Overview of OSI Layers
The OSI (Open Systems Interconnection) model is a conceptual framework that describes the communication functions of a telecommunication or computing system. It is divided into seven layers, each of which corresponds to a specific set of functions and protocols.
Layer 1 – Physical Layer
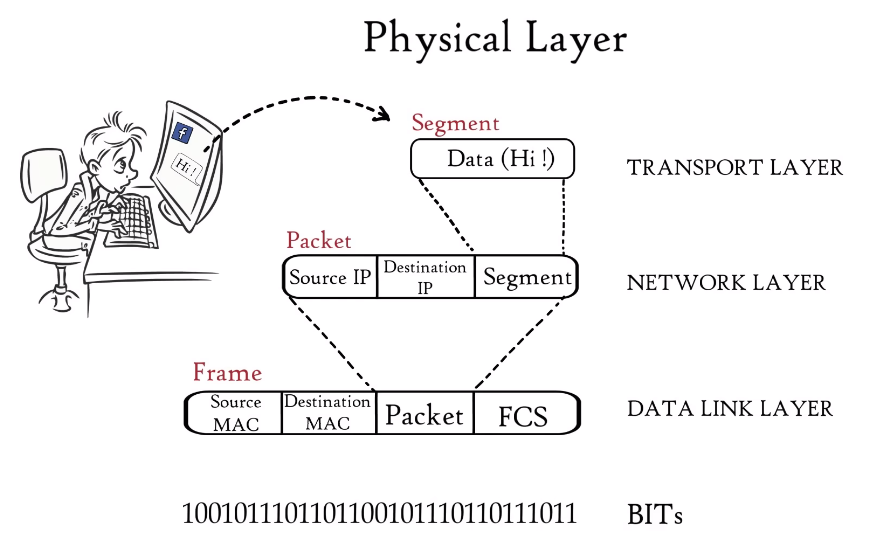
The Physical Layer is the lowest layer in the OSI model and is responsible for the transmission and reception of raw data between devices. It defines the physical characteristics of the communication medium, such as the voltage levels, data rates, and cable specifications. This layer also handles the conversion of digital data into analogue signals that can be transmitted over the communication medium and vice versa. Examples of devices that operate at the Physical Layer include network interface cards, hubs, and repeaters.
Advantages and Disadvantages of Physical Layer Encryption
Advantages:
– Physical Layer encryption can provide a basic level of security for data in transit.
– It can be used in conjunction with other security measures to create a layered security approach.
Disadvantages:
– Physical Layer encryption is not very secure as it is easy to use.
Layer 2 – Data Link Layer
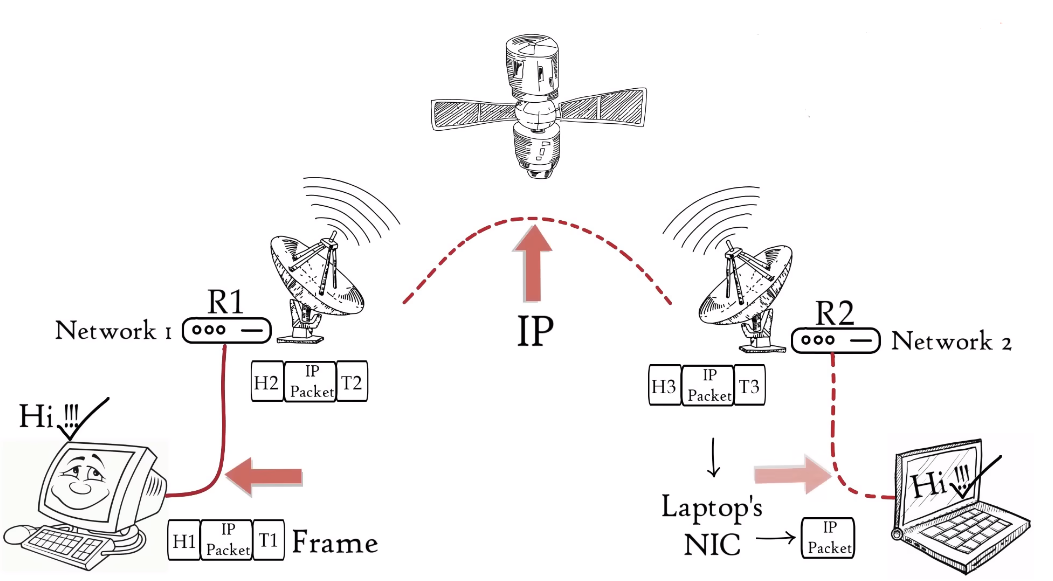
The Data Link Layer is responsible for the reliable transfer of data between two nodes on a network. This layer is divided into two sub-layers: the Media Access Control (MAC) Layer and the Logical Link Control (LLC) Layer. The MAC Layer is responsible for controlling access to the physical network medium, while the LLC Layer is responsible for error checking and flow control.
