Introduction
A denial of service (DOS) attack refers to a type of cyber attack that is aimed at rendering a website or network unavailable by overwhelming it with traffic. During such an attack, the attacker sends huge amounts of data requests to the targeted system or network, causing it to crash or become unresponsive. In most cases, DOS attacks are carried out as an act of sabotage or revenge against a particular company or individual.
While DOS attacks can be devastating and cause significant damage to the affected party, they are not always considered data security breaches. This is because such attacks do not typically result in unauthorized access to sensitive information stored within the target system. Nonetheless, some DOS attacks may be used as a smokescreen for more sinister activities like stealing passwords and other confidential data from unsuspecting victims.
Types Of Denial Of Service Attacks
Basic DOS Attack
One of the most basic types is the Basic DOS Attack, which involves flooding a targeted system with traffic until it becomes overwhelmed and unable to respond to legitimate requests.
Distributed Denial of Service Attack (DDOS)
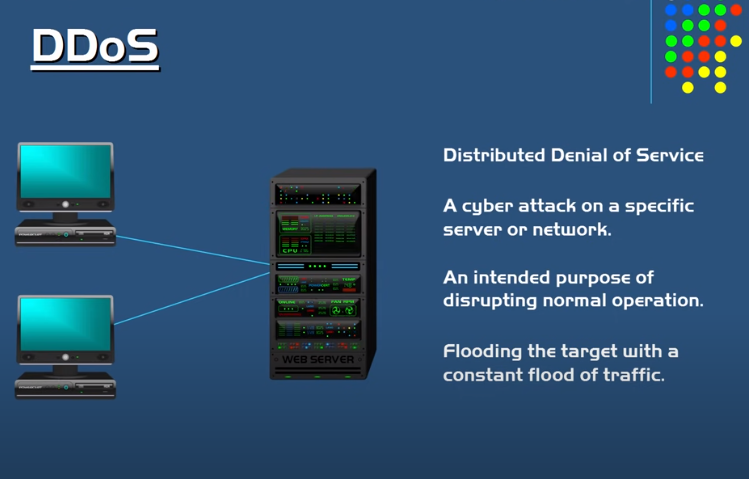
A Distributed Denial of Service (DDOS) attack is a type of cyberattack that targets a website or network by overwhelming it with traffic from multiple sources.
While DDOS attacks do not typically involve the theft or exposure of sensitive data, they can still be considered a data security breach. This is because denial-of-service attacks can disrupt business operations and cause financial losses, which can impact customer trust and confidence in the affected organization.
Application Layer DOS Attack
Application layer DOS attacks are specifically targeted at the application layer of the OSI model, which is where communication between software applications takes place. In an application layer DOS attack, attackers exploit vulnerabilities in the target’s application layer protocols and services to disrupt service availability.
Effects of Denial of Service Attacks
Financial Losses
During a DOS attack, a hacker sends a large volume of traffic to a website or server, overwhelming its capacity and causing it to crash. As a result, the targeted website or server becomes unavailable to users. This can lead to lost revenue from customers who are unable to access the website or use its services.
Reputational Damage
Denial of service (DOS) attacks can have an impact on a company’s reputation, even if they do not result in any data being stolen. A DOS attack involves overwhelming a network or website with traffic, causing it to crash and become unavailable to users.
Customers may view a business as unreliable if its website crashes due to a DOS attack. This can lead to negative reviews and comments online, which could potentially harm the company’s reputation. Additionally, customers may be hesitant to trust the business with their personal information if they perceive that it has weak security measures in place.
Data Security Breaches
Definition of a Data Security Breach
A data security breach refers to any situation where an unauthorized individual or entity gains access to sensitive information. This could happen through hacking, social engineering, or even the physical theft of devices that contain the data. A key aspect of a breach is that it involves information that should have been kept private and secure.
Types of Data Security Breaches
There are various types of data security breaches that do involve the unauthorized access or theft of sensitive information. These include phishing attacks, malware infections, insider threats, and physical theft of devices containing confidential data. Each type of breach poses unique risks and requires specific measures to prevent and mitigate its impact.
Consequences of a Data Security Breach
One of the main consequences of a data security breach is the loss or theft of sensitive information, including personal identification numbers (PINs), social security numbers, credit card information, and other confidential data. This loss can lead to identity theft or financial fraud.
In addition to financial losses, companies can also suffer reputational damage from a data security breach. Customers may lose trust in the company’s ability to protect their information, leading to lost business and negative publicity. Legal action may also be taken against a company if it is found that it did not take proper measures to secure its customers’ information.
