Importance of Data Security in Databases
Data security is a crucial aspect of databases as they store sensitive and confidential information that needs to be protected from unauthorized access, modification, or disclosure. Databases store a wide range of sensitive information such as personal identification details, financial information, medical records, and business data. Without proper security measures, this information can be accessed by unauthorized individuals and used for malicious purposes.
Oracle Database Encryption Basics
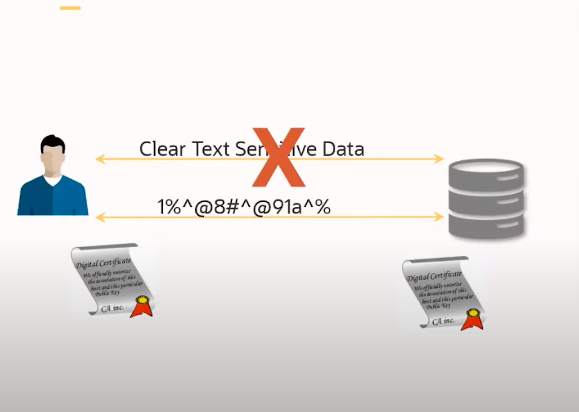
Oracle database encryption is a technique to protect sensitive data stored in an Oracle database. The encryption process involves converting plain text data into a coded format that can only be accessed by authorized users who have the decryption key. Oracle database encryption can be applied to various types of data, including columns, tablespaces, and backup files. The encryption process can be performed either at the application level or at the database level, depending on the specific requirements of the organization.
Preparing to Encrypt Column Data
To prepare for encrypting column data in an Oracle database, you should first identify the columns that need to be encrypted. This may involve reviewing the data stored in the database and assessing the security risks associated with certain types of data. Next, you should determine the appropriate encryption algorithm and key management strategy for your organization. Oracle provides several encryption algorithms, including AES, DES, and Triple DES.
Reviewing Oracle Database And Version
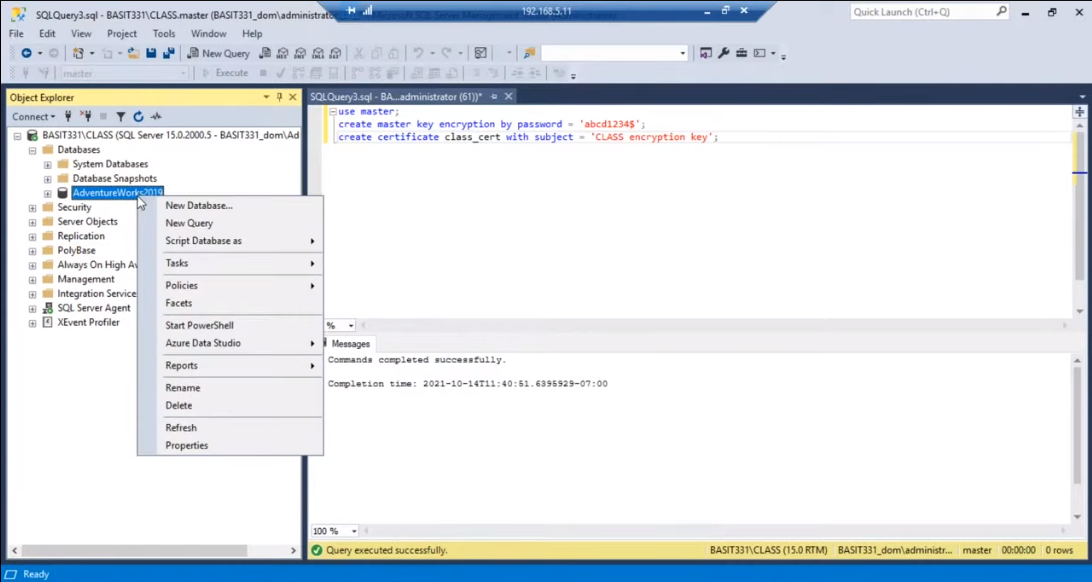
To review the Oracle database and version, you can use the following steps:
1. Connect to the Oracle database using SQL*Plus or any other database client tool.
2. Execute the following SQL command to check the version of the database:
SELECT * FROM v$version;
This will display the version of the Oracle database, including the release number and patch level.
