Overview of Data Compression And Encryption
Data compression is the process of reducing the size of a file or data stream without losing any important information. This is achieved by using various algorithms that identify and remove redundancies in the data. Compression is commonly used to reduce the amount of storage space required for files, as well as to speed up data transfer over networks. Encryption, on the other hand, is the process of converting plain text or data into a coded message that can only be read by someone who has the key to decode it.
Explanation of The OSI Model
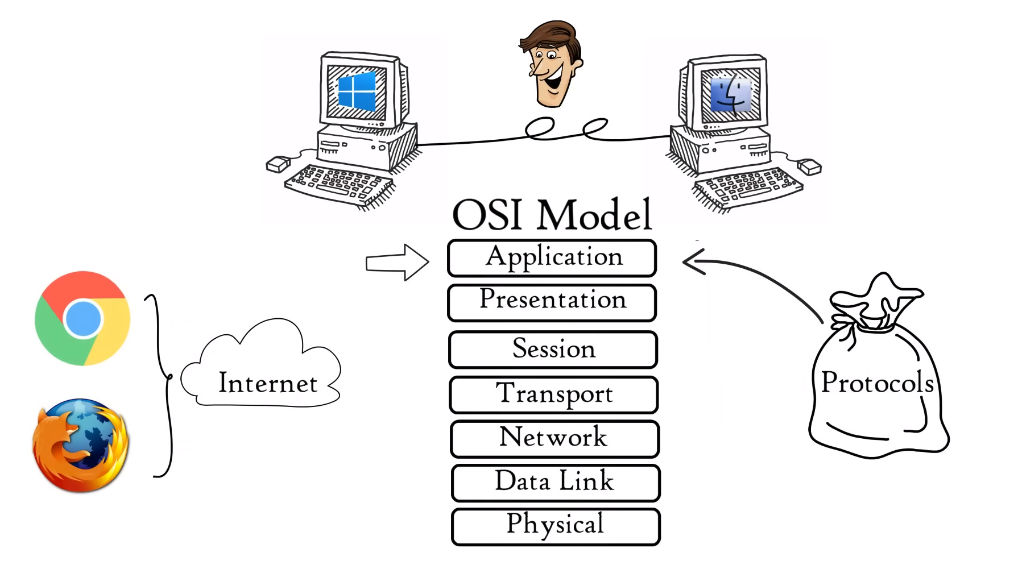
The OSI (Open Systems Interconnection) model is a conceptual framework used to describe the communication process between different systems in a network. It consists of seven layers, each with a specific function and set of protocols. The layers are:
1. Physical Layer: This layer deals with the physical transmission of data over the network, including the hardware and cables used.
2. Data Link Layer: This layer provides a reliable way to transfer data between two devices on the same network.
3. Network Layer: This layer is responsible for addressing and routing data between different networks.
4. Transport Layer: This layer ensures reliable delivery of data between applications running on different devices.
5. Session Layer: This layer establishes, manages, and terminates communication sessions between applications.
6. Presentation Layer: This layer is responsible for data encryption, compression, and conversion between different data formats.
7. Application Layer: This layer provides services and interfaces for applications to access network resources and services..
The Transport Layer
The Transport Layer is a crucial layer in the OSI model that ensures reliable delivery of data between applications running on different devices. Its main responsibility is to provide end-to-end data transfer services to the upper layers of the OSI model. This layer uses protocols such as TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) to provide reliable and efficient data transfer services.TCP is a connection-oriented protocol that establishes a reliable connection between two devices before transferring data.
Role of Transport Layer In Data Transmission
The Transport Layer plays a crucial role in data transmission by providing end-to-end data transfer services to the upper layers of the OSI model. Its main responsibility is to ensure that data is transferred reliably and efficiently between applications running on different devices. To achieve this, the Transport Layer uses protocols such as TCP and UDP.TCP is a connection-oriented protocol that establishes a reliable connection between two devices before transferring data. This ensures that data is delivered in the correct order and that no data is lost during transmission.
