AES Encryption and its Role in Securing Information
AES (Advanced Encryption Standard) is a widely used encryption algorithm that is used to secure data transmission and storage. It is a symmetric-key encryption algorithm, which means that the same key is used for both encryption and decryption of the data.AES encryption is used in various applications such as online banking, e-commerce, and secure communication systems. It provides a high level of security by using a complex encryption process that makes it difficult for unauthorized users to access the information.
Intro to AES Encryption
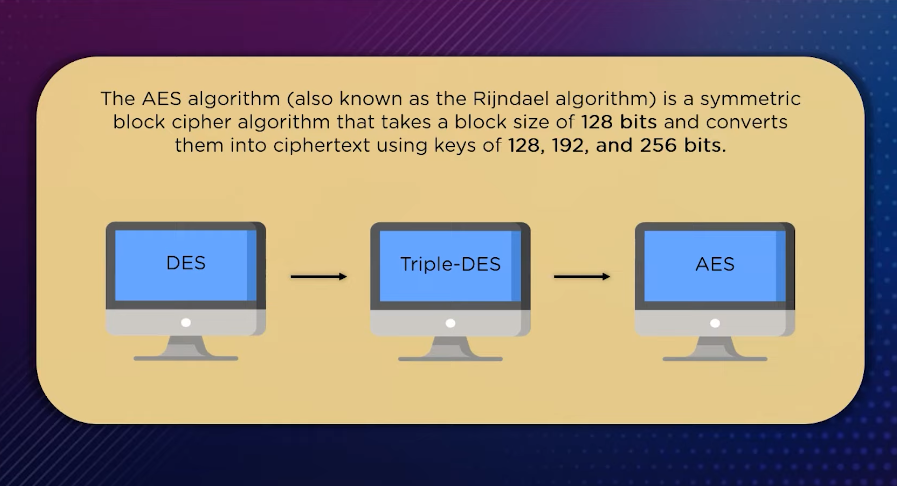
AES encryption is a widely used encryption algorithm that is used to secure data transmission and storage. It is a symmetric-key encryption algorithm, which means that the same key is used for both encryption and decryption of the data. AES encryption provides a high level of security by using a complex encryption process that makes it difficult for unauthorized users to access the information. It is used in various applications such as online banking, e-commerce, and secure communication systems.
Background and Development of AES
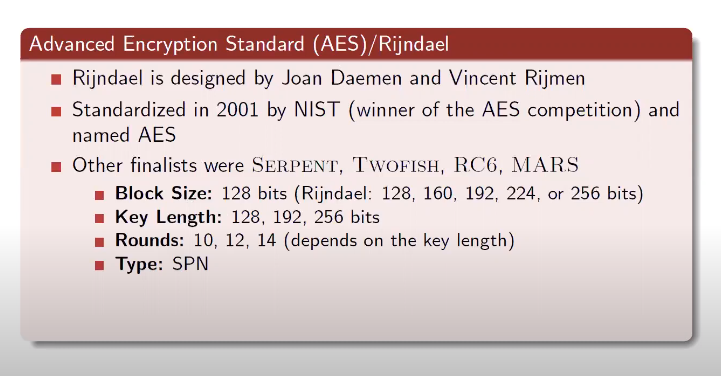
The development of AES began in the late 1990s when the National Institute of Standards and Technology (NIST) announced a competition to find a new encryption standard to replace the ageing Data Encryption Standard (DES). The competition attracted submissions from around the world, and after several rounds of evaluation, the Rijndael algorithm, developed by Belgian cryptographers Joan Daemen and Vincent Rijmen, was selected as the winner in 2001.
Key Features and Strengths of AES
AES, or Advanced Encryption Standard, is a symmetric encryption algorithm that uses a block cypher to encrypt and decrypt data. It has several key features and strengths that make it a popular choice for securing sensitive information:
1. Security: AES is considered to be one of the most secure encryption algorithms available today. It uses a 128-bit block size and supports key sizes of 128, 192, or 256 bits, making it virtually impossible to crack with brute-force attacks.
2. Speed: AES is designed to be fast and efficient, even on older hardware. It has a relatively low computational overhead, which means it can encrypt and decrypt data quickly and without consuming too much processing power.
3. Flexibility: AES can be used in a variety of applications and environments, from securing data on personal computers to protecting sensitive information on government networks. It is also compatible with a wide range of operating systems and programming languages.
4. Standardization: AES is a widely recognized and accepted encryption standard, which means it is supported by a large number of software and hardware vendors. This makes it easier to integrate into existing systems and applications.
Overall, AES is a powerful and versatile encryption algorithm that provides strong security and efficient performance.
