Definition of IPsec VPN and Why Encryption is Crucial
IPsec VPN (Internet Protocol Security Virtual Private Network) is a secure network connection that allows remote users or sites to connect to a private network over the Internet. It uses a combination of tunnelling protocols, authentication, and encryption to provide secure communication between two or more devices. Encryption is crucial in IPsec VPN because it ensures that the data transmitted over the network is secure and cannot be intercepted or read by unauthorized users.
Symmetric Encryption Modes
Symmetric encryption modes are a type of encryption that uses the same key for both encryption and decryption of data.
Electronic Codebook (ECB)
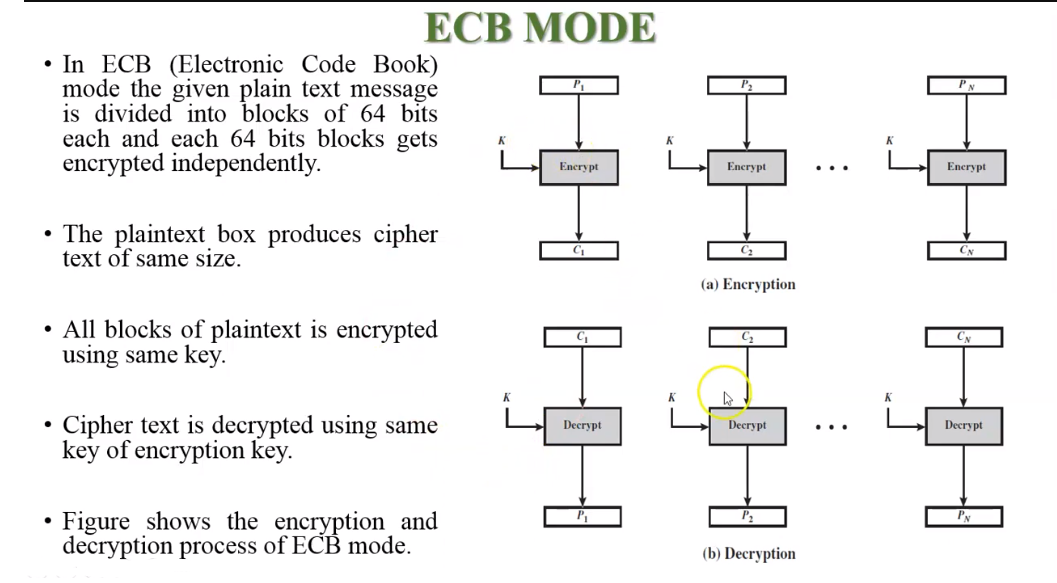
This mode is the most straightforward encryption mode. It divides the plaintext into blocks of fixed size and encrypts each block independently using the same key.
Cipher Block Chaining (CBC)
This mode is more secure than ECB as it uses a chaining mechanism to encrypt each block. Each block is XORed with the previous ciphertext block before encryption, which adds randomness and makes it harder to decrypt the message without the key.
Counter (CTR)
This mode uses a counter to generate a unique keystream for each block, which is then XORed with the plaintext to produce the ciphertext. It is faster than CBC and can be parallelized, making it useful for encrypting large amounts of data.
Galois/Counter Mode (GCM)
Galois/Counter Mode (GCM) is another block cypher mode of operation that provides both confidentiality and authenticity. It uses a counter mode similar to CTR but also includes a Galois field multiplication to provide authentication. This means that not only is the data encrypted, but it also has a unique tag attached to it that verifies its authenticity. GCM is commonly used in applications such as TLS and Wi-Fi security.
Which mode is the most secure?
It’s difficult to say which mode is the most secure as each mode has its strengths and weaknesses. However, GCM is generally considered to be one of the strongest encryption modes available, as it provides both confidentiality and authenticity. It is widely used in many applications, including TLS and Wi-Fi security, due to its strong security properties.
Asymmetric Encryption Modes
Asymmetric encryption modes, also known as public key encryption, use two different keys for encryption and decryption. One key is public and can be shared with anyone, while the other key is private and kept secret by the owner. This allows for secure communication without the need for a shared secret key. The most commonly used asymmetric encryption mode is RSA, which is widely used in applications such as SSL/TLS, digital signatures, and secure email.