Explanation of Transport Layer Protocols
The Transport Layer of the OSI model is responsible for ensuring reliable and efficient data transfer between applications running on different devices. This is achieved through the use of protocols such as TCP and UDP.TCP (Transmission Control Protocol) is a connection-oriented protocol that establishes a reliable connection between two devices before transferring data. This means that it ensures that data is delivered in the correct order and that no data is lost during transmission.
Definition of the Presentation Layer
The Presentation Layer is the sixth layer of the OSI model, responsible for the formatting and presentation of data to be transmitted between applications. It is responsible for ensuring that the data is in a format that can be understood by the receiving application. It also handles data encryption and decryption, compression and decompression, and character encoding and decoding. The Presentation Layer plays a critical role in ensuring that the data is delivered in a usable format to the receiving application.
Role of The Presentation Layer In Data Transmission
The Presentation Layer is responsible for formatting and presenting the data in a way that can be understood by the receiving application. It ensures that the data is in a format that is compatible with the receiving application and that any encryption, compression, or character encoding is properly handled. The Presentation Layer also handles any necessary conversions between different data formats, such as converting text to images or audio.
Explanation of Presentation Layer Protocols
The Presentation Layer protocols are a set of rules and standards that govern the way in which data is formatted and presented by the Presentation Layer. Some common protocols used in the Presentation Layer include:
1. ASCII (American Standard Code for Information Interchange): This protocol is used to represent text characters using a standard code. It ensures that the data is properly formatted and can be understood by the receiving application.
2. Unicode: This protocol is used to represent text characters from different languages and scripts.
Definition of the Application Layer
The Application Layer is the topmost layer of the OSI (Open Systems Interconnection) model, which is used to define how different applications communicate with each other over a network. This layer is responsible for providing services to the end-user applications, such as email, web browsing, file transfer, and remote access. The Application Layer interacts directly with the user and provides a user interface to access network services. It also manages the communication between different applications on the same or different networks.
Role of the Application Layer in Data Transmission
The Application Layer plays a crucial role in data transmission as it is responsible for providing services to end-user applications and managing the communication between different applications on the network. It provides a user interface to access network services, such as email, web browsing, and file transfer. The Application Layer also ensures that the data being transmitted is in the correct format for the receiving application to understand. Additionally, it handles the encryption and decryption of data for secure communication over the network.
Explanation of Application Layer Protocols
The Application Layer protocols are a set of rules and standards that govern the communication between applications on a network. Some of the most commonly used Application Layer protocols include HTTP (Hypertext Transfer Protocol) for web browsing, SMTP (Simple Mail Transfer Protocol) for email, FTP (File Transfer Protocol) for file transfer, and DNS (Domain Name System) for resolving domain names to IP addresses.
Definition of the Session Layer
The Session Layer is the fifth layer of the OSI (Open Systems Interconnection) model, which is responsible for managing and maintaining communication sessions between applications. This layer establishes, manages, and terminates connections between applications, and ensures that data is delivered error-free and in the correct order. The Session Layer also provides services such as authentication, authorization, and encryption to secure communication between applications. Examples of Session Layer protocols include NetBIOS (Network Basic Input/Output System) and RPC (Remote Procedure Call).
Role of the Session Layer in Data Transmission
The Session Layer plays a crucial role in data transmission by providing a reliable and secure communication channel between applications. It establishes, maintains, and terminates sessions between applications, allowing them to exchange data in an organized and controlled manner. The Session Layer also ensures that data is delivered error-free and in the correct order, by implementing mechanisms such as flow control, error detection, and retransmission. This helps to prevent data loss or corruption during transmission.
Explanation of Session Layer Protocols
The Session Layer protocols include:
1. Remote Procedure Call (RPC): This protocol allows communication between applications running on different systems by enabling a procedure call from one system to be executed on another system.
