Introduction
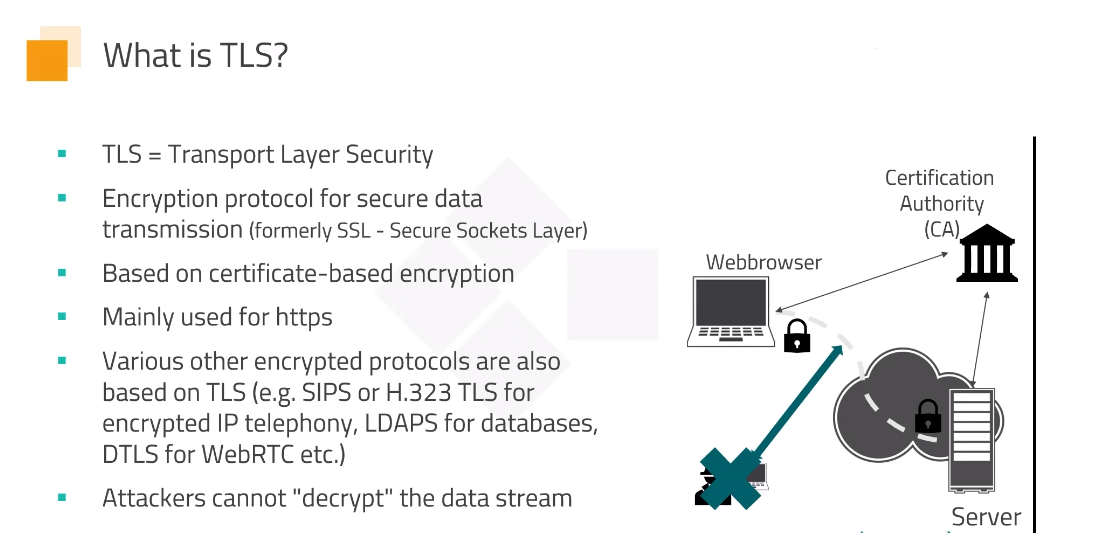
Encryption converts plain text into a coded message to prevent unauthorized access during transmission or storage. In web data transfer, encryption is necessary to protect sensitive information like passwords, credit card details, and personal information from being intercepted and read by hackers or other malicious entities. The standard for transferring encrypted data on the web is known as the Transport Layer Security (TLS) protocol, which is a successor to the Secure Sockets Layer (SSL) protocol. TLS ensures that data is securely transmitted over the internet by providing encryption, authentication, and integrity checks.
However, not all TLS implementations are created equal. In this article, we will explore the several elements of the TLS protocol and how they contribute to secure web data transfer. We will also discuss common vulnerabilities and best practices for implementing TLS to ensure maximum security for web users.
Understanding The Standard For Web Data Transfer
This article will discuss the importance of Transport Layer Security (TLS) in securing web data transfer. TLS is a cryptographic protocol that provides encryption, authentication, and integrity checks to ensure the confidentiality and integrity of data exchanged between web servers and clients. Encryption is the method of encoding data so that only authorized parties can access it. TLS uses asymmetric encryption to create a secure connection between the client and server. Through the TLS handshake, the client and server exchange public keys, which are used to encrypt and decrypt data transmitted between them.
Authentication is the method of verifying the identity of the communicating parties. TLS uses digital certificates to authenticate web servers. These certificates are supplied by trusted third-party Certificate Authorities (CAs) and contain information such as the server’s public key and domain name.
Integrity checks ensure that data transmitted between the client and server has not been altered during transmission. TLS uses message authentication codes (MACs) to provide integrity checks. MACs are generated using a secret key shared between the client and server and included in the transmitted data.
