Introduction
In today’s digital age, data security is of utmost importance. With the growing amount of sensitive information being shared and stored online, it is crucial to ensure that this data is protected from unauthorized access. One way to achieve this is through encryption, which involves converting data into a code that can only be deciphered with a key. However, storing and sharing encrypted data can be complex, especially when using APIs. This article will explore how to store and share encrypted data with APIs.
APIs play a crucial role in storing and sharing encrypted data, providing a standardized way for applications to connect. APIs allow developers to easily integrate encryption into their applications by providing a set of rules and protocols for data exchange. When storing encrypted data, APIs can securely transmit the data to a storage service that supports encryption. This ensures that the data is protected while at rest. APIs can also retrieve the encrypted data from storage and decrypt it for use in an application. In addition to encryption, APIs can be used for other security measures, such as authentication and authorization. APIs can provide a secure way for users to authenticate themselves before accessing sensitive data or performing certain actions within an application. APIs can also enforce authorization rules, ensuring only authorized users can access certain data or functionality within an application.
Storing Encrypted Data With APIs
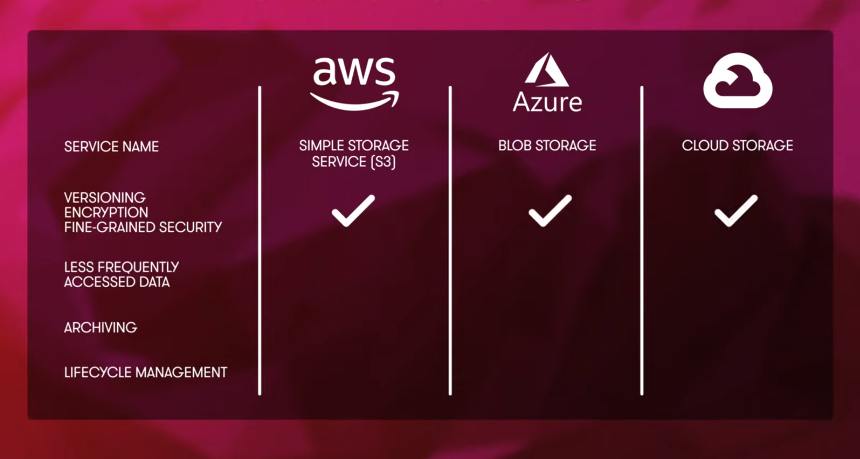
When storing encrypted data, APIs can be a useful tool. APIs, or application programming interfaces, allow for secure communication between software applications. Data can be encrypted before it is sent through the API and then decrypted on the receiving end. Various APIs are available for storing encrypted data, including cloud-based storage solutions like Amazon S3 and Google Cloud Storage. These APIs typically offer built-in encryption tools, allowing users to encrypt data before storing it in the cloud.
Another option for storing encrypted data is to use a database encryption API, which can be used to encrypt data stored in a database. This can be particularly useful for organizations that need to store sensitive information, such as financial or healthcare data.
Sharing Encrypted Data Through APIs
Sharing encrypted data through APIs can be done in a few different ways. One option is to use a secure communication protocol, such as HTTPS, to transfer the encrypted data between systems. Another choice is to use an API that supports the encryption and decryption of data, such as the Amazon Web Services Key Management Service (KMS) API. This API allows users to encrypt and decrypt data using keys managed by AWS, making it easy to share encrypted data between systems securely. Additionally, some APIs may support using digital signatures to verify the authenticity of encrypted data, further enhancing security when sharing sensitive information.
API Encryption Implementation
API encryption implementation is the process of encrypting data transmitted between a client and a server through an API. This ensures that the data is secure and cannot be interrupted or tampered with by unauthorized third parties. There are several methods of API encryption implementation, including symmetric key encryption, asymmetric key encryption, and hashing. Symmetric key encryption involves using the same key to encrypt and decrypt data. In contrast, asymmetric key encryption uses a public key to encode data and a private key to decrypt it. Hashing involves converting data into a fixed-length string of characters that cannot be reversed.
