Introduction
Data security is of utmost importance to individuals and organizations alike. In today’s digital age, an increasing amount of sensitive information is stored electronically, making it vulnerable to cyber threats. A data breach can result in significant financial losses, reputational damage, and legal liabilities.
Organizations must comply with laws such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). Non-compliance can lead to severe penalties for organizations failing to protect their customers’ data. Financial details, intellectual property, trade secrets, and personally identifiable information are all valuable assets that must be kept confidential. Cybercriminals aim to steal this information for financial gain or other malicious purposes.
Understanding Data Security
Definition Of Data Security
Data security refers to protecting sensitive information from unauthorized access or theft. This may include personal information such as names, addresses, social security numbers or financial details like credit card numbers or bank account credentials. Properly securing data involves implementing various technical controls such as firewalls, encryption protocols, and intrusion detection systems.
Different Types Of Data
Personal Data

Personal data refers to any information that can be used to identify an individual. This includes names, addresses, social security numbers, and more. Personal data is often the target of cybercriminals who want to use it for identity theft or other nefarious purposes.
Financial Data

Financial data includes credit card numbers, bank account information, and transaction history. This data type is also highly sought by hackers who want to steal money or commit fraud. Businesses and individuals alike need to take steps to protect their financial data from unauthorized access.
Sensitive Business Information

This data type can give competitors an unfair advantage if it falls into the wrong hands. Businesses must take extra precautions when safeguarding this type of information by implementing security measures such as firewalls and encryption protocols.
The Importance Of Data Classification
Data classification helps organizations prioritize their security measures and allocate resources effectively. It also ensures that sensitive information is given the appropriate level of protection, thus reducing the risk of data breaches.
Classifying data allows businesses to comply with regulatory requirements such as GDPR and HIPAA, which mandate that organizations adequately protect sensitive information. It also helps companies to manage access rights by ensuring that only authorized individuals have access to critical data. This way, they can prevent insider threats and unauthorized access.
Identifying Security Threats
Overview Of Common Security Threats
- Phishing Scams: These involve an attacker sending fraudulent emails or messages to deceive individuals into divulging sensitive information such as usernames, passwords, and account details.
- Malware Attacks: This is when malicious software is installed on an individual’s computer without their knowledge or consent. The malware can then steal sensitive information or damage the system.
- Insider Threats: These occur when an employee intentionally or unintentionally accesses data that they do not have permission to view, copy, or share outside of the organization.
Analysis Of The Causes Of Security Threats
Inadequate Access Control Measures: When an organization fails to limit access to sensitive data or enforce good password policies, it leaves the door open for unauthorized individuals to enter its networks and systems. This can lead to data theft, manipulation, and compromise.
Outdated Software And Hardware: As technology continues to evolve, so do the methods used by cybercriminals to exploit vulnerabilities. Using outdated systems increases the likelihood of these vulnerabilities being discovered and exploited by attackers. Organizations must ensure that they are regularly updating their software and hardware components with patches and upgrades.
Human Error: Employees who lack knowledge about cybersecurity practices or fail to follow established protocols can inadvertently expose sensitive data or provide unauthorized access points for attackers.
Implementing Data Security Measures
Implementing Physical Security Measures
Physical security measures can be implemented in various ways, including surveillance cameras, access control systems, and secure storage areas. Surveillance cameras can be useful in deterring unauthorized physical access to sensitive areas by capturing footage that can be used as evidence in case of a breach.
Access control systems such as biometric scanners, key cards or PIN codes restrict entry to authorized personnel only. This ensures that only employees with the required clearance levels have access to sensitive data stored on computers or servers within the restricted area. Secure storage areas provide a physically safe location for storing confidential information.
Securing Data In Transit
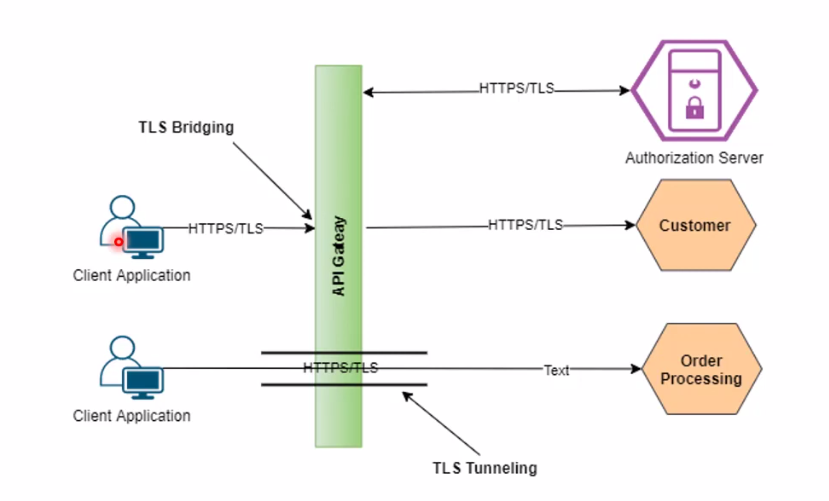
Data in transit refers to the information that is moving from one location to another over a network. This can be email, file transfers, or any other type of communication between computers or devices. To ensure that data is protected during this process, encryption protocols like SSL/TLS and SSH can be used. These protocols encrypt the information being transferred so that it cannot be intercepted or read by unauthorized parties.
