Importance of Data Security
Data security is crucial in today’s digital age. With the increasing amount of sensitive information being stored and shared online, it is important to ensure that this data is kept secure and protected from unauthorized access. It helps to safeguard sensitive information such as personal details, financial records, and confidential business data. This information can be used for identity theft, fraud, and other malicious activities if it falls into the wrong hands.
Overview of USB Drives

USB drives, also known as flash drives or thumb drives, are small, portable storage devices that can be used to transfer data between computers or store files. They are often used as a backup for important files or to transfer files between computers. USB drives come in various sizes and storage capacities, ranging from a few gigabytes to several terabytes. They are compatible with most computers and devices that have a USB port.
Risks Associated With Storing Sensitive Data on USB Drives
While USB drives are convenient for transferring and storing data, there are some risks associated with storing sensitive data on them:
1. Loss or theft: USB drives are small and portable, which makes them easy to lose or steal. If a USB drive containing sensitive data falls into the wrong hands, it could be a serious security breach.
2. Malware: USB drives can be infected with malware, which can then infect the computer it is plugged into. This can result in data loss or theft, as well as other security issues.
3. Data corruption: USB drives can sometimes become corrupted, resulting in data loss or corruption. This can be especially problematic if the data is sensitive or important.
4. Lack of encryption: Many USB drives do not come with encryption software, which means that sensitive data stored on them is not protected. This can make it easier for hackers or other unauthorized users to access the data.
To mitigate these risks, it is important to use encryption software, keep USB drives in a secure location, and regularly back up important data to other storage devices.
Understanding Encryption
Encryption is the process of converting data into a code to prevent unauthorized access. This is done by using an encryption algorithm, which is a mathematical formula that converts the data into a code that can only be deciphered with a key or password. There are two main types of encryption: symmetric encryption and asymmetric encryption. Symmetric encryption uses the same key to encrypt and decrypt the data, while asymmetric encryption uses two different keys – one to encrypt the data and another to decrypt it.
How Encryption Works?

Encryption is a process of converting plain text or data into a coded format to prevent unauthorized access. This process is done by using an encryption algorithm, which is a mathematical formula that converts the data into a code that can only be deciphered with a key or password. Symmetric encryption uses the same key to encrypt and decrypt the data. This means that the sender and receiver must have the same key to communicate securely.
Types of Encryption
There are two main types of encryption: symmetric encryption and asymmetric encryption.
Symmetric Encryption:
In symmetric encryption, the same key is used to encrypt and decrypt
the data. This means that both the sender and receiver must have the same key to communicate securely. Symmetric encryption is typically faster than asymmetric encryption, but it is less secure because if the key is compromised, all the encrypted data can be easily decrypted.
In symmetric encryption, the same key is used to encrypt and decrypt the data. This means that both the sender and receiver must have the same key to communicate securely. Symmetric encryption is typically faster than asymmetric encryption, but it is less secure because if the key is compromised, all the encrypted data can be easily decrypted.
Asymmetric Encryption:
In asymmetric encryption, two keys are used: a public key and a private key. The public key can be shared with anyone, but the private key must be kept secret. When someone wants to send a message to the owner of the public key, they encrypt the message using the public key. The owner of the public key can then decrypt the message using the private key. Asymmetric encryption is more secure than symmetric encryption because even if the public key is compromised, the private key is still secret. However, asymmetric encryption is slower than symmetric encryption.
Factors to Consider When Selecting An Encryption Method
When selecting an encryption method, there are several factors to consider.
1. Security: The most important factor to consider is the level of security offered by the encryption method. The encryption method should be strong enough to protect the data from unauthorized access.
2. Speed: The speed at which the encryption and decryption process takes place is another important factor. Asymmetric encryption is slower than symmetric encryption, so it may not be suitable for applications that require fast processing.
3. Key management: The management of keys is critical in encryption. The encryption method should have a reliable key management system that ensures the keys are kept secure and accessible only to authorized users.
4. Compatibility: The encryption method should be compatible with the systems and applications in use. It should be able to integrate with existing systems without causing any compatibility issues.
5. Complexity: The complexity of the encryption method should be considered. The more complex the encryption method, the more difficult it may be to implement and manage.
6. Cost: The cost of the encryption method should also be considered. Some encryption methods may be expensive to implement and maintain, so it is important to weigh the cost against the benefits.
