Introduction
Session data is an important aspect of security logs that can provide valuable insights into user activity and potential security threats. This article will explore what session data is, why it is important, and how to interpret it in security logs. Understanding session data can better protect your organization’s data and systems from potential security breaches.
Which Statement Describes Session Data In Security Logs?
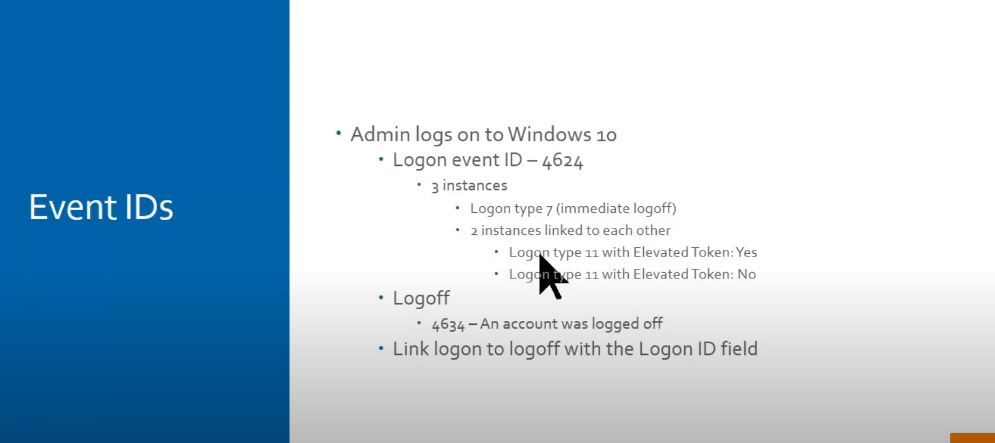
Session data in security logs refers to information recorded about user activity during a particular session, such as login time, logout time, and the actions taken during the session. This data can provide insights into potential security threats and help organizations identify and respond to security breaches.
Which Statement Describes Statistical Data In Network Security Monitoring Processes?
Statistical data in network security monitoring processes refers to collecting and analyzing data related to network traffic, usage patterns, and anomalies. This data can be applied to identify potential security threats, such as unusual spikes in traffic or unauthorized access attempts, and to develop strategies for preventing and mitigating such threats. Statistical data analysis can also help organizations identify trends and patterns in network activity, informing decisions about network architecture and resource allocation.
Session Data Basics
Session data in security logs refers to the information recorded about a user’s interaction with a system or application during a specific session. This information includes login and logout times, IP addresses, user IDs, and the actions taken during the session. Session data is critical for identifying and investigating security incidents, providing a detailed record of what occurred during a particular session. It can also monitor user activity and detect suspicious behavior, such as unauthorized access or data exfiltration. Properly analyzing and managing session data can help organizations improve their overall security posture and mitigate the risk of cyber attacks.
Session Data In Security Logs
Session data is an essential component of security logs. It provides a detailed record of user activity involving login and logout times, commands executed, and files accessed. Security logs capture and store this information in a centralized location, allowing security teams to review and analyze the data for signs of malicious activity. Session data can also be used to monitor user behavior and detect anomalies. For example, if a client typically logs in during regular business hours but suddenly logs in at 2 am, it could be a sign of unauthorized access. Similarly, if a user accesses files outside of their normal work responsibilities, it could indicate data exfiltration.
Analyzing session data can help organizations identify and investigate security incidents quickly. It can also help them improve their security posture by identifying areas where additional controls may be needed. For example, if a user repeatedly fails to enter the correct password, it could be a sign that the organization needs to implement stronger authentication measures.
Session data is a critical component of security logs. Properly analyzing and managing this data can help organizations improve their overall security posture and mitigate the risk of cyber attacks.
Interpretation Of Session Data In Security Logs
Interpreting session data in security logs is crucial for identifying potential security threats and improving an organization’s overall security posture. Security professionals can gain insights into user behavior, network activity, and system performance by analyzing session data. One important aspect of interpreting session data is identifying anomalies. Anomalies may indicate potential security threats, such as unauthorized access or malware infections. For example, if a user logs in from an unusual location or time, it could be a sign of a compromised account.
