Introduction
Definition Of A Timestamp Attack
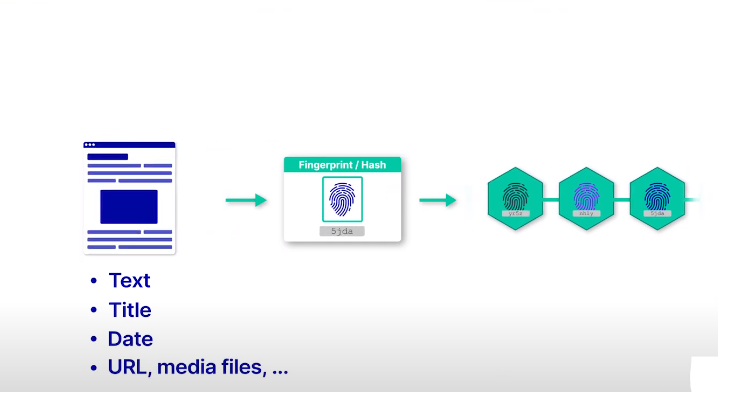
Timestamp attacks refer to the manipulation of timestamps in a data system with the aim of compromising its integrity. Time stamps play a critical role in data security, especially when it comes to determining when transactions or events occur in a system.
Importance Of Timestamps In Data Security
Timestamps are crucial in maintaining the integrity of data, especially when it comes to securing information from potential tampering. They provide a record of when and where a piece of data was accessed or modified, allowing for easy tracking and detection of any unauthorized changes made. Timestamps also play a significant role in forensic investigations, providing valuable evidence that can be used to identify culprits responsible for security breaches.
However, timestamp attacks pose a significant threat to data security. Attackers can manipulate timestamps by altering system clocks or creating false timestamps, leading to inaccurate records that can compromise the authenticity and reliability of data. This is particularly dangerous in industries such as finance or healthcare where even minor discrepancies could have severe consequences.
To prevent timestamp attacks, organizations must implement robust security measures such as encryption and multifactor authentication. Regular audits should also be conducted to ensure the accuracy and consistency of timestamps used across various systems. By prioritizing timestamps as an essential aspect of data security, organizations can safeguard their sensitive information against malicious actors looking to exploit vulnerabilities for personal gain.
Understanding Timestamps in Data Security
Definition And Purpose Of Timestamps
Timestamps are digital markers that indicate the date and time of an event, transaction, or communication. They serve as a crucial tool in data security by establishing the sequence of events within a particular system or process. Timestamps play a vital role in ensuring accountability, transparency, and integrity when it comes to handling sensitive information.
The purpose of timestamps is to create a record of events that cannot be altered retrospectively. By adding timestamps, it’s possible to track when specific actions were taken on specific pieces of data. Timestamps may also help identify whether there have been any delays or discrepancies in the processing or transmission of data. Additionally, timestamps can be used to establish proof of existence for certain documents, emails, or other electronic records.
Role Of Timestamps In Data Integrity And Verification
Timestamps play a crucial role in maintaining the integrity of data. In simple terms, timestamps are used to record the exact time at which an event or action occurred. By doing so, it becomes easier to verify data and detect any possible tampering with the data. Timestamps help establish a chronological order of events and actions, making it simpler to trace changes made to the data.
Types of Timestamp Attacks
Backdating Attacks
The first type of timestamp attack is called a backdating attack. In this attack, an attacker modifies the system clock or changes the timezone settings on their device to make it appear as if an activity occurred at an earlier time than it actually did. This can be used to cover up illegal activities or gain access to sensitive information that has already expired.
One consequence of backdating attacks is that they can undermine confidence in the accuracy and reliability of digital records. If people cannot trust that the dates and times associated with certain files are correct, then they may be less likely to use those files or rely on them for important decisions. Additionally, backdating attacks can lead to legal disputes over contracts, agreements, and other business transactions where timing is crucial.
Forwarding Attacks
In this type of attack, an attacker intercepts and modifies data packages as they travel from one entity to another, all while disguising themselves as an authorized recipient. This can lead to the attacker gaining access to sensitive information such as passwords or financial data, and even being able to manipulate the transmission for their own gain.
The consequences of forwarding attacks, including timestamp attacks, can be severe for both individuals and organizations alike. Unauthorized access to sensitive information can cause financial losses or reputational damage, while manipulation of data transmissions could potentially result in physical harm if it affects critical systems like those used in the healthcare or transportation sectors.
