Definition of Web Application Attacks
Web application attacks refer to malicious activities that exploit vulnerabilities in web applications to gain unauthorized access or steal sensitive information. These attacks can occur due to various reasons, including weak passwords, unpatched software, and social engineering tactics.
Common Web Application Attacks
Cross-Site Scripting (XSS)
Cross-site scripting, or XSS, is a type of web application attack that involves injecting malicious code into a web page viewed by other users. This code can be used to steal sensitive information, such as login credentials or personal data, from unsuspecting users.
SQL Injection
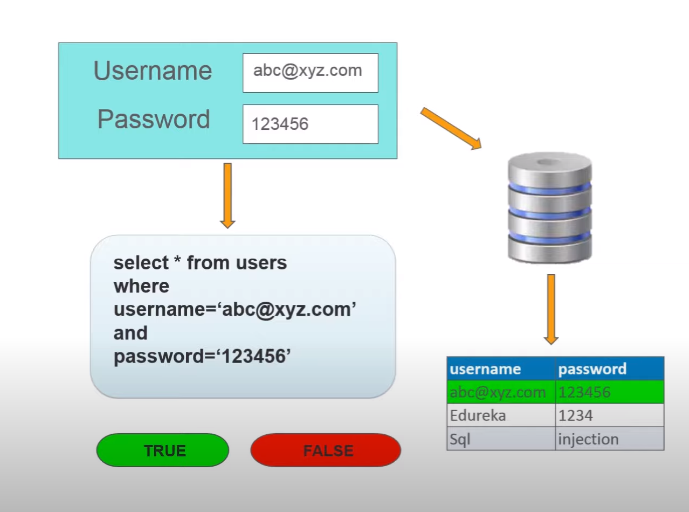
SQL injection is another type of web application attack that involves exploiting vulnerabilities in a web application’s database to extract sensitive information. Attackers can use SQL injection to bypass authentication measures and gain access to sensitive data stored in the database.
Cross-Site Request Forgery (CSRF)
Cross-site request forgery, or CSRF, is an attack that tricks a user into acting on a web application without their knowledge or consent. This can include actions such as making a purchase or changing a password, which can result in the theft of sensitive information.
Factors Affecting the Likelihood of Data Extraction
Vulnerability of the Web Application
The vulnerability of a web application is a significant factor that can affect the likelihood of data extraction. If a web application has security vulnerabilities, it can be exploited by attackers to gain unauthorized access to sensitive data. Common vulnerabilities include SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms. Web developers need to ensure that their applications are secure and regularly updated to prevent the exploitation of vulnerabilities. Additionally, web application security testing can help identify and address vulnerabilities before they can be exploited by attackers.
Way to Identify Vulnerabilities in A Web Application
Identifying vulnerabilities in a web application can be a complex process, but several techniques can be used to help identify potential issues.
1. Manual Testing: One approach is to manually test the web application by attempting to exploit known vulnerabilities or by performing a thorough analysis of the code and system architecture. This can be time-consuming and requires a deep understanding of web application security.
2. Automated Scanning: Another approach is to use automated scanning tools that can quickly identify vulnerabilities by scanning the web application for common issues such as SQL injection, cross-site scripting, and insecure file uploads. These tools are often more efficient than manual testing, but they may also generate false positives or miss certain vulnerabilities.
3. Penetration Testing: A more comprehensive approach is to conduct a penetration test, which involves simulating an attack on the web application to identify vulnerabilities and assess the overall security posture of the system. This approach requires specialized skills and tools but can provide valuable insights into the security of the web application.
Regardless of the approach used, it is important to prioritize vulnerabilities based on their severity and likelihood of exploitation and to take appropriate steps to remediate any identified issues.
Role of User Behaviour in Data extraction
User behaviour can play a significant role in data extraction, particularly in cases where sensitive information is being accessed or shared. For example, if users are not properly trained on how to handle sensitive data, they may inadvertently expose it through actions such as emailing it to unauthorized recipients or storing it on unsecured devices. Similarly, if users are not following proper security protocols, such as using strong passwords and regularly updating them, they may leave themselves and the system vulnerable to cyber-attacks. Organizations need to have clear policies and procedures in place for handling sensitive data and to provide regular training and reminders to users on how to properly handle and secure this information. Additionally, implementing technical controls such as access controls, encryption, and monitoring can help mitigate the risks associated with user behaviour.
Best practices for preventing data extraction through user behaviour
Here are some best practices for preventing data extraction through user behaviour:
1. Limit user access: Only grant access to sensitive data to those who need it to perform their duties. Implement access controls and permissions to ensure that users can only access the data necessary for their work.