Another important aspect of interpreting session data is identifying trends. Trends can help organizations identify areas where additional controls may be needed. For example, if there is an unexpected increase in failed login attempts, it could be a sign that the organization needs to implement stronger authentication measures.
In addition to identifying anomalies and trends, interpreting session data can help organizations improve their incident response capabilities. Security professionals can identify patterns and develop more effective incident response plans by analyzing session data from past incidents.
Best Practices For Interpreting Session Data
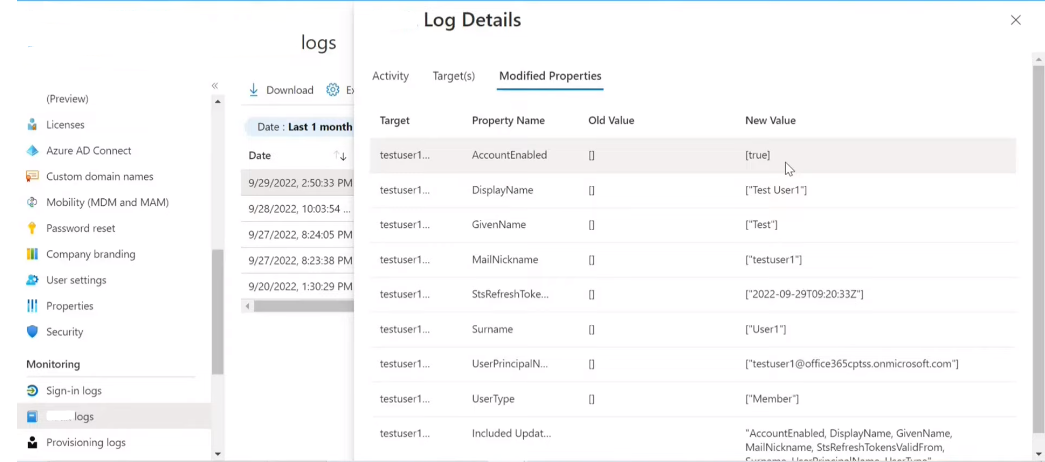
Here are some best practices for interpreting session data in security logs:
1. Understand the context: Before analyzing session data, it’s important to understand the context in which it was generated clearly. This includes information about the systems, applications, and users involved in the sessions.
2. Identify anomalies: Look for anomalies in the session data that may indicate potential security threats. This could include unusual login times, multiple failed attempts, or unusual data transfers.
3. Correlate data: Correlate session data with other security events to identify potential patterns or relationships. For example, if a user’s account is compromised, look for session data that may indicate unauthorized access.
4. Prioritize alerts: Not all security alerts are created equal. Prioritize alerts based on the severity of the potential threat and the impact it could have on your organization.
5. Continuously monitor: Session data should be continuously monitored to identify new threats and vulnerabilities. This includes monitoring for changes in user behavior, new attack vectors, and emerging threats.
By following these practices, organizations can effectively interpret session data in their security logs and improve their overall security posture.
Tools For Analyzing Session Data In Security Logs
There are several tools available for analyzing session data in security logs. Some of the popular ones include:
1. Splunk: Splunk is a powerful log analysis tool that can collect, index, and analyze data from various sources, including security logs. It provides real-time monitoring, alerting, and reporting capabilities to help organizations quickly detect and respond to security incidents.
2. ELK Stack: ELK Stack combines three open-source tools – Elastic Search, Logstash, and Kibana. Elastic search is a search and analytics engine, Logstash is a log processing pipeline, and Kibana is a visualization tool. Together, they provide a powerful platform for log analysis and security monitoring.
3. Graylog: Graylog is another open-source log management platform that collects, indexes, and analyzes logs from various sources, including security logs. It provides real-time alerting, dashboards, and search capabilities to help organizations recognize and respond to security incidents.
4. IBM QRadar: IBM QRadar is a security data and event management (SIEM) solution that can collect, analyze, and relate log data from various sources, including security logs. It provides real-time monitoring, advanced analytics, and incident response capabilities to help organizations detect and respond to security threats.
