Importance of Securing Data Centers
Securing data centers is critical for organizations as they hold sensitive and confidential information that needs to be protected from unauthorized access, theft, and cyber attacks. Data breaches can result in significant financial losses, legal liabilities, and damage to the organization’s reputation. Therefore, it is essential to have robust security measures in place to safeguard data centers. One effective way to secure data centers is through Identity and Access Management (IAM) integration.
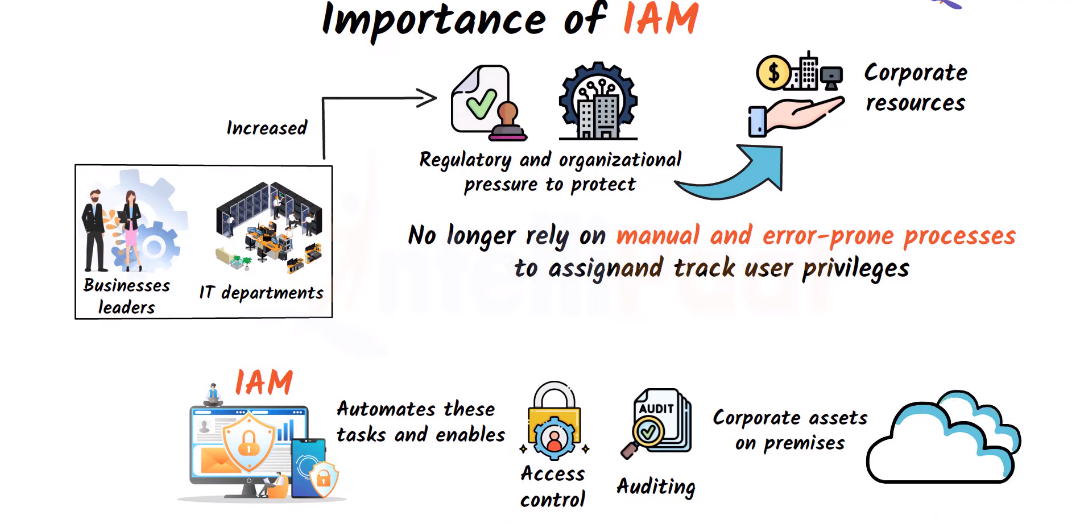
Introduction to IAM (Identity and Access Management)
Identity and Access Management (IAM) is a framework of policies, processes, and technologies that enable organizations to manage digital identities and control access to their systems, applications, and data. IAM solutions help organizations ensure that only authorized users have access to sensitive information and resources while preventing unauthorized access and data breaches. IAM solutions typically include features such as authentication, authorization, and access control, and can be integrated with other security technologies such as encryption, firewalls, and intrusion detection systems.
IAM and Data Center Security: An Overview

IAM, or Identity and Access Management, is a framework of policies, technologies, and processes that manage digital identities and their access to resources within an organization. IAM plays a critical role in data center security by ensuring that only authorized individuals have access to sensitive data and resources. IAM solutions typically involve the use of authentication mechanisms, such as passwords or biometric factors, to verify the identity of users.
Benefits of IAM Integration With Data Center Security

Integrating IAM with data center security provides several benefits, including:
- Improved security: IAM ensures that only authorized individuals have access to sensitive data and resources, reducing the risk of data breaches and cyber-attacks.
- Simplified access management: IAM solutions automate the process of granting and revoking access to resources, making it easier for administrators to manage access.
- Increased efficiency: IAM solutions streamline the authentication process, reducing the time and effort required for users to access resources.
IAM Integration with Data Center Security: Key Considerations
When integrating IAM solutions with data center security, there are several key considerations to keep in mind:
- Compatibility: Ensure that the IAM solution is compatible with your existing data center security infrastructure, including firewalls, intrusion detection systems, and other security tools.
- Scalability: Consider the scalability of the IAM solution, particularly if you have a large number of users and resources to manage.
- User authentication: Choose an IAM solution that offers strong user authentication mechanisms, such as multi-factor authentication,
Understanding The Existing Security Landscape
Before implementing an IAM solution, it is important to understand the existing security landscape of your organization. This includes identifying the types of data and resources that need to be protected, as well as the current security measures in place, such as firewalls, intrusion detection systems, and other security tools. By understanding the existing security landscape, you can ensure that the IAM solution you choose is compatible with your current security infrastructure and can effectively protect your organization’s resources and data.
Identifying And Prioritizing Critical Assets And Data
To identify and prioritize critical assets and data, you should start by conducting a thorough risk assessment. This involves identifying the potential risks and threats to your organization’s assets and data, as well as the potential impact of these risks and threats. Once you have identified your critical assets and data, you should prioritize them based on their importance to your organization. (Diazepam)
Evaluating IAM Solutions And Their Compatibility With Existing Systems
When evaluating IAM (Identity and Access Management) solutions, it’s important to consider their compatibility with your existing systems. This includes your network infrastructure, applications, and databases. You should also consider the scalability of the solution, as well as its ease of use and management. It’s important to choose an IAM solution that can integrate seamlessly with your existing systems, without causing any disruptions or compatibility issues. This will help to ensure a smooth transition and minimize any downtime or productivity losses.
Implementing IAM in Data Center Security: Best Practices
When implementing IAM in data center security, there are several best practices to consider. Firstly, it’s important to define clear roles and responsibilities for all users within the organization. This will help to ensure that each user has the appropriate level of access to data and systems, based on their job function and responsibilities.
Secondly, it’s important to implement strong authentication measures, such as multi-factor authentication, to ensure that only authorized users can access sensitive data and systems.
Developing An IAM Strategy And Implementation Plan
To develop an effective IAM strategy and implementation plan, you should consider the following steps:
- Define your organization’s IAM objectives: Identify the goals and objectives that your organization wants to achieve through IAM. This will help you to prioritize your efforts and ensure that your IAM strategy aligns with your business objectives.
- Conduct a risk assessment: Identify the potential risks and threats to your organization’s data and systems. This will help you to determine the level of security and access controls that are required.
Implementing IAM Policies And Procedures
To implement effective IAM policies and procedures, follow these steps:
- Define roles and responsibilities: Clearly define roles and responsibilities for all users, including employees, contractors, and vendors. This will help to ensure that everyone has the appropriate level of access to data and systems.
- Implement strong authentication: Use strong authentication methods, such as multi-factor authentication (MFA), to verify the identity of users before granting access to sensitive data and systems.
- Monitor and analyze activity: Implement monitoring and analysis tools to track user activity and detect any suspicious behavior or unauthorized access attempts.
- Enforce least privilege: Enforce the principle of least privilege, which means granting users only the minimum level of access necessary to perform their job functions.
- Regularly review access: Regularly review user access and permissions to ensure that they are still necessary and appropriate. Remove any unnecessary access or permissions.
Case Studies: IAM Integration in Data Center Security