VPNs create a secure connection between two devices over the internet, allowing for encrypted communication and ensuring that sensitive data remains confidential. Additionally, firewalls can provide an added layer of protection by monitoring incoming and outgoing traffic and blocking any unauthorized access.
Securing Data At Rest
Data at rest refers to information that is stored on a device or system, such as in a database, hard drive, or server.
One way to ensure the security of data at rest is through encryption. Encryption involves converting plain text into an unreadable format that can only be deciphered with a decryption key. This makes it difficult for unauthorized users to access and exploit the data. Additionally, regularly backing up your encrypted data ensures its safety if storage devices are compromised.
Another approach is implementing access controls and authentication protocols. These measures limit who has access to sensitive information and require proper identification from authorized users before granting them permission to view the data. This helps prevent internal attacks where employees attempt to steal or misuse company information.
Importance Of Access Controls
Access controls help to limit access to sensitive information to only those who need it. This can be achieved through various means such as passwords, biometric verification systems, or smart cards.
There are different types of access controls that can be implemented depending on the level of security required. For example, some systems may use simple password authentication while others may require multi-factor authentication for greater protection. Additionally, access control policies should be reviewed regularly and updated as needed to ensure that they remain effective.
Access controls also reduce the risk of data breaches by preventing unauthorized access attempts. By limiting the number of people with access to sensitive information, businesses can minimize their exposure to potential cyber-attacks or internal threats.
Securing data backups
Data backups safeguard against accidental deletion, ransomware attacks, or hardware failures. However, if your backup isn’t secured properly, it could be compromised like the original data. Choose an encryption method that matches the sensitivity of your data. This will ensure that only authorized personnel can access the backup.
Storing them in multiple locations. If one storage location is compromised, you still have other backup copies available. It’s also recommended that you keep at least one copy of the backup offsite so that it’s not affected by any physical damage or natural disasters.
Ensuring Data Privacy
Understanding Data Privacy Regulations
As a business owner or part of an organization that collects, stores and uses data, it’s important to understand the various data privacy regulations applicable to your industry. Data protection laws such as the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) impose strict rules on how organizations should collect, store and process personal data.
Organizations must clearly state why they’re collecting this information and for what purposes it will be used. Additionally, businesses must have processes in place to secure this information from potential breaches, accidental exposure or loss.
Implementing Data Privacy Policies And Procedures
Data privacy policies should be created to specify how data should be collected, used, processed, stored and deleted. It is recommended that organizations conduct regular audits on their existing data privacy practices to identify areas where they can improve.
When implementing new procedures, ensure that all employees are trained in the importance of data protection and understand the purpose of the newly created policies. Data protection officers (DPOs) play a critical role in ensuring compliance with these policies and should be appointed by companies handling large volumes of personal information.
Best Practices For Protecting Sensitive Data
It’s important to establish who has access to sensitive data. Limiting access to data to only those who need it will help reduce the risk of breaches. Regular password updates and two-factor authentication can also mitigate unauthorized access.
Implementing encryption protocols is essential for keeping sensitive data secure. Encrypting data in transit and at rest provides an additional layer of protection against theft or interception. It’s important to use strong encryption algorithms that are updated regularly.
A disaster recovery plan can prevent potential loss of sensitive data due to system crashes or cyber-attacks. A backup system should be implemented that is both offsite and offline for maximum protection from threats like ransomware attacks.
Importance Of Transparency In Data Handling
Transparency in data handling means that companies are open and honest with their customers about what data they collect, why they collect it, and how it will be used. This transparency builds trust between businesses and their clients, as well as helps protect against potential breaches or misuse of personal information.
Moreover, transparent practices give consumers more control over their personal information. If people understand how their data is being used, they can make informed decisions about whether or not to share it with a particular company.
Educating Employees
Importance Of Employee Training
Employees not trained in proper security protocols can unknowingly put confidential information at risk, leading to potential data breaches and loss of trust from clients. Training programs should include topics such as password management, email phishing scams, and data encryption.
