Intro to Database Security
Database security refers to the set of measures taken to protect the confidentiality, integrity, and availability of data stored in a database. It involves implementing various security controls, such as encryption, access controls, and auditing, to prevent unauthorized access, modification, or destruction of data. User access control is a critical component of database security. It involves limiting access to the database to only authorized users and ensuring that each user has the appropriate level of access based on their role and responsibilities.
Overview of Two Central Steps for Allowing User Access to Data
The two central steps for allowing user access to data in a database are authentication and authorization. Authentication involves verifying the identity of a user, typically through a username and password or other credentials. Once a user has been authenticated, authorization determines what level of access they have to the database and its data. This is typically based on the user’s role and responsibilities within the organization. Access control policies can be implemented to ensure that users only have access to the data they need to perform their job functions and nothing more. Regular auditing and monitoring can also help detect and prevent unauthorized access attempts and other security breaches.
Part I: Authentication
Authentication in the Context of Database Security
Authentication in the context of database security refers to the process of verifying the identity of a user or entity attempting to access the database. This is typically done through the use of login credentials, such as a username and password, that are unique to each user. Authentication helps ensure that only authorized users can access the database and its data. It is a critical component of database security, as it helps prevent unauthorized access and data breaches.
Types of Authentication Methods
Authentication is the process of verifying the identity of a user or entity attempting to access a system or database. There are several types of authentication methods, including:
1. Passwords: This is the most common type of authentication method, where users are required to enter a unique username and password combination to access the database. Passwords should be strong and complex to prevent unauthorized access.
2. Biometrics: This type of authentication uses physical characteristics, such as fingerprints or facial recognition, to verify a user’s identity. Biometric authentication is becoming more common and is considered more secure than passwords.
3. Two-factor authentication: This type of authentication requires users to provide two forms of identification, such as a password and a fingerprint scan, to access the database. Two-factor authentication is considered more secure than single-factor authentication methods.
It is important to choose the appropriate authentication method based on the level of security required for the database or system.
Best Practices for Implementing Authentication in Database Security
Here are some best practices for implementing authentication in database security:
1. Use strong and unique passwords: Encourage users to create strong and unique passwords that are difficult to guess or crack. Implement password policies that require users to change their passwords regularly and prevent them from using common words or phrases.
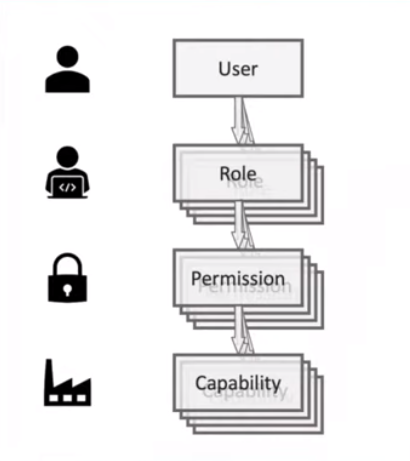
2. Limit access: Only grant access to the database to those who need it. Implement role-based access control (RBAC) to restrict access based on job roles and responsibilities.
Part II: Authorization
Authorization in Context of Database Security
Authorization in the context of database security refers to the process of granting or denying access to specific resources or actions within a database system. This includes controlling access to data, tables, views, stored procedures, and other database objects. Authorization is typically implemented through user accounts and permissions, which are assigned based on the user’s role, job responsibilities, and level of trust. The goal of authorization is to ensure that only authorized users can access and modify data, and that sensitive information is protected from unauthorized access.
Types of Authorization Models
Authorization is a crucial aspect of database security, and several different models can be used to implement it.
1. Discretionary Access Control (DAC): This model is based on the discretion of the data owner or administrator, who determines which users or groups are granted access to specific resources. In DAC, the owner of the resource has complete control over who can access it and what actions they can perform on it.
2. Mandatory Access Control (MAC): This model is based on a system of labels or tags that are attached to data and users. The labels represent the sensitivity level of the data, and users are granted access based on their clearance level. MAC is often used in government and military environments where security is of utmost importance.
3. Role-Based Access Control (RBAC): This model is based on the concept of roles, which are sets of permissions that are assigned to users based on their job responsibilities or functions within an organization. RBAC is a flexible and scalable model that can be used to manage access to complex systems with many users and resources.
Each of these models has its strengths and weaknesses, and the choice of which one to use will depend on the specific needs and requirements of the organization.
Best Practices for Implementing Authorization in Database Security
Here are some best practices for implementing authorization in database security:
1. Use RBAC: RBAC is a widely accepted and flexible model for managing access to complex systems. It allows for the creation of roles that are assigned to users based on their job responsibilities or functions within an organization.
2. Limit access: Limit access to only those resources that are necessary for a user’s job function. This reduces the risk of unauthorized access to sensitive data.
Part III: Combining Authentication and Authorization
Explanation of How Authentication and Authorization Work Together
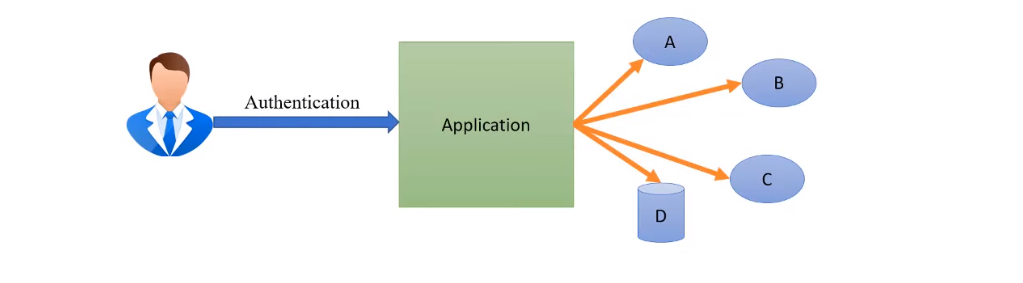
Authentication and authorization work together to ensure that only authorized users have access to sensitive data and resources within a system. Authentication is the process of verifying a user’s identity, typically through the use of a username and password or other credentials. Once a user has been authenticated, the system can then determine what resources they are authorized to access based on their assigned roles or permissions.
Authorization is the process of granting or denying access to specific resources based on a user’s identity and assigned roles.
Benefits of Using Both Steps for User Access Control
Using both authentication and authorization steps for user access control provides several benefits, including:
1. Improved Security: By requiring users to authenticate themselves before accessing resources and then authorizing them based on their assigned roles or permissions, the system can ensure that only authorized users have access to sensitive data and information.
2. Better Control: With a proper authentication and authorization system in place, administrators can easily manage user access across the organization and ensure that users only have access to the resources they need to do their job.
Challenges When Combining The Two Steps And How To Address Them
One common challenge when combining authentication and authorization is ensuring that the system accurately identifies and verifies the identity of users before granting access. This can be addressed by implementing multi-factor authentication, such as requiring users to provide a password and a unique code sent to their mobile device. Another challenge is managing permissions and roles effectively. This can be addressed by regularly reviewing and updating user roles and permissions based on their job responsibilities and changes in the organization.
Conclusion
In conclusion, implementing a strong identity and access management system is critical for ensuring the security and integrity of an organization’s data and systems. By addressing challenges such as accurate user identification and effective permission management, organizations can minimize the risk of unauthorized access and potential data breaches. Regular reviews and updates to the system can also help to ensure ongoing effectiveness and protection.