Replay Attacks
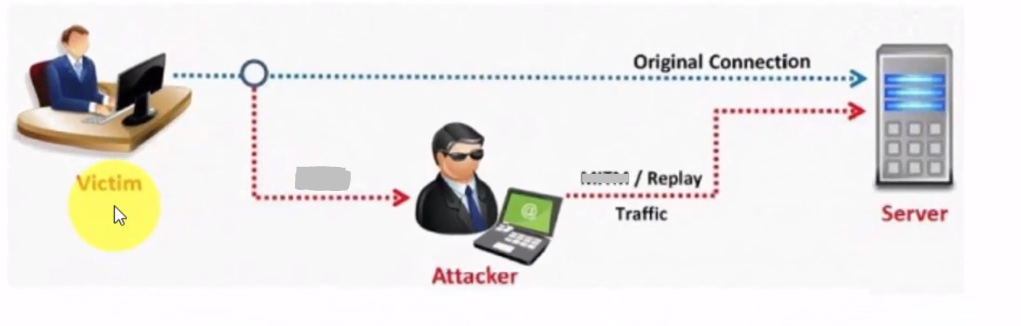
In this scenario, attackers intercept legitimate timestamps and then reuse them later on in other transactions. This can lead to unauthorized access or other forms of fraud.
The consequences of replay attacks can be severe, particularly in industries such as finance or healthcare where sensitive data is frequently transmitted. An attacker who successfully executes a replay attack could potentially steal financial information, manipulate medical records, or cause other types of harm.
Consequences of Timestamp Attacks
Data Manipulation
One major consequence of timestamp attacks is data manipulation. By altering timestamps on important files or documents, attackers can make it appear as if certain events happened earlier or later than they actually did. This can lead to confusion and misinformation in critical decision-making processes, resulting in financial losses, legal disputes, and reputational damage.
Fraud and Misrepresentation
If an attacker successfully manipulates the timestamp on a financial transaction document, they could alter the date on which payment was made. This could have legal implications and result in financial losses for one or both parties involved.
Legal and Regulatory Implications
The legal and regulatory implications of timestamp attacks are severe, as they can result in hefty fines for companies that fail to comply with relevant legislation.
The most prominent regulatory framework governing data security is the General Data Protection Regulation (GDPR), which came into effect in May 2018. Under GDPR, organizations must ensure the confidentiality, integrity, and availability of personal data at all times. Timestamp attacks that compromise these principles can lead to costly penalties for non-compliance.
Apart from GDPR, other regulations such as the California Consumer Privacy Act (CCPA) and the Payment Card Industry Data Security Standard (PCI DSS) also impose strict requirements on organizations regarding data security. Companies must take proactive measures to protect their systems against timestamp attacks and stay up-to-date with relevant legal and regulatory frameworks to avoid any legal repercussions.
Reputation and Trust
This type of attack can greatly damage an individual or company’s reputation and destroy the trust that has been built with customers.
Detection and Prevention Strategies
Timestamp Validation
Timestamp validation involves verifying the accuracy and authenticity of the timestamp associated with data records or transactions. Timestamps are used to track when an event occurred, but they can be vulnerable to attacks, which can compromise the integrity of the data and undermine trust in the system.
Secure Timestamping Protocols
Secure timestamping protocols play a crucial role in ensuring the integrity and authenticity of data. They provide a means of verifying when a specific piece of information was created or modified, which is essential for maintaining trust in digital transactions.
Digital Signatures
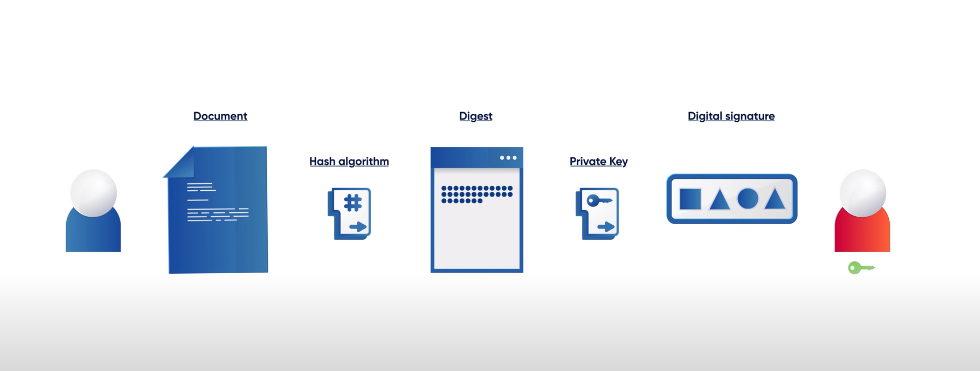
Digital signatures are used to verify the authenticity and integrity of digital documents and transactions. They provide a way to ensure that the sender of a document is who they claim to be, and that the contents of the document have not been tampered with or altered in any way.
