Your Ultimate Guide To AWS Storage Services: Which One Encrypts Your Data At Rest?
Introduction
AWS (Amazon Web Services) offers a range of storage services to meet the needs of businesses of all sizes. However, with so many options, it can be overwhelming to determine which is the best fit for your organization’s needs. In addition to factors such as pricing and storage capacity, it’s also important to consider security measures, such as data encryption. In this guide, we will explore AWS storage services and identify which ones encrypt your data at rest, providing you with the ultimate guide to making an informed decision for your business.
What AWS Storage Service Encrypts Data At Rest?
Several AWS storage services encrypt data at rest. These include:
1. Amazon S3: Amazon S3 (Simple Storage Service) provides server-side encryption for data at rest. You can choose to have your data encrypted with either Amazon S3-managed keys or customer-managed keys.
2. Amazon EBS: Amazon EBS (Elastic Block Store) encrypts data at rest by default using AWS-managed keys. You can also use customer-managed keys for added security.
3. Amazon Glacier: Amazon Glacier is a low-cost storage service that provides secure and durable data archiving and backup storage. It encrypts data at rest using AES-256 encryption.
4. Amazon RDS: Amazon RDS (Relational database Service) encrypts data at rest using AES-256 encryption. You can also use your encryption keys for added security.
5. Amazon Redshift: Amazon Redshift is a data warehousing service that encrypts data at rest using AES-256 encryption. You can also use your encryption keys for added security.
Understanding Data Encryption
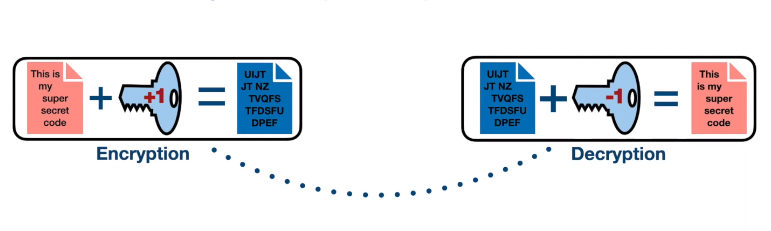
Data encryption is the process of converting plain text into a coded message to protect the confidentiality of data. Encryption uses an algorithm to scramble the data, making it unreadable to anyone who does not have the decryption key. This ensures that even if the data is intercepted, it cannot be read without the key.
There are two types of encryption: symmetric and asymmetric. Symmetric encryption uses the same key to encrypt and decrypt the data, while asymmetric encryption uses a public key to encrypt the data and a private key to decrypt it.
Encryption is an important security measure for protecting sensitive data, such as personal information, financial data, and trade secrets. It is used in a variety of applications, including online banking, e-commerce, and secure communication.
What Security Do Data At Rest Use?
Data at rest refers to data that is stored on a device or system, such as a hard drive, database, or cloud storage. To ensure the security of this data, various security measures can be implemented, such as encryption, access controls, and backup and recovery procedures. Encryption is a common method used to protect data at rest, as it can render the data unreadable to unauthorized users. Additionally, access controls can limit who has permission to access the data, and backup and recovery procedures can ensure that the data can be restored in case of a security breach or data loss.
Best Practices For Managing Encrypted Data

Managing encrypted data can be a complex process, but some best practices can help ensure the security and integrity of the data. Here are some tips:
1. Use strong encryption algorithms: Choose an encryption algorithm that is considered secure and has been widely tested and reviewed by security experts.
2. Implement key management: Proper key management is crucial for the security of encrypted data. Keys should be stored securely and only accessible to authorized users.
3. Use multi-factor authentication: Adding an extra layer of authentication, such as a password and a token, can help prevent unauthorized access to encrypted data.
4. Regularly update encryption software: Keep encryption software up to date with the latest security patches and updates to ensure that any vulnerabilities are addressed.
5. Perform regular audits: Regularly auditing encrypted data can help identify any security risks or vulnerabilities and ensure that encryption policies are being followed.
By following these best practices, organizations can help ensure that their encrypted data remains secure and protected from unauthorized access.
How To Enable Encryption For AWS Storage Services?
To enable encryption for AWS storage services, follow these steps:
1. Choose the storage service you want to enable encryption for (such as Amazon S3, Amazon EBS, or Amazon RDS).
2. Create a new encryption key or use an existing one.
3. Configure your storage service to use the encryption key you created or selected.
4. Verify that your data is being encrypted by checking the encryption status of your storage service.
5. Monitor your encrypted data regularly to ensure that encryption policies are being followed and to identify any security risks or vulnerabilities.
It’s important to note that enabling encryption for AWS storage services does not guarantee complete security. It’s still important to follow best practices for encryption and data security, such as keeping your encryption software up to date and performing regular audits.