API encryption can be implemented using various programming languages and libraries, such as OpenSSL, Java Cryptography Architecture (JCA), and .NET Framework Cryptography. It is important to choose a secure encryption algorithm and to keep the encryption keys and certificates secure to prevent unauthorized access to the data.
Securing API Endpoints
Securing API endpoints is another important aspect of API security. One way to secure endpoints is through authentication and authorization mechanisms. This involves verifying the user’s or application’s identity by accessing the API and determining if they have the necessary consents to perform the requested action. Various authentication methods, such as OAuth, JWT, and basic authentication, can be used. It is important to choose a method appropriate for the level of security required for the API and to ensure that the authentication credentials are securely transmitted and stored.
Authorization mechanisms can also be implemented to control access to specific endpoints or resources within the API. This can involve assigning roles and permissions to users or applications and enforcing access control rules based on these roles and permissions.
In addition to authentication and authorization, other security measures, such as rate limiting, input validation, and error handling, can further enhance API endpoints’ security.
Auditing And Logging For Compliance
Auditing and logging are important aspects of API security that can help ensure compliance with regulatory requirements and detect potential security incidents. By keeping detailed records of API activity, organizations can track who accessed which endpoints, when they accessed them, and what actions were performed. This information can be used to identify and investigate suspicious activity and demonstrate compliance with regulations such as HIPAA or PCI-DSS. Organizations should consider using tools such as log management systems or security information and event management (SIEM) solutions to implement auditing and logging. These tools can help aggregate and analyze log data from multiple sources, allowing organizations to identify and respond to security incidents quickly.
It’s important to note that auditing and logging can also have privacy implications, as they may collect sensitive information about users or applications. To address these concerns, organizations should establish clear policies and procedures for handling log data, including data retention and disposal, and ensure they comply with relevant data protection regulations.
Testing And Quality Assurance
Testing and quality assurance are critical processes that help ensure that software meets its intended purpose and operates as expected. Testing involves running software through a series of tests to identify any defects or issues affecting its performance or functionality. Quality assurance, on the other hand, involves ensuring that the software meets established standards and requirements.
Effective testing and quality assurance require a well-defined process and a dedicated team with the necessary skills and expertise. Organizations should establish clear testing and quality assurance procedures and ensure they are followed consistently throughout the development lifecycle.
In addition, organizations should consider using automated testing tools and techniques to improve efficiency and accuracy. Automated testing can help identify defects and issues more quickly and efficiently than manual testing, allowing developers to address them before they become more serious problems.
What Is Encrypted Volume For Storing Data?
An encrypted volume is a secure and protected storage area used for storing data that has been encrypted using encryption keys. This volume can be a physical device like a hard drive or a virtual one created within a larger storage system. The data stored in an encrypted volume is protected from unauthorized access because it can only be decrypted with the correct encryption key. This makes encrypted volumes an effective way to protect sensitive data from potential security breaches.
Best Practices For Secure Data Sharing

Here are some best practices for secure data sharing:
- Use encryption: Encrypting data ensures that it cannot be read without the encryption key, even if it is intercepted. Make sure to use strong encryption methods and keep the encryption keys secure.
- Limit access: Only grant access to data to those who need it to accomplish their job functions. Use access controls to restrict access to sensitive data.
- Use secure channels: When sharing data, use secure channels such as secure file transfer protocols or email.
- Monitor data sharing: Keep track of who is accessing data and when. This can help identify any unauthorized access or suspicious activity.
- Train employees: Educate employees on the importance of secure data sharing and the risks of sharing sensitive information. Provide training on best practices for secure data sharing.
- Have a data-sharing policy: Establish a policy outlining the rules and guidelines for sharing data. Please ensure all employees know the policy and understand their responsibilities.
Conclusion
Storing and sharing encrypted data is crucial for maintaining the privacy and integrity of sensitive information. It confirms that only authorized individuals can access and use the data while protecting against potential cyber threats and attacks. By implementing strong encryption techniques and regularly reviewing and testing your API encryption, you can ensure your data remains secure and protected. As a writing assistant, I hope this information has helped me understand the importance of encrypted data storage and sharing.
Frequently Asked Questions (FAQs)
What Is Encrypted Data?