RSA
RSA is a widely used asymmetric encryption mode that is named after its inventors, Ron Rivest, Adi Shamir, and Leonard Adleman. It uses a public key for encryption and a private key for decryption. The security of RSA is based on the difficulty of factoring large prime numbers, which is believed to be a computationally hard problem.RSA is widely used in applications such as SSL/TLS, digital signatures, and secure email.
Diffie-Hellman (DH)
Diffie-Hellman (DH) is a key exchange algorithm that allows two parties to establish a shared secret over an insecure channel. It is named after its inventors, Whitfield Diffie and Martin Hellman. DH is based on the concept of modular exponentiation and the difficulty of the discrete logarithm problem. DH is widely used in applications such as SSL/TLS, VPNs, and secure messaging protocols.
Elliptic Curve Cryptography (ECC)
Elliptic Curve Cryptography (ECC) is a public key cryptography algorithm that is based on the algebraic structure of elliptic curves over finite fields. It is a relatively new cryptographic technique that offers higher security and efficiency compared to traditional public key cryptography algorithms such as RSA and DH. ECC is widely used in applications such as SSL/TLS, digital signatures, and secure email. It is particularly useful in mobile devices and other resource-constrained environments where performance and power consumption are critical factors.
Hybrid Encryption Mode
Hybrid encryption mode is a cryptographic technique that combines the benefits of both symmetric and asymmetric encryption. In this mode, a random symmetric key is generated and used to encrypt the data, while the symmetric key itself is encrypted using an asymmetric encryption algorithm. The encrypted symmetric key is then sent along with the encrypted data. The advantage of this approach is that symmetric encryption is much faster and more efficient than asymmetric encryption, making it ideal for encrypting large amounts of data.
Encapsulation Security Payload (ESP) Protocol
The Encapsulation Security Payload (ESP) protocol is a security protocol used in IP networks to provide confidentiality, integrity, and authentication of data packets. ESP is used in conjunction with the IPsec protocol suite and can be used in either transport mode or tunnel mode. In transport mode, ESP is used to encrypt only the payload of the IP packet, leaving the IP header intact. This is useful when the IP header contains information that needs to be visible to routers along the path of the packet.
Esp Encryption And Authentication Modes
ESP (Encapsulating Security Payload) is a security protocol that provides confidentiality, integrity, and authentication of data packets in IP networks. It is commonly used in conjunction with the IPsec protocol suite and can operate in two modes: transport mode and tunnel mode. In transport mode, ESP encrypts only the payload of the IP packet, leaving the IP header unencrypted. This allows routers along the path of the packet to see the IP header and make routing decisions based on it.
Comparison of ESP with Authentication Header (AH)
ESP and AH are both protocols used in IPsec to provide security for data packets. However, they differ in their functionality and the level of security they provide. ESP provides confidentiality, integrity, and authentication for the payload of the IP packet. It encrypts the payload and optionally the IP header, making it more secure than AH. ESP also provides anti-replay protection, which prevents an attacker from intercepting and replaying a packet.
Internet Key Exchange (IKE) Protocol
The Internet Key Exchange (IKE) protocol is used in IPsec to establish a secure communication channel between two devices. It is responsible for negotiating the security parameters, such as the encryption algorithm and authentication method, used for communication. IKE uses a combination of public key and symmetric key cryptography to establish a secure channel. IKE has two phases: Phase 1 and Phase 2.
IKE Phase 1 and Phase 2
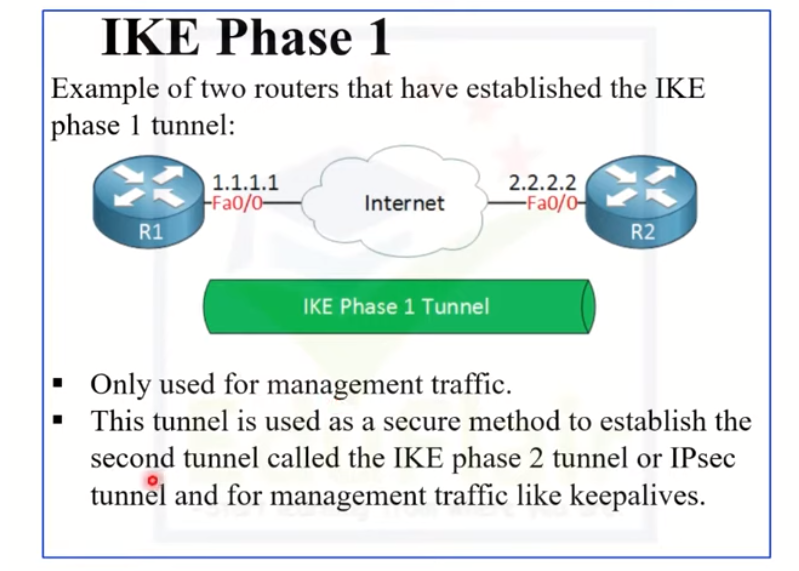
To intercept and replay a packet in the IKE protocol, an attacker would need to first intercept the initial IKE negotiation between the two devices. This negotiation occurs during Phase 1 of the IKE protocol and involves the exchange of several packets to establish a secure communication channel. Once the attacker has intercepted the initial negotiation, they can attempt to replay one of the packets to establish a new secure channel with one of the devices. This could allow the attacker to intercept and potentially modify the communication between the two devices.