Conclusion
Timestamp attacks pose a significant threat to data security and should be taken seriously by all organizations that handle sensitive information. The consequences of such attacks can be devastating, including the loss or theft of critical data, reputational damage, and legal liabilities that could result in hefty fines.
It is imperative for companies to take proactive measures to prevent timestamp attacks by implementing robust security protocols such as encryption and multi-factor authentication. Additionally, regular audits and assessments should be conducted to identify vulnerabilities in systems that may allow hackers to exploit timestamp weaknesses.
Frequently Asked Questions (FAQs)
How Can Timestamp Attacks Impact Data Integrity?
Timestamp attacks, also known as replay attacks, pose a significant threat to data integrity. In this type of attack, an adversary intercepts and records a legitimate timestamp token sent by a user or system. The attacker then replays the recorded token at a later time to gain unauthorized access to the system or data.
One potential consequence of timestamp attacks is the manipulation or alteration of data values. If attackers can successfully manipulate timestamps, they can tamper with timestamps embedded in authentication tokens and other sensitive data types. This can lead to incorrect information being used for decision-making processes that rely on accurate timestamps.
Another impact of timestamp attacks is that they can compromise system security by allowing attackers to bypass authentication measures. An attacker who successfully replays a legitimate timestamp token may be able to impersonate the original user’s identity and gain access to confidential information or systems. This could result in financial loss, reputational damage, and legal consequences for affected organizations.
What Are Some Preventive Measures Against Timestamp Attacks?
One of the preventive measures is to use secure and reliable time synchronization protocols such as Network Time Protocol (NTP) or Precision Time Protocol (PTP). These protocols ensure that all devices in the network have accurate and synchronized timestamps, which makes it harder for attackers to manipulate them.
Another preventive measure against timestamp attacks is to encrypt timestamps using strong encryption algorithms. By doing this, even if an attacker manages to intercept and modify a timestamp, they will not be able to decrypt it without the proper key. Additionally, organizations can implement access controls and authentication mechanisms to restrict unauthorized access to sensitive information that contains timestamps.
Regular monitoring and auditing of logs can help detect any unusual activity related to timestamps in the system. This includes identifying any discrepancies between different device timestamps or detecting suspicious requests sent at unusual times. By taking these preventive measures against timestamp attacks, organizations can significantly reduce their risk of data breaches or cyberattacks that exploit vulnerabilities in their systems timestamps.
Can Blockchain Technology Completely Eliminate Timestamp Attacks?
Many experts believe that blockchain technology can eliminate timestamp attacks completely. This is because blockchain provides a tamper-proof record of all transactions that cannot be altered without consensus from the network participants. As each block on the chain contains a unique cryptographic hash, any attempt to alter one block’s data would invalidate the entire chain.
However, some critics argue that while blockchain technology may significantly reduce timestamp attacks’ likelihood, it cannot entirely eliminate them. For instance, if an attacker gains control over more than 50% of a blockchain’s computing power (known as a 51% attack), they could still tamper with timestamps and records in the blockchain.
How Are Timestamp Attacks Relevant In Legal Proceedings?
In legal proceedings, timestamps are used as evidence to establish timelines and prove the authenticity of documents, emails, or other electronic records. If these timestamps have been manipulated through a timestamp attack, it can cast doubt on the integrity of the evidence presented.
In some cases, courts may rely heavily on timestamps to make determinations about liability or guilt. For example, if a company is accused of not complying with data retention regulations and claims that certain records were deleted before the deadline, the timestamps on those files could be crucial in determining whether they are telling the truth or not. If those timestamps have been tampered with through a timestamp attack, it becomes much more difficult for courts to determine what really happened.