The Encryption Process
The encryption process using AES involves several steps:
1. Key Generation: A secret key is generated by encryption software or hardware. This key is used to encrypt and decrypt data.
2. Substitution: The plaintext is divided into blocks of fixed size and each block is substituted with a corresponding ciphertext block using a substitution table.
3. Permutation: The order of the blocks is changed using a permutation table.
AES and Data Encryption
AES (Advanced Encryption Standard) is a widely used encryption algorithm that provides strong security for data encryption. It is used in various applications such as online banking, secure email communication, and data storage. The encryption process using AES ensures that data is protected by converting it into an unreadable format that can only be decrypted using a secret key. The key generation step ensures that only authorized parties can access the encrypted data.
Creating Digital Signatures
Creating digital signatures is an important aspect of secure communication and data transfer. Digital signatures use asymmetric cryptography to ensure the authenticity, integrity, and non-repudiation of digital documents. To create a digital signature, the sender uses their private key to encrypt a hash of the message. The encrypted hash is then attached to the message and sent to the recipient. The recipient can then use the sender’s public key to decrypt the hash and verify its authenticity.
Role of AES in Generating Secure Digital Signatures
AES (Advanced Encryption Standard) is not directly involved in generating digital signatures. Digital signatures use asymmetric cryptography, while AES is a symmetric encryption algorithm used for encrypting and decrypting data. However, AES can be used in combination with digital signatures to provide additional security. For example, before creating a digital signature, the message can be encrypted using AES with a randomly generated key. The encrypted message is then signed using the sender’s private key and sent to the recipient.
Significance of Digital Signatures
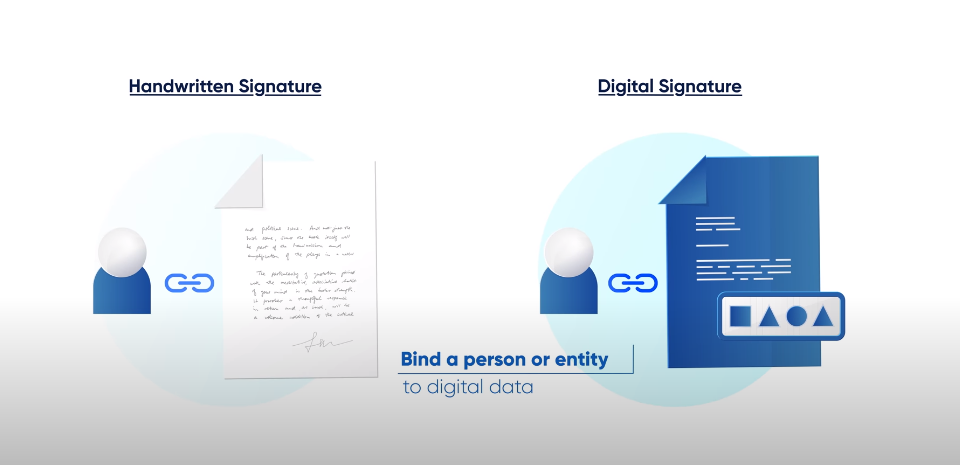
Digital signatures are significant because they provide a way to verify the authenticity and integrity of electronic documents and messages. They ensure that the sender of the document or message is who they claim to be and that the content has not been altered in transit. This is important for a variety of reasons, such as ensuring the validity of legal contracts, financial transactions, and government documents. Digital signatures also provide non-repudiation, meaning that the sender cannot later deny having sent the message or document.
Authenticating the integrity and origin of data
Digital signatures play a crucial role in authenticating the integrity and origin of data. They use encryption technology to ensure that the data has not been tampered with or altered in any way during transmission. This is particularly important in situations where data security and authenticity are critical, such as financial transactions, legal documents, and government records. Digital signatures work by using a public key infrastructure (PKI) to verify the identity of the sender and ensure that the message or document has not been altered in transit.
Secret Key Exchange
Secret key exchange is a method of securely sharing a secret key between two parties. This key can then be used to encrypt and decrypt messages between the parties. The secret key is typically a long string of random characters that are known only to the parties involved in the exchange. There are several methods of secret key exchange, including the Diffie-Hellman key exchange and the RSA key exchange.
Security Strength of AES
The Advanced Encryption Standard (AES) is a widely used symmetric encryption algorithm that is considered to be highly secure. The security strength of AES is based on the length of the key used for encryption. AES supports key lengths of 128, 192, and 256 bits, with longer keys providing stronger security. AES has been extensively analyzed by security experts and is resistant to various types of attacks, including brute force attacks.