Differences Between Encryption Methods
There are several differences between encryption methods, such as:
1. Symmetric vs. Asymmetric: Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses different keys for each process.
2. Block vs. Stream: Block encryption divides the data into blocks and encrypts each block separately, while stream encryption encrypts the data bit by bit.
3. Hashing vs. Encryption: Hashing is a one-way process that converts data into a fixed-length string.
Compatibility With Different Operating Systems And Devices
When choosing an encryption method, it’s important to consider compatibility with different operating systems and devices. Some encryption methods may not be compatible with certain systems or devices, which could cause issues with data transfer or access. It’s important to research and test encryption methods to ensure compatibility before implementing them in your system. Additionally, it’s important to consider the level of security needed for your specific use case and choose an encryption method that meets those requirements.
Preparing Your USB Drive for Encryption
To prepare your USB drive for encryption, follow these steps:
1. Back up any important data on the USB drive to another location.
2. Format the USB drive to remove any existing data and ensure a clean slate for encryption.
3. Choose an encryption method that is compatible with your operating system and devices. Some popular options include BitLocker (for Windows), FileVault (for Mac), and VeraCrypt (for both Windows and Mac).
4. Install and set up the encryption software on your computer.
5. Connect the USB drive to your computer and select it as the target for encryption.
6. Follow the prompts to encrypt the USB drive. This may involve setting a password or passphrase, choosing the level of encryption, and configuring any additional security settings.
7. Once the encryption process is complete, test the USB drive to ensure that it is working properly and that you can access the encrypted data.
By following these steps, you can ensure that your USB drive is properly encrypted and secure for storing sensitive data.
How to Encrypt Your USB Drive?
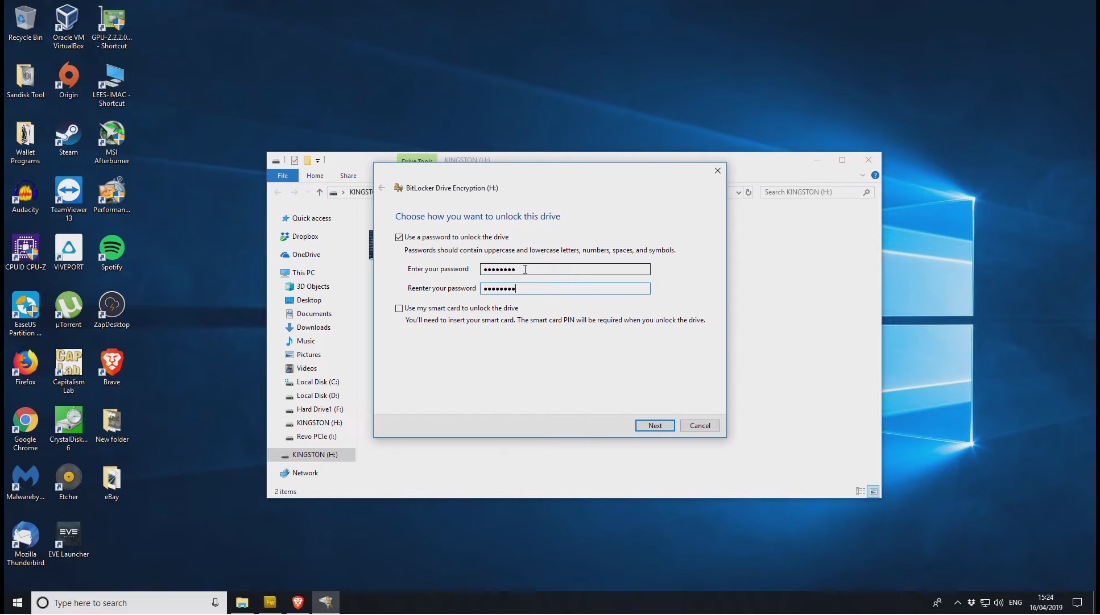
To encrypt your USB drive, follow these steps:
1. Insert your USB drive into your computer’s USB port.
2. Open File Explorer and right-click on the USB drive.
3. Select “Turn on BitLocker” from the context menu.
4. Choose how you want to unlock the drive. You can use a password or a smart card if your computer has a smart card reader.
5. Choose where you want to save the recovery key. This key will allow you to access your data if you forget your password or lose your smart card. You can save it to a file, print it, or store it in your Microsoft account. It’s important to keep this key in a safe place.