2. Monitor user activity: Use monitoring tools to track user activity and detect any suspicious behaviour, such as large data downloads or access to data outside of normal working hours.
3. Implement encryption: Encrypt sensitive data both in transit and at rest to prevent unauthorized access in case of a breach.
4. Use strong passwords: Require users to create strong passwords and implement policies for regular password changes.
5. Conduct regular training: Educate users on the importance of data security and provide regular training on best practices for handling sensitive data.
6. Implement multi-factor authentication: Require users to provide additional authentication factors, such as a fingerprint or a security token, to access sensitive data.
By implementing these best practices, organizations can reduce the risk of data extraction through user behaviour and protect their sensitive information from cyber threats.
Best Practices for Protecting Privacy Data Elements
Protecting private data elements is crucial for organizations that handle sensitive information. Here are some best practices to follow:
1. Implement data minimization: Collect only the minimum amount of data necessary for business purposes and dispose of it securely when it is no longer needed.
2. Use encryption: Encrypt sensitive data both in transit and at rest to prevent unauthorized access.
3. Implement access controls: Limit access to sensitive data to only those who need it to perform their duties.
4. Conduct regular audits: Regularly review access logs and audit trails to identify any unauthorized access attempts.
5. Train employees: Educate employees on the importance of protecting privacy data elements and provide regular training on best practices for handling sensitive data.
By following these best practices, organizations can safeguard privacy data elements and prevent data breaches that can cause irreparable harm to individuals and businesses alike.
Best Practices For Securing Web Applications Against Attacks
Web application security is a crucial aspect of protecting sensitive data elements. Here are some best practices for securing a web application against attacks:
1. Use secure coding practices: Ensure that your developers follow secure coding practices, such as input validation, output encoding, and proper error handling.
2. Implement access controls: Use access controls to restrict access to sensitive data elements and functionality within the application.
3. Use encryption: Use encryption to protect sensitive data elements in transit and at rest. This includes using SSL/TLS for communication between the client and server and encrypting data stored in databases or on disk.
4. Regularly update software and patches: Keep your web application software up-to-date with the latest security patches and updates.
5. Use intrusion detection and prevention systems: Use intrusion detection and prevention systems to identify and prevent attacks on your web application.
By following these best practices, organizations can significantly reduce the risk of a data breach through their web application.
Implement Web Application Security Measures
Implementing web application security measures can be a complex process, but it is essential to ensure the safety of sensitive data. Here are some steps that organizations can take to implement web application security measures:
1. Conduct a security audit: Conduct a thorough security audit of your web application to identify vulnerabilities and risks.
2. Use secure coding practices: Use safe coding practices to ensure that your web application is not vulnerable to common attacks such as SQL injection and cross-site scripting.
3. Implement access controls: Implement access controls to restrict access to sensitive data and ensure that only authorized personnel can access it.
4. Use encryption: Use encryption to protect sensitive data in transit and at rest.
5. Regularly test and monitor your web application: Regularly test and monitor your web application for vulnerabilities and suspicious activity.
6. Train your employees: Train your employees on best practices for web application security to ensure that they are aware of potential risks and know how to respond to security incidents.
By taking these steps, organizations can significantly improve the security of their web applications and reduce the risk of a data breach.
Definition And Explanation Of Data Encryption
Data encryption is converting plain text or data into a coded language to protect it from unauthorized access or theft. This is done by using an algorithm to scramble the data, which can only be accessed and read by someone who has the key to decrypt the information. Encryption is commonly used to secure sensitive data such as financial, personal, and confidential business data. It is an essential security measure for protecting data from cyber-attacks and unauthorized access.
Best Practices For Data Encryption
Here are some best practices for data encryption:
1. Use strong encryption algorithms: Make sure to use strong encryption algorithms such as AES (Advanced Encryption Standard) or RSA (Rivest-Shamir-Adleman) to encrypt your data.
2. Use a secure key management system: A secure key management system is essential for protecting the encryption keys used to encrypt and decrypt your data. Make sure to use a system that provides strong key protection and access controls.
3. Encrypt data at rest and in transit: Encrypt data both at rest (stored on a device or server) and in transit (being sent over a network) to ensure maximum protection.
4. Implement multi-factor authentication: Implement multi-factor authentication to ensure that only authorized users can access the encrypted data.
5. Regularly update encryption protocols: Keep your encryption protocols up-to-date to ensure that you are using the latest and most secure encryption algorithms.
6. Conduct regular security audits: Conduct regular security audits to identify any vulnerabilities in your encryption system and take appropriate measures to address them.
By following these best practices, you can ensure that your data is well-protected and secure from cyber-attacks and unauthorized access.