Definition And Explanation Of The HTTPS Protocol

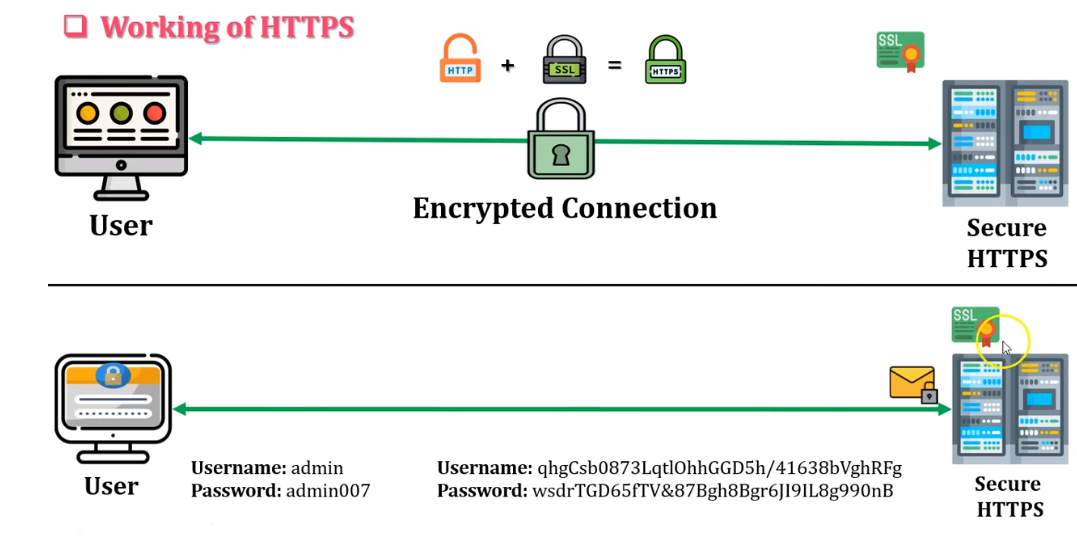
HTTPS stands for Hypertext Transfer Protocol Secure. It is a protocol to encrypt and secure data transmitted between web browsers and websites. When users visit an HTTPS website, their browser establishes a secure connection using a digital certificate with the website’s server. This certificate verifies the identity of the website. It encrypts the data transmitted between the two parties, making it tougher for hackers to intercept and steal sensitive information like login credentials, credit card numbers, and other personal data. HTTPS is commonly used for online banking, e-commerce, and other websites that require secure transmission of sensitive data.
Comparison Of HTTPS Vs. HTTP And Their Differences In The Data Transfer Security
HTTPS and HTTP are protocols used for transmitting data over the internet, but they differ in security. HTTP (Hypertext Transfer Protocol) is the typical protocol for transmitting data over the internet. It is a simple and fast protocol that does not encrypt or authenticate the transmitted data. Any data transmitted over HTTP can be intercepted and read by anybody with access to the network, making it vulnerable to hacking and other security threats.
HTTPS (Hypertext Transfer Protocol Secure) is a secure version of HTTP that uses SSL/TLS encryption to protect the transmitted data. SSL/TLS encryption creates a protected connection between the client and the server, encrypting the data transmitted between the parties. This reflects it much more difficult for hackers to intercept and steal sensitive information like login credentials, credit card numbers, and any additional data.
HTTPS is more secure than HTTP as it provides encryption and authentication of transmitted data, making it tough for hackers to intercept and steal sensitive information. It is commonly used for online banking, e-commerce, and other websites requiring secure sensitive data transmission.
Encryption Methods And Protocols
Encryption methods and protocols are essential for ensuring secure communication over the internet. There are several encryption methods and protocols available, including:
1. SSL (Secure Sockets Layer): SSL was the predecessor to HTTPS and is still used today. It provides encryption and authentication of data transmitted between web servers and clients.
2. TLS (Transport Layer Security): TLS is the successor to SSL and is now the standard encryption protocol used for HTTPS. It provides encryption and authentication of data transmitted between web servers and clients.
3. AES (Advanced Encryption Standard): AES is a symmetric encryption method widely used to encrypt data. It is considered one of the safest encryption methods available.
4. RSA (Rivest-Shamir-Adleman): RSA is an asymmetric encryption method widely used for digital signatures and key exchange. It is considered one of the most protected encryption methods available.
5. SHA (Secure Hash Algorithm): SHA is a cryptographic hash function widely used for data integrity and authentication. It ensures that data has not been altered during transmission.
Potential Vulnerabilities In Data Transfer Security, And How Can They Be Mitigated?
