Introduction
Symmetric key encryption is a type of encryption where the same key is used for both data encryption and decryption. This means the sender and the receiver must have the same key to encrypt and decrypt messages. Symmetric key encryption is widely used in various applications such as secure communication, data storage, and authentication. However, some potential drawbacks and vulnerabilities associated with symmetric key encryption should be considered before implementing it. In this comprehensive guide, we will explore the dark side of symmetric key encryption and provide insights on mitigating these risks. One of the main drawbacks of symmetric key encryption is that the key must be shared between the sender and the receiver. If the key is compromised, all encrypted messages can be easily decrypted. Therefore, ensuring the key is kept secure and changed regularly is important.
Data security is paramount today, where data breaches and cyber attacks are becoming increasingly common. Protecting sensitive information such as personal data, financial information, and intellectual property from unauthorized access, theft, or modification is essential. A data breach can result in severe consequences such as loss of reputation, financial loss, legal liabilities, and even the collapse of a business. Therefore, it is crucial to implement robust security measures such as encryption, access controls, and regular security audits to ensure data security.
The article discusses the importance of protecting sensitive information from unauthorized access, theft, or modification. It emphasizes the severe consequences of a data breach, including loss of reputation, financial loss, legal liabilities, and even business collapse. The article suggests implementing robust security measures such as encryption, access controls, and regular security audits to ensure data security.
Understanding Symmetric Key Encryption
Symmetric key encryption is a type of encryption where the same key is used for both data encryption and decryption. This means that the sender and receiver of the data must have the same key to access the information. The process involves converting plain text into cipher text using the key and then converting the cipher text back to plain text using the same key. Symmetric key encryption is often used when data needs to be transmitted securely over a network or stored securely on a device. It is considered a fast and efficient method of encryption, as the same key is used for both encryption and decryption, which reduces processing time. However, it poses a security risk, as the key must be shared between the sender and receiver. If the key is compromised, unauthorized parties can easily access the data.
It is recommended to use strong and complex keys to mitigate this risk and to change them regularly. Additionally, additional security measures such as access controls and regular security audits can enhance data security.
How Does Symmetric Key Encryption Work?
Symmetric Key Encryption uses a single key to encrypt and decrypt data. The sender and receiver of the data must both have access to the same key to communicate securely. The process involves converting the original data into an unreadable format using the key and then returning it to its original form using the same key. This ensures that only the intended recipient can read the data, as they are the only ones with access to the key.
Downside of Using A Symmetric Key To Encrypt Data
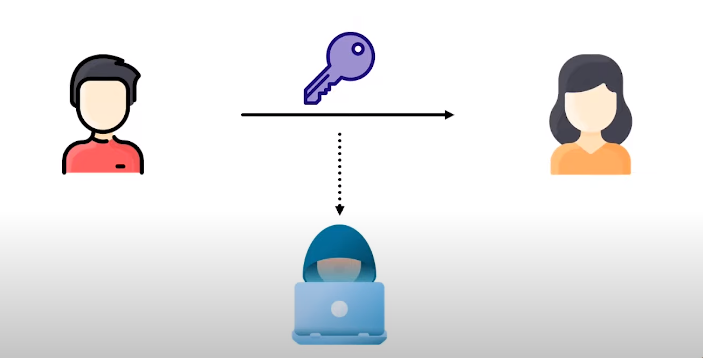
The downside to using a symmetric key to encrypt data is that it requires the key to be shared between the sender and the receiver. This means that if the key is compromised, unauthorized parties can easily access the data. Additionally, managing and distributing the key can be challenging, especially if multiple parties need access to the encrypted data. As a result, symmetric key encryption is not always the best choice for situations where data security is a top priority.
Disadvantages Of Symmetric Key Encryption
There are several disadvantages of symmetric key encryption, including:
1. Key distribution: The biggest disadvantage of symmetric key encryption is securely distributing the key to the recipient. The system’s security is compromised if the key falls into the wrong hands.
2. Lack of scalability: Symmetric key encryption is not scalable for large networks, as each pair of users would require a unique key. This can become unmanageable in a large organization with many users.