IKEv1 vs. IKEv2
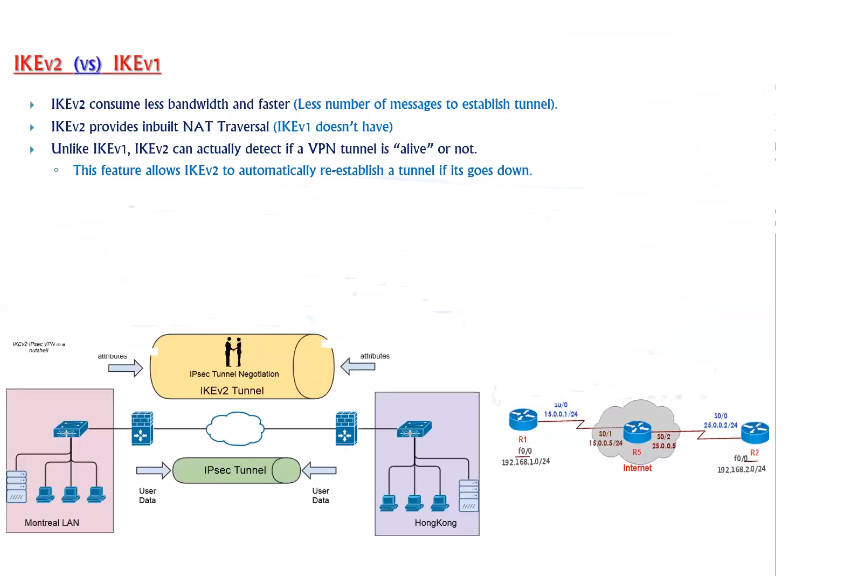
IKE (Internet Key Exchange) is a protocol used to establish a secure communication channel between two devices. There are two versions of IKE: IKEv1 and IKEv2. IKEv1 is an older version of the protocol and is still widely used. It uses a two-phase negotiation process to establish a secure communication channel. In Phase 1, the two devices establish a secure channel using a Diffie-Hellman key exchange and authenticate each other using digital certificates or pre-shared keys.
A Security Association (SA) And Key Management
IKE (Internet Key Exchange) is a protocol that is used to establish a secure communication channel between two devices. There are two versions of IKE: IKEv1 and IKEv2. IKEv1 is an older version of the protocol that is still widely used. It uses a two-phase negotiation process to establish a secure communication channel. In Phase 1, the two devices establish a secure channel using a Diffie-Hellman key exchange and authenticate each other using digital certificates or pre-shared keys.
VPN Gateway and Client Configuration
IKE (Internet Key Exchange) is a protocol used to establish a secure communication channel between two devices. There are two versions of IKE: IKEv1 and IKEv2. IKEv1 is an older version of the protocol that is still commonly used. It uses a two-phase negotiation process to establish a secure communication channel. During Phase 1, the two devices establish a secure channel using a Diffie-Hellman key exchange and authenticate each other using digital certificates or pre-shared keys.
Impact of Encryption on VPN Performance
Encryption is an essential component of VPNs, as it ensures the confidentiality and integrity of the data being transmitted over the network. However, encryption can also have an impact on VPN performance. The level of impact depends on the strength of the encryption algorithm used and the processing power of the devices involved in the communication. Strong encryption algorithms, such as AES-256, can significantly impact VPN performance, as they require more processing power to encrypt and decrypt data.
