL injection attacks by addressing known vulnerabilities in the software.
Why Is Secure Data Posting Important?
Secure data posting is important to protect sensitive information from unauthorized access or manipulation. Without proper security measures, data posted to a database can be vulnerable to cyber attacks such as SQL injection or data breaches. By ensuring that data is posted securely, organizations can maintain their data’s confidentiality, integrity, and availability and protect themselves and their customers from potential harm.
Risks Of Insecure Data Posting
The risks of insecure data posting include the following:
- Unauthorized access: Hackers or unauthorized users can gain access to sensitive information, like personal data, financial information, or trade secrets.
- Data manipulation: Attackers can alter or delete data, leading to incorrect decisions, financial loss, or reputational damage.
- Malware infection: Malicious software can be injected into the database, spreading to other systems and causing damage.
- Compliance violations: Organizations that handle sensitive data are subject to various regulations and compliance standards, such as GDPR or HIPAA. Failure to comply with the regulations can result in legal and financial penalties.
- Reputational damage: A data breach or security incident can damage an organization’s reputation and erode customer trust, leading to loss of business and revenue.
Best Practices For Secure Data Posting
When it comes to posting data online, there are several best practices you should follow to ensure the security of your information. Here are some tips:
In the realm of data posting, employing optimal security measures is of paramount importance. The safeguarding of sensitive information demands meticulous attention to detail and the implementation of robust encryption techniques. This article delves into the best practices for securing data during the process of posting, providing you with a comprehensive understanding of the subject matter.
Utilize Advanced Encryption Protocols

When transmitting data over a wireless network, it is imperative to employ advanced encryption protocols. Encryption serves as a protective shield, rendering the data incomprehensible to unauthorized individuals. By employing state-of-the-art encryption algorithms, the security of your data can be significantly enhanced. These algorithms employ complex mathematical computations, converting the data into an encrypted form that can only be deciphered with the corresponding decryption key.
Embrace Multi-Factor Authentication
Implementing multi-factor authentication adds an additional layer of security to your data posting endeavors. This approach necessitates the provision of multiple credentials for accessing the posted information. By requiring users to provide two or more forms of identification, such as a password, a fingerprint scan, or a security token, the risk of unauthorized access is substantially mitigated. Multi-factor authentication serves as a formidable deterrent against cyber threats, enhancing the overall security posture of your data.
Regularly Update Security Measures
To stay ahead of evolving cyber threats, it is essential to regularly update your security measures. Software vulnerabilities can be exploited by malicious actors, compromising the integrity of your data. By promptly applying security patches and updates, you can close potential entry points for unauthorized access. Additionally, keeping abreast of the latest encryption standards and best practices ensures that your data remains protected against emerging threats.
Employ Intrusion Detection Systems
Intrusion detection systems play a crucial role in identifying and mitigating potential security breaches. These systems continuously monitor network traffic, analyzing patterns and behaviors to detect any suspicious activities. By promptly alerting system administrators of potential threats, intrusion detection systems enable swift response and remediation. Their implementation bolsters the overall security posture of your data posting process, providing an additional layer of defense against unauthorized access attempts.
Conduct Regular Security Audits
Regular security audits are indispensable in evaluating the effectiveness of your data posting security measures. These audits involve comprehensive assessments of your systems, protocols, and infrastructure to identify potential vulnerabilities. By conducting periodic reviews, you can proactively address any weaknesses and enhance the resilience of your security framework. This diligent approach ensures that your data remains secure and protected from potential threats.
Following these best practices, you can protect your personal and business data from threats and secure your information.
Recommended Scenarios For Each Secure Data Posting Method
The recommended scenarios for each secure data posting method depend on various factors, such as the size and complexity of the application, the programming language used, and the level of security required. If the application is small and simple, and the level of security required is not very high, then using prepared statements or parameterized queries may be sufficient. These methods can provide basic protection against SQL injection attacks without adding significant overhead or additional setup time.
On the other hand, if the application is large and complex, and the level of security required is high, then using an ORM framework may be recommended. ORM frameworks offer a higher level of abstraction and can reduce the risk of SQL injection attacks. However, they may introduce performance overhead and require additional configuration and setup time.
Conclusion
In conclusion, securely posting data is essential to protect sensitive information from unauthorized users. To achieve this, it is important to use HTTPS protocol when transmitting data over the internet. By doing so, you can confirm that the data remains encrypted and cannot be intercepted by hackers. Remember always to prioritize the security of your data when posting online.
The conclusion of your post highlights the key points discussed in the article and emphasizes the importance of secure data posting to the database. It reminds readers to prioritize data security and use HTTPS protocol to ensure that sensitive information remains encrypted and protected from unauthorized access. Your post effectively delivers the message without being repetitive or redundant. Individuals and businesses must prioritize data security and take the necessary steps to protect sensitive information. Using HTTPS protocol and implementing other security measures, we can help ensure our data remains safe and secure.