3. Limited security: Symmetric key encryption is vulnerable to brute-force attacks, where an attacker tries every possible key to decrypt the message. With enough computing power, an attacker can eventually crack the key and access the data.
4. Lack of authenticity: Symmetric key encryption does not provide any means of verifying the sender’s authenticity. An attacker can intercept the message, decrypt it, make changes to the data, and re-encrypt it with the same key, without the recipient knowing.
5. Key management: Symmetric key encryption requires careful management to ensure the system’s security. Keys must be changed regularly and stored securely to prevent unauthorized access.
Encryption Methods That Uses A Single Key To Encrypt And Decrypt Data
Symmetric key encryption is the encryption method that uses a single key to encrypt and decrypt data.
Lack Of Confidentiality
It is important to know that symmetric key encryption may not provide the same level of confidentiality as other encryption methods. This is because the same key is used for both encryption and decryption, which means an attacker would have access to all the encrypted data if the key is compromised. Additionally, symmetric key encryption does not protect against interception or eavesdropping, as anyone with access to the key can still intercept and read the encrypted data. Therefore, it is important to carefully consider the level of security needed for any given situation and choose an encryption method that provides the appropriate level of protection.
Vulnerability To Brute Force Attacks
Symmetric key encryption is vulnerable to brute force attacks, where an attacker tries every possible key until the correct one is found. The encryption’s strength depends on the key’s length, but even with a long key, a determined attacker can eventually crack the encryption. This is why using strong, unique keys and changing them regularly is important. Additionally, using a key management system can help to protect against brute force attacks by securely storing and rotating keys.
Key Management Issues
Key management is a critical aspect of encryption and data security. One of the biggest issues with key management is the risk of key loss or theft. If a key is lost or stolen, it can compromise the security of the encrypted data. To mitigate this risk, it is important to have proper key backup and recovery procedures in place. Another issue with key management is key distribution. If keys are not distributed securely, they can be intercepted and compromised. It is important to use secure channels for key distribution, such as encrypted communication channels or physical delivery of keys.
Finally, key rotation is an important aspect of key management. Over time, keys can become compromised or weakened, so it is important to regularly rotate keys to maintain the security of the encrypted data. However, key rotation can also be challenging, as it requires updating all systems and applications that use the old key with the new one. A key management system can help automate this process and ensure that all systems use the most up-to-date key.
Key Distribution Challenges
Key distribution can also pose challenges in key management. Ensuring that the right keys are distributed to the right individuals or systems can be complex, especially in large organizations with numerous users and systems. Additionally, securely transmitting keys to their intended recipients can also be a challenge, as intercepted or stolen keys can compromise the security of the encrypted data. Key management systems can help to streamline the key distribution process and ensure that keys are securely distributed to their intended recipients.
Alternatives To Symmetric Key Encryption
While symmetric key encryption is a widely used and effective method of securing data, alternative encryption methods are also available. One such method is asymmetric key encryption, also known as public-key encryption. This method uses a pair of keys, a public, and a private key, to encrypt and decrypt data. The public key can be freely shared with anyone, while the private key is kept secret. This allows for secure communication between parties without needing a pre-shared key. Another alternative is homomorphic encryption, which allows for computation on encrypted data without the need for decryption, thus preserving the privacy of the data. However, homomorphic encryption is less practical and computationally intensive than symmetric or asymmetric key encryption. There are several alternatives to symmetric key encryption, including:
1. Asymmetric key encryption: This type of encryption uses two keys, one for encryption and one for decryption. The keys are mathematically related, but it is computationally infeasible to derive one from the other. Asymmetric key encryption provides a means of verifying the authenticity of the sender.
2. Hash functions: Hash functions are one-way functions that take an input and produce a fixed-size output. The output, or hash, is unique to the input, and any change will result in a different hash. Hash functions are used for message authentication and digital signatures.
3. Digital signatures: Digital signatures are used to ensure the authenticity and integrity of a message. A digital signature is created by encrypting a hash of the message with the sender’s private key. The recipient can verify the signature by decrypting the hash with the sender’s public key.
4. Public key infrastructure (PKI): PKI manages digital certificates and public keys. It provides a means of verifying the sender’s authenticity and encrypting messages securely. PKI is used in many applications, including secure email, online banking, and e-commerce.