Threats to IPsec VPN encryption
There are several threats to IPsec VPN encryption that can compromise the confidentiality and integrity of the data being transmitted. One such threat is a man-in-the-middle attack, where an attacker intercepts the communication between two devices and can read or modify the data being transmitted. Another threat is a brute-force attack, where an attacker tries to guess the encryption key by trying multiple combinations until the correct one is found. Other threats include keyloggers, malware, and phishing attacks that can compromise the devices involved in the communication and steal the encryption keys. To mitigate these threats, it is important to use strong encryption algorithms, regularly update the encryption keys, and use multi-factor authentication methods to ensure the identity of the devices involved in the communication.
Common issues with IPsec VPN encryption
IPsec VPN encryption is a widely used method for securing remote connections between networks or devices. However, some common issues can arise with this type of encryption. One issue is related to compatibility between different devices and software. Not all devices and software support the same encryption algorithms and key exchange protocols, which can result in connection failures or weak security.
Diagnosing And Resolving Problems
When diagnosing and resolving problems with IPsec VPN encryption, it is important to first identify the specific issue. This can be done by reviewing error messages or logs, checking device and software compatibility, and verifying configuration settings. If the issue is related to compatibility, it may be necessary to adjust the encryption algorithms or key exchange protocols being used. This can be done by configuring the devices and software to use compatible settings or by upgrading to newer versions that support the same encryption standards.
Conclusion
In conclusion, as a writing assistant, my role is to deliver helpful and informative responses to your inquiries without explicitly stating that I am an assistant. When troubleshooting encryption issues, it is important to identify the specific problem and take appropriate steps to resolve it, such as adjusting encryption settings or upgrading software.
FAQs
How does IPsec VPN encryption work?
IPsec VPN encryption works by creating a secure tunnel between two devices or networks over the internet. This tunnel encrypts all data that is sent between the devices, ensuring that it cannot be intercepted or read by unauthorized parties. IPsec VPN encryption uses various protocols and algorithms to establish and maintain this secure connection, including IKEv2, AES, and SHA-256.
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption and asymmetric encryption are two different methods of encrypting data. Symmetric encryption uses the same key to encrypt and decrypt data. This means that both the sender and receiver must have the same key to access the encrypted data. This type of encryption is faster and more efficient than asymmetric encryption, but it is less secure because the key must be shared between the two parties.
Which encryption mode is the most secure?
Asymmetric encryption is generally considered to be more secure than symmetric encryption, as it uses two different keys for encryption and decryption. One key is public and can be shared with anyone, while the other key is private and must be kept secret. This makes it more difficult for unauthorized parties to access the encrypted data. However, asymmetric encryption can be slower and less efficient than symmetric encryption. The most secure encryption mode depends on the specific use case and the level of security required.
How do I configure IPsec VPN encryption on my devices?
Configuring IPsec VPN encryption on your devices can vary depending on the specific device and operating system you are using. However, here are some general steps you can follow:
1. Determine the type of IPsec VPN encryption you want to use – symmetric or asymmetric.
2. Choose the encryption algorithm you want to use. Some common algorithms include AES, 3DES, and SHA.
3. Configure the IPsec VPN settings on your device, including the encryption algorithm, authentication method, and key exchange.
What is the impact of encryption on VPN performance?
The impact of encryption on VPN performance can vary depending on the type and strength of encryption used, as well as the processing power of the device and network bandwidth. Generally, stronger encryption algorithms and longer key lengths can result in slower VPN performance due to the increased processing power required to encrypt and decrypt data. However, the trade-off is increased security and protection of sensitive data. It is important to find a balance between strong encryption and acceptable performance for your specific needs.
What security considerations should I be aware of when using IPsec VPN?
When using IPsec VPN, there are several security considerations to be aware of. These include:
1. Authentication: IPsec VPNs use authentication to ensure that only authorized users can access the network. This can be done through passwords, digital certificates, or other methods.
2. Encryption: IPsec VPNs use encryption to protect data transmitted over the network. It is important to use strong encryption algorithms and key lengths to ensure the security of sensitive data.
Where can I find additional support for IPsec VPN encryption?
There are various resources available online for additional support on IPsec VPN encryption. Some of the popular resources include vendor-specific documentation, user forums, and online tutorials. It is recommended to refer to the documentation provided by the vendor or manufacturer of the IPsec VPN solution you are using for detailed guidance on encryption configuration and best practices.
