Data Encryption: An Overview
Data encryption is the process of converting plain text or data into a coded format that can only be accessed or deciphered by authorized parties. It is a crucial security measure that helps protect sensitive information from unauthorized access, theft, or tampering. Encryption works by using algorithms to scramble the data, making it unreadable without the correct decryption key. This key is typically only known by authorized parties who have been granted access to the encrypted data.
Encryption And Its Significance In Modern Information Security
Data encryption is a critical component of modern information security. With the increasing amount of sensitive information being stored and transmitted electronically, it has become essential to protect this data from unauthorized access. Encryption helps to ensure that sensitive data, such as financial information, personal data, and confidential business information, is kept secure and private. It helps to prevent data breaches and cyber attacks, which can have severe consequences for individuals and organizations.
Exploring The Primary Objectives of Data Encryption
Data encryption has several primary objectives, including:
1. Confidentiality: Encryption helps to maintain the confidentiality of sensitive data by ensuring that it can only be accessed by authorized individuals who have the necessary decryption keys.
2. Integrity: Encryption also helps to maintain the integrity of data by ensuring that it has not been tampered with or altered during transmission or storage.
3. Authentication: Encryption can be used to authenticate the identity of individuals accessing sensitive data, helping to prevent unauthorized access.
Cryptographic Algorithms: Foundation of Data Encryption
Cryptographic algorithms are the foundation of data encryption. These algorithms are complex mathematical functions that transform plain text into encrypted data that can only be decrypted with the appropriate key. There are two main types of cryptographic algorithms: symmetric and asymmetric. Symmetric algorithms use the same key for both encryption and decryption. This means that the key must be kept secret and secure, as anyone who possesses the key can decrypt the data. Examples of symmetric algorithms include Advanced Encryption Standard (AES) and Data Encryption Standard (DES).
Asymmetric algorithms, also known as public-key cryptography, use a pair of keys: a public key and a private key. The public key can be freely distributed, while the private key must be kept secret. Data encrypted with the public key can only be decrypted with the private key, and vice versa. Examples of asymmetric algorithms include RSA and Elliptic Curve Cryptography (ECC).
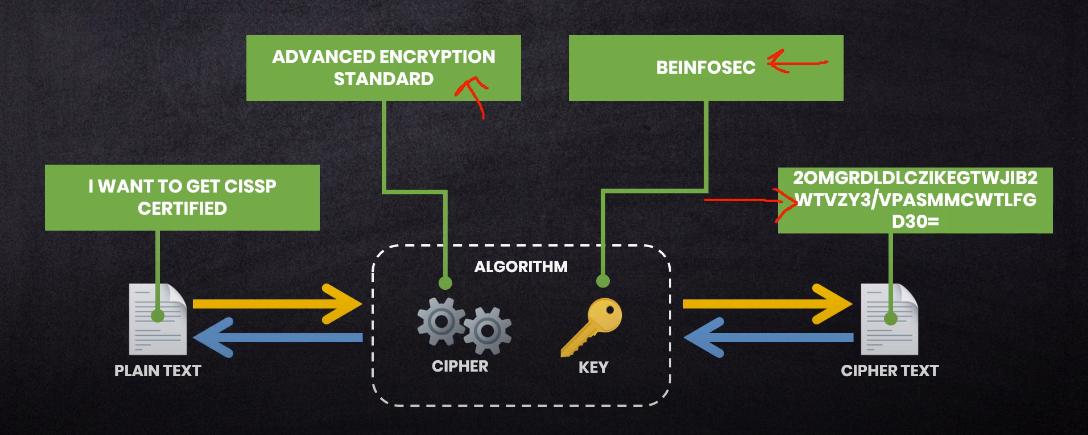
Encryption Process: From Plain Text to Cipher Text
The encryption process involves converting plain text into cypher text, which is unreadable without the proper decryption key. The process typically involves the following steps:
1. Key generation: A key is generated using either a symmetric or asymmetric algorithm.
2. Encryption: The plain text is encrypted using the key. In symmetric encryption, the same key is used for both encryption and decryption. In asymmetric encryption, the public key is used for encryption, and the private key is used for decryption.
Importance of Data Preparation Before Encryption
Data preparation is an important step before encryption because it can affect the security and effectiveness of the encryption process. Proper data preparation ensures that the data being encrypted is accurate, complete, and in the correct format. This helps to avoid errors or corruption during the encryption process that could compromise the security of the data. Additionally, data preparation can help to improve the efficiency of the encryption process. By reducing the amount of data that needs to be encrypted, the process can be completed more quickly and with fewer resources.