Implementation Of Alternatives
The implementation of encryption alternatives depends on the specific use case and security requirements. For example, symmetric key encryption is commonly used when speed and efficiency are important, such as encrypting large amounts of data in real time. Asymmetric key encryption is often used for secure communication between parties who do not have a pre-shared key, such as in online banking or e-commerce transactions. Homomorphic encryption, while still in its early stages of development, has the potential to revolutionize the way data is processed and analyzed in fields such as healthcare and finance. However, it is currently more suited for specialized use cases and may not be practical for general-purpose encryption.
The implementation of encryption alternatives also requires careful consideration of key management and distribution and the potential impact on system performance and usability. It is important to work with experienced security professionals to ensure that the chosen encryption method meets the organization’s specific needs and provides the necessary level of protection for sensitive data.
Best Practices For Encryption
Encrypting sensitive data is an important step in protecting it from unauthorized access. Here are some best practices to keep in mind when implementing encryption:
1. Choose a strong encryption algorithm: Use encryption algorithms that are widely accepted and have been thoroughly vetted by the security community.
2. Use appropriate key lengths: Longer ones generally provide stronger encryption but may impact system performance. Choose key lengths that balance security and performance requirements.
3. Implement proper key management: Keys should be protected and stored securely and rotated periodically.
4. Use secure key distribution: Keys should only be distributed securely to authorized parties.
5. Consider the impact on system performance: Encryption may impact system performance, so it is important to test and benchmark performance before implementation.
6. Train users on proper use: Users should be trained on the proper use of encryption tools and the importance of protecting encryption keys.
7. Regularly review and update encryption practices: Encryption technology and best practices are constantly evolving, so it is important to review and update encryption practices to ensure they remain effective.
Conclusion
Encryption is crucial for protecting sensitive information from unauthorized access. To ensure the effective use of encryption, organizations should consider using strong encryption algorithms, secure key management practices, and regular system performance testing and benchmarking. Additionally, user training and regular review and updating of encryption practices are essential for maintaining the security of sensitive information.
Data security should be a top priority for businesses and individuals in today’s digital age. The consequences of a data breach can be devastating, both financially and in terms of reputation. Therefore, organizations and individuals must take proactive steps to protect sensitive information. This includes implementing strong encryption algorithms, secure key management practices, and regular system performance testing and benchmarking. Providing user training and regularly reviewing and updating encryption practices is also important. Businesses and individuals can safeguard sensitive information by prioritizing data security and protecting themselves from potential harm.
Frequently Asked Questions (FAQs)
How Can The Problems Of Symmetric Key Encryption Be Mitigated?
One solution is using asymmetric encryption for key exchange, and then using symmetric encryption for the actual data transfer. This method, often referred to as hybrid encryption, combines the speed of symmetric encryption with the safety of asymmetric key exchange. Additionally, effective key management systems and security practices, like regular key changes, can mitigate some of the risks associated with symmetric encryption.
Is Symmetric Key Encryption Obsolete Due To Its Drawbacks?
No, symmetric key encryption is not obsolete despite its drawbacks. It is still widely used because it’s faster and requires fewer computational resources compared to asymmetric encryption. It’s particularly useful for encrypting large amounts of data. The key is to understand its limitations and use it in a way that mitigates potential security risks.
What Happens When A Symmetric Key Is Lost Or Stolen?
If a symmetric key is lost, the encrypted data cannot be decrypted. It’s as if the data is lost as well. If the key is stolen or intercepted by a malicious entity, they can decrypt any data encrypted with that key. This is why it’s so important to keep symmetric keys secure and use secure methods for their distribution.
How Does Key Rotation Help Mitigate The Risks Of Symmetric Key Encryption?
Key rotation is the practice of regularly changing encryption keys. The idea is that even if a key is compromised, it won’t be useful to an attacker for very long because it will soon be replaced by a new key. Regular key rotation can therefore limit the potential damage of a key compromise.
Is Symmetric Encryption Suitable For Cloud Storage?
Symmetric encryption is often used in cloud storage to protect data at rest. The main challenge is securely managing and storing the encryption keys. Cloud service providers often offer key management services that handle this, though they come with their own security considerations.