Advantages and Disadvantages of Data Link Layer Encryption
Advantages of Data Link Layer Encryption:
1. Provides an additional layer of security to the network.
2. Protects against unauthorized access to the network.
3. Helps to prevent data tampering and eavesdropping.
Disadvantages of Data Link Layer Encryption:
1. Can cause additional latency and slow down network performance.
2. Can be difficult to implement and manage.
3. May not be compatible with all network devices and protocols.
Layer 3 – Network Layer
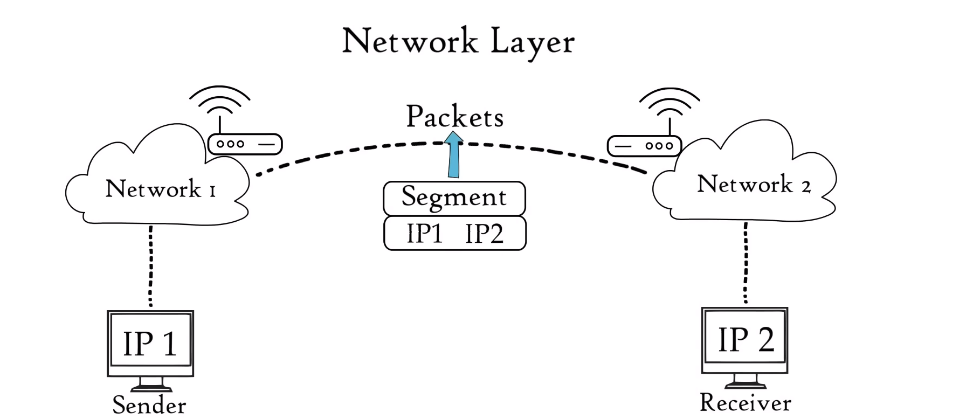
The Network Layer is the third layer of the OSI (Open Systems Interconnection) model, responsible for providing logical addressing and routing services for data packets. It determines the best path for data to travel from the source to the destination across multiple networks. The Network Layer also provides services such as fragmentation and reassembly of packets, congestion control, and error handling.
Advantages and Disadvantages of Network Link Layer Encryption
The advantages and disadvantages of the Network Layer are Advantages:
1. Provides logical addressing, which allows packets to be routed to their destination.
2. Enables the creation of virtual networks, which can improve network efficiency.
3. Allows for the implementation of network security policies, such as firewalls and intrusion detection systems.
Disadvantages:
1. Can cause additional latency and slow down network performance.
2. Can be complex to configure and manage, especially in large networks.
Layer 4 – Transport Layer
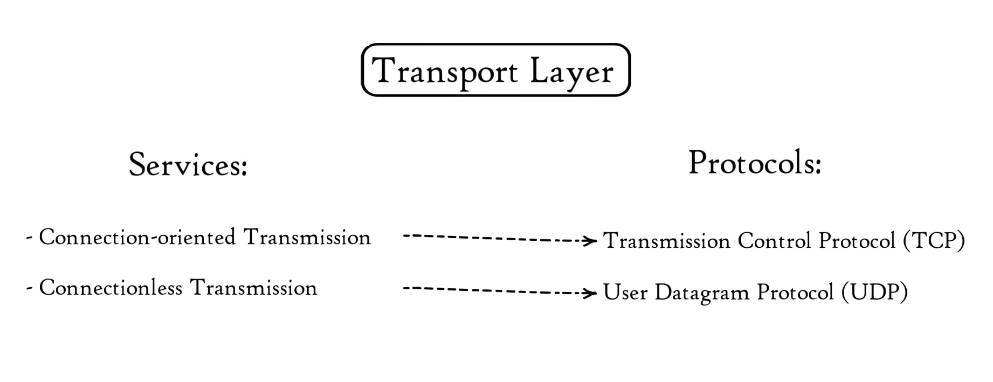
The Transport Layer is a layer in the OSI (Open Systems Interconnection) model and the TCP/IP (Transmission Control Protocol/Internet Protocol) model that provides end-to-end communication services for applications. It is responsible for ensuring reliable and efficient data transfer between network devices, and it accomplishes this by providing services such as error detection and correction, flow control, and congestion control.
