Introduction
A Brief Explanation Of Data Encryption And Its Importance
Data encryption is the process of converting plain text into code that can only be read by authorized parties. This technology is essential for safeguarding sensitive information, such as banking details, personal identification numbers, and confidential business data. With hackers becoming more sophisticated in their methods of accessing private information, it’s crucial to implement strong encryption measures to protect ourselves from cyber threats.
Overview of the Concept of Dual Stat Data Encryption
Dual Stat Data Encryption is a security technique used to protect sensitive information by encrypting data using two separate keys. In this approach, the encryption and decryption processes are separated into two parts: statistical reconciliation and cryptographic encryption. The first step of statistical reconciliation involves analyzing the plaintext message and generating statistics that will be used in the encryption process. These statistics are then run through a mathematical algorithm to generate a key that will be used for cryptographic encryption.
The second part of Dual Stat Data Encryption involves actually encrypting the data using the generated key from statistical reconciliation. This ensures that even if one key is compromised, it cannot decrypt sensitive information without also having access to the other key generated through statistical analysis.
The Basics of Data Encryption
Definition Of Data Encryption
Encryption is a process of converting plain text data into an encoded format that can only be accessed by authorized individuals. It involves the use of mathematical algorithms to scramble the data into meaningless characters, making it unreadable by anyone without proper decryption keys.
Different Types Of Encryption
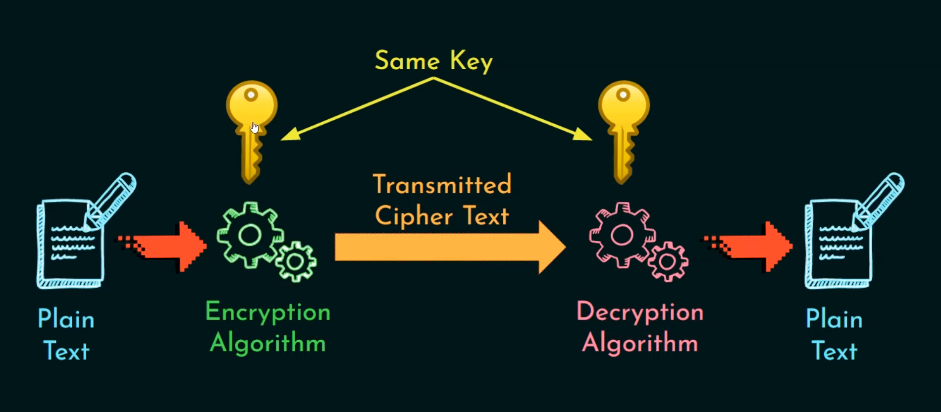
Symmetric Key Encryption: As the name suggests, this type of encryption uses a single secret key that is shared between the sender and receiver to encrypt and decrypt messages. Both parties need access to this same secret key in order to communicate securely.
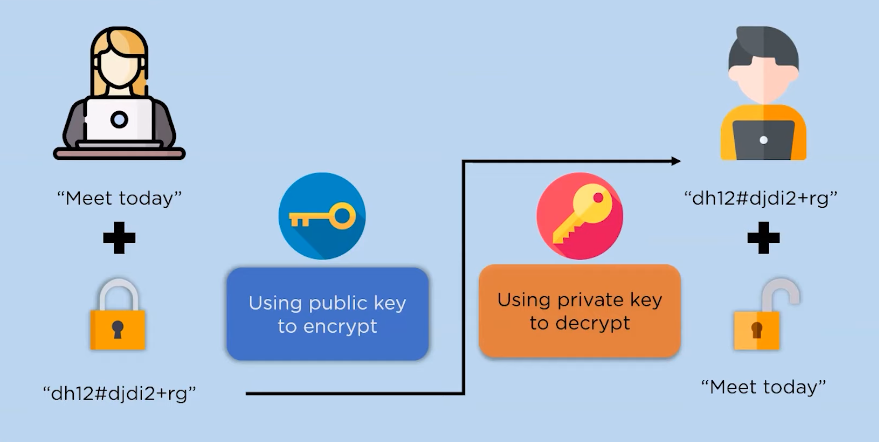
Asymmetric key encryption: Asymmetric key encryption, also known as public-key cryptography, is a data encryption method that uses two different keys to encrypt and decrypt data. One key is a public key, which can be freely shared with anyone who wants to send encrypted messages. The other key is the private key, which should be kept secret and is used by the recipient to decrypt messages sent using the public key.
Hashing Encryption creates fixed-length outputs or hashes from inputs of any size or length. This means that even if you have access to the output value (the hash), you cannot determine what input produced it unless you have knowledge of its hashing function and parameters.
Advantages And Disadvantages Of Data Encryption
One of the main advantages of data encryption is that it makes it much more difficult for hackers to steal or manipulate data. This is especially important in industries like finance and healthcare, where even a single data breach can have serious consequences. Additionally, encrypted data can be safely stored and transmitted across public networks without fear of interception.
