Introduction
Data security is a vital aspect of any organization, and one of the most important components of data security is encryption. Encryption is changing data into a code that can only be decrypted by sanctioned parties. When data is in transit, it is particularly vulnerable to interception and theft, so it is critical to use proper encryption to protect it. This article will discuss the practices for securing data in transit through proper encryption techniques.
Understanding Data Encryption
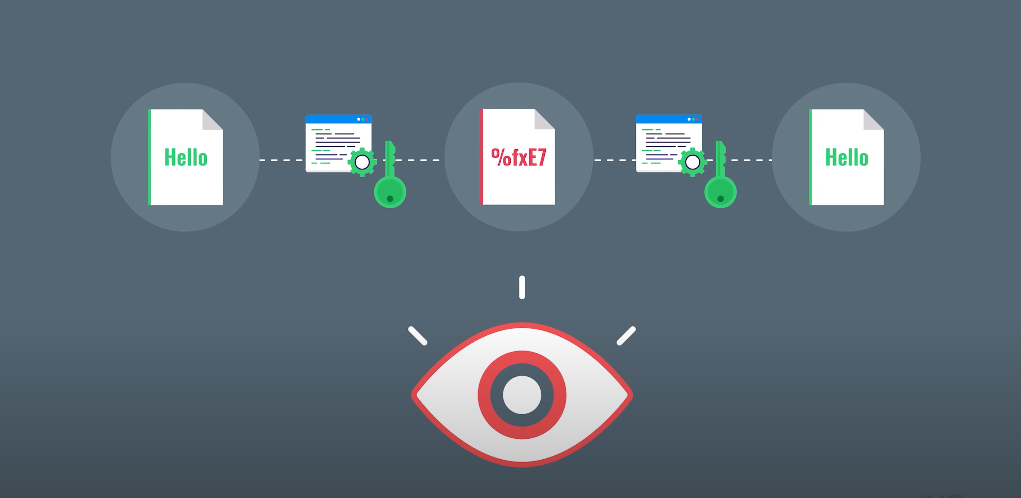
Data encryption is a method of converting plain text into cipher text that authorized parties can only read. Encryption algorithms use intricate mathematical formulas to scramble the data, making it unreadable to anybody who does not have the decryption key. There are two main types of encryption: symmetric encryption and asymmetric encryption. Symmetric encryption uses only a key to encrypt and decrypt data. This means the sender and receiver must have the same key to access the data.
On the other hand, asymmetric encryption uses two keys: a public key and a private key. The public key encrypts the data, while the private key decrypts it. This means anyone can encrypt the data using the public key, but only the recipient with the private key can decrypt it.
Best Practices For Encrypting Data In Transit
A secure communication protocol like HTTPS, SSH, or TLS is the best way to ensure data is properly encrypted while in transit. These protocols use encryption algorithms to protect data as it travels between two endpoints, a web browser, and a server. It’s also important to confirm the authenticity of the endpoint you are communicating with to ensure you are not sending sensitive information to an attacker. Additionally, strong passwords and two-factor authentication can further enhance the security of your data in transit.
Utilizing Https
HTTPS (Hypertext Transfer Protocol Secure) is a widely accepted best practice for encrypting data in transit. It uses SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocols to encrypt the transmitted data between the sender and receiver. This ensures that the data is protected from interception or modification by unauthorized parties. HTTPS is commonly used for secure communication over the Internet, such as online banking, e-commerce transactions, and email services. It is important to note that HTTPS only encrypts the data in transit and does not guarantee the security of the data at rest or on the server. Therefore, it is important to implement other security measures such as strong passwords, firewalls, and regular software updates to ensure the system’s overall security.