Conclusion
In conclusion, choosing the right storage service that encrypts data at rest is crucial for maintaining the security and privacy of sensitive information. AWS offers various options for key management and backup, such as AWS KMS and AWS CloudHSM, to ensure that your encryption keys are stored securely and can be recovered in case of loss or damage. It is important to regularly rotate your encryption keys and test your key recovery process to ensure that your data remains accessible and secure. By taking these measures, you can have peace of mind knowing that your data is protected from unauthorized access and theft.
AWS provides several storage services that encrypt data at rest, including Amazon S3, Amazon EBS, Amazon RDS, and Amazon Glacier. These services use different encryption methods such as server-side encryption, client-side encryption, and AWS Key Management Service (KMS) encryption. It is important to properly manage and back up encryption keys to ensure the security and accessibility of data. Regular key rotation and testing of key recovery processes are also recommended. With these measures in place, AWS users can have confidence in the protection of their data. AWS provides a wide range of security features and services to help protect user data. However, users need to understand their security requirements and implement additional security measures as needed. This includes proper management and backup of encryption keys, regular key rotation, and testing of key recovery processes. Additionally, users should stay up-to-date on AWS security best practices and regularly review and adjust their security settings to ensure the ongoing protection of their data.
Frequently Asked Questions (FAQs)
What Is The Difference Between Customer-Managed Keys And AWS-Managed Keys?
Customer-managed keys are encryption keys that are created and managed by the customer, outside of AWS. The customer has full control over the key, including managing access and revoking the key if necessary. AWS-managed keys, on the other hand, are created and managed by AWS. The customer has limited control over the key, such as being able to rotate the key or disable it, but cannot access the key itself.
How Does Amazon S3 Server-Side Encryption Work?
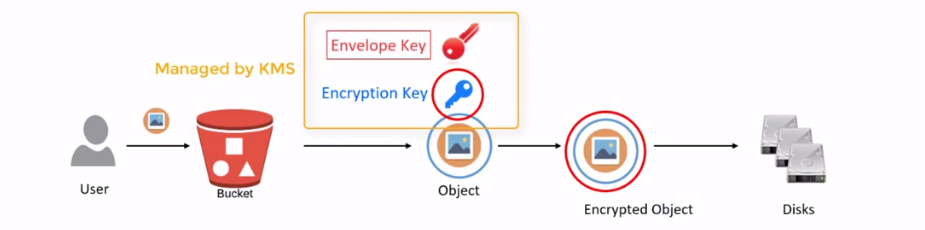
Amazon S3 server-side encryption allows you to encrypt your data at rest in S3. When you upload an object to S3, you can choose to have the object encrypted using either server-side encryption with Amazon S3-managed keys (SSE-S3) or server-side encryption with customer-provided keys (SSE-C). With SSE-S3, Amazon S3 automatically encrypts your data using 256-bit Advanced Encryption Standard (AES-256) encryption. Amazon S3 uses encryption keys that are managed and protected by AWS. SSE-S3 encrypts the object before saving it to disk and decrypts it when you download the object.
With SSE-C, you provide your encryption key that is used to encrypt and decrypt your data. When you upload an object, you must provide the encryption key as part of the request. Amazon S3 does not store the encryption key anywhere, so you must provide it every time you want to access the object. This provides you with full control over the encryption key and allows you to manage the key’s lifecycle.
Can I Encrypt My Existing Data In AWS Storage Services?
Yes, you can encrypt your existing data in AWS storage services using various encryption options provided by AWS. For example, you can use AWS Key Management Service (KMS) to encrypt your data at rest in Amazon S3, EBS volumes, and RDS instances. You can also use server-side encryption with Amazon S3-managed keys (SSE-S3) or customer-provided keys (SSE-C) to encrypt your data in Amazon S3. Additionally, you can use client-side encryption to encrypt your data before uploading it to AWS storage services. It is recommended to encrypt your data to ensure its confidentiality and integrity.
How Can I Ensure That My Data Is Always Encrypted At Rest?
To ensure that your data is always encrypted at rest in AWS, you can use AWS Key Management Service (KMS) to manage your encryption keys and enable server-side encryption for your AWS storage services such as Amazon S3, EBS volumes, and RDS instances. You can also use client-side encryption to encrypt your data before uploading it to AWS storage services. Additionally, you can enforce encryption requirements by using AWS IAM policies to restrict access to unencrypted data. By implementing these best practices, you can ensure that your data remains secure and protected at all times.
What Happens If I Lose My Encryption Keys?
If you lose your encryption keys, you cannot access your encrypted data. It is important to securely store your encryption keys and have a backup plan in place in case of loss or damage. AWS provides key management and backup options, such as AWS Key Management Service (KMS) and AWS CloudHSM. You should regularly rotate your encryption keys and test your key recovery process to ensure that your data remains accessible and secure.
