Introduction
Data security is of paramount importance for businesses of all sizes. Data breaches have become a common occurrence in recent years, affecting both small and large organizations alike. These security incidents occur when sensitive information, such as personal data or financial records, is accessed by unauthorized individuals. The financial losses incurred from data breaches can be significant; not to mention the damage done to a company’s reputation.
To prevent data security breaches, companies must take proactive measures such as implementing strong password policies, encrypting sensitive information and conducting regular employee training sessions on cybersecurity best practices. In addition, organizations can employ advanced technologies like artificial intelligence (AI) and machine learning algorithms that can detect abnormal behaviour within their network systems in real-time and alert security teams to potential threats before any damage is done.
Data breaches can be a costly affair for businesses of all sizes. The cost of a data breach is not limited to just the financial aspect but also includes the loss of reputation and customer trust.
Understanding Data Security Breaches
What Is A Data Breach?
A data breach is an incident where sensitive or confidential information has been accessed, disclosed, or stolen by an unauthorized party. This can occur due to various reasons such as hacking attacks, malware infections, physical theft of devices containing sensitive information or even accidental disclosure by employees. Once a data breach occurs, the attackers may use the information obtained for fraudulent activities such as identity theft and financial fraud.
The consequences of a data breach can be severe and long-lasting for both individuals and organizations. It can damage reputations and result in legal penalties and fines. In addition to the immediate financial impact of remediation efforts following a data breach, companies may also have to deal with a loss of customers’ trust and decreased revenue.
Preventing data breaches requires continued vigilance through implementing security measures such as strong passwords policies, employee training on safe online behaviors, regular software updates that fix known vulnerabilities among others.
Types Of Data Breaches
Physical theft or loss of devices: In this case, the thief gains access to all the data on these devices, which could include personal identification information (PII) such as social security numbers and banking details.
Malware attacks: Malware can be in the form of viruses or Trojan horses that infect computers through email attachments or downloads from untrusted websites.
Internal threats: There are also internal threats where employees accidentally expose sensitive information through human error such as misplacing documents containing PII or sending emails to unintended recipients. Effective training and strict policies regarding handling sensitive information can help prevent such breaches from occurring.
Assessing Your Data Security Risks
Identify Your Most Sensitive Data
This could include personally identifiable information (PII) such as social security numbers, credit card information, and medical records. It may also include confidential business information such as financial statements, trade secrets or strategic plans.
Once you have identified what data needs to be protected, it is crucial to implement strict security measures to ensure its safety. This may involve restricting access to certain employees who do not need the data for their job functions and utilizing encryption technologies for secure storage and transmission of sensitive data.
Evaluate Your Current Security Measures
Start by reviewing your website’s security protocols, such as using SSL encryption and firewalls. Ensure that all software and plugins are up-to-date with the latest security patches, and consider implementing two-factor authentication for added protection.
Another aspect to evaluate is your password policy. Encourage employees to use strong passwords or passphrases that include uppercase and lowercase letters, numbers, and special characters. Additionally, limit access to sensitive information only to those who need it.
Conduct regular vulnerability scans and penetration testing to identify any potential weaknesses in your system before a hacker can exploit them. By taking these steps, you can significantly reduce the risk of a data breach occurring within your organization.
Perform A Security Risk Assessment
A thorough risk assessment will identify potential vulnerabilities in your organization’s systems, processes, and policies that could be exploited by hackers or other malicious actors. The assessment should include a comprehensive review of all hardware and software used within your organization, as well as an examination of access controls such as passwords and user permissions.
Once vulnerabilities have been identified, they can be prioritized based on the level of risk they pose to the organization. This allows for the development of a targeted approach to mitigating risks and strengthening security measures across all areas of the organization. It’s important to note that performing a security risk assessment is not a one-time event; it should be done regularly to ensure ongoing protection against evolving threats.