Implementing SSL/TLS
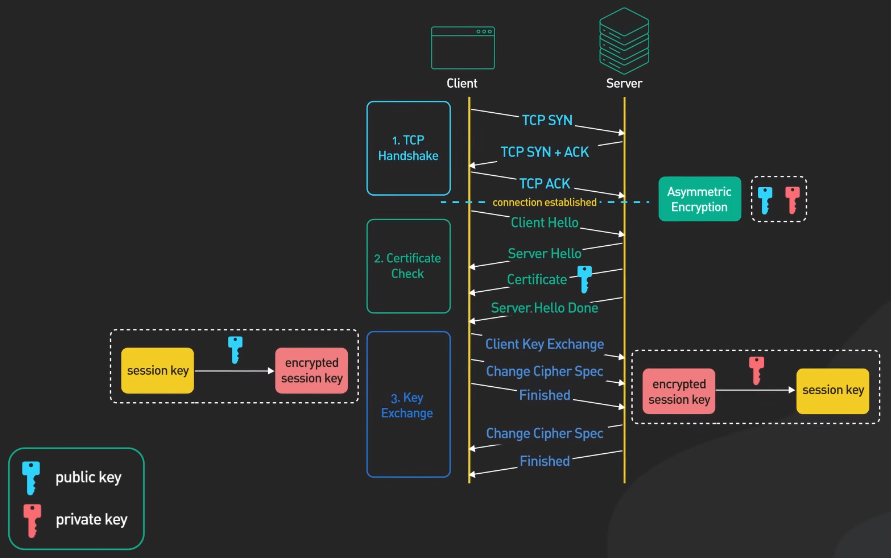
Implementing SSL/TLS is a crucial step in securing communication over the internet. SSL/TLS is a protocol that encrypts data in transit between a client and a server. This encryption ensures that sensitive information like passwords, credit card numbers, and personal data are protected from interception and unauthorized access. To implement SSL/TLS, you must get an SSL/TLS certificate from a reliable certificate authority (CA). This certificate verifies the server’s identity and establishes a protected connection between the user and the server.
Once you have obtained the SSL/TLS certificate, you must configure your web server to use HTTPS instead of HTTP. This involves configuring the web server to use the SSL/TLS certificate and redirecting all HTTP traffic to HTTPS.
It is also important to regularly update your SSL/TLS certificate to ensure that it is valid and up-to-date. In addition, you should configure your web server to use the latest and most secure SSL/TLS protocols and cipher suites.
Utilizing VPNs
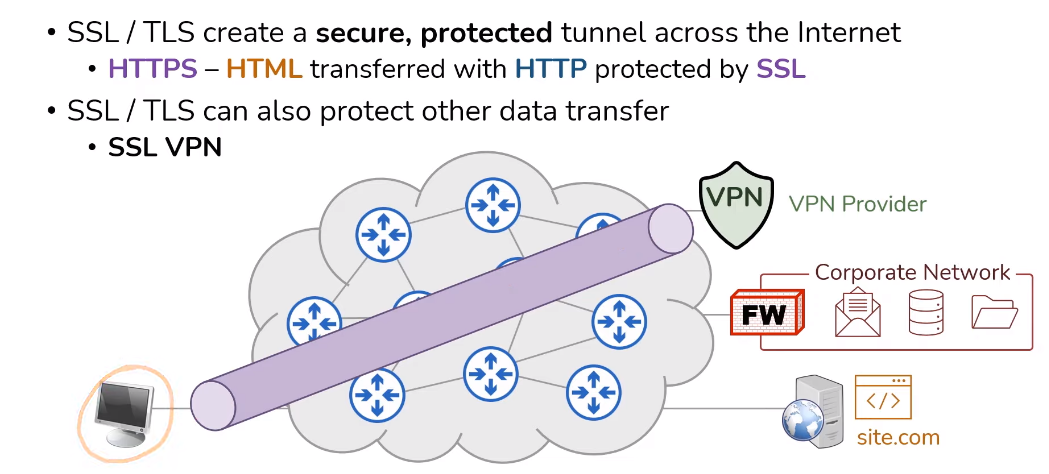
Virtual Private Networks (VPNs) are popular for enhancing online security and privacy. VPNs establish a secure, encrypted connection between the user’s device and a remote server anywhere. This connection creates a private “tunnel” through which all internet traffic is routed, effectively masking the user’s IP address and encrypting their data. VPNs are useful for accessing sensitive information or conducting online transactions using public Wi-Fi networks.
Implementing IPsec
IPsec (Internet Protocol Security) is a protocol suite for securing internet communications. It provides authentication, integrity, and confidentiality to IP packets. Implementing IPsec can enhance online security and privacy by encrypting all traffic between two endpoints, preventing unauthorized access and eavesdropping.
To implement IPsec, you need to do the following:
1. Choose an IPsec protocol suite: There are two commonly used IPsec protocol suites: Authentication Header (AH) and Encapsulating Security Payload (ESP). AH provides authentication and integrity but not confidentiality, while ESP provides authentication, integrity, and confidentiality.
2. Configure the IPsec policy: This involves defining the security parameters and policies for the IPsec connection, such as the encryption algorithm, authentication method, and key exchange protocol.
3. Set up the key exchange: IPsec requires a secure method of exchanging keys between the two endpoints. This can be done using a pre-shared key, digital certificates, or a key exchange protocol such as Internet Key Exchange (IKE).