Regular Auditing and Monitoring
Auditing and monitoring are crucial for maintaining the security and integrity of your data. Regular audits help identify potential vulnerabilities or weaknesses in your security measures, while monitoring allows you to detect and respond to suspicious activity in real-time. By implementing regular auditing and monitoring practices, you can ensure that your data is always protected and that any security incidents are detected and addressed promptly.
Best Practices For Auditing And Monitoring
Several best practices can help you effectively audit and monitor your data security:
1. Develop a comprehensive security policy: A security policy should outline the procedures and protocols that you will follow to protect your data. It should include guidelines for access control, data storage, and incident response.
2. Conduct regular security assessments: Regular security assessments can help you identify any vulnerabilities or weaknesses in your security measures. You can use the results of these assessments to make necessary improvements to your security policies and procedures.
3. Use automated monitoring tools: Automated monitoring tools can help you detect any suspicious activity in real-time. These tools can alert you to potential security incidents, allowing you to respond quickly and effectively.
4. Implement access controls: Access controls can help you limit access to sensitive data. By implementing access controls, you can ensure that only authorized users can access your data.
5. Train your employees: Your employees are your first line of defence against data breaches. By providing them with regular security training, you can help them identify potential security threats and respond appropriately.
By following these best practices, you can ensure that your data is always protected and that your security measures are effective.
Frequently Asked Questions (FAQs)
What is a web application attack?
A web application attack is a type of cyber attack that targets web-based applications such as online banking systems, e-commerce websites, and social media platforms. The goal of such an attack is to exploit vulnerabilities in the web application’s code or infrastructure to gain unauthorized access to sensitive data or to disrupt the application’s normal functioning. Some common types of web application attacks include SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks.
What are privacy data elements?
Privacy data elements are pieces of personal information that are considered sensitive and private and therefore require special protection and handling. These can include a person’s name, address, date of birth, social security number, financial information, medical records, and other personally identifiable information (PII). It is important to safeguard these privacy data elements to prevent identity theft, fraud, and other malicious activities that can harm individuals and organizations. Privacy laws and regulations, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA), set standards for the collection, use, and disclosure of personal information. Organizations must comply with these laws and implement appropriate security measures to protect private data. Failure to do so can result in legal and financial consequences, as well as damage to the reputation of the organization.
How can web application attacks be prevented?
Several measures can be implemented to prevent web application attacks. Here are a few examples:
1. Input validation: All user input should be validated and sanitized to ensure that it is safe to use within the application.
2. Authentication and authorization: Strong authentication and authorization mechanisms should be in place to prevent unauthorized access to the application and its resources.
3. Encryption: Sensitive data should be encrypted both in transit and at rest to prevent unauthorized access.
4. Access controls: Access controls should be implemented to ensure that only authorized users can access the application and its resources.
5. Regular updates and patches: Web applications should be kept up-to-date with the latest security patches and updates to prevent known vulnerabilities from being exploited.
6. Security testing: Regular security testing should be performed to identify and remediate any vulnerabilities in the application.
By implementing these measures, web application attacks can be prevented, and the application can be kept secure from malicious actors.
How often should a web application be audited and monitored?
The frequency of web application audits and monitoring depends on several factors, including the complexity of the application, the sensitivity of the data it handles, and the level of risk associated with potential security threats. Generally, it is recommended to audit and monitor web applications regularly, at least once a year or more frequently if the application handles sensitive data or is subject to compliance regulations.
What are the consequences of a data breach?
A data breach can have severe consequences for individuals and organizations. Some of the consequences include:
1. Financial loss: Data breaches can result in financial loss for individuals and organizations. This can include the cost of investigating the breach, notifying affected parties, and providing credit monitoring services.
2. Damage to reputation: A data breach can damage an organization’s reputation, leading to a loss of trust from customers and stakeholders. This can result in a loss of business and revenue.
3. Legal consequences: Data breaches can result in legal consequences, including fines and lawsuits. Organizations may also be subject to regulatory penalties for failing to comply with data protection laws.
4. Identity theft: A data breach can result in the theft of personal information, which can be used for identity theft and other fraudulent activities.
5. Loss of intellectual property: Data breaches can result in the loss of intellectual property, including trade secrets and proprietary information. This can have a significant impact on an organization’s competitiveness and ability to innovate.
Conclusion
In conclusion, protecting private elements is crucial for individuals and organizations alike. It helps to maintain trust, prevent legal liabilities, avoid financial losses, and protect sensitive information from theft and misuse. By implementing strong security measures and adhering to data protection laws, organizations can safeguard personal and confidential information and ensure their customers’ and employees’ safety and privacy.