Advantages and Disadvantages of Transport Layer Encryption
Advantages of the Transport Layer:
1. Provides reliable data delivery through mechanisms such as error detection and correction, flow control, and congestion control.
2. Enables multiplexing and demultiplexing of data streams, allowing multiple applications to share the same network connection.
3. Supports both connection-oriented and connectionless communication.
Disadvantages of the Transport Layer:
1. Can add overhead to the network traffic, which can impact performance.
2. May require additional configuration and management to ensure optimal performance
Layer 5 – Session Layer
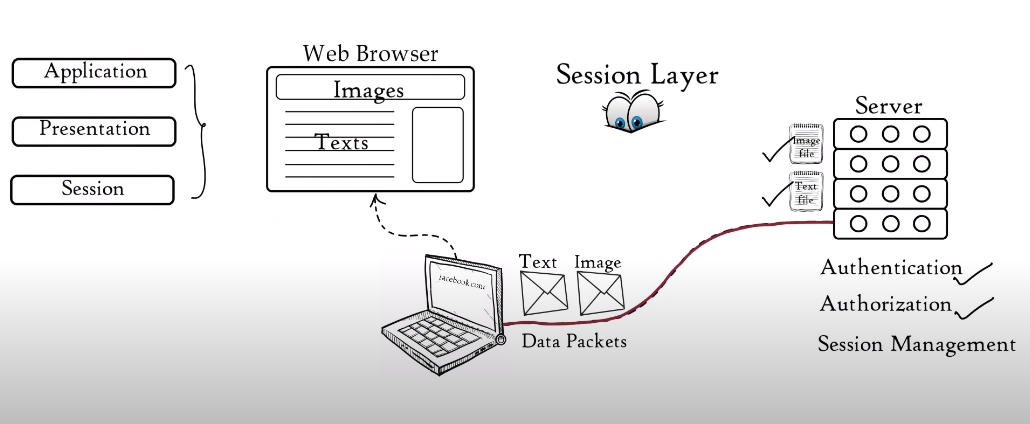
The Session Layer is responsible for establishing, maintaining, and terminating communication sessions between applications. It provides services such as session establishment, synchronization, and checkpointing.
Advantages and Disadvantages of Session Layer Encryption
Advantages of the Session Layer:
1. Allows applications to establish and manage sessions, which can improve communication reliability and efficiency.
2. Provides a mechanism for managing and coordinating communication between multiple applications.
Disadvantages of the Session Layer:
Can add additional overhead to network traffic, which can impact performance.
Layer 6 – Presentation Layer
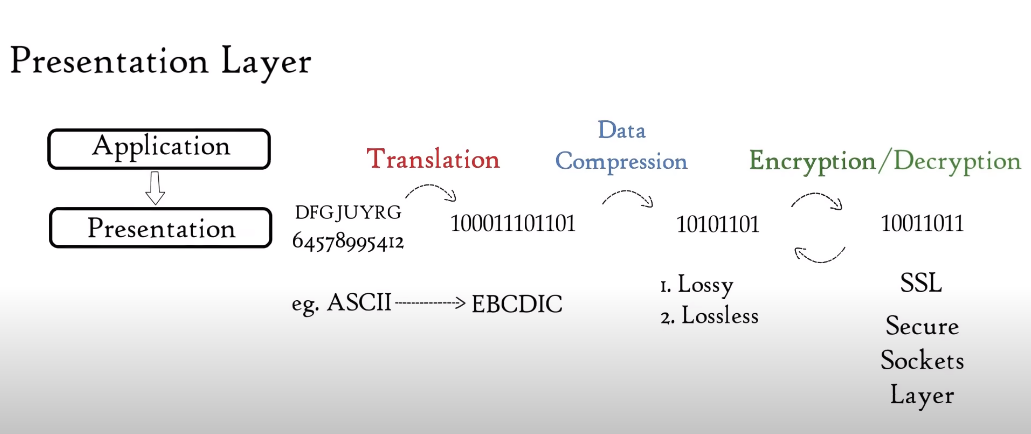
The Presentation Layer is responsible for the formatting and presentation of data to the application layer. It handles tasks such as data compression, encryption, and decryption. This layer ensures that data is presented in a format that can be understood by the application layer.