Third-Party Encryption Software
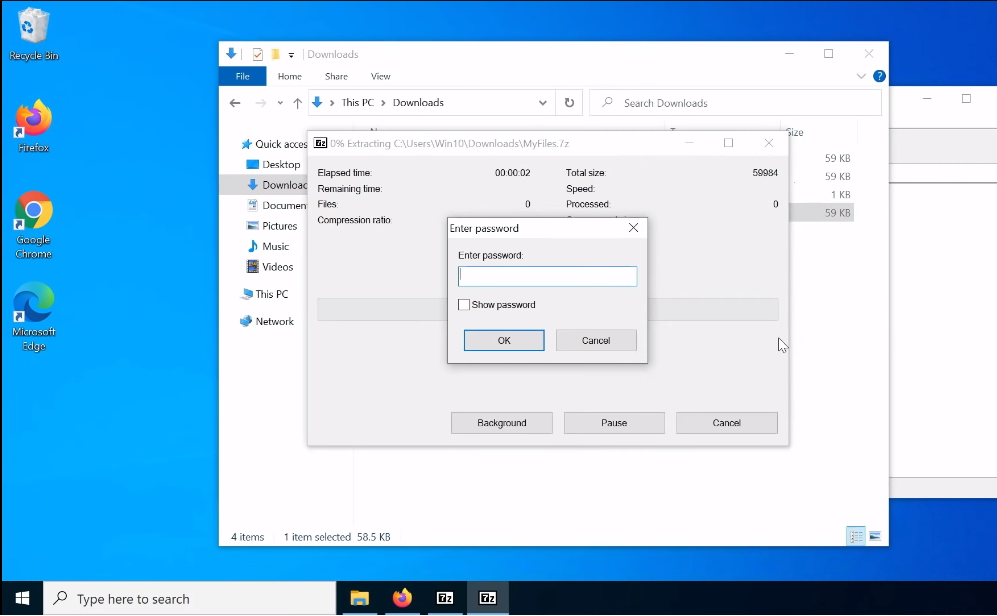
If you prefer to use third-party encryption software, there are many options available. Some popular choices include VeraCrypt, AxCrypt, and 7-Zip. Before selecting software, make sure to research and compare different options to find one that meets your needs. Once you have chosen your software, follow the instructions provided by the software to encrypt your USB drive. Make sure to keep any necessary passwords or keys in a safe place in case you need them in the future.
Mounting And Unmounting Encrypted USB Drive
To access the files on your encrypted USB drive, you will need to mount it. This process varies depending on the software you are using but typically involves entering a password or key to unlock the encrypted files. Once the drive is mounted, you can access the files as you would with any other USB drive. When you are finished using the drive, it is important to properly unmount it to ensure that your files remain secure.
Troubleshooting Common Encryption Issues
- Forgotten passwords
- Data loss or corruption
- Compatibility issues
- Drive failure
Best Practices for Securely Using Encrypted USB Drives
- Keeping your encryption software up to date
- Using strong passwords and keys
- Avoiding untrusted networks
- Regularly backing up your data
Conclusion
It’s important to keep in mind that encrypted USB drives can be a valuable tool for protecting sensitive data, but it’s also important to use them correctly to avoid potential issues. In addition to the tips you provided, it’s also a good idea to store your encrypted USB drive in a secure location when not in use and to avoid sharing it with others unless necessary. By following these best practices, you can help ensure that your data remains secure and protected.
FAQs
What Is The Difference Between Encryption And Password Protection?
Encryption and password protection are two different methods of securing data. Encryption is the process of converting plain text into a code or cypher that is unreadable without the correct decryption key. This means that even if someone gains access to the encrypted data, they won’t be able to read it without the key.
Password protection, on the other hand, is a method of restricting access to a file or device by requiring a password to be entered before access is granted.
Can I Encrypt Only Certain Files on My USB Drive?
Yes, you can encrypt only certain files on your USB drive. Many encryption software programs allow you to select specific files or folders to encrypt while leaving others unencrypted. You can also choose to encrypt the entire USB drive if you prefer. It’s important to note that once you have encrypted a file or folder, you will need the correct decryption key to access it. So, make sure to keep your decryption key safe and secure.
Can I Use My Encrypted USB Drive on Multiple Devices?
Yes, you can use your encrypted USB drive on multiple devices as long as the devices have the necessary software to decrypt the files. However, it’s important to keep in mind that if you are using the USB drive on a public or shared computer, there is a risk that someone could access your files if they have access to the decryption key. It’s always best to use caution when using an encrypted USB drive on multiple devices and to make sure that you are using it in a secure environment.