Best Practices For Preventing Data Security Breaches
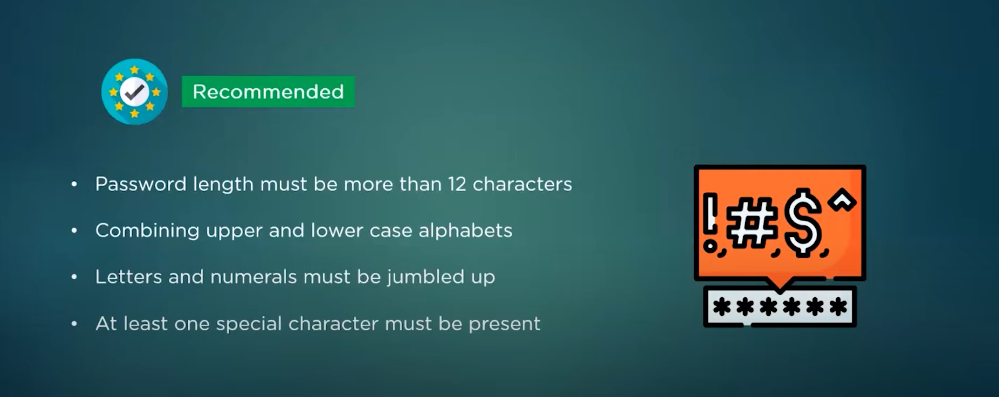
Strong Password Policies
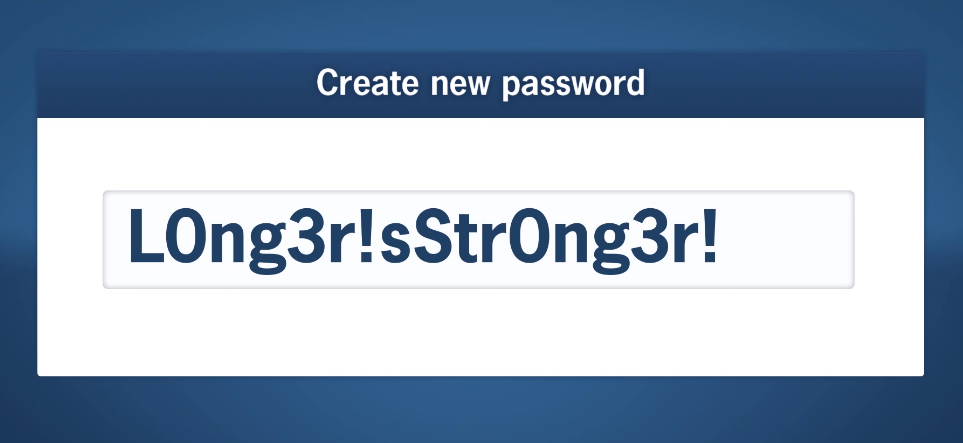
A good password policy should include guidelines such as minimum length requirements, complexity requirements (including the use of uppercase and lowercase letters, numbers, and special characters), and mandatory regular password changes. It is also important to educate employees on best practices for creating secure passwords, such as avoiding easily guessable information like birthdays or pet names.
Multi-Factor Authentication
Multi-factor authentication (MFA) is a security measure that requires users to present two or more pieces of evidence to verify their identity. It’s an effective way for businesses to protect their data from unauthorized access, especially in an era where cyber threats are evolving at an alarming rate.
With MFA, users have to provide something they know (such as a password), something they have (like a smart card or token), or something they are (like biometric identifiers such as fingerprints). This approach significantly reduces the risks associated with stolen passwords and other common vulnerabilities that cybercriminals exploit. While no security system is foolproof, using multiple factors makes it much harder for attackers to penetrate sensitive systems.
Regular Security Updates
Regular security updates are essential for protecting your data from potential security breaches. These updates often include critical security fixes that address known vulnerabilities, so failing to install them could leave your system at risk.
Data Encryption
Encryption can be applied at various levels, including in transit and at rest. In-transit encryption protects data as it is being transmitted from one point to another over a network, such as when you send an email or share files via cloud storage services. At-rest encryption protects data stored on devices such as hard drives or USBs.
Secure Data Disposal
Secure data disposal methods include degaussing, physical destruction, and software-based solutions. Degaussing involves using a magnetic field to erase all traces of data from hard drives and tapes, rendering them unusable afterwards. Physical destruction involves shredding or crushing storage media devices such as hard drives and USBs until they are rendered irrecoverable. And finally, software-based solutions involve overwriting deleted files with meaningless characters several times until it’s impossible to recover any meaningful information.
Restricting Access To Sensitive Data
Only authorized personnel should be allowed to view, modify or delete confidential information. To achieve this, businesses need to implement a stringent access control policy that limits access to sensitive data based on the principle of least privilege.
This policy ensures that employees only have access to the minimum amount of information needed to do their job effectively. Additionally, companies should also ensure their employees are trained on how to handle sensitive data properly and understand the consequences of mishandling it.