In this case study, a large financial institution successfully integrated an identity and access management (IAM) solution into its data center security measures. The IAM solution allowed the institution to enforce the least privilege and regularly review user access, as recommended in the previous tips. Through the IAM solution, the institution was able to track user activity and detect any suspicious behavior or unauthorized access attempts. This helped them prevent potential security breaches and protect sensitive financial data.
Overview of Successful IAM Integration In Data Center Security
The integration of an Identity and Access Management (IAM) solution into a data center’s security measures can provide significant benefits in terms of enforcing the least privilege and regularly reviewing user access. By tracking user activity and detecting suspicious behavior, an IAM solution can help prevent potential security breaches and protect sensitive data. This was exemplified by an institution that successfully integrated an IAM solution into its data center security measures, leading to improved security and peace of mind.
Emerging Trends In IAM And Data Center Security
Emerging trends in IAM and data center security include the use of artificial intelligence and machine learning to enhance identity verification and authentication processes. This can help prevent identity theft and fraudulent access attempts. Additionally, there is a growing emphasis on identity governance and administration, which involves managing user access and permissions in a more centralized and automated manner. This can help organizations stay compliant with regulations and reduce the risk of data breaches caused by human error or oversight.
Impact of Cloud Computing on IAM Integration
The adoption of cloud computing has had a significant impact on IAM integration. With more organizations moving their applications and data to the cloud, traditional on-premises IAM solutions are becoming less effective. As a result, IAM vendors are developing cloud-based solutions that can integrate with various cloud platforms and applications. One of the benefits of cloud-based IAM solutions is that they can provide more flexibility and scalability than traditional on-premises solutions.
Conclusion
In conclusion, the adoption of cloud computing has led to the development of cloud-based IAM solutions that can integrate with various cloud platforms and applications. These solutions offer more flexibility and scalability than traditional on-premises IAM solutions, making them a better fit for modern organizations. As a writing assistant, I hope this information helps you understand the impact of cloud computing on IAM integration.
FAQs
What is IAM, and Why Is It Important In Data Center Security?
IAM stands for Identity and Access Management, and it is essential in data center security because it helps organizations control access to sensitive data and resources. IAM solutions ensure that only authorized individuals can access specific data and resources, reducing the risk of data breaches and unauthorized access. It also helps organizations comply with regulatory requirements, such as HIPAA and GDPR, by providing audit trails and access controls.
What are The Key Considerations When Integrating IAM with Data Center Security?
When integrating IAM with data center security, there are several key considerations to keep in mind. These include:
- Identity verification: IAM solutions should be able to verify the identity of users before granting access to data and resources. This can be done through multi-factor authentication, biometric authentication, or other methods.
- Access control: IAM solutions should provide granular access controls to ensure that users only have access to the data and resources they need to perform their job functions.
What are The Biggest Challenges to IAM Integration with Data Center Security, and How Can They Be Addressed?
The biggest challenges to IAM integration with data center security include:
- Complexity: IAM solutions can be complex to implement and manage, especially in large organizations with multiple systems and applications. This complexity can lead to errors and security vulnerabilities.
- User resistance: Users may resist IAM solutions if they perceive them as overly restrictive or burdensome. This can lead to non-compliance and security risks.
- Integration with legacy systems: Many organizations have legacy systems that were not designed with IAM in mind.
Can You Provide Examples of Successful IAM Integration in Data Center Security?
Certainly! Here are a few examples of successful IAM integration in data center security:
- Amazon Web Services (AWS): AWS offers a variety of IAM features that allow organizations to manage access to their AWS resources. This includes the ability to create and manage users, groups, and roles, as well as to set permissions and policies.
- Microsoft Azure: Azure also offers a range of IAM capabilities, including the ability to manage access to Azure resources using Azure Active Directory (Azure AD).
