Hashing in Ensuring Data Integrity And Authenticity
Hashing is a powerful tool used in computer science and cryptography to ensure the integrity and authenticity of data transmission across networks. At its core, hashing is a process of generating a fixed-length string of characters from a given input data. This string, known as the hash value or message digest, is unique to the input data, and any changes made to the input data will result in a different hash value. Hashing is commonly used in digital signatures, password verification, and data transmission protocols.
Understanding Hashing Basics
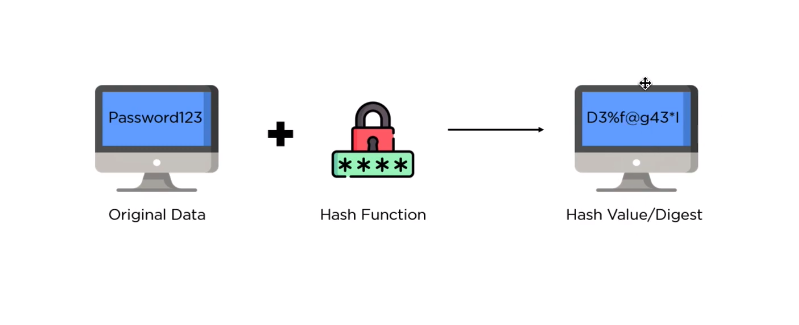
Hashing is a fundamental concept in computer science and cybersecurity. It involves the use of mathematical algorithms to convert input data into a fixed-length string of characters, known as a hash value or message digest. The resulting hash value is unique to the input data, and any changes made to the input data will result in a different hash value. Hashing is widely used in various applications, including digital signatures, password verification, and data transmission protocols.
How Hashing Functions Work?
Hashing functions work by taking an input message and processing it through a mathematical algorithm to produce a fixed-length hash value. The algorithm used is designed to be one-way, meaning it is difficult to reverse engineer the input message from the hash value. The resulting hash value is typically represented as a hexadecimal string. The process of hashing involves three main steps: initialization, processing, and output. During initialization, the hashing function sets up its internal state and prepares to process the input message.
Key Properties of Hash Functions
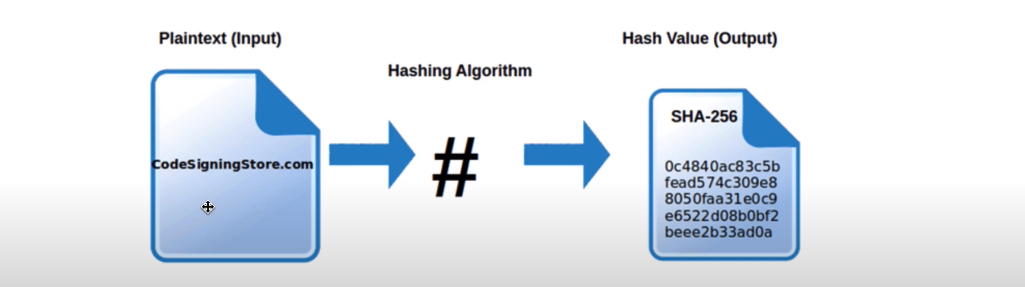
1. Deterministic: For a given input message, the hash function will always produce the same output hash value.
2. Fixed-length output: The output hash value is of a fixed length, regardless of the size of the input message.
3. One-way: It is difficult to reverse engineer the input message from the hash value.
4. Uniformity: A small change in the input message should result in a significant change in the output hash value.
Role of Hashing in Data Transmission
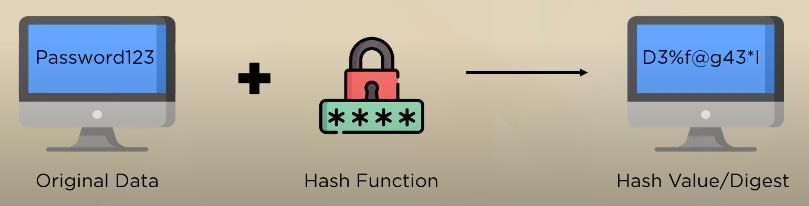
Hashing plays a crucial role in data transmission as it provides a way to ensure data integrity and authenticity. By generating a hash value for a message before transmission, the recipient can verify that the message has not been tampered with during transmission. This is because any alteration to the message would result in a different hash value. Hashing can also be used to verify the authenticity of a message by comparing the received hash value with a pre-shared hash value.
