Overview of Salesforce Data Loader
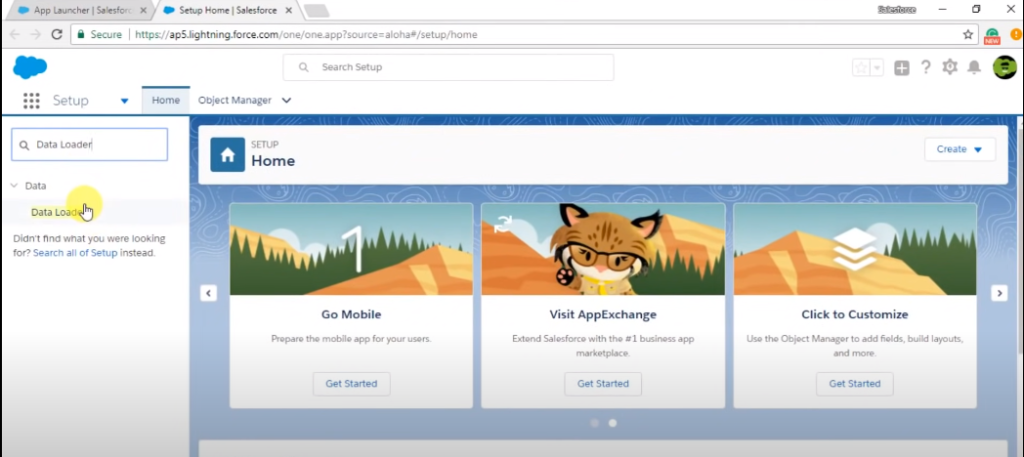
Salesforce Data Loader is a powerful tool that allows users to import, export, and delete data in Salesforce. It is a desktop application that can be installed on Windows or Mac OS and is available for free to Salesforce users. The Data Loader supports various data formats, including CSV, XML, and Excel, and can handle large data sets. It also offers a command-line interface for automation and scheduling data loads.
Key Features And Functionalities of Data Loader
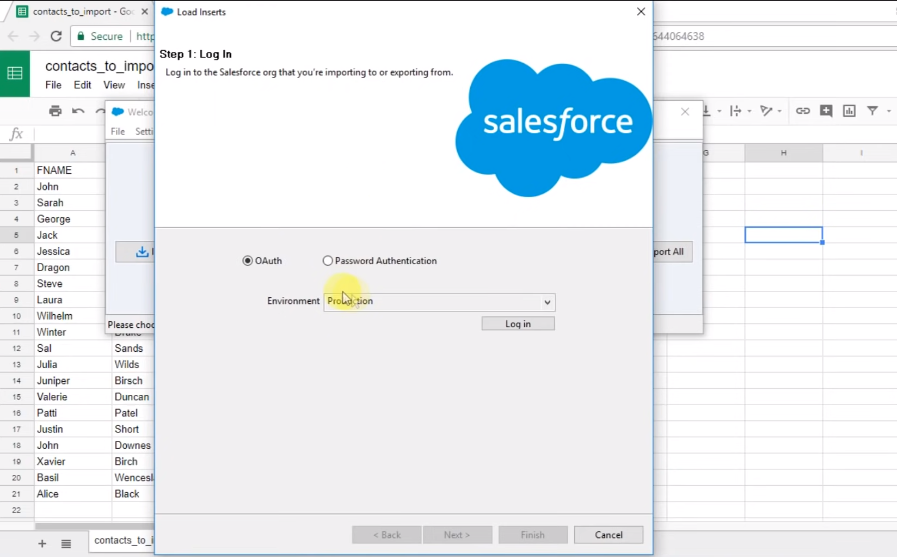
Some of the key features and functionalities of Salesforce Data Loader include:
1. Import and Export Data: The Data Loader allows users to easily import and export data between Salesforce and external systems. Users can import data from CSV, XML, and Excel files and export data to CSV or XML files.
2. Bulk Data Management: The Data Loader can handle large data sets and allows users to perform bulk operations, such as updating or deleting multiple records at once.
Security Tokens in Salesforce
Security tokens in Salesforce are unique, automatically generated codes that add an extra layer of security to a user’s login credentials. They are required for users who access Salesforce from outside the trusted IP range or from a new device or browser. The security token is sent to the user’s email address and must be entered along with their password to complete the login process. By requiring a security token, Salesforce helps to ensure that only authorized users can access sensitive data and information.
Explanation of Security Tokens
Security tokens are automatically generated codes that add an extra layer of security to a user’s login credentials. They are required for users who access Salesforce from outside the trusted IP range or from a new device or browser. The security token is sent to the user’s email address and must be entered along with their password to complete the login process. By requiring a security token, Salesforce helps to ensure that only authorized users can access sensitive data and information. This helps to protect against unauthorized access and potential security breaches.