2. Session Control Protocol (SCP): This protocol manages the establishment, maintenance, and termination of sessions between applications. It also provides flow control and error recovery mechanisms.
3. Session Announcement Protocol (SAP): This protocol is used to announce the availability of sessions on a network.
Definition of the Data Link Layer
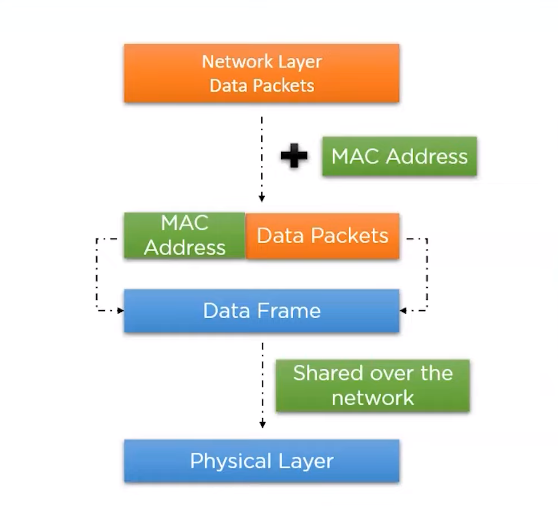
The Data Link Layer is the second layer of the OSI (Open Systems Interconnection) model and is responsible for providing reliable data transfer across a physical link. It takes the data from the Network Layer and formats it into a frame, adding a header and trailer to the data. The Data Link Layer also performs error detection and correction, flow control, and access control to the physical media. It is responsible for managing the communication between two adjacent network nodes and providing a means for error-free transmission of data.
Role of the Data Link Layer in Data Transmission
The Data Link Layer plays a crucial role in data transmission by providing reliable and error-free communication between two adjacent network nodes. It ensures that the data is transmitted correctly and efficiently across the physical link by performing several tasks.
Explanation of Data Link Layer Protocols
Data Link Layer protocols are responsible for managing the communication between two adjacent network nodes and providing a means for error-free transmission of data. There are two main types of Data Link Layer protocols: the Media Access Control (MAC) protocol and the Logical Link Control (LLC) protocol. The MAC protocol is responsible for controlling access to the physical medium, such as a network cable or wireless channel.
Definition of the Physical Layer
The Physical Layer is the lowest layer of the OSI (Open Systems Interconnection) model, which is responsible for the transmission and reception of raw bit streams over a physical medium, such as copper wires, optical fibres, or wireless channels. It defines the electrical, mechanical, and functional specifications for the physical connection between network devices. The Physical Layer also handles the encoding and decoding of data into a format suitable for transmission over the physical medium.
Role of the Physical Layer in Data Transmission
The Physical Layer plays a crucial role in data transmission. It is responsible for converting digital data into a format that can be transmitted over a physical medium, such as electrical signals, light waves, or radio waves. The layer also handles the modulation and demodulation of signals to ensure that they can be transmitted accurately and reliably. Additionally, the Physical Layer is responsible for managing the physical characteristics of the transmission medium, such as bandwidth, data rate, and signal strength.
Explanation of Physical Layer Protocols
The Physical Layer is responsible for implementing various protocols that ensure reliable and efficient transmission of data over a physical medium. Some of the commonly used Physical Layer protocols include Ethernet, Wi-Fi, Bluetooth, and USB. These protocols define the rules and procedures for transmitting data over the physical medium, including the type of cables, connectors, and other hardware required. Ethernet, for example, is a protocol that is widely used in local area networks (LANs) to connect computers and other devices.