Comparing DOS Attacks and Data Security Breaches
Differences Between A DOS Attack and a Data Security Breach
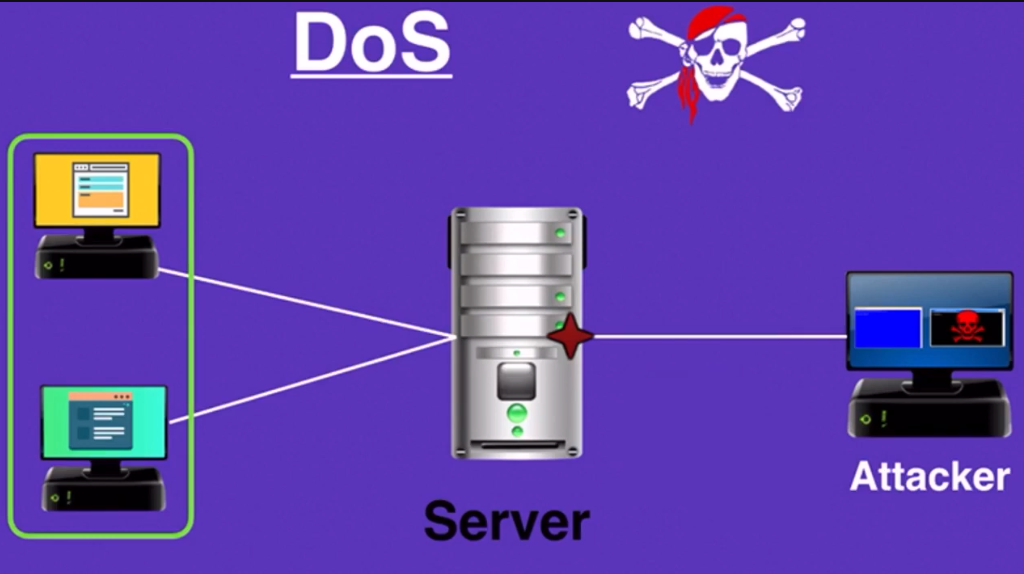
A DOS attack is an attempt to make a website or network unavailable to its intended users by overwhelming the target with traffic from multiple sources. This type of attack does not necessarily involve accessing confidential information or stealing data. Instead, it aims to disrupt the normal operation of a system.
On the other hand, a data security breach involves unauthorized access to sensitive information such as personally identifiable information (PII), financial records, or intellectual property. Cybercriminals use various methods such as phishing, malware attacks, or social engineering tactics to gain access to valuable data that they can either sell on the dark web or use for further criminal activities like identity theft.
While both DOS attacks and data security breaches may cause significant harm to an organization’s reputation and finances, they differ in their impact and objectives. A DOS attack seeks to disrupt services temporarily while a data breach could lead to loss of confidential customer information leading up to hefty fines for affected organizations under regulations like GDPR or HIPAA.
Similarities Between A DOS Attack and a Data Security Breach
Both attacks require prompt action from affected organizations to mitigate damages and prevent future incidents. A DOS attack may require network monitoring tools and mitigation techniques while a data security breach may involve notifying affected customers, conducting forensic analysis, and improving security measures.
Are DOS Attacks Considered Data Security Breaches?
Legal Perspective
From a legal perspective, determining whether or not a DOS attack constitutes a data breach can be complex. Generally speaking, under most data breach notification laws, the definition of what constitutes personal information is broad and inclusive. This means that if the attacker gains access to any information that could identify an individual or an organization in some way, then it could be considered a data breach.
However, in the case of DOS attacks, there may be no actual access gained to an organization’s network or sensitive information. Instead, these attacks aim to disrupt normal business operations by overwhelming servers with traffic until they are unable to function properly. As such, whether or not this type of attack is deemed a data security breach depends on the specific language used in each state’s respective notification law.
Experts’ Opinions
Experts are divided on whether a denial of service (DOS) attack is considered a data security breach. Some argue that DOS attacks do not result in unauthorized access, theft, or exposure of sensitive information, which are typically the defining characteristics of a data security breach. Rather, these attacks render computer systems unavailable by overwhelming them with traffic and requests from multiple sources, making it impossible for legitimate users to access the system.
However, others believe that DOS attacks should be treated as a type of data security breach because they compromise the availability and integrity of data. These experts contend that when an attacker is able to disable or disrupt a computer system through a DOS attack, they could potentially cause significant harm to an organization’s operations and reputation. Moreover, some attackers may use DOS attacks as part of a larger scheme to gain unauthorized access to sensitive information or manipulate data in other ways.
Impact of DOS Attacks on Data Security
How DOS Attacks Affect Data Security?
While a DOS attack does not directly access or steal data, it can lead to data breaches by making systems vulnerable to other types of attacks.