5. LogRhythm: LogRhythm is another SIEM solution that collects, analyzes, and correlates log data from various sources, including security logs. It provides real-time monitoring, threat intelligence, and automated response capabilities to help organizations detect and respond to security incidents.
Comparison Of Popular Session Data Analysis Tools
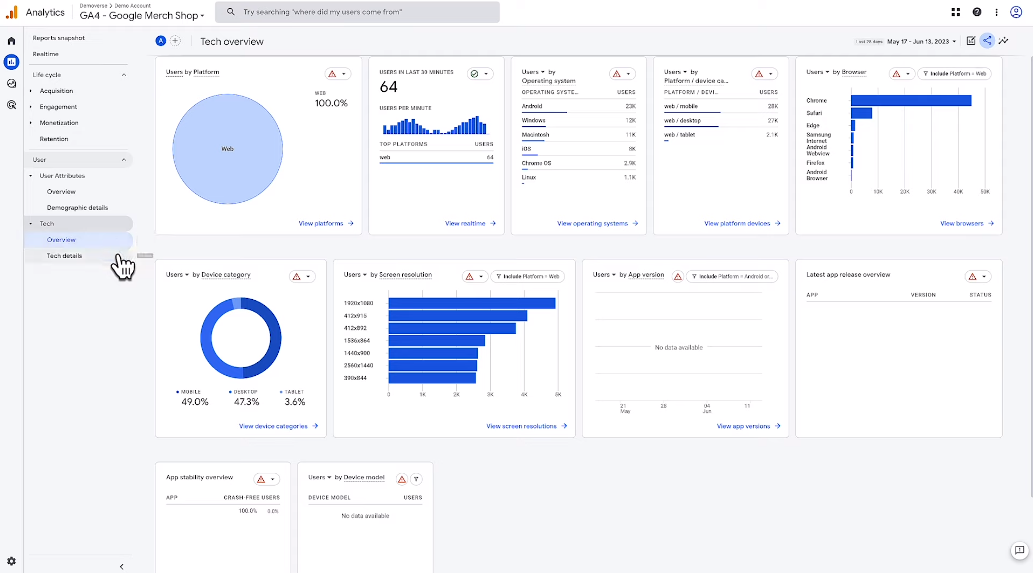
Here’s a comparison of some popular session data analysis tools:
1. Google Analytics: Google Analytics is a free web analytics service that offers insights into website traffic and user behavior. It offers a variety of reports and metrics to help businesses understand how users interact with their websites.
2. Mixpanel: Mixpanel is a paid analytics service that provides real-time data on user behavior. It offers advanced analytics and segmentation tools that allow businesses to create targeted campaigns and track user engagement.
3. Amplitude: Amplitude is another paid analytics service specializing in mobile app analytics. It provides real-time data on user behavior and offers advanced analytics and segmentation tools to help businesses optimize their mobile apps.
4. Heap: Heap is a paid analytics service that provides insights into client behavior on websites and mobile apps. It automatically captures all user interactions and provides advanced analytics and segmentation tools to help businesses understand how users engage with their products.
5. Kissmetrics: Kissmetrics is a paid analytics service that focuses on user engagement and retention. It provides insights into user behavior and offers advanced analytics and segmentation tools to help businesses optimize their marketing campaigns and improve user retention.
Conclusion
This article discussed the importance of protecting user privacy in data collection practices. We highlighted six key points organizations should consider when collecting and handling user data. These include minimizing data collection, obtaining user consent, implementing strong security measures, regularly reviewing and updating privacy policies, deleting session data when no longer needed, and being transparent with users about data collection practices. By following these guidelines, organizations can build trust with their users and reduce the risk of data breaches.
Session data is important in security logs because it records user activity during a specific session. This information can identify potential security threats or breaches and help security teams quickly respond to and mitigate any issues. Session data can include details such as the user’s IP address, the time and date of their activity, the pages or resources accessed, and any errors or warnings encountered. By reviewing session data, security teams can identify patterns of suspicious activity, investigate incidents, and take steps to prevent future attacks. Additionally, session data can be used to monitor compliance with security policies and regulations and serve as evidence in legal proceedings.
Frequently Asked Questions (FAQs)
What Is Session Data In Security Logs?