Hash Functions: Types and Algorithms
Hash functions are mathematical algorithms that convert input data of arbitrary size into a fixed-size output known as a hash value. There are various types of hash functions, including:
1. Cryptographic hash functions: These are designed to be secure and are used for data authentication and integrity. Examples include SHA-256 and MD5.
2. Non-cryptographic hash functions: These are simpler and faster than cryptographic hash functions and are used for tasks such as indexing and searching data. Examples include MurmurHash and JenkinsHash.
3. Keyed hash functions: These use a secret key to generate a hash value, providing an additional layer of security. Examples include HMAC and KMAC. (https://kidsrkids.com)
The choice of hash function depends on the specific use case and the level of security required. It is important to choose a hash function that is resistant to attacks such as collision attacks, where two different inputs produce the same hash value.
Hashing in Network Protocols
Hashing is also commonly used in network protocols for various purposes such as authentication, integrity verification, and load balancing. For example, in the Transport Layer Security (TLS) protocol, a hash function is used to verify the integrity of the messages exchanged between the client and server. Similarly, in the Internet Protocol Security (IPsec) protocol, a hash function is used to authenticate the packets and protect them from tampering.
Digital Signatures: Enhancing Data Transmission Security
Digital signatures are another important tool for enhancing data transmission security. A digital signature is a mathematical technique used to verify the authenticity and integrity of a digital message or document. It is essentially an electronic equivalent of a handwritten signature. Digital signatures are created using a combination of public key cryptography and hash functions. The sender of a message or document uses their private key to generate a unique digital signature based on the content of the message or document.
Using Hash Functions For Digital Signatures
Hash functions are an essential component of digital signatures. They are used to create a unique digital fingerprint of the message or document being signed. This fingerprint is then encrypted using the sender’s private key to create the digital signature. Hash functions are one-way mathematical functions that take an input (the message or document) and produce a fixed-length output (the hash value). The hash value is unique to the input, meaning that any change to the input will result in a different hash value.
Public Key Infrastructure (PKI) And Certificates
Public key infrastructure (PKI) is a system that uses public key cryptography to enable secure communication over the Internet. PKI involves the use of digital certificates, which are electronic documents that verify the identity of the sender and receiver of a message or document. Certificates are issued by trusted third-party organizations called certificate authorities (CAs). They contain information about the identity of the certificate holder, including their public key. When a user wants to communicate securely with another user, they can use the recipient’s public
Verifying Data Integrity With Digital Signatures
Digital signatures are another important aspect of PKI. They are used to verify the authenticity and integrity of digital documents or messages. A digital signature is created using the sender’s private key and is attached to the document or message. The recipient can then use the sender’s public key to verify that the signature is authentic and that the document or message has not been tampered with. Digital signatures are important in ensuring that sensitive information is not altered or modified during transmission.
Hashing and Password Storage
Hashing is a process that converts data of any size into a fixed-size output, which is typically a string of characters. This output is known as a hash value or message digest. Hashing is commonly used to verify the integrity of data, such as passwords, by comparing the hash value of the original data with the hash value of the data that is being verified.III. Password storage is another area where hashing is commonly used.
Hashing Passwords for Secure Storage
Hashing passwords is a crucial step in ensuring the secure storage of user credentials. When a user creates a password, it is hashed and the resulting hash value is stored in a database. When the user logs in, the password they enter is hashed and compared to the stored hash value. If the two hashes match, the user is granted access. However, not all hashing algorithms are created equal. Some are more vulnerable to attacks than others.