3. To review the database structure, you can use the following SQL command:
SELECT * FROM dba_tables;
Identifying the Data to Be Encrypted
To identify the data to be encrypted, you should first determine the sensitivity level of the data. This can be done by conducting a data classification exercise to identify the different types of data and their respective levels of sensitivity. Once you have identified the sensitive data, you can then determine the appropriate encryption method to use based on the type of data and the level of protection required. For example, you may choose to use symmetric encryption for data at rest and asymmetric encryption for data in transit.
Configuring the Database for Encryption
Configuring a database for encryption involves several steps. First, you need to identify the specific data that needs to be encrypted. This could include sensitive customer information, financial data, or any other data that could be considered confidential. Next, you need to determine the appropriate encryption algorithm and key size based on the level of protection required for the identified data. This could involve using AES-256 encryption or another industry-standard encryption method.
Encrypting Column Data
Encrypting column data in a database involves several steps as well. First, you need to identify the specific columns that contain sensitive or confidential information. This could include columns that store credit card numbers, social security numbers, or other personal information. Next, you need to determine the appropriate encryption method and key size for the identified columns. This could involve using a symmetric key encryption method such as AES or a public key encryption method such as RSA.
Encryption Issues And Their Solutions
Encryption is an important tool to protect sensitive information, but it can also present some challenges. Here are some common encryption issues and their solutions:
1. Key management: One of the biggest challenges with encryption is managing the keys used to encrypt and decrypt data. If the keys are lost or stolen, the encrypted data may be inaccessible. To address this issue, organizations should implement a secure key management system that includes regular backups and secure storage.
2. Performance impact: Encryption can have a performance impact on systems, particularly if large amounts of data need to be encrypted or decrypted. To mitigate this issue, organizations should consider using hardware-based encryption solutions or optimizing their encryption algorithms.
3. Compatibility issues: Different encryption methods may not be compatible with each other, which can create interoperability issues. To address this issue, organizations should standardize on a single encryption method and ensure that all systems and applications are compatible with it.
4. User education: Encryption is only effective if users understand how to use it properly. Organizations should provide training and education to users on how to encrypt and decrypt data, as well as how to manage encryption keys.
By addressing these common encryption issues, organizations can ensure that their sensitive information remains secure and protected.
Decrypting Column Data
To decrypt column data, organizations should first determine the encryption method used to encrypt the data. Once the encryption method is identified, the organization should have the appropriate decryption key to decrypt the data. It is important to note that decrypting column data should only be done by authorized personnel who have been trained on how to properly handle sensitive information. Organizations should also ensure that the decrypted data is protected from unauthorized access and that the decryption process is properly documented for auditing purposes.
Decryption Issues And Their Solutions
Some common decryption issues that organizations may face include:
1. Lost decryption keys: If the decryption key is lost or unavailable, the data cannot be decrypted. To avoid this issue, organizations should securely store their decryption keys and have backup copies in case of loss or damage.
2. Incorrect decryption: If the decryption process is not done correctly, the data may be corrupted or lost. Organizations should ensure that authorized personnel are properly trained on the decryption process and that it is done carefully and accurately.
3. Unauthorized access: Decrypted data should only be accessible to authorized personnel. Organizations should implement access controls and other security measures to prevent unauthorized access to decrypted data.
4. Lack of documentation: Organizations should ensure that the decryption process is properly documented for auditing purposes. This includes documenting who accessed the decrypted data when it was accessed, and why it was accessed.
To avoid these issues, organizations should have clear policies and procedures in place for decrypting data, and should regularly review and update their security measures to ensure that they are effective and up-to-date.