Session data in security logs refers to the information recorded about a user’s activity during a particular session on a computer or network. This can include details such as the user’s login time, the applications they accessed, the files they opened or modified, and any network connections they made. By analyzing this data, security teams can identify potential threats or anomalies that may indicate a security breach or attack.
Why Is Session Data Important In Security?
Session data is important in security because it provides a detailed record of a user’s activity on a computer or network. This information can be used to identify security threats or suspicious behavior, such as unauthorized access or data exfiltration. By analyzing session data, security teams can detect and respond to security incidents promptly, minimizing the impact of a potential breach. Additionally, session data can be used to investigate security incidents after the fact, enabling organizations to identify the incident’s root cause and take appropriate measures to prevent similar incidents. Session data typically includes login and logout times, IP addresses, user IDs, and the specific activities performed during the session. This data can be collected and analyzed using specialized software tools like security information and event management (SIEM) systems.
How Is Session Data Recorded In Security Logs?
Session data is typically recorded in security logs using specialized software tools, such as security information and event management (SIEM) systems. These tools are designed to collect and analyze data from various sources involving network devices, servers, and applications. When a user logs into a system or application, the SIEM system will record information such as the user’s login and logout times, IP address, user ID, and the specific activities performed during the session. This data is stored in a centralized database for further analysis and link with other security events. SIEM systems also use algorithms and rules to detect potential security threats and irregularities in user behavior. For example, if a user logs in from an unusual location or time, this may trigger an alert that could indicate a potential security breach. SIEM systems can also be configured to automatically respond to security incidents, such as blocking a user’s access or alerting security personnel.
What Are The Challenges Of Using Session Data For Security Purposes?
There are several challenges associated with using session data for security purposes. One of the major challenges is the sheer volume of data that needs to be processed and analyzed. Session data can include a wide range of information, such as user activity, network traffic, and system logs, making it difficult to identify and distinguish relevant security events from normal user behavior. Another challenge is the complexity of analyzing session data. Security analysts need to be able to identify patterns and irregularities in the data, which can require advanced analytical skills and specialized tools. Additionally, session data can be difficult to interpret, particularly if it is incomplete or contains errors.
What Are The Practices For Managing And Analyzing Session Data In Security Logs?
Several best practices exist for managing and analyzing session data in security logs. These include:
1. Collecting only the necessary data: Organizations should only collect session data for security purposes. This can help reduce the amount of data that needs to be stored and analyzed, which can help simplify the process.
2. Storing data securely: Session data should be stored securely to prevent unauthorized access. This can involve encryption, access controls, and other security measures to protect the data.
3. Analyzing data in real-time: Session data should be analyzed in real-time to identify potential security threats as they occur. This can help organizations respond quickly to security incidents and prevent them from escalating.
4. Regularly reviewing logs: Organizations should review their security logs regularly to identify trends and patterns that could indicate potential security issues. This can help organizations proactively address security threats before they become major problems.
5. Training security personnel: Security personnel should be trained to handle session data appropriately and to follow best practices for managing and analyzing security logs. This can help ensure that the data is used effectively for security purposes while also protecting users’ privacy.
What Are The Legal And Privacy Considerations Related To Session Data In Security Logs?
Organizations should know several legal and privacy considerations related to session data in security logs. These include:
1. Data protection laws: Depending on the jurisdiction, there may be data protection laws that regulate the collection, use, and storage of session data. Organizations should ensure that they comply with these laws to avoid legal liability.
2. Personally identifiable information (PII): Session data may contain PII, such as IP addresses, login credentials, and browsing history. Organizations should take appropriate measures to protect this data and ensure it is not misused or disclosed to unauthorized parties.
3. Data retention policies: Organizations should have clear policies for how long session data will be retained and when it will be deleted. This can help ensure that data is not kept for longer than necessary and reduces the risk of data breaches.
4. Access controls: Access to session data should be restricted to authorized personnel only. This can help prevent unauthorized access and misuse of the data.
5. Transparency and disclosure: Organizations should be transparent about their collection and use of session data and provide users with clear information about their data use. Organizations may sometimes be required to disclose their data collection practices to users or regulators.