Elements Of An Effective Security Training Program
One of the most important aspects of ensuring data security in any organization is to have an effective security training program. Such a program should include several elements, including regular training sessions that cover topics such as password management, phishing attacks, and safe browsing practices. The training should also cover how to recognize potential security threats and what to do when they are identified.
Employees should be encouraged to participate actively in the program, ask questions, and provide feedback on their experiences with various types of cybersecurity incidents. They should also be given access to resources such as online courses or articles that can help them stay up-to-date on emerging threats and best practices for securing data.
Raising Awareness Of Security Threats
To ensure that your data remains secure, it is essential to raise awareness of these threats and educate employees on how to avoid them.
Raise awareness through training programs that teach employees about cybersecurity best practices. These programs can cover topics such as password management, avoiding suspicious links and emails, and recognizing potential security risks. By providing regular training sessions for employees at all levels of the organization, you can create a culture of security awareness that helps prevent costly data breaches.
Conducting Regular Security Audits
Security audits help identify potential vulnerabilities in the system, ensuring that businesses can take proactive measures to protect their data from hackers and other cyber threats.
To conduct a comprehensive security audit, it’s crucial to define the scope of the audit, including the systems, applications, and infrastructure involved in storing or accessing sensitive information. The next step is to perform a risk assessment by identifying potential risks and evaluating their likelihood of occurrence.
Once you have identified potential risks, implement appropriate control measures to mitigate them. These control measures may include updating software patches regularly, strengthening password policies, limiting access privileges based on job roles or functions, and encrypting sensitive data at rest and in transit.
Responding To Security Breaches
When it comes to responding to security breaches, speed is of the essence. The longer a breach goes unnoticed or unaddressed, the more damage it can inflict and the more time hackers have to continue their attack. Therefore, having a solid incident response plan in place is crucial. This plan should include clear protocols for identifying and containing breaches as soon as they occur, as well as a step-by-step process for investigating and remedying any damage that has been done.
Another critical component of responding to security breaches is communication. Companies must be transparent with customers about what has happened and what steps are being taken to remedy the situation. Failure to do so can lead to a loss of trust among customers and long-term reputational damage for the organization. Additionally, companies must communicate internally with employees about what has happened so that everyone understands their role in the response effort and how they can help prevent future incidents from occurring.
Staying Up-To-Date With The Latest Threats And Solutions
Cybercriminals are constantly developing new techniques to breach security systems, which makes staying current on the latest trends critical in protecting sensitive data. Regularly reviewing security reports and attending industry conferences can be a valuable source of information for identifying and mitigating potential cybersecurity risks.
Implementing software updates and patches for all applications, operating systems, and devices can also help prevent cyberattacks. These updates often contain bug fixes or enhanced security features that address known vulnerabilities in previous versions. Additionally, utilizing advanced antivirus and anti-malware software can detect and remove malicious code from your computer or network.
Technology is evolving rapidly; thus, it’s crucial to remain vigilant about potential cybersecurity risks while keeping up-to-date with the latest threats and solutions. Implementing these measures can significantly reduce the risk of cyberattacks on your organization’s sensitive data.
FAQs
What Are The Causes Of Security Breaches?
Weak passwords. Many people use simple or easily guessable passwords, making it easy for hackers to gain access to sensitive information.
Out-of-date software and systems. When software and systems are not regularly updated, they become vulnerable to attack.
Phishing scams. These scams involve tricking individuals into providing login credentials or other sensitive information through fake emails or websites.
What Are Some Physical Security Measures That Can Be Implemented?
Restrict access to the premises. This can be done by installing CCTV cameras at all entry and exit points and using security personnel to vet visitors before granting them access. Additionally, it is important to have a logbook where visitors provide their details, including name, ID number, and reason for visiting.
Implement biometric authentication systems. These systems use unique physical characteristics such as fingerprints or facial recognition to grant access only to authorized individuals. This eliminates the need for keys or passwords, which can easily be stolen or hacked.
What Is Access Control?
Access control is a security measure that restricts authorised individuals’ access to data or resources. This method safeguards against unauthorized access or theft of sensitive information, which can have significant consequences for individuals and organizations. Access control systems can be physical (e.g., locks, keys, badges) or digital (e.g., passwords, biometrics)
What Is An Incident Response Plan?
An incident response plan is a written document that outlines an organisation’s actions in response to a potential security breach or another critical event. It serves as a blueprint for the company’s IT and security teams, outlining who is responsible for what during an incident and providing specific steps that should be taken to minimize damage and return systems to normal operation.
Conclusion
Securing data is crucial for both individuals and organizations. With the increasing rate of cyber attacks, it’s essential to take proactive measures to protect sensitive information. Businesses must implement robust security policies and protocols to safeguard their data from cybercriminals. This includes using encryption technology, regularly updating software and operating systems, conducting employee training on security awareness, and developing incident response plans.
