Importance of Secure Data Transmission
In today’s digital age, secure data transmission is more important than ever. With cyber threats on the rise, it’s crucial to ensure that sensitive information is protected during transmission. Whether it’s personal information, financial data, or confidential business documents, the consequences of a data breach can be severe. That’s why choosing the right protocol for secure data transmission is essential. In this guide, we’ll explore the different protocols available and help you decide which one is best for your needs.
Different Types of Protocols
There are several protocols available for secure data transmission, each with its strengths and weaknesses. Here are some of the most common ones:
- Secure Sockets Layer (SSL): SSL is one of the most widely used protocols for secure data transmission. It provides encryption and authentication for data transmitted over the internet. SSL is commonly used for online transactions, such as e-commerce and online banking.
- Transport Layer Security (TLS): TLS is the successor to SSL and is now the standard protocol for secure data transmission. It provides similar encryption and authentication as SSL but with stronger security features. TLS is commonly used for email, instant messaging, and virtual private networks (VPNs).
- Internet Protocol Security (IPsec): IPsec is a protocol used to secure Internet communication. It provides encryption and authentication for data transmitted over the internet. IPsec is commonly used for VPNs and remote access to corporate networks.
- Point-to-Point Tunneling Protocol (PPTP): PPTP is a protocol used for secure data transmission over the Internet. It provides encryption and authentication for data transmitted between two points. PPTP is commonly used for VPNs.
What is Secure Data Transmission?
Secure data transmission refers to the process of transmitting data over a network in a way that ensures the confidentiality, integrity, and availability of the data. This involves using encryption to protect the data from unauthorized access, as well as authentication to verify the identities of the parties involved in the communication. Secure data transmission is important for protecting sensitive information, such as personal and financial data, from being intercepted or tampered with during transmission.
Understanding Data Transmission Protocols
Data transmission protocols are sets of rules and standards that govern the way data is transferred between devices over a network. Some common protocols include TCP/IP, HTTP, FTP, and SMTP. Each protocol has its specific functions and features, and choosing the right protocol for a particular application or use case is important for ensuring efficient and secure data transmission. It is also important to understand the limitations and potential vulnerabilities of each protocol, as well as any potential compatibility issues with different devices and systems.
Differences Between Protocols
There are many differences between protocols, including their specific functions, features, and limitations. For example, TCP/IP is a protocol used for transmitting data over the internet, while HTTP is a protocol used for transmitting web pages and other content. FTP is a protocol used for file transfer, while SMTP is a protocol used for email transmission. Each protocol has its own set of rules and procedures for transmitting data, and these rules can vary widely depending on the protocol.
Common Data Transmission Protocols
- Transmission Control Protocol (TCP)
- User Datagram Protocol (UDP)
- Hypertext Transfer Protocol (HTTP)
- File Transfer Protocol (FTP)
Security Protocols for Data Transmission
- Transport Layer Security (TLS)
- Secure Sockets Layer (SSL)
- Secure Shell (SSH)
- Internet Protocol Security (IPsec)
- Datagram Transport Layer Security (DTLS)
- Simple Mail Transfer Protocol (SMTP)
What is SSL/TLS?
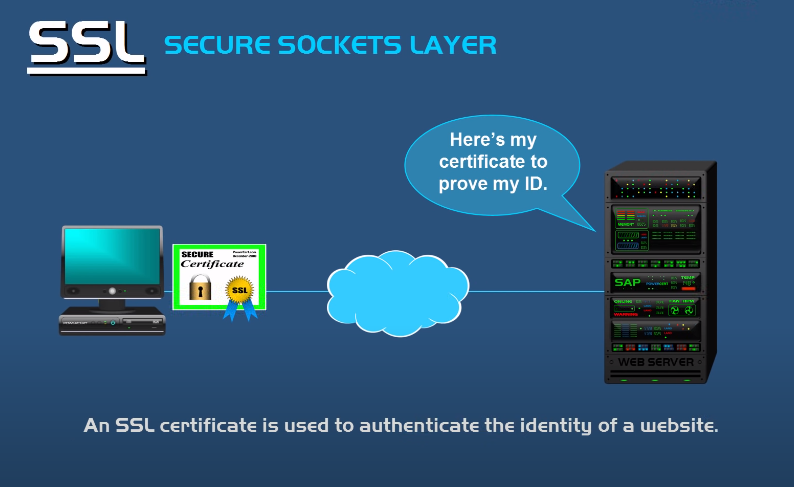
SSL/TLS stands for Secure Sockets Layer/Transport Layer Security. It is a security protocol used for data transmission over the internet. SSL/TLS encrypts the data being transmitted between two endpoints, making it difficult for anyone to intercept or read the data. This protocol is commonly used for secure online transactions, such as online banking, e-commerce, and secure email communication. SSL/TLS uses a combination of public and private keys to establish a secure connection between two endpoints.