Frequently Asked Questions (FAQs)
What Is Data Posting To The Database?
Data posting to the database refers to adding or updating information in a database. This can be done via several means, such as web forms, APIs, or direct database connections. It is important to ensure the data posted is valid and secure to prevent potential vulnerabilities or attacks on the database.
What Is HTTPS Protocol, And How Does It Secure Data Posting?
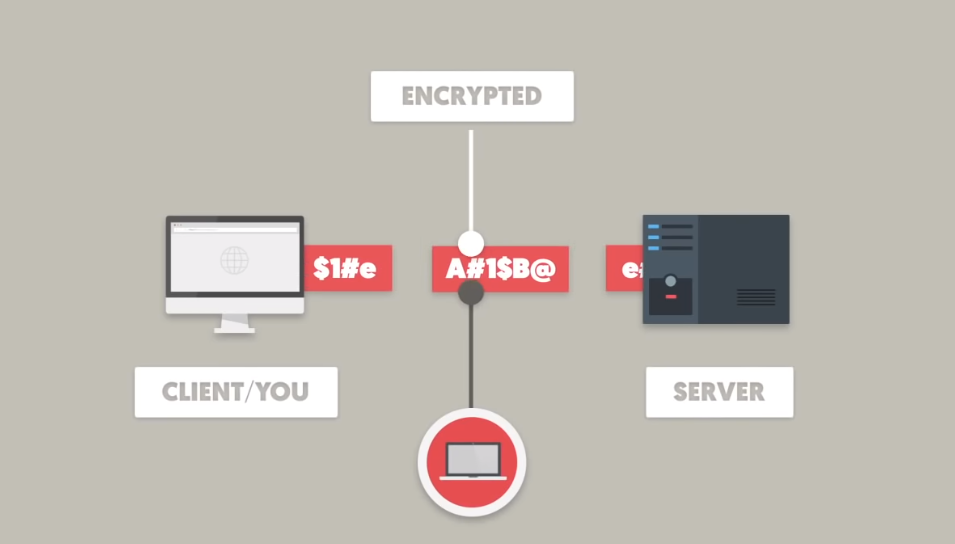
HTTPS stands for Hypertext Transfer Protocol Secure. An internet communication protocol encrypts data sent between a web server and a web browser. This encryption ensures that the data is secure and cannot be interrupted or tampered with by unauthorized parties. When data is posted using HTTPS, it is first encrypted before being sent over the internet. The receiving server then decrypts the data using only its private key. This confirms that the data remains secure and confidential during transmission.
What Is Encryption, And How Does It Secure Data Posting?
Encryption converts plain text or data into a coded language authorized parties with the decryption key can only understand. In the case of HTTPS, when data is posted using this protocol, it is first encrypted before being sent over the internet. This means that the data is transformed into an unreadable arrangement that can only be deciphered using a private key possessed by the receiving server. As a result, even if someone intercepts the data during transmission, they cannot read or make sense of it without the decryption key. This confirms that the data remains secure and confidential during transmission.
What Is Input Validation, And How Does It Secure Data Posting?
Input validation is checking the data entered by a user to ensure that it meets certain criteria or standards. This is done to prevent malicious or invalid data from being submitted to a system, which could compromise the system’s security or the data it contains. For example, if a user must enter their email address, input validation can ensure that the email address is in the correct format (e.g., contains an “@” symbol and a domain name). This can prevent users from entering invalid email addresses or using the input field to inject malicious code into the system.
Input validation can secure data posting by ensuring only valid data is submitted to the system. This can prevent malicious users from submitting invalid or harmful data that could compromise the security of the system or the data it contains. By validating the input data, the system can ensure that it is safe and secure and can process it accordingly.
What Is Server-Side Validation, And How Does It Secure Data Posting?
Server-side validation is validating the data entered by the user on the server side before it is processed and stored in the database. It involves checking the data against predefined rules and constraints to ensure it is valid, accurate, and safe. Server-side validation helps secure data posting by preventing invalid or malicious data submissions. It ensures the data is in the correct format, meets the required length and size, and contains only valid characters.
The system can detect and reject any attempts to inject malicious code into the data by performing server-side validation, such as SQL injection attacks. This helps to protect the system from potential security breaches and ensures that the data stored in the database is accurate, reliable, and safe to use.
Can Secure Data Posting Be Achieved Without HTTPS?
No, secure data posting cannot be achieved without HTTPS. HTTPS (Hyper Text Transfer Protocol Secure) is an encrypted protocol that provides secure communication over the internet. It ensures that the data transmitted between the user’s browser and the server is encrypted and cannot be intercepted by hackers. Without HTTPS, the transmitted data is vulnerable to interception and can be accessed by unauthorized users. Therefore, it is crucial to use HTTPS to ensure secure data posting.