Salting And The Prevention of Rainbow Table Attacks
Salting is another important technique used in the secure storage of user credentials. It involves adding a random string of characters, known as a salt, to the user’s password before hashing it. This makes it much more difficult for attackers to use precomputed tables, known as rainbow tables, to crack the password. Rainbow tables are essentially large databases of precomputed hash values for a range of possible passwords.
Best Practices for Password Hashing
In addition to salting, several other best practices for password hashing can help prevent attacks. These include using a strong and secure hashing algorithm, such as bcrypt or scrypt, using a unique salt for each password, and using a sufficiently long and complex password policy. It is also important to regularly update and rotate passwords, and to use multi-factor authentication whenever possible. By following these best practices, organizations can significantly reduce the risk of password-related attacks and protect their users’ sensitive information.
Implementing Hashing in Network Applications
When implementing hashing in network applications, it is important to ensure that the hashing algorithm used is strong and secure. Bcrypt and scrypt are commonly recommended for this purpose. Additionally, a unique salt should be used for each password to further enhance security. It is also important to consider the length and complexity of the password policy. Longer passwords with a mix of upper and lowercase letters, numbers, and symbols are generally more secure. Password policies should also be regularly updated and rotated to prevent attackers from gaining access.
Integrating Hash Functions Into Network Architectures
Integrating hash functions into network architectures is an important step in securing sensitive information. Hash functions can be used to verify the integrity of data transmitted over a network, ensuring that it has not been tampered with or altered in any way. Additionally, hash functions can be used to securely store passwords and other sensitive information. One common approach is to use a salted hash function to store passwords.
Ensuring Secure Data Transmission in Web Applications
To ensure secure data transmission in web applications, it is important to use HTTPS protocol instead of HTTP. HTTPS encrypts the data being transmitted between the client and server, making it more difficult for attackers to intercept and read the information. Additionally, web developers should implement secure coding practices and use frameworks that have built-in security features. It is also important to regularly update software and security patches to address any vulnerabilities that may arise.
FAQs (Frequently Asked Questions)
What is hashing, and how does it contribute to secure data transmission?
Hashing is the process of converting a plain text message or data into a fixed length value, known as a hash. This hash is unique to the original message or data, and any change to the message or data will result in a different hash value. Hashing is commonly used in secure data transmission to ensure the integrity of the data being transmitted. By comparing the hash of the received data with the expected hash, the recipient can verify that the data has not been tampered with during transmission.
Are there different types of hash functions used for data transmission?
Yes, there are different types of hash functions used for data transmission. Some of the commonly used hash functions include MD5, SHA-1, SHA-2, and SHA-3. Each of these hash functions has its unique algorithm for generating hash values. The choice of hash function depends on the specific requirements of the application, such as the level of security needed and the size of the data being transmitted.
Can hashing protect against data tampering or corruption?
Yes, hashing can protect against data tampering or corruption. When data is hashed, a unique hash value is generated based on the contents of the data. If any part of the data is changed, even a single bit, the hash value will also change. This makes it possible to detect any unauthorized changes to the data during transmission. By comparing the hash value of the received data with the hash value of the original data, it is possible to verify that the data has not been tampered with.
How can hash functions be implemented in network applications?
Hash functions can be implemented in network applications by incorporating them into the data transmission process. For example, a sender can generate a hash value for the data they want to transmit and send both the data and the hash value to the receiver. The receiver can then generate their hash value for the received data and compare it with the hash value sent by the sender. If the two hash values match, the receiver can be confident that the data has not been tampered with during transmission.
What are the performance considerations when using hashing?
There are several performance considerations when using hashing:
1. Hashing can be computationally intensive, especially for large amounts of data. This means that the time it takes to generate a hash value can be significant, which can impact the overall performance of the system.
2. Hashing can also require significant amounts of memory, especially when dealing with large data sets. This can impact the performance of the system if there is not enough memory available to store the hash values.