Differences Between SSL and TLS
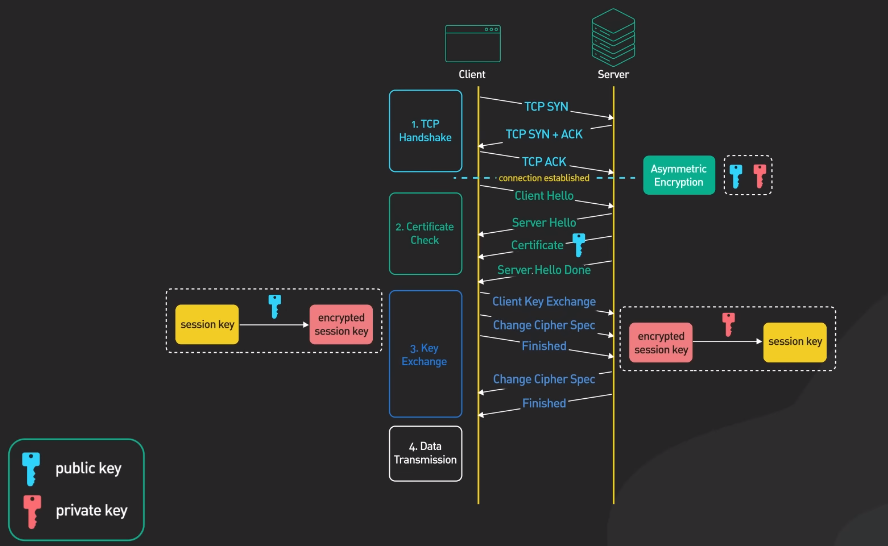
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are both cryptographic protocols used to secure data transmission over the internet. However, there are some differences between the two. Firstly, SSL is an older protocol that is no longer considered secure, while TLS is the newer and more secure successor to SSL. TLS has several updated security features that make it more resistant to attacks and vulnerabilities.
What is SSH?

SSH (Secure Shell) is a cryptographic network protocol used for secure communication between two endpoints. It provides a secure channel over an unsecured network, such as the Internet, allowing remote access to a computer or server. SSH uses encryption to protect the confidentiality and integrity of data being transmitted, as well as authentication to verify the identity of the endpoints involved in the communication. It is commonly used by system administrators and developers to remotely access and manage servers and other network devices.
How Does SSH Work?
SSH works by establishing a secure connection between two endpoints, typically a client and a server. The client initiates the connection by sending a request to the server, which response by sending an encrypted message containing its public key. The client then uses this public key to encrypt a random session key, which is sent back to the server. The server uses its private key to decrypt the session key, which is then used to encrypt all subsequent communication between the two endpoints. This process provides several layers of security.
Differences Between SSHv1 and SSHv2
SSHv1 and SSHv2 are two different versions of the SSH protocol used for secure communication between two endpoints. SSHv2 is considered more secure than SSHv1 due to its improved encryption algorithms and key exchange methods. SSHv1 uses the RSA algorithm for key exchange, whereas SSHv2 supports multiple algorithms including Diffie-Hellman, Elliptic Curve, and RSA.
What is IPsec?
IPsec (Internet Protocol Security) is a protocol suite used for securing Internet Protocol (IP) communications by encrypting and authenticating each IP packet of a communication session. It provides confidentiality, integrity, and authenticity of data transmitted over IP networks by using cryptographic security services. IPsec can be used to create Virtual Private Networks (VPNs) to connect remote networks securely over the internet. It operates at the network layer of the OSI model and can be implemented in both transport mode and tunnel mode.
How Does IPsec work?
IPsec works by adding security features to IP packets as they are transmitted over a network. It uses two main protocols: Authentication Header (AH) and Encapsulating Security Payload (ESP).AH provides authentication and integrity by adding a digital signature to each IP packet. This signature ensures that the packet has not been altered in transit and that it originated from a trusted source.
ESP provides confidentiality by encrypting the contents of each IP packet. This ensures that the data cannot be read by unauthorized parties.
Differences Between IPsec Transport Mode And Tunnel Mode
The main difference between IPsec transport mode and tunnel mode is the scope of protection they provide. In transport mode, only the payload (the actual data being transmitted) of the IP packet is encrypted and authenticated. The IP header remains intact and is not encrypted. This mode is typically used for end-to-end communication between two hosts within a network.
On the other hand, in tunnel mode, both the IP header and the payload are encrypted and authenticated.
What is DTLS?
DTLS stands for Datagram Transport Layer Security. It is a protocol that provides security for datagram-based applications by adding encryption, message authentication, and integrity checking to the transport layer. DTLS is based on the same principles as SSL/TLS, but it is designed to work with datagram protocols such as UDP, which are connectionless and unreliable. DTLS is commonly used for secure real-time communication applications such as VoIP, video conferencing, and online gaming.
How Does DTLS Work?
DTLS works by adding security features to the transport layer of datagram-based applications. It uses a combination of encryption, message authentication, and integrity checking to secure the data being transmitted. When a DTLS connection is established between two endpoints, the endpoints exchange information to negotiate the encryption and authentication algorithms to be used. Once the negotiation is complete, the endpoints use these algorithms to encrypt and authenticate the data being transmitted.