Key Generation and Management
Key generation and management are crucial aspects of the encryption process. A key is a piece of information that is used to encrypt and decrypt data. It is important to generate strong keys that are difficult to guess or crack, as weak keys can compromise the security of the encrypted data. Key management involves securely storing and distributing keys to authorized parties, as well as revoking or changing keys when necessary.
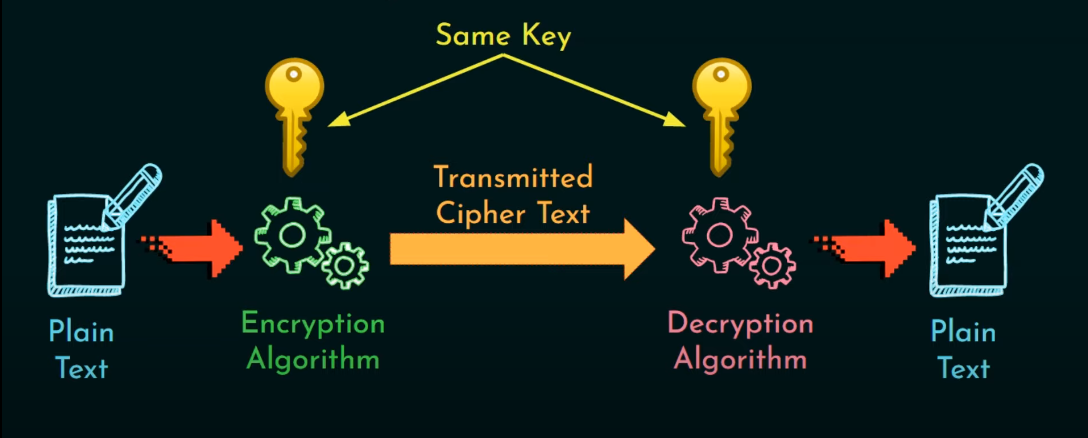
Encryption Phase
During the encryption phase, the plaintext (original message) is transformed into ciphertext (encrypted message) using a specific algorithm and the generated key. The ciphertext can only be decrypted back to plaintext using the same key that was used to encrypt it. This ensures that only authorized parties with the key can access the original message.
Post-Encryption Considerations
After the encryption phase, there are several post-encryption considerations that need to be taken into account. One important consideration is the secure storage and transmission of the encrypted message and key. This can involve using secure communication channels and storage methods, such as encryption of the data in transit and at rest. Another consideration is the management of the encryption keys. This includes securely storing and distributing keys to authorized parties, as well as revoking or changing keys when necessary.
Encryption Standards and Best Practices
When it comes to encryption standards and best practices, there are several key factors to keep in mind. First, it’s important to use strong, industry-standard encryption algorithms, such as AES or RSA. Additionally, it’s important to use long, complex encryption keys, ideally with a length of at least 256 bits. Another important best practice is to use a different encryption key for each piece of sensitive data, rather than using the same key for all data.
Compliance with Regulatory Frameworks
When it comes to compliance with regulatory frameworks, it’s important to understand the specific requirements that apply to your industry and region. For example, the General Data Protection Regulation (GDPR) in the European Union requires organizations to implement appropriate technical and organizational measures to protect personal data. Similarly, the Health Insurance Portability and Accountability Act (HIPAA) in the United States requires healthcare organizations to implement safeguards to protect patient health information.