Encrypted data is data that has been converted into a code to prevent unauthorized access or theft. Encryption involves algorithms scrambling the original data and creating a new code that can only be deciphered with a specific key or password. This helps protect sensitive personal, financial, and confidential business data from being accessed by unauthorized individuals or cybercriminals.
How Does API Encryption Work?
API encryption involves using encryption algorithms to secure the communication between two systems using an API (Application Programming Interface). When a request is made from one system to another via an API, the data is encrypted before it is referred to the network. The receiving system then uses a specific key or password to decrypt the data and read the original message. This helps to prevent unauthorized access to sensitive data, confirming that only authorized parties can access and use the information exchanged via the API.
What Are The Benefits Of Storing Data With APIs?
Storing data with APIs has several benefits. Firstly, APIs provide a secure and efficient way to store and retrieve data. APIs use encryption to protect data from unauthorized access, ensuring only authorized parties can access and use the information. Additionally, APIs provide a standardized way to access data, making it easier for different systems to exchange information. This can help to streamline business processes and improve overall efficiency. Finally, APIs can also provide real-time access to data, allowing businesses to make faster and more informed decisions based on up-to-date information.
How Can I Ensure The Security Of My Encrypted Data?
To ensure the security of your encrypted data, you should follow best practices for encryption and data security. This includes using strong encryption algorithms, such as AES or RSA, and implementing proper key management practices to ensure that only authorized parties can access the encryption keys. It would help to use secure communication channels, such as SSL or TLS, to transmit the encrypted data. Additionally, you should regularly monitor and audit your encryption processes to identify and address potential vulnerabilities or weaknesses in your security measures. It is also important to stay up-to-date with the latest security standards and best practices to ensure your encryption methods remain effective.
What Are The Compliance Requirements For Encrypted Data Storage?
The compliance requirements for encrypted data storage vary depending on the industry and specific regulations. However, some common requirements include:
- Encryption standards: The encryption must meet certain standards, such as FIPS 140-2, a US government standard for cryptographic modules.
- Key management: The keys used for encryption must be managed securely, including proper storage and access control.
- Access controls: The encrypted data must only be restricted to authorized personnel.
- Audit trails: A system must be in place to track access to the encrypted data and any changes made to it.
- Data Retention: Encrypted data must be retained for a certain period, depending on the industry and regulations.
How Can I Choose The Right API Storage Provider?
Choosing the right API storage provider can be a daunting task, but there are a few key factors to consider:
- Security: As discussed earlier, security is paramount when storing sensitive data. Look for a provider with strong encryption, access controls, and audit trails.
- Scalability: Your storage needs may change over time, so choosing a provider that can grow with you is important. Make sure they offer flexible storage options and can handle increased traffic and data volumes.
- Reliability: Your API storage needs to be available and accessible at all times. Look for a provider with a strong uptime and reliability track record, and consider their disaster recovery and backup options.
- Integration: Your API storage should integrate seamlessly with your existing systems and workflows. Look for a provider that easily integrates popular development frameworks and tools.
- Cost: API storage can be expensive, so choosing a provider that offers transparent pricing and flexible payment options is important. Ensure you understand their pricing model and any additional data transfer or storage overages fees.
Can Encrypted Data Be Shared Securely Through APIs?
Yes, encrypted data can be shared securely through APIs. Encryption often ensures data security when sharing sensitive information through APIs. However, it’s important to choose an API storage provider that offers strong encryption methods and follows industry-standard security practices to confirm the safety of your data. It would assist if you also considered implementing secure authentication and authorization mechanisms to control access to your encrypted data.
How Can I Test The Security Of API Encryption Implementation?
There are several ways to test the security of API encryption implementation, including:
- Penetration testing: This involves attempting to exploit vulnerabilities in the API encryption by simulating attacks from a hacker’s perspective.
- Vulnerability scanning: Using automated tools to scan the API encryption for known vulnerabilities.
- Code review: This involves analyzing the source code of the API encryption to identify any potential security issues.
- Threat modeling: This involves identifying potential threats to the API encryption and developing strategies to mitigate them.
- Security testing frameworks: Several security testing frameworks are available that can help you test the security of your API encryption implementation.
