Introduction
Explanation Of What Data Encryption Is
Data encryption is converting plain text into an unreadable format to protect the data from unauthorized access. Those with the key or password can only read the encrypted data to decrypt it. Encryption is one of the most effective ways to secure data, especially in today’s digital age, where cyber-attacks are rising.
Importance Of Data Encryption

Data encryption is becoming increasingly important in today’s digital age, with the rise of cyber-attacks and data breaches. Encrypting sensitive information, such as personal or financial data, becomes unreadable to anyone without the proper decryption key. This ensures that even if hackers gain access to the data, they cannot use or read it without permission.
A Brief History Of Data Encryption
The invention of telegraphy in the 19th century led to more sophisticated encryption methods, such as polyalphabetic cyphers and rotor machines. During World War II, encryption played a crucial role in military operations with Axis and Allied powers using various encryption techniques.
Recently, computer technology has revolutionized data encryption, with algorithms such as RSA becoming popular for securing online communication. Today’s digital world relies heavily on data security measures like end-to-end encryption and SSL/TLS protocols that encrypt traffic between websites and users’ devices. As technology continues to evolve, so will techniques for securing private information from unauthorized access.
Types of data encryption
Various types of data encryption are available for securing sensitive information online, such as symmetric key encryption, asymmetric key encryption and hashing.
What Is Data Encryption?
Definition Of Data Encryption
Data encryption is transforming data into an unreadable format to protect it from unauthorized access. Encryption uses algorithms, or mathematical formulas, to scramble the data so that only authorized individuals with the appropriate decryption key can access and read it. Data encryption is crucial for protecting sensitive information, such as financial transactions or personal information, from falling into the wrong hands.
How Data Encryption Works
Data encryption is the process of converting plain text into encoded ciphertext, making it unreadable to anyone who doesn’t have the key. Encryption algorithms use complex mathematical formulas to transform data into an unreadable format. The most common type of encryption used today is AES (Advanced Encryption Standard), developed by the National Institute of Standards and Technology in 2001.
AES uses a symmetric-key algorithm, meaning that both the sender and receiver must have access to the same key to encrypt and decrypt messages. The algorithm consists of several rounds of substitution, permutation, and shifting operations that scramble the plaintext into a seemingly random sequence of bits. During each round, a different set of keys is applied to obfuscate the message further.
Difference Between Encryption And Decryption
Encryption algorithms use mathematical functions to convert plain text into a series of numbers or symbols that can only be deciphered using a specific key. The key can be a password, passphrase or any other information used in the encryption process. Decryption involves using the same key to convert the encrypted message to its original form.
Importance Of Data Encryption
Protecting Sensitive Data From Unauthorized Access
One of the most important things organizations can do is protect their sensitive data from unauthorized access. Encryption involves converting data into an unreadable format that someone with the right decryption key can only decipher.
Compliance With Data Protection Regulations
Encryption is a commonly used technique to ensure compliance with these regulations. By encrypting data, businesses can protect the confidentiality and integrity of their customer’s personal information.
The General Data Protection Regulation (GDPR) is the most common data protection regulation. GDPR requires businesses to take appropriate measures to protect personal data, including encryption. Failure to comply with GDPR can result in hefty fines and damage to reputation.
Mitigating Cyber Threats And Attacks
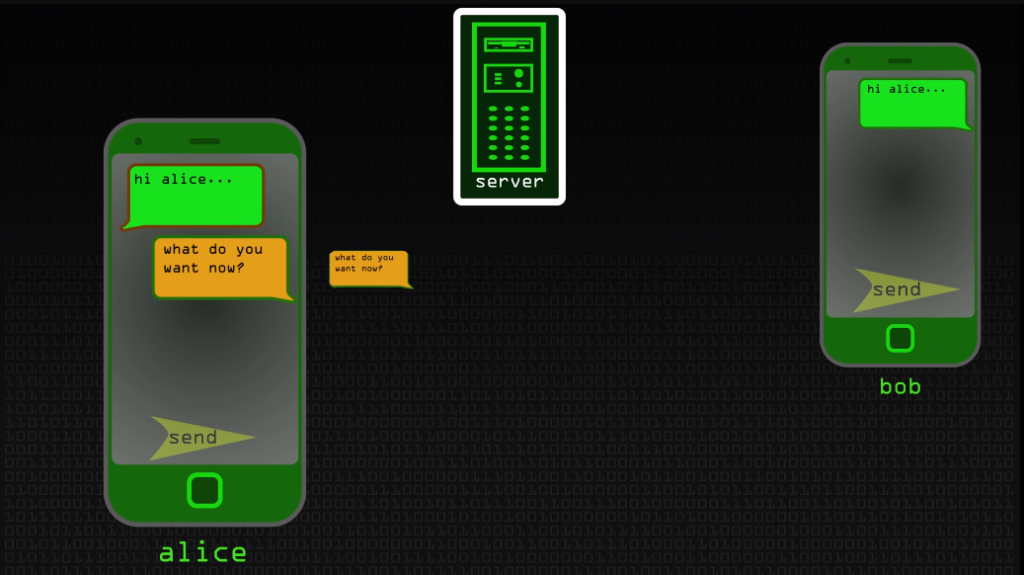
Encryption helps prevent unauthorized access to sensitive information. Companies should consider adopting end-to-end encryption (E2EE) for all data transmissions between devices or networks as an additional layer of protection.