Definition of the Network Layer
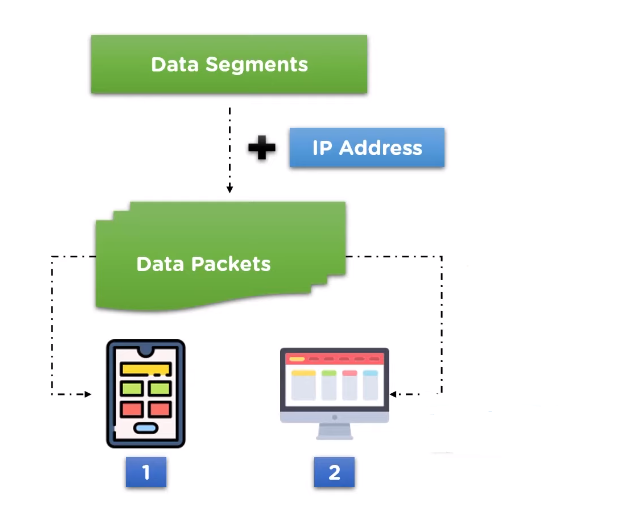
The Network Layer is the third layer of the OSI (Open Systems Interconnection) model that is responsible for providing end-to-end communication between devices on different networks. This layer is responsible for routing data packets from the source device to the destination device through multiple network devices such as routers, switches, and gateways. The Network Layer protocols include IP (Internet Protocol), ICMP (Internet Control Message Protocol), and ARP (Address Resolution Protocol).
Role of the Network Layer in Data Transmission
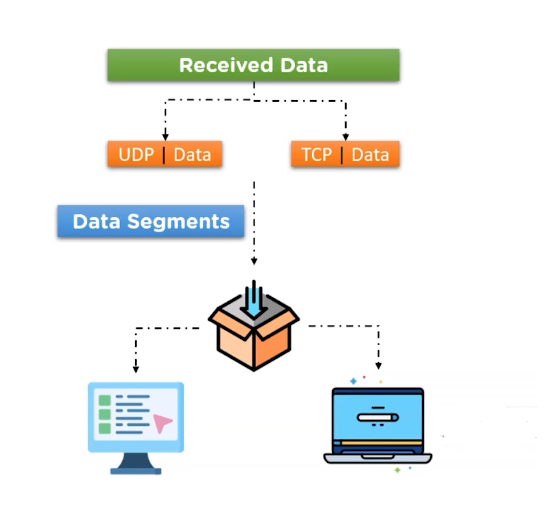
The Network Layer plays a crucial role in data transmission by ensuring that data packets are properly routed from the source device to the destination device across multiple networks. It provides logical addressing and routing services that enable communication between devices on different networks. The Network Layer protocols, such as IP, ICMP, and ARP, allow for the identification of devices on a network, the establishment of routes between them, and the management of network congestion.
Explanation of Network Layer Protocols
The Network Layer protocols are a set of rules and procedures that are used to facilitate communication between devices on different networks. These protocols provide logical addressing and routing services that enable data packets to be properly routed from the source device to the destination device across multiple networks. The Internet Protocol (IP) is one of the most commonly used Network Layer protocols. It is responsible for providing logical addressing services that enable devices to be identified on a network.
The Data Compression Process
The data compression process is a technique used to reduce the size of data by removing redundant or unnecessary information. This is done to save storage space and make the transmission of data more efficient. There are two types of data compression: lossless and lossy. In lossless compression, the original data can be completely recovered after compression. This is achieved by eliminating redundancy in the data without losing any information. Examples of lossless compression algorithms include ZIP, RAR, and GZIP.
The Data Encryption Process
Data encryption is the process of converting plain text into a coded message to prevent unauthorized access. Encryption is commonly used to secure sensitive data such as financial transactions, personal information, and confidential communications. The encryption process involves using an algorithm to scramble the data into an unreadable format, which can only be deciphered with a key or password.
Conclusion
In summary, lossless compression algorithms such as ZIP, RAR, and GZIP are effective ways to reduce the size of data files without losing any information. On the other hand, data encryption is a crucial process that helps protect sensitive information from unauthorized access. By using encryption algorithms, data can be converted into an unreadable format that can only be accessed with a key or password, ensuring that it remains secure.