Implementing Firewalls And Antivirus Software
Firewalls act as a barrier between your network and the internet, blocking unauthorized access to your system. It monitors incoming and outgoing traffic, identifying potential threats before they can cause damage. Installing a firewall is an effective way of keeping hackers out of your network.
Antivirus software is another essential tool that helps protect your system from malicious programs, such as viruses, worms, and Trojans. Antivirus software scans for threats on your computer or device in real time or at scheduled intervals to detect any suspicious activity. It then removes or quarantines any detected malware from the system.
Regular Security Training For Employees

It is essential to educate all employees on how they can contribute to maintaining a secure work environment, including ways to identify potential threats and how to respond in the event of a breach.
Regular security training should cover topics such as password management, phishing emails, and social engineering scams. Employees should be taught how to create strong passwords that are hard for hackers to guess and techniques for identifying fraudulent emails or phone calls that may be used by attackers.
Responding To A Data Security Breach
Steps To Take When You Discover A Breach
When you discover a security breach, it’s crucial to act fast and take the necessary steps to minimize the damage.
Notification Requirements
Notification should be given to affected individuals as soon as possible. However, some states have specific timeframes for notification and require businesses to notify the state attorney general or other regulatory agencies.
It is important to note that not all data breaches require notification. Some minor breaches may not pose a significant risk to affected individuals and do not need to be reported. However, it is always best practice to err on the side of caution and notify individuals if there is any doubt about whether their personal information has been compromised.
Containment And Recovery
Containment involves identifying the source of the breach, isolating it and taking necessary measures to stop further damage from occurring. This includes shutting down affected systems, disabling user accounts and changing passwords. Additionally, containment also involves preserving evidence for forensic analysis to determine the cause of the breach.
Recovery is equally important as it involves restoring systems back to their original state before the breach occurred. Depending on the severity of the breach, this may involve reinstalling operating systems, restoring backups or rebuilding entire servers from scratch. It is important to have a comprehensive disaster recovery plan in place beforehand so that these steps can be taken quickly and efficiently.
Data Restoration
Data restoration refers to the process of recovering lost or damaged data from backups or other sources. It’s important to have a backup strategy in place so that you can quickly and efficiently restore your data in case of an emergency. This includes regularly backing up your files and making sure that those backups are stored securely off-site.
There are many tools and software available for data restoration, but it’s important to choose one that suits your needs and budget. Some options include file-level backup/restore software, disk imaging software, cloud backup services, and more advanced disaster recovery solutions for large enterprises.
Compliance And Legal Considerations
Data Privacy Regulations
With the rise of cyberattacks and data breaches, governments around the world have implemented laws to protect individuals’ personal information. One of the most well-known data privacy regulations is the General Data Protection Regulation (GDPR) introduced by the European Union in 2018. The GDPR gives individuals more control over their personal data and requires organizations to obtain explicit consent before collecting, processing, or storing their data.
In addition to the GDPR, other countries have also implemented their own data privacy regulations. For example, California introduced a landmark privacy law called the California Consumer Privacy Act (CCPA), which went into effect on January 1st, 2020. The CCPA grants Californians new rights regarding their personal information and imposes strict obligations on businesses operating in California.
Liability And Legal Responsibilities
In terms of liability, companies may be held responsible for any damages caused by a data breach, including loss of customers’ personal information or intellectual property theft. Organizations that collect personal information are also required by law to inform individuals if their data has been compromised. Failure to do so could result in significant fines or even legal action.
Fines And Penalties For Non-Compliance
Under the General Data Protection Regulation (GDPR), businesses found guilty of violating data protection laws could face fines of up to €20 million or 4% of their global annual revenue, whichever is greater. In addition to these financial penalties, companies may also face lawsuits from individuals affected by breaches, leading to further costs and potential reputational damage.
Planning For The Worst: Creating A Data Breach Response Plan
Developing A Response Team
A response team is critical to every organization’s data security strategy. In the event of a security breach, having a pre-established team in place can help mitigate damage and prevent further harm. The first step in developing a response team is identifying key stakeholders across various departments, including IT, legal, HR, and communications.
Define their roles and responsibilities. This includes outlining who will be responsible for communicating with affected parties, managing media relations, and investigating the cause of the breach. Additionally, it’s essential to establish clear protocols for reporting incidents and responding promptly.