In many cases, attackers use DOS attacks as a diversionary tactic to distract IT personnel while they attempt to gain unauthorized access to systems or networks. This could allow them to install malware, exfiltrate data, or perform other malicious activities undetected. Additionally, prolonged downtime caused by a DOS attack may result in lost revenue and reputational damage for businesses that rely on their online presence.
Therefore, it is essential for organizations to take proactive measures against DOS attacks and ensure that their security protocols can withstand such an attack without compromising the confidentiality, integrity, and availability of their data.
Vulnerabilities Exposed by DOS Attacks
One of the vulnerabilities exposed by DOS attacks is the impact on an organization’s reputation. A successful DOS attack can cause severe damage to an organization’s brand image and customer trust. The inability to access essential services such as online banking, e-commerce sites, and other critical systems can lead customers to lose faith in the company’s ability to provide secure services.
Another vulnerability exposed by DOS attacks is the potential for further exploitation. Hackers often use DOS attacks as a distraction technique while they carry out more sophisticated cyberattacks against an organization’s infrastructure.
Mitigating DOS Attacks
Best Practices for DOS Attack Prevention
To prevent DOS attacks, organizations need to implement several best practices.
To prevent DOS attacks conduct regular vulnerability assessments and penetration testing on infrastructure systems. This will help identify weaknesses that attackers can exploit and give an opportunity for fixing them before any harm is done. It’s also important to monitor network traffic regularly and have security policies that govern access control and resource allocation.
Having an incident response plan in place can help mitigate the impact of a DOS attack if one occurs. Organizations need to ensure that their employees understand what actions they should take in case such an event occurs, such as disconnecting from the network or reporting suspicious behavior immediately.
Effective DOS Attack Response Strategies
To effectively respond to a DOS attack, organizations must have strategies in place that focus on mitigating the damage caused by such an incident. One approach is to invest in scalable infrastructure that can handle sudden spikes in traffic without going down. Another strategy is implementing firewalls and filters that block malicious traffic before it reaches its target destination. Additionally, having an emergency response plan in place can help reduce downtime and minimize disruption when an attack occurs.
Conclusion
A denial of service (DOS) attack is not necessarily considered a data security breach. This is because while a DOS attack can disrupt access to data or systems, it does not necessarily involve the theft or compromise of sensitive information.
However, it is important to note that DOS attacks can still have serious consequences for businesses and organizations. These attacks can result in significant downtime and loss of productivity, as well as damage to reputation and customer trust.
FAQs
What is the difference between a DOS attack and a DDOS attack?
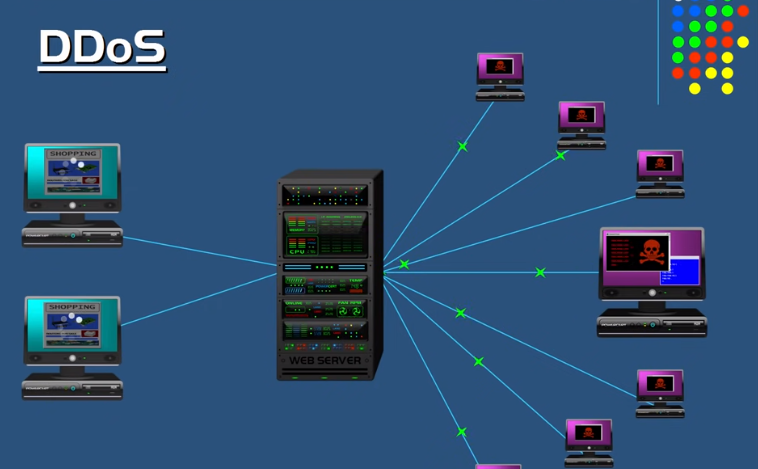
A DOS attack is an attempt to overload a server or network resource with a massive amount of traffic, rendering it inaccessible to legitimate users. On the other hand, DDOS attacks involve multiple sources flooding the targeted system with traffic from various locations, making it even more challenging to counter.
Can a DOS attack cause a data security breach?
A DOS attack can lead to a security breach if hackers leverage this technique as part of their multi-pronged approach toward infiltrating an organization’s IT infrastructure. Hackers often use DDOS (Distributed Denial of Service) attacks as a smokescreen to cover up other malicious activities such as stealing data or planting malware on vulnerable devices.
What should I do if my company falls victim to a DOS attack?
Isolate the affected system or network by disconnecting it from the internet. This will prevent further damage while you assess the situation and implement countermeasures. Gather as much information as possible about the attack pattern, source IP address(es), and duration of the attack. This data will help you identify potential vulnerabilities in your system or network that need addressing.
It’s important also to report any DOS attacks to relevant authorities such as law enforcement agencies, internet service providers (ISPs), and regulatory bodies if applicable. Some states have specific regulations governing how companies should respond to data security breaches like DOS attacks.