4. Configure the IPsec tunnel: This involves setting up the IPsec tunnel between the two endpoints, which will encrypt and decrypt all traffic passing through it.
5. Test and troubleshoot: Once the IPsec connection is configured, it is important to test and troubleshoot the connection to ensure it works correctly and securely.
Utilizing SSH
SSH, or Secure Shell, is a network protocol that permits secure remote access to a server or computer. It encrypts all data transmitted between the users and server, ensuring that sensitive information such as usernames, passwords, and data are protected from eavesdropping and tampering.
To utilize SSH, you must have an SSH client installed on your computer and a server or computer that supports SSH. You will also need to have login credentials for the server or computer.
To connect to the server or computer via SSH, you must open your SSH client and enter the server’s IP address, domain name, and login credentials. Once connected, you can access a command-line interface to execute commands and perform tasks on the remote server or computer.
It is important to ensure that your SSH client and server are configured securely to prevent unauthorized access and protect your data. Additionally, it is recommended to use a strong password or key-based authentication to enhance security further.
Implementing SFTP
To implement SFTP (Secure File Transfer Protocol), you can follow these steps:
1. Install an SFTP server on the remote computer or server you want to transfer files to/from. Several options are available, such as OpenSSH, vsftpd, and ProFTPD.
2. Configure the SFTP server to use secure authentication methods, such as password or key-based authentication, and restrict access to authorized users only.
3. Install an SFTP client on your local computer, such as WinSCP, FileZilla, or Cyberduck.
4. Configure the SFTP client to connect to the remote SFTP server using the appropriate hostname or IP address, port number, and authentication method.
5. Transfer files securely between your local computer and the remote SFTP server using the SFTP client’s file transfer features.
By implementing SFTP, you can ensure your file transfers are encrypted and secure, reducing the risk of data breaches or unauthorized access to sensitive information. You discuss setting up and using an SFTP client for secure file transfers.
Implementing FTPS
To implement FTPS for secure file transfers, you will need to follow these steps:
1. Obtain an SSL/TLS certificate for your FTP server. This certificate will encrypt the data being transferred between the client and server.
2. Install and configure an FTP server software that supports FTPS. Some popular options include FileZilla Server, ProFTPD, and Pure-FTPd.
3. Configure the FTP server to use the SSL/TLS certificate you obtained in Step 1. This will ensure that all data transfers are encrypted.
4. Obtain an FTPS client software. Some popular options include FileZilla, WinSCP, and Cyberduck.
5. Configure the FTPS client with the FTP server’s hostname, IP address, port number, and authentication method.
6. Use the FTPS client’s file transfer features to securely transfer files between the local computer and the remote FTP server.
By implementing FTPS, you can ensure your file transfers are encrypted and secure, reducing the risk of data breaches or unauthorized access to sensitive information.
Utilizing DNSSEC
DNSSEC is a security protocol that augments a defense layer to the Domain Name System (DNS). It digitally signs DNS records to ensure their authenticity and prevent DNS spoofing attacks. To utilize DNSSEC, you can follow these steps:
1. Check if your domain name registrar supports DNSSEC. If it does, enable DNSSEC for your domain.
2. Generate a DNSSEC key pair and sign your DNS records with the private key.
3. Publish the DNSSEC public key as a DNS record in your domain’s DNS zone file.
4. Set up your DNS resolver to validate DNSSEC signatures when resolving DNS queries.
By implementing DNSSEC, you can ensure your website visitors connect to the correct server and are not redirected to a malicious site. It also helps to prevent DNS cache poisoning attacks, where an attacker can employ the DNS cache to redirect users to a malicious site.
Implementing PGP
To implement PGP (Pretty Good Privacy), you can follow these steps:
1. Install PGP software on your computer, such as GnuPG or Kleopatra.
2. Generate a PGP key pair consisting of public and private keys. Keep your private key secure, and never share it with anyone.
3. Share your public key with the people you want to communicate securely. You can publish it on a key server or send it to them directly.
4. Use your PGP software to encrypt your messages using the recipient’s public key. Only the recipient with the matching private key can decrypt the message.
5. If you receive an encrypted message, use your PGP software to decrypt it using your private key.
6. You can also use PGP to digitally sign your messages, which verifies that you sent the message and has not been altered in transit. To do this, use your private key to sign the message, and the recipient can use your public key to verify the signature. Remember to keep your private key secure and never share it with anyone.