Advanced Encryption Techniques
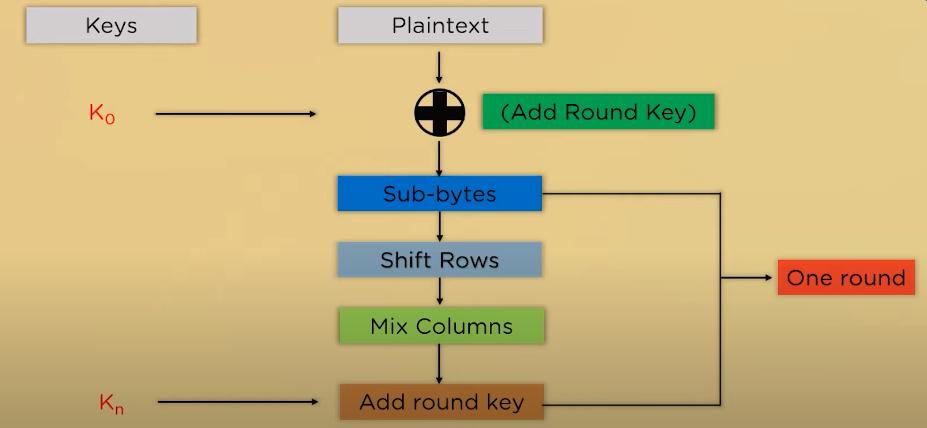
Advanced Encryption Techniques (AET) are a set of cryptographic methods that provide enhanced security and protection for sensitive data. AET includes algorithms such as AES (Advanced Encryption Standard), RSA (Rivest-Shamir-Adleman), and Elliptic Curve Cryptography (ECC), among others. AES is a symmetric key encryption algorithm that uses a block cypher to encrypt data in fixed-size blocks. RSA, on the other hand, is an asymmetric key encryption algorithm that uses a public and private key pair to encrypt and decrypt data. ECC is another asymmetric key encryption algorithm that is based on the mathematics of elliptic curves.
AET provides a higher level of security than traditional encryption methods, as it uses more complex algorithms and longer key lengths. However, AET can also be more resource-intensive and may require more processing power and memory to implement.
Overall, AET is an important tool for organizations that need to protect sensitive data from unauthorized access and ensure the confidentiality, integrity, and availability of their information assets.
Data Masking And Obfuscation
Data masking and obfuscation are techniques used to protect sensitive data by replacing it with fictitious data or altering it in a way that makes it unreadable or unusable to unauthorized users. This can include techniques such as encryption, tokenization, and data shuffling. Data masking involves replacing sensitive data with a fictitious equivalent that looks and behaves like the original data but does not reveal any sensitive information.
Best Practices for Oracle Database Encryption
- Creating an encryption policy
- Documenting encryption processes
- Regularly reviewing and updating encryption procedures
- Staying up-to-date with security patches and updates
Comparison with Other Database Encryption Methods
Encryption is an effective method for protecting sensitive data stored in databases. However, it is not the only method available. Tokenization and data shuffling are two other techniques that can be used to protect data. Tokenization involves replacing sensitive data with a non-sensitive token that still represents the original data. Data shuffling involves randomly shuffling data values in a way that still allows the data to be used for analysis but prevents sensitive information from being revealed.
Common Encryption Myths
Encryption is a powerful tool for protecting sensitive data, but there are also many myths and misconceptions surrounding it. Here are some common encryption myths:
1. Encryption is only for tech experts: While encryption can be complex, there are many user-friendly encryption tools available that are easy to use.
2. Encryption is only necessary for sensitive data: All data is potentially sensitive, and encrypting all data can help prevent data breaches and protect privacy.
3. Encryption is unbreakable: While encryption can be very strong, it is not completely unbreakable. However, strong encryption can make it very difficult and time-consuming for attackers to access encrypted data.
4. Encryption is only necessary for online data: Encryption is important for protecting data both online and offline, such as data stored on laptops or USB drives.
5. Encryption slows down data access: While encryption can add some processing overhead, modern encryption algorithms are very efficient and typically have a minimal impact on data access speeds.
Overall, encryption is an essential tool for protecting sensitive data and should be used whenever possible.
FAQs
How Does Oracle Database Encryption Work?