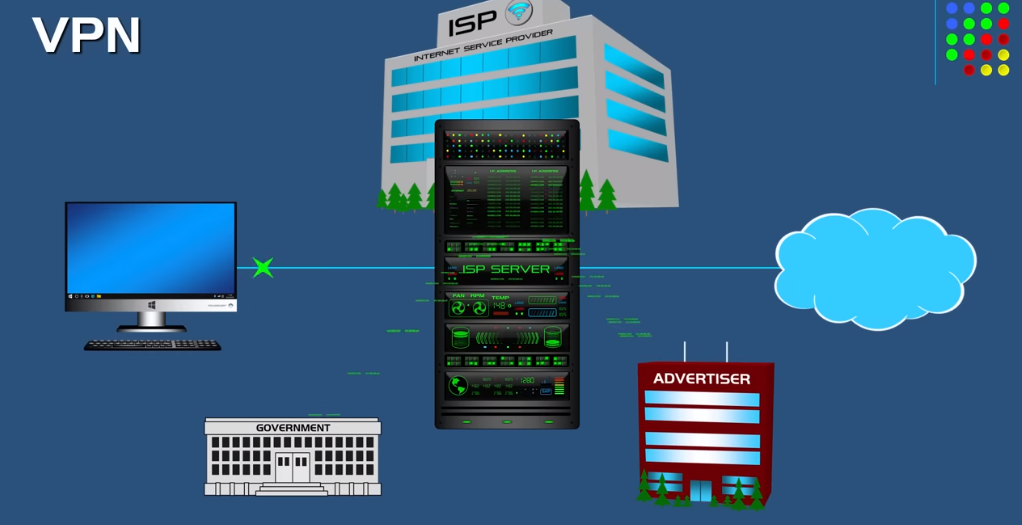
There are several potential vulnerabilities in data transfer security, including:
1. Man-in-the-Middle (MITM) attacks: This is where an attacker interrupts the communication between two parties and can access or modify the information being transmitted.
2. Weak passwords: If weak, they can be guessed or cracked easily, allowing unauthorized access to the transmitted data.
3. Unsecured networks: If the network being used to transmit data is not secure, it can be vulnerable to attacks.
4. Malware: Malware can be used to infect devices and steal data being transmitted.
To mitigate these vulnerabilities, several steps can be taken:
1. Use strong encryption: This can help protect against MitM attacks and ensure data is secure in transit.
2. Use strong passwords: Use complex and unique passwords that are hard to guess or crack.
3. Use secure networks: Use networks secured with firewalls, VPNs, and other security measures.
4. Use anti-malware software: This can help protect against malware that may infect devices and steal data.
5. Keep software up-to-date: Ensure that all software, including operating systems and applications, is up-to-date with the latest security patches and updates
Advantages And Disadvantages Of Various Encryption Methods And Protocols
Various encryption methods and protocols are available, each with advantages and disadvantages. Symmetric encryption is a method where the same key is utilized for encryption and decryption. It is fast and efficient, but the key must be kept secret, which can be challenging.
Asymmetric encryption, also called public-key encryption, uses two keys – a public key for encryption and a private key for decryption. This method is more secure than symmetric encryption but slower and more resource-intensive.
SSL/TLS is a protocol commonly used to secure web connections. It provides a secure channel for data transmission and uses a combination of symmetric and asymmetric encryption. It is widely adopted and supported but can be vulnerable to man-in-the-middle attacks.
Another protocol, IPsec, is also used to secure internet protocol (IP) communications. It provides strong security and can be used for a wide range of applications, but it can be complex to configure and may not be compatible with all network devices.
What Protocol Encrypts Data Before It Is Sent Across The Internet?
One protocol encrypts data before it is sent across the internet is the Transport Layer Security (TLS) protocol. It is usually used to secure web traffic and email communication. TLS uses symmetric and asymmetric encryption to protect data from interception and tampering. It is important to note that TLS should be implemented with the latest and strongest encryption algorithms to ensure maximum security.
Best Practices For Secure Web Data Transfer
There are several best practices for secure web data transfer, including:
1. Use HTTPS: Ensure that all web traffic is encrypted using HTTPS, which provides secure communication over the internet.
2. Implement SSL/TLS: SSL/TLS protocols to encrypt data in transit and protect against man-in-the-middle attacks.
3. Use strong encryption algorithms: Strong encryption algorithms such as AES ensure data is encrypted securely.
4. Limit access to sensitive data: Limit access to sensitive data by using access controls and ensuring that only approved individuals can access it.
5. Regularly monitor and audit data transfer: Regularly monitor and audit data transfer to identify potential security threats and vulnerabilities.