How Security Tokens Enhance Data Security
Security tokens play a critical role in enhancing data security in Salesforce. By requiring a security token for login, Salesforce ensures that only authorized users can access sensitive data and information. This helps to protect against unauthorized access and potential security breaches. When a user logs in from outside the trusted IP range or from a new device or browser, Salesforce sends a security token to the user’s email address. The user must then enter this security token along with their password to complete the login process.
Exceptions to Security Token Requirement
There are some exceptions to the security token requirement in Salesforce. For example, if a user logs in from a trusted IP address or a pre-approved device, they may not need to enter a security token. Additionally, if an organization has enabled single sign-on (SSO) for their Salesforce org, users may not need to enter a security token to log in.
Scenario 1: Trusted IP Ranges
In Salesforce, trusted IP ranges allow users to access their org without requiring a security token. This means that if a user logs in from an IP address that is within the trusted IP range defined by their organization, they will not be prompted to enter a security token. To set up trusted IP ranges in Salesforce, an administrator can navigate to Setup > Security Controls > Network Access and add the IP addresses or ranges that they want to trust.
How trusted IP ranges can bypass security token requirement?
Trusted IP ranges can bypass security token requirements because they are a way for Salesforce to recognize and trust certain IP addresses or ranges as being safe and authorized to access their organization’s data. When a user logs in from an IP address within the trusted range, Salesforce assumes that the user is already authorized and does not require an additional security token to prove their identity. This makes it more convenient for users to access their organization’s data without sacrificing security.
Configuring Trusted IP Ranges in Salesforce
To configure trusted IP ranges in Salesforce, follow this steps:1. Log in to your Salesforce account and go to Setup.
2. In the Quick Find box, type “network access”.
3. Click on “Network Access” under the Security Controls section.
4. Click the “New” button to add a new trusted IP range.
5. Enter a name for the trusted IP range.
6. Enter the starting and ending IP addresses for the range.
Scenario 2: Single Sign-On (SSO)
To set up Single Sign-On (SSO) in Salesforce, you can follow this steps:1. Log in to your Salesforce account and go to Setup.
2. In the Quick Find box, type “single sign-on”.
3. Click on “Single Sign-On Settings” under the Security Controls section.
4. Choose the type of SSO you want to set up (for example, SAML or OAuth).
5. Follow the instructions provided by your identity provider (IDP) to configure
How SSO Eliminates The Need For Security Tokens
Single Sign-On (SSO) eliminates the need for security tokens by allowing users to authenticate once and gain access to multiple applications or systems without having to enter their credentials again. With SSO, a user logs in to a single system, known as the identity provider (IDP), and that system then authenticates the user and provides them with a token that can be used to access other systems or applications that are connected to the IDP.
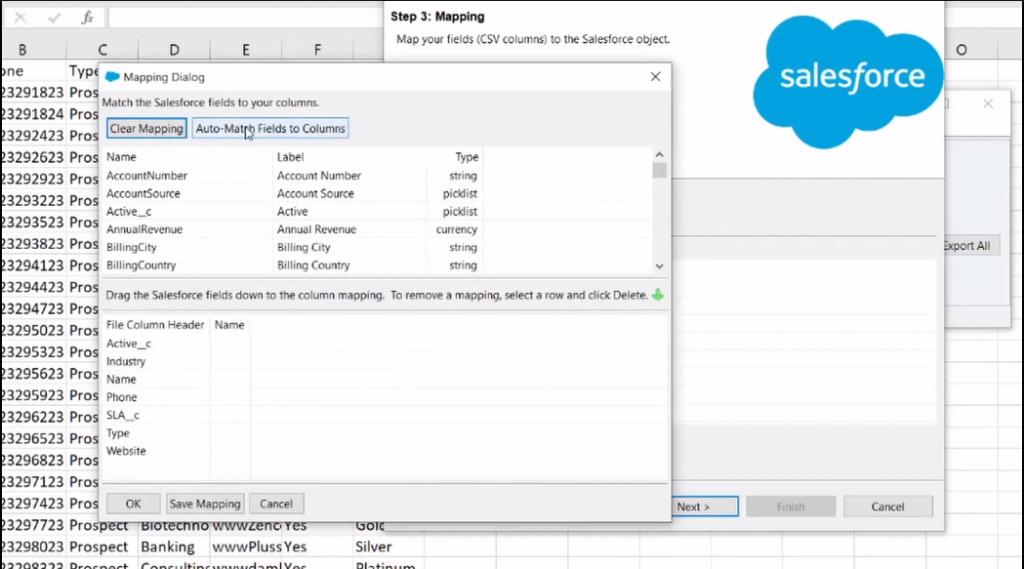
Integrating SSO with Salesforce Data Loader
Integrating SSO with Salesforce Data Loader can be done by following these steps:
1. Set up SSO in Salesforce: This involves configuring the Identity Provider (IDP) and Service Provider (SP) settings in Salesforce. You will need to create a connected app and enable SSO for the app.