Oracle database encryption works by using encryption algorithms to convert plain text data into ciphertext that cannot be read without the appropriate decryption key. The encryption process is transparent to users and applications, and encrypted data can be stored in any database column or tablespace. Oracle offers several encryption options, including Transparent Data Encryption (TDE), which encrypts data at rest, and Oracle Data Safe, which provides a comprehensive set of security controls for managing sensitive data.
What Are The Benefits of Encrypting Database Data?
Encrypting database data provides several benefits, including:
1. Data protection: Encryption protects sensitive data from unauthorized access, theft, or loss. Even if an attacker gains access to the database, encrypted data is useless without the decryption key.
2. Compliance: Many regulatory standards require the protection of sensitive data, and encrypting database data can help organizations meet these requirements.
3. Confidentiality: Encryption ensures that only authorized users can access sensitive data, providing confidentiality and privacy.
What Are The Risks of Not Encrypting Database Data?
The risks of not encrypting database data include:
1. Data Breaches: Without encryption, sensitive data stored in a database is vulnerable to theft or unauthorized access. This can result in a data breach, which can damage an organization’s reputation and lead to legal and financial consequences.
2. Non-Compliance: Not encrypting sensitive data can result in non-compliance with regulatory standards, which can lead to fines and legal penalties.
What Types of Data Should Be Encrypted?
Sensitive data that should be encrypted includes personally identifiable information (PII) such as names, addresses, social security numbers, credit card numbers, and other financial information. Additionally, any confidential business information such as trade secrets, intellectual property, and other proprietary information should also be encrypted. It’s important to assess the specific needs and risks of your organization to determine what types of data should be encrypted.
How Do I Know Which Encryption Algorithm To Use?
Choosing the right encryption algorithm depends on various factors such as the level of security required, the type of data being encrypted, and the resources available for encryption and decryption. Some commonly used encryption algorithms include Advanced Encryption Standard (AES), RSA, and Blowfish. It’s important to consult with security experts and conduct a thorough risk assessment to determine the most appropriate encryption algorithm for your organization’s needs.
How Can I Ensure That My Encryption Keys Are Secure?
There are several best practices you can follow to ensure that your encryption keys are secure:
1. Use strong passwords: Choose strong passwords for your encryption keys and ensure that they are not easily guessable. Avoid using common words or phrases, and use a combination of uppercase and lowercase letters, numbers, and special characters.
2. Use key management systems: Implement a key management system to securely store and manage your encryption keys. This will help prevent unauthorized access and ensure that your keys are only accessible to authorized persons.
How Do I Monitor And Audit Encrypted Data In My Oracle Database?
To monitor and audit encrypted data in your Oracle database, you can use Oracle’s Database Vault and Audit Vault. Database Vault allows you to restrict access to sensitive data and control who can view or modify it. It also provides auditing capabilities to track all database activity, including access to encrypted data. Audit Vault collects audit data from multiple sources, including Database Vault, and provides centralized reporting and analysis of audit data. By using both of these tools together, you can ensure that your encrypted data is secure.
Can I Encrypt My Entire Database At Once?
Yes, you can encrypt your entire Database at once using Oracle Transparent Data Encryption (TDE). TDE is a feature of Oracle Database that enables you to encrypt sensitive data stored in tables, tablespaces, and backups. TDE uses industry-standard Advanced Encryption Standard (AES) encryption to protect your data. With TDE, you can encrypt the entire database or specific columns in tables.
How Does Database Encryption Affect Performance?
Database encryption can have a performance impact, as the encryption and decryption processes require additional processing power and resources. However, the impact on performance can vary depending on factors such as the size of the database, the type of encryption used, and the hardware configuration of the system. It is recommended to perform performance testing before implementing database encryption to ensure that the impact on performance is acceptable for your specific use case. Additionally, using hardware encryption accelerators or optimizing database configuration settings can help mitigate performance impacts.
Conclusion
In conclusion, encryption is a critical tool for safeguarding sensitive data, both online and offline. It is not only necessary for online data but also for data stored on laptops, USB drives, and other devices. While encryption may add some processing overhead, modern encryption algorithms are highly efficient and have minimal impact on data access speeds. As a writing assistant, I highly recommend the use of encryption whenever possible to ensure the security and confidentiality of your data.