Key Components Of Encrypted Data Transfer
A few key components are important to understand regarding encrypted data transfer. These include:
1. Encryption algorithms: These are mathematical formulas used to scramble data so that it may not be read by anybody who doesn’t have the key to decrypt it.
2. Public key infrastructure (PKI): This system uses digital certificates to verify the identity of parties involved in data transfer. PKI helps ensure that data is sent to the intended recipient and not an imposter.
3. Digital certificates are electronic documents containing information about the certificate holder’s identity, such as their name and public key. They are issued by trusted third-party organizations called Certificate Authorities (CAs).
4. Secure Sockets Layer (SSL) or Transport Layer Security (TLS): These protocols provide secure internet communication. They use encryption algorithms and digital certificates to protect data in transit.
Factors Affecting Encryption And Security
Several factors can affect encryption and security. Some of these factors include:
1. Key length: The longer the encryption key, the more secure the data is. A longer key makes it more difficult for hackers to crack the encryption.
2. Algorithm strength: The strength of the encryption algorithm also plays a role in security. Stronger algorithms are more difficult to crack.
3. Certificate Authority (CA) trustworthiness: The trustworthiness of the CA used to issue digital certificates is important. If the CA is not trusted, the digital certificate may not be trusted, compromising security.
4. Implementation: Implementing encryption and security measures is also important. The proper implementation ensures that encryption and security measures are effective and functioning as intended.
Considering these factors, individuals and organizations can certify their data is encrypted and secure.
Challenges In Implementing Encryption
Implementing encryption can be a challenging task for individuals and organizations. Some of the challenges include:
1. Complexity: Encryption can be complex and difficult to implement. It requires a good understanding of encryption algorithms, key management, and digital certificates.
2. Compatibility: Encryption can be incompatible with some systems and applications. This can result in data loss, corruption, or other issues.
3. Cost: Implementing encryption can be costly, especially for organizations with large amounts of data. This includes the cost of hardware, software, and personnel to manage the encryption process.
4. Performance: Encryption can impact system performance, especially for systems with large amounts of data. This can result in slower system response times and reduced productivity.
5. User resistance: Users may resist the implementation of encryption, especially if it adds additional steps or complexity to their workflow.
To overcome these challenges, it is significant to plan and implement encryption carefully and to provide training and support to users to ensure they understand the importance and benefits of encryption.
Conclusion
In conclusion, securing web data transfer is crucial for any organization that handles sensitive information. It is crucial to prioritize data protection and comply with industry regulations and standards to prevent data breaches and maintain customer trust. As a writing assistant, I recommend that readers stay informed about the latest security measures and implement them in their organizations. It is also important to conduct regular security audits and training sessions for employees to ensure everyone knows the risks and how to prevent them. Organizations can protect their data and reputation in the long run by taking proactive steps.
Frequently Asked Questions (FAQs)
What Is Encryption, And Why Is It Required For Web Data Transfer?
Encryption is converting data into a code to prevent unauthorized access. Web data transfer must ensure that sensitive information, like passwords, credit card numbers, and personal information, is protected from hackers and cybercriminals. Without encryption, this information could be intercepted and used for malicious purposes, leading to data breaches and identity theft. Encrypting data becomes unreadable to anyone who does not have the key to unlock it, making it much tougher for hackers to gain access.
What Is The Difference Between HTTPS And HTTP?
HTTP is called Hypertext Transfer Protocol, while HTTPS stands for Hypertext Transfer Protocol Secure. The main difference is that HTTPS uses encryption to protect data transferred between a website and a user’s browser, while HTTP does not. This means that data transmitted over HTTPS is more secure and less vulnerable to interception by hackers. When browsing a website using HTTPS, you typically see a padlock icon in your browser’s address bar, highlighting that the connection is secure.
How Does SSL/TLS Ensure Secure Communication?
SSL/TLS (Secure Sockets Layer/Transport Layer Security) is a protocol that confirms secure communication between a client and a server. It encrypts data transmitted between the two, making it unreadable to anyone who intercepts it. When a client joins a server using SSL/TLS, it leads its digital certificate to the client. This certificate contains the server’s public key, which encrypts data sent to the server. The client then generates a random session key, which is used to encrypt data sent back to the client.
Once the client and server have made a secure connection using SSL/TLS, all data transmitted between them is encrypted and cannot be intercepted by hackers. This ensures that sensitive information, such as login credentials and credit card numbers, remains secure.