2. Configure Data Loader: Next, you will need to configure Data Loader to use SSO. This involves specifying the SAML endpoint and the certificate for the IDP.
Best Practices for Data Security
When it comes to data security in Salesforce, there are several best practices that you should follow. Here are a few examples:
1. Limit Access: Only provide access to data and features that are necessary for each user’s job. Use roles, profiles, and permission sets to control access.
2. Use Strong Passwords: Encourage users to create strong passwords and require them to change their passwords periodically. Consider implementing two-factor authentication.
3. Monitor Login Activity: Monitor login activity and set up alerts for suspicious activity. Use IP restrictions to limit access to trusted networks.
4. Encrypt Sensitive Data: Use encryption to protect sensitive data, such as credit card numbers and Social Security numbers. Consider using Salesforce Shield for additional security features.
5. Regularly Review Security Settings: Regularly review your security settings and adjust them as needed. Stay up-to-date on the latest security threats and best practices.
By following these best practices, you can help ensure that your Salesforce data is secure and protected.
Conclusion
In conclusion, Salesforce provides a robust security framework to protect your data. However, it’s essential to take additional steps to ensure the security of your data. By implementing best practices like using strong passwords, enabling multi-factor authentication, limiting user access, encrypting sensitive data, and regularly reviewing security settings, you can enhance the security of your Salesforce data. It’s crucial to stay vigilant and up-to-date on the latest security threats and best practices to keep your data safe.
Common FAQs
What is the purpose of security tokens in Salesforce?
The purpose of security tokens in Salesforce is to provide an additional layer of security for user authentication. When a user logs in to Salesforce from an untrusted network or device, they are required to enter a security token in addition to their username and password. This helps to prevent unauthorized access to Salesforce data and protects against potential security breaches. Security tokens are randomly generated and can be obtained from the user’s Salesforce account settings.
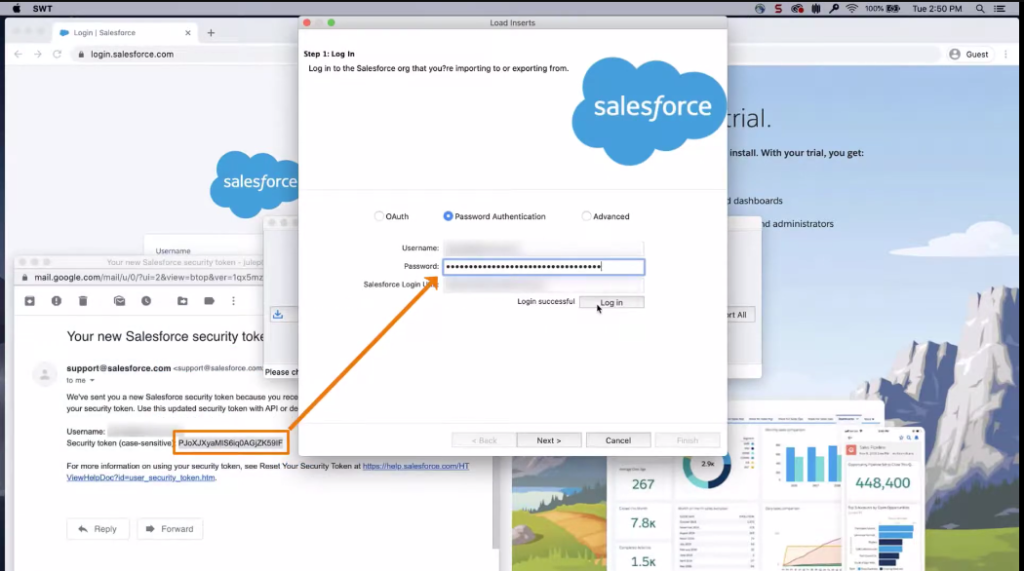
How can I generate a security token in Salesforce?
To generate a security token in Salesforce, follow these steps:
1. Log in to your Salesforce account.
2. Click on your profile picture and select “Settings.”
3. Under the “Personal” tab, click on “Reset My Security Token.
4. Salesforce will send an email to the email address associated with your account containing your security token.
5. Use the security token along with your username and password when logging in to Salesforce from an untrusted network or device.
Do I need a security token for every API integration?
Yes, you will need a security token for every API integration you set up in Salesforce. This is to ensure that your account is secure and that only authorized users can access your data. You can generate a new security token at any time by following the steps mentioned earlier. It is recommended that you keep your security token safe and secure, and avoid sharing it with anyone else.
Can I use Data Loader without a security token?
No, you cannot use Data Loader without a security token. The security token is required to authenticate your connection to Salesforce and ensure that your data remains secure. Without a security token, you will not be able to establish a connection to Salesforce using Data Loader. Therefore, it is important to ensure that you have a valid security token before attempting to use Data Loader or any other Salesforce API integration.