Advantages and disadvantages of Presentation Layer encryption
Advantages of Presentation Layer encryption:
1. Provides an additional layer of security to protect sensitive data.
2. Ensures that only authorized users can access and understand the data.
3. Helps to prevent unauthorized interception and tampering of data during transmission.
Disadvantages of Presentation Layer encryption:
1. Encryption can increase the processing overhead and slow down the data transmission.
2. Encryption can make it difficult to troubleshoot network problems and diagnose issues.
3. Encryption can also make it more difficult to integrate
Layer 7 – Application Layer
The Application Layer is the topmost layer in the OSI (Open Systems Interconnection) model of computer networking. It is responsible for providing services and protocols that enable user applications to access network resources and communicate with other systems. This layer interacts directly with the end-user applications and provides a platform for applications to exchange data over a network. Examples of protocols that operate at the Application Layer include HTTP, SMTP, FTP, and DNS.
Advantages and Disadvantages of Application Layer encryption
Advantages of Application Layer encryption:
1. Provides end-to-end encryption, ensuring that data remains secure throughout the entire communication process.
2. Offers more granular control over which data is encrypted and how it is protected.
3. Can be used to encrypt specific types of data, such as passwords or credit card numbers, while leaving other data unencrypted.
Disadvantages of Application Layer encryption:
1. Can be more complex to implement and manage than lower-layer encryption methods.
Factors to Consider When Choosing an Encryption Technique
- Security
- Performance
- Compatibility
- Cost
- Ease of implementation
Best Practices for Data Encryption Across OSI Layers
- Encryption key management
- Regular key rotation
- Multifactor authentication
- Regular system audits
- Secure backup and disaster recovery processes
Challenges of Data Encryption at OSI Layers
- Balancing Security and Performance
- Ensuring compatibility with legacy systems
- Compliance with regulatory requirements
- Addressing the threat of insider attacks
Conclusion
Data encryption is the process of transforming data into an unreadable format, also known as ciphertext, using an algorithm and a secret key. Encryption is a fundamental security measure that protects sensitive information from unauthorized access, interception, and tampering. Encryption can be applied at different layers of the OSI model, from the physical layer to the application layer, depending on the level of granularity and the security requirements.
FAQs
What is OSI?
OSI stands for Open Systems Interconnection, which is a conceptual model that describes how different communication systems can communicate with each other over a network. The OSI model has seven layers, each with its own set of protocols and functions, and it serves as a framework for designing and implementing network communication protocols.
What are the factors to consider when choosing an encryption technique?
There are several factors to consider when choosing an encryption technique, including:
1. Security level: The encryption technique should provide the required level of security to protect the data from unauthorized access.
2. Speed: The encryption technique should not significantly slow down the data transfer process.
3. Key management: The encryption technique should have a robust key management system to ensure the security of the keys used for encryption and decryption.
4. Compatibility: The encryption technique should be compatible with the systems and devices being used.
How can I ensure the effectiveness of data encryption across OSI layers?
To ensure the effectiveness of data encryption across OSI layers, you can follow this steps:
1. Understand the OSI model: To effectively implement data encryption across OSI layers, you must have a clear understanding of the OSI model and how it works.
2. Identify the layers that require encryption: Identify the layers within the OSI model that require encryption based on the sensitivity of the data being transmitted.
3. Choose the appropriate encryption technique: Choose an encryption technique that is appropriate for the layers that require encryption.
What are the challenges of data encryption at OSI layers?
Some of the challenges of data encryption at OSI layers include:
1. Compatibility: Different encryption techniques may not be compatible with different layers of the OSI model, which can make it difficult to implement encryption across all layers.
2. Performance: Encryption can slow down the transmission of data, which can impact the performance of the network.
3. Key management: Managing encryption keys can be challenging, especially when dealing with multiple layers and different encryption techniques.