Key Management and Storage
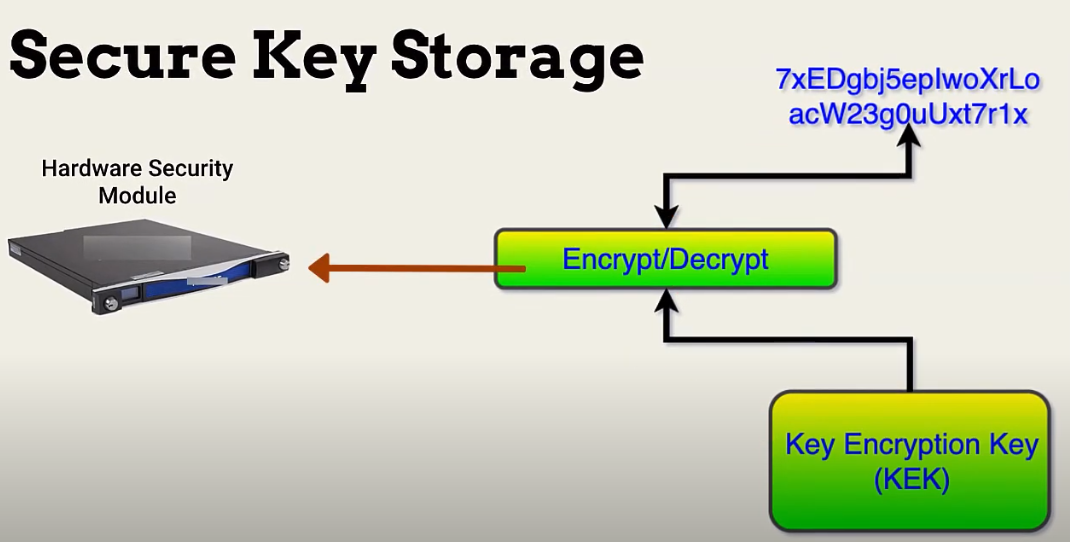
When it comes to key management and storage, it’s important to ensure that your organization has a secure and reliable system in place. This includes using strong encryption algorithms to protect sensitive data, as well as implementing access controls to restrict who can view or modify the keys. In addition, it’s important to have a backup system in place to ensure that keys are not lost or damaged. This can include using redundant storage systems or implementing a disaster recovery plan.
Encryption in Different Domains
Encryption is used in various domains to protect sensitive information. In the healthcare industry, encryption is used to protect patient data, such as medical records and personal information. This helps to ensure that only authorized personnel can access this information, protecting patient privacy. In the financial industry, encryption is used to protect sensitive financial information, such as credit card numbers and bank account information. This helps to prevent fraud and identity theft.
Challenges and Limitations of Data Encryption
While data encryption is an effective way to protect sensitive information, there are also some challenges and limitations associated with it. One challenge is that encryption can be resource-intensive, requiring additional processing power and storage space. This can be a problem for organizations with limited resources or older technology. Another challenge is that encryption can make data harder to access in certain situations. For example, if a user forgets their encryption key or password, they may not be able to access their own data.
Conclusion
In conclusion, encryption is a powerful tool for protecting sensitive information from unauthorized access. While it offers many benefits, such as increased security and privacy, it also comes with challenges and limitations that must be considered. Organizations should carefully weigh the pros and cons of encryption before implementing it, and ensure that they have the necessary resources and procedures in place to manage encrypted data effectively.
FAQs (Frequently Asked Questions)
How does data encryption work?
Data encryption is the process of converting plain text into a coded message that can only be read by authorized recipients with the corresponding decryption key. Encryption algorithms use complex mathematical formulas to scramble data, making it unreadable to anyone who doesn’t have the key to unlock it. This ensures that sensitive information, such as passwords, credit card numbers, and personal data, remains secure and protected from hackers and other unauthorized users.
What are cryptographic algorithms?
Cryptographic algorithms are mathematical procedures used in encryption to transform plain text into an unreadable form. There are many different types of cryptographic algorithms, including symmetric key algorithms, which use the same key for both encryption and decryption and asymmetric key algorithms, which use different keys for encryption and decryption. Cryptographic algorithms are designed to be highly secure and difficult to crack, ensuring that sensitive information remains protected. Some common cryptographic algorithms include AES, RSA, and SHA.
How are encryption keys generated and managed?
Encryption keys can be generated using a variety of methods, including random number generators, key derivation functions, and key exchange protocols. The method used to generate the key depends on the specific cryptographic algorithm being used. Once a key is generated, it must be securely managed to ensure the security of the encrypted data. Key management involves tasks such as key storage, key distribution, key rotation, and key revocation.
How secure is data encryption?
The security of data encryption depends on the strength of the encryption algorithm used and the security of the encryption key. Strong encryption algorithms use complex mathematical functions to scramble data in a way that is nearly impossible to reverse without the correct key. The security of the key, however, is equally important. If the key is weak or compromised, an attacker can easily decrypt the encrypted data. Therefore, it is important to use strong encryption algorithms and to manage encryption keys securely to ensure the security of encrypted data.
How does encryption protect data during transmission?
Encryption protects data during transmission by scrambling the data in a way that can only be unscrambled by someone with the correct key. When data is encrypted, it is transformed into a ciphertext that is unreadable and meaningless to anyone who intercepts it. The encrypted data is transmitted over the internet or other network and can only be unscrambled by the intended recipient who has the correct key.