Additionally, verify the authenticity of the recipient’s public key before using it to encrypt your messages. PGP is a powerful tool for secure communication, but it needs careful attention to detail to ensure its effectiveness.
Factors To Consider In Choosing An Encryption Method
There are various factors to consider when choosing an encryption method, including the level of security needed, compatibility with existing systems, ease of implementation and use, and cost. The level of security required will depend on the sensitivity of the transmitted data. For highly sensitive data, strong encryption methods such as AES-256 or RSA may be necessary, while for less sensitive data, simpler encryption methods may suffice.
Compatibility with existing systems is also important. It’s important to choose an encryption method compatible with the systems and devices that will be used to transmit and receive the data.
Ease of implementation and use is another important factor to consider. Encryption methods that are easy to implement and use will be more likely to be adopted and used consistently.
Finally, cost is also a consideration. Some encryption methods may be more expensive than others, and it’s important to weigh the cost against the level of security provided and the other factors mentioned above.
What Encryption Protocols Should I Use For Data In Transit?
Several encryption protocols can be used to protect data in transit, depending on your organization’s specific needs and requirements. Some common encryption protocols include:
1. Transport Layer Security (TLS) – This widely used protocol delivers secure internet communication between servers and clients. It is commonly used for email, web browsing, and other online transactions.
2. Secure Sockets Layer (SSL) – This predecessor to TLS is still used in some cases. It provides secure communication between servers and clients but is less secure than TLS and is being phased out.
3. Internet Protocol Security (IPsec) – This protocol secures internet communication at the network layer. It can create a virtual private network (VPN) between two networks or between a remote user and a network.
4. Secure Shell (SSH) – This protocol is used for secure remote access to servers. It provides encrypted communication between the client and server and can be used for file transfers, remote command execution, and other tasks.
5. Pretty Good Privacy (PGP) – This protocol is used for secure email communication. It provides end-to-end encryption for email messages and can be used to sign and verify the authenticity of messages.
6. Virtual Private Network (VPN) – This technology generates a secure, encrypted connection between two networks or between a remote user and a network. It can be used to protect data in transit and to provide remote access to network resources.
What Encryption Tools And Services Are Available?
There are a variety of encryption tools and services available that organizations can use to protect their sensitive data. Some popular options include:
1. Encryption software: This software is designed to encrypt data at rest, in transit, or both. Examples include VeraCrypt, BitLocker, and FileVault.
2. Virtual Private Networks (VPNs): A VPN is a service that encrypts all internet traffic between a user’s device and a remote server, making it difficult for anybody to intercept or eavesdrop on the data.
3. Cloud encryption services: Cloud encryption services provide an additional layer of security for data stored in the cloud. Examples include Amazon Web Services (AWS) Key Management Service (KMS) and Microsoft Azure Key Vault.
4. Hardware encryption devices: These devices encrypt data stored on external hard drives, USB drives, and other portable storage devices. Examples include IronKey and Kingston DataTraveler.
It’s important to choose the right encryption tool or service based on the specific needs of your organization and the type of data you are looking to protect.
Conclusion
In summary, organizations should prioritize protecting personal information by implementing best practices for encryption. This includes using strong encryption algorithms, such as AES and RSA, and ensuring that encryption tools and services comply with recognized encryption standards. Additionally, organizations should properly implement and configure encryption to provide the necessary level of protection for personal information. By following these practices, organizations can help safeguard personal information and protect against data breaches and cyber-attacks.
Data security is of utmost importance in today’s digital age, as the amount of personal and sensitive information being stored and transmitted online continues to increase. Data breaches and cyber attacks can have serious consequences, including financial losses, damage to reputation, and legal liabilities. In some cases, data breaches can even result in identity theft and fraud, which can have long-lasting effects on individuals. By implementing strong data security measures, organizations can help prevent these negative outcomes and ensure that personal information is kept safe and secure.
Frequently Asked Questions (FAQs)
What Is Data Encryption?
Data encryption is changing plain text or data into a coded arrangement that can only be read by approved parties with the key to decode the information. Encryption is a broadly used method for securing sensitive data, such as financial information, personal identification details, and confidential business data. It helps to protect data from illegal access, theft, and cyber attacks.
What Is The Difference Between Data At Rest And Data In Transit?
Data at rest refers to data stored or saved on a device or server, while data in transit refers to data transmitted or sent over a network, such as email or file transfers. The key difference between the two is that data at rest is already encrypted and stored securely, while data in transit is more vulnerable to interception and attack. Therefore, additional security measures, such as encryption and secure protocols, are often used to protect data in transit.