However, there are also some disadvantages to consider when using data encryption. Encrypting and decrypting large amounts of data can be time-consuming and resource-intensive. This means that implementing strong encryption measures may slow down system performance or require additional processing power. Additionally, there is always the risk of losing access to encrypted data if the encryption key is lost or stolen.
Common Encryption Algorithms
Advanced Encryption Standard (AES). It was first introduced in 2001 and has since become a standard for encryption. AES uses a block cipher, which means it divides data into blocks and encrypts each one separately. Each block is encrypted using a round function that transforms the plaintext into ciphertext. The number of rounds depends on the key size, with more rounds being added for larger keys.
Rivest-Shamir-Adleman. RSA (Rivest-Shamir-Adleman) is widely used for secure communication over the Internet. Unlike AES, RSA uses asymmetric cryptography, meaning that it uses two keys: one for encryption and another for decryption. This ensures that only authorized parties can access sensitive information.
Blowfish. Blowfish – an algorithm known for its speed and efficiency in encrypting large amounts of data. With its variable key length of up to 448 bits, Blowfish offers strong security against brute-force attacks.
Understanding Dual Stat Data Encryption
Definition of Dual Stat Data Encryption
Dual Stat Data Encryption is a security mechanism that involves two distinct encryption processes, namely statistical and cryptographic. The statistical encryption process employs mathematical algorithms to generate random numbers which are used to mask the original data. This makes it impossible for hackers to decipher the data even if they acquire access to the encrypted files.
The cryptographic encryption process, on the other hand, uses a key-based system where data is scrambled and can only be accessed by individuals with the corresponding key. This ensures that even if an unauthorized person gains access to the encrypted data, they will not be able to read or manipulate it.
How It Differs From Traditional Encryption Methods?
Unlike traditional encryption, which relies on the use of a single key to encrypt and decrypt data, dual stat encryption uses two keys for this purpose. These keys are generated separately and are not related to each other in any way.
The first key in dual stat data encryption is used to encrypt the plain text of the message. The second key is then used to encrypt the first encrypted message further. This process creates an additional layer of security, making it much more difficult for hackers or attackers to gain access to sensitive information.
Advantages of using Dual Stat Data Encryption
One major advantage of using Dual Stat Data Encryption is that it ensures regulatory compliance. Various governmental and industry regulations require businesses to protect sensitive information, such as personally identifiable information (PII) and financial records. Dual Stat encryption helps companies meet these requirements by significantly reducing the risk of breaches.
Another benefit of using Dual Stat encryption is that it provides peace of mind for both businesses and their customers. When clients know that their information is being securely protected, they are more likely to trust a business with their confidential data in the future. Additionally, businesses can rest assured knowing that they have taken all necessary steps to safeguard their valuable assets from cyber-attacks and other security threats.
How Dual Stat Data Encryption Works?
Explanation Of The Mathematical Concepts Behind Dual Stat Data Encryption
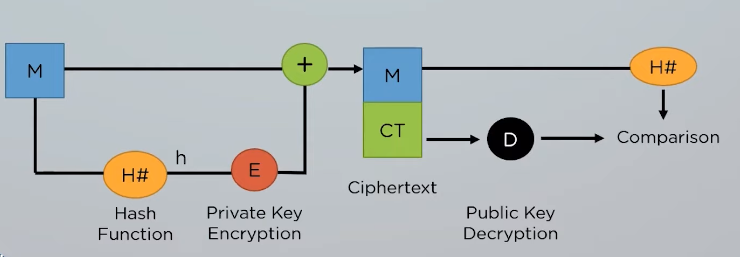
Dual Stat Data Encryption is a unique method of encrypting data that utilizes mathematical concepts such as prime numbers, modular arithmetic, and the Chinese Remainder Theorem. At its core, Dual Stat Data Encryption is based on the idea of splitting data into two parts or “states” and then encrypting each state separately using different encryption methods.
The first step in Dual Stat Data Encryption involves selecting two prime numbers, p and q, and computing their product n=pq. This value n serves as the modulus for both encryption states. Next, two encryption keys are generated – one public key for encrypting messages and one private key for decrypting them. The public key consists of an exponent e that is relatively prime to (p-1)(q-1), while the private key consists of an exponent d that satisfies ed=1 mod (p-1)(q-1).
Steps Involved In Encrypting And Decrypting Data Using Dual Stat Data Encryption
The first step in encrypting data using Dual Stat Data Encryption is to generate a pair of public and private keys. This can be done using software tools such as OpenSSL or GnuPG. Once the keys have been generated, the sender can encrypt their message using the recipient’s public key.
To decrypt this message, the recipient would need to use their own private key, which is kept secret from everyone else. This ensures that only authorized individuals are able to access sensitive information.
Applications of Dual Stat Data Encryption
Use Cases Of Dual Stat Data Encryption
There are several use cases for Dual Stat Data Encryption. One such use case is in online banking and financial transactions where sensitive information such as account numbers, passwords, and transaction history needs to be protected from hackers and cybercriminals. By using Dual Stat Data Encryption, banks can ensure that customer data remains secure.