What is SMTP?
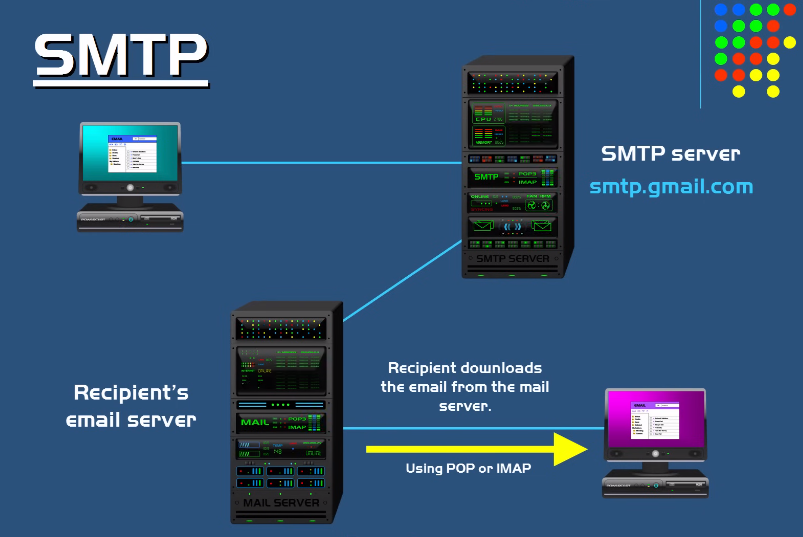
SMTP stands for Simple Mail Transfer Protocol. It is a standard protocol used for sending and receiving email messages over the Internet. SMTP is responsible for the transfer of outgoing mail from the sender’s email client to the email server, and for the transfer of incoming mail from the email server to the receiver’s email client. SMTP is a text-based protocol that uses a set of commands and responses to transfer email messages.
How Does SMTP Work?
SMTP works by establishing a connection between the sender’s email client and the email server. Once the connection is established, the sender’s email client sends a series of commands to the email server to initiate the email transfer process. These commands include identifying the sender and recipient email addresses, specifying the email content and formatting, and requesting the email server to send the email to the recipient. The email server then processes the commands and sends a series of responses back to the sender’s email client to confirm the successful transmission.
Choosing Right Protocol for Your Needs
When it comes to choosing the right protocol for your email needs, there are a few factors to consider. The most common protocols are POP3, IMAP, and SMTP.POP3 (Post Office Protocol version 3) is a protocol used for retrieving email from a remote server. It downloads the email from the server to the user’s device and typically deletes the email from the server once it has been downloaded. This protocol is best suited for users who only access their email from one device.
IMAP (Internet Message Access Protocol) is a protocol used for accessing email on a remote server. It allows users to access their email from multiple devices and keeps the email stored on the server. This protocol is best suited for users who access their email from multiple devices.
SMTP (Simple Mail Transfer Protocol) is a protocol used for sending emails. It is used to transfer email from the sender’s email client to the recipient’s email server. This protocol is necessary for sending emails, regardless of which protocol is used for accessing the email.
Ultimately, the protocol you choose will depend on your specific needs and how you access your email. It’s important to consider factors such as device usage and email storage preferences when making your decision.
Best Practices for Secure Data Transmission
SMTP (Simple Mail Transfer Protocol) is the protocol used for sending emails. It is a standard protocol that is widely used across the internet. SMTP is responsible for transferring email messages from the sender’s email client to the recipient’s email server. It is essential for sending emails, regardless of which protocol is used for accessing the email.
Real-World Applications of Secure Data Transmission
Secure data transmission is essential for many real-world applications, including:
- Online Banking: Banks use secure data transmission protocols to ensure that their customer’s financial information is protected.
- E-commerce: Online retailers use secure data transmission to protect their customers’ personal and financial information during transactions.
- Healthcare: Healthcare providers use secure data transmission to protect patients’ medical records and other sensitive information.
- Government: Government agencies use secure data transmission to protect classified information and ensure the privacy of citizens.
Emerging Trends in data transmission protocols
There are several emerging trends in data transmission protocols that are gaining popularity in various industries. One such trend is the use of blockchain technology for secure data transmission. Blockchain technology uses a decentralized and distributed ledger system that is highly secure and resistant to tampering. Another trend is the use of quantum cryptography for secure data transmission. This technology uses the principles of quantum mechanics to create unbreakable encryption keys that are highly secure and virtually impossible to hack.
Conclusion
In conclusion, the use of advanced technologies such as blockchain and quantum cryptography is gaining popularity in various industries for secure data transmission. These technologies offer highly secure and tamper-resistant solutions that can help organizations protect their sensitive information from cyber threats. As technology continues to evolve, businesses need to stay up-to-date with the latest trends and adopt new technologies to ensure the security of their data.