AES vs. Other Encryption Algorithms
Compared to other encryption algorithms, AES is considered to be more secure and efficient. For example, the older Data Encryption Standard (DES) uses a 56-bit key, which is not considered to be secure enough for modern applications. Another popular algorithm, Triple DES (3DES), uses multiple iterations of DES to increase security, but it is slower and less efficient than AES. Overall, AES is a reliable and widely used encryption algorithm that provides strong security for sensitive data.
A Comparative Analysis of AES, DES, and RSA
AES, DES, and RSA are all encryption algorithms that are used to secure data. However, they differ in terms of their security, efficiency, and key length.AES (Advanced Encryption Standard) is a symmetric encryption algorithm that uses a block cypher and a variable-length key. It is widely used and considered to be highly secure and efficient. AES uses a key length of 128, 192, or 256 bits, which makes it more secure than DES.
DES (Data Encryption Standard) is an older symmetric encryption algorithm that uses a block cypher and a fixed-length key of 56 bits. It is no longer considered to be secure enough for modern applications due to its short key length.
RSA (Rivest–Shamir–Adleman) is an asymmetric encryption algorithm that uses a public key and a private key. It is widely used for secure communication and digital signatures. RSA uses a key length of 1024, 2048, or 4096 bits, which makes it more secure than DES but less efficient than AES.
In summary, AES is considered to be the most secure and efficient encryption algorithm, followed by RSA. DES is no longer considered to be secure enough for modern applications.
AES Implementation and Applications
AES (Advanced Encryption Standard) is a symmetric encryption algorithm that uses a block cypher to encrypt and decrypt data. It is widely used for secure communication, data storage, and digital signatures. AES uses a key length of 128, 192, or 256 bits, which makes it more secure and efficient than DES and RSA. The implementation of AES involves the selection of a key and the use of a block cypher to encrypt and decrypt data.
Implementing AES in Software And Hardware Systems
Implementing AES in software and hardware systems requires careful consideration of various factors such as performance, security, and flexibility. In software systems, AES can be implemented using various programming languages such as C, C++, Java, Python, and others. Software implementations of AES can be optimized for performance by using techniques such as loop unrolling, pipelining, and parallel processing.
Common Uses of AES in Various Industries
Before discussing the common uses of AES in various industries, it is important to understand what AES is. AES stands for Advanced Encryption Standard, which is a symmetric encryption algorithm used to protect data confidentiality. It is widely used in various industries to secure sensitive data. One industry that commonly uses AES is the financial sector. Financial institutions use AES to protect their customer’s sensitive financial information such as bank account numbers, credit card information, and personal identification numbers (PINs).
Advancements and Ongoing Research in AES Technology
AES technology has seen significant advancements and ongoing research to enhance its security and efficiency. One such advancement is the development of AES-GCM, which combines the AES algorithm with Galois/Counter Mode (GCM) to provide authenticated encryption and data integrity. This ensures that not only is the data encrypted, but it also remains unaltered during transmission. Another ongoing research area is the development of quantum-resistant AES algorithms.
Conclusion
In conclusion, AES technology continues to evolve and improve, with advancements such as AES-GCM and ongoing research in quantum-resistant algorithms. These developments aim to enhance the security and efficiency of AES, making it a reliable encryption method for various applications.
Frequently Asked Questions (FAQs)
How does AES create digital signatures?

AES is not used to create digital signatures. AES is a symmetric encryption algorithm that is used to encrypt and decrypt data. Digital signatures, on the other hand, are created using asymmetric encryption algorithms like RSA or Elliptic Curve Cryptography (ECC). Digital signatures are used to ensure the authenticity and integrity of digital documents or messages. They work by creating a unique digital “signature” that can only be created by the original signer and can be verified by anyone who has access to specified personnel.
What are secret key exchange protocols, and why are they important?
Secret key exchange protocols are methods used to securely exchange secret keys between two parties over an insecure network. These protocols are important because they allow two parties to establish a shared secret key that can be used to encrypt and decrypt messages, ensuring the confidentiality and integrity of the communication. Without a secure key exchange protocol, it would be difficult to establish a secure communication channel between two parties, as an attacker could intercept and modify the communication.
Is AES the only encryption algorithm used for key exchange?
No, AES is not the only encryption algorithm used for key exchange. Several other encryption algorithms are used for key exchange, such as Diffie-Hellman (DH), RSA, and Elliptic Curve Cryptography (ECC). Each of these algorithms has its strengths and weaknesses, and the choice of algorithm depends on the specific requirements of the communication and the level of security needed.
How long should AES keys be to ensure maximum security?
The recommended key length for AES encryption to ensure maximum security is 256 bits. However, a key length of 128 bits is also considered secure for most applications. The longer the key, the more secure the encryption, but longer keys also require more processing power and can slow down the encryption and decryption process.