Another use case for Dual Stat Data Encryption is in healthcare. Patient medical records contain highly sensitive information that must be protected under HIPAA regulations. Using this form of encryption can help healthcare providers keep patient data confidential while allowing authorized personnel to access it when necessary.
Industries And Sectors That Can Benefit From Dual Stat Data Encryption
Industries such as healthcare, insurance, and retail can benefit significantly from Dual Stat Data Encryption. In healthcare, patient records contain sensitive information such as medical history, diagnosis, and treatment plans. These records must be kept confidential from unauthorized access or cyber-attacks by hackers who might want to get hold of these details.
Insurance companies also have vast amounts of customer data stored digitally that need to be secured with the best encryption techniques available. Retail businesses often store customers’ personal details such as credit card numbers or addresses on their servers; this type of information is highly sought after by cybercriminals.
Limitations and Challenges of Dual Stat Data Encryption
Challenges in Implementing Dual Stat Data Encryption
One of the significant challenges is maintaining data privacy and security while implementing it. With increasing data breaches, organizations are becoming more cautious about their data privacy practices; however, implementing dual stat encryption requires additional measures such as key management and secure storage.
Another challenge in implementing Dual Stat Data Encryption is its compatibility with existing systems. Organizations already have several tools and software that encrypt and decrypt their data using various algorithms. Integrating dual stat encryption into these systems can be complicated, time-consuming, and expensive due to differences in the encryption protocols used.
Limitations of Dual Stat Data Encryption
The potential risk of key exposure. If an attacker gains access to both keys (static and dynamic), they can decrypt the protected data, making it vulnerable to theft or misuse.
The complexity of implementation. Dual Stat Data Encryption requires a high level of technical expertise and resources for setup and maintenance. This may make it difficult for small organizations with limited budgets to adopt this technology.
Risks Associated with Dual Stat Data Encryption
Possible Risks And Threats Associated With Dual Stat Data Encryption
Dual Stat Data Encryption requires two keys – one for encryption and the other for decryption. If these keys fall into the wrong hands, they can compromise the security of the encrypted data.
Another risk associated with Dual Stat Data Encryption is that it may have a negative impact on system performance due to the increased processing time required for encryption and decryption. This can result in slower response times or even system crashes if not properly optimized. In addition, there is also a possibility of compatibility issues with different software applications or operating systems.
Conclusion
Dual stat data encryption is a powerful tool that can help organizations protect sensitive information from unauthorized access. By using two different types of encryption keys, this technique makes it much more difficult for hackers to breach security systems and access confidential data. In addition to its effectiveness, dual stat data encryption is also relatively easy to implement and manage. With the right tools and expertise, organizations of all sizes should be able to take advantage of this technology and keep their most important information safe.
FAQs
What Is The Difference Between Dual Stat Data Encryption And Traditional Encryption Methods?
Traditional encryption involves using one key to encrypt and decrypt messages, whereas Dual Stat Data Encryption uses two keys instead of one. This double layer of protection provides an extra level of security that is not found in traditional encryption methods.
Is Dual Stat Data Encryption More Secure Than Other Encryption Methods?
Dual Stat Data Encryption can offer superior security benefits over traditional encryption techniques when implemented correctly with proper key management protocols in place. As technology continues to evolve and cyber threats become more sophisticated, businesses must consider adopting advanced security measures like Dual Stat Data Encryption to protect their sensitive information from potential breaches.
What Are The Limitations Of Dual Stat Data Encryption?
One of the main limitations of Dual Stat Data Encryption is its complexity. The process of encrypting data using two different algorithms can be confusing and difficult to implement for those who are not familiar with cryptography. Moreover, maintaining the system’s integrity requires specialized skills that may not be readily available in all organizations.
Another limitation is the potential for performance issues due to the increased processing power required for dual encryption. Encrypting data twice can put a strain on systems, particularly older or less powerful ones, which could cause delays or even crashes during high-volume transactions.
How Is Dual Stat Data Encryption Implemented In Real-World Scenarios?
In real-world scenarios, there are several ways this encryption method can be implemented. One common implementation is in the healthcare industry, where patient information needs to be protected at all times.
In healthcare, dual stat data encryption is used to protect electronic health records (EHRs) from unauthorized access by hackers or other malicious actors. The first encryption algorithm encrypts the entire EHR file while the second algorithm encrypts only specific fields such as the patient’s name, social security number, and medical history. This helps ensure that even if attackers gain access to some parts of the EHR file, they will not be able to read or use sensitive information for malicious purposes.
Another example where dual stat data encryption can be implemented is in financial institutions such as banks and credit card companies. These organizations process large amounts of sensitive financial data every day which requires high levels of security measures in place.
Can Dual Stat Data Encryption Be Hacked Or Breached?
No security system is foolproof. Dual Stat Data Encryption can also be hacked or breached if the attacker finds vulnerabilities in either of the algorithms used. If any of these algorithms have a flaw or weakness, cybercriminals can exploit it to gain access to confidential information. Moreover, if passwords used for encrypting data are weak or compromised, hackers can use brute-force attacks to crack them and access your sensitive files.