Documenting Procedures And Policies
A well-documented set of procedures and policies provides a reference point for all employees when handling sensitive data, ensuring that everyone is on the same page. Employees should be trained on these documents regularly to ensure they are up-to-date with any changes or new protocols. In addition, organizations should consider using technology solutions like automated policy management tools to streamline compliance processes and monitor adherence.
Testing Your Response Plan
After creating a response plan for data breaches, it’s essential to test the plan regularly. Testing helps identify weaknesses in the plan and provides an opportunity to improve it before an actual breach occurs.
There are various ways to test your response plans, such as tabletop exercises or simulated attacks. Tabletop exercises involve walking through hypothetical scenarios with key stakeholders and discussing how they would respond. Simulated attacks mimic real-life situations to assess the preparedness of your organization’s response team.
Protecting Your Business Partners And Vendors
Assessing Your Third-Party Risks
Organizations often rely on third-party vendors and suppliers for various services, including IT support, cloud storage, and financial processing. However, these third parties may not have the same level of security measures in place as the organization itself, which can create vulnerabilities that cybercriminals can exploit.
To assess your third-party risks, start by identifying all of the vendors and suppliers that you work with. Evaluate their security practices and policies to determine if they meet your organization’s standards. This should include a thorough review of their data handling processes, encryption methods, network security protocols, and employee training procedures.
It’s also important to monitor your third-party relationships on an ongoing basis to ensure that they continue to prioritize data security. Regularly reviewing contracts and service level agreements (SLAs) can help identify any potential gaps or vulnerabilities in these partnerships so that corrective action can be taken before a breach occurs.
Contractual Security Obligations
These obligations are usually outlined in contracts between the data controller and processor. In essence, these agreements specify the steps that must be taken by both parties to ensure the confidentiality, integrity, and availability of personal data.
Typically, contractual security obligations require service providers to use appropriate technical and organizational measures to protect against unauthorized access or disclosure of personal information. They also mandate prompt reporting of any breaches or suspected breaches involving such data. Additionally, these agreements may require periodic audits or assessments of a service provider’s information security program.
To ensure compliance with contractual security obligations, organizations should conduct thorough due diligence when selecting third-party vendors or service providers. This process involves reviewing their policies and procedures for protecting confidential information as well as assessing their overall level of risk management competence.
Conclusion
Safeguarding your data is paramount in today’s digital age. Data breaches can have devastating consequences for both individuals and businesses alike. It is essential to implement a robust security system that incorporates the latest technologies and strategies. This includes firewalls, anti-virus software, secure passwords, encryption protocols, and employee training programs.
FAQs
How Can I Assess My Organization’s Data Security Risks?
To assess your organization’s data security risks thoroughly, you need to examine the technical and human aspects of your operation. Your technical assessment should focus on system vulnerabilities, including firewalls, anti-virus software, and intrusion detection systems. The human element involves gauging employees’ understanding of cybersecurity policies and procedures.
What Are Some Common Insider Threats To Data Security?
The accidental disclosure of sensitive information. This can occur when an employee mistakenly sends an email or shares a document with confidential data to the wrong recipient. Carelessness in handling sensitive information can also lead to insider threats, as employees may leave their computers unlocked or fail to properly dispose of paper documents containing confidential data.
Malicious intent. This can come from disgruntled employees seeking revenge against employers or co-workers, or from individuals who have been bribed or coerced into stealing sensitive information. These insiders may use their access privileges to steal trade secrets, customer data, financial records, and other valuable information.
In addition to intentional and accidental insider threats, there are also unintentional insider threats caused by employees who fall victim to phishing scams or other cyber attacks that compromise their login credentials. Cybercriminals then use these stolen credentials to gain access to company networks and databases.
What Are The Emerging Technologies And Trends In Data Security?
The use of artificial intelligence (AI) in data security: AI can analyze large amounts of data and quickly recognize patterns, anomalies, and potential threats. This technology is particularly useful in detecting sophisticated attacks that traditional security measures may miss.
The use of blockchain technology: Blockchain is a decentralized digital ledger that records transactions securely and transparently. The decentralized nature of blockchain makes it difficult for hackers to breach since they would need to hack multiple blocks across a network simultaneously.
Cloud-based solutions are also increasingly being used for data storage and management due to their convenience, scalability, cost-effectiveness, and reliability. However, with the growing reliance on these solutions comes increased vulnerability to cyber-attacks which can lead to serious consequences such as reputational damage or financial loss if not properly secured.