Preserving Data Integrity And Confidentiality
Data encryption provides an excellent solution for preserving data confidentiality. It ensures that even if hackers intercept the data during transmission or steal it from storage devices, they cannot read it without the decryption key.
Types Of Data Encryption
Symmetric Encryption
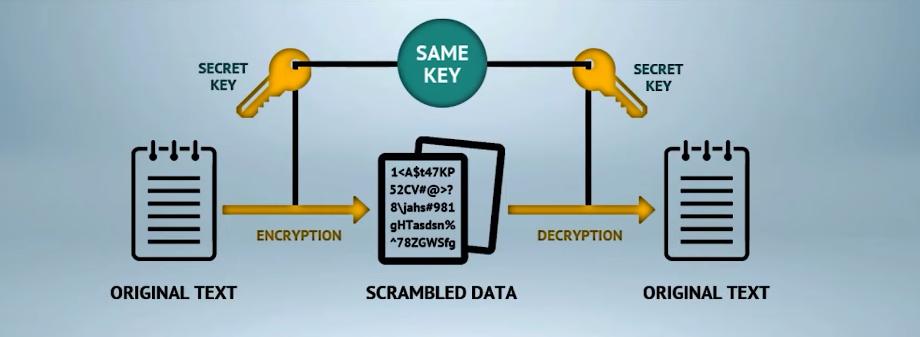
It is a type of encryption where the sender and receiver share a common secret key to encrypt and decrypt messages. This method is called symmetric because the same key is used for encryption and decryption.
Symmetric encryption provides high-speed data transfer as it uses simple algorithms that are easy to implement. However, this method of data protection has some drawbacks as well. The biggest drawback with symmetric encryption is that if someone gains access to the key, they can easily decrypt all encrypted data.
Asymmetric Encryption
Asymmetric encryption, also known as public-key cryptography, is a type of data encryption that uses two public and private keys to secure communication between two parties. The public key is widely distributed and can be accessed by anyone who wants to send an encrypted message to the private key owner. On the other hand, the private key is kept secret by its owner and is used to decrypt any encrypted message with the corresponding public key.
Hybrid Encryption
Hybrid encryption is a method of encrypting data that combines the best features of both symmetric and asymmetric encryption. This type of encryption leverages both techniques to provide an extra layer of security, making it more difficult for attackers to intercept or tamper with sensitive information.
In this process, the symmetric key algorithm encrypts large amounts of data because it’s faster and more efficient. However, the key used for this process is encrypted using an asymmetric public key algorithm, enabling only authorized users or systems to decrypt it. This combination helps prevent hackers from accessing sensitive information by creating a secure channel between two parties.
Stream Cypher And Block Cypher
Stream cyphers encrypt the data one bit or byte at a time, allowing for real-time encryption of streamed data such as video or audio. They generate a key stream that is XOR’d with the plaintext to produce ciphertext. The key stream can be generated using mathematical functions or derived from an initial value known as the seed.
Block cyphers, on the other hand, encrypt fixed blocks of data at a time, typically 64 or 128 bits in length. The input is divided into fixed-size blocks, and each block is encrypted separately using a symmetric key algorithm such as AES (Advanced Encryption Standard). Block cypher modes like ECB (Electronic Codebook) and CBC (Cipher Block Chaining) are commonly used to extend functionality and address security issues.
How Data Encryption Works
Encryption Process Step-By-Step
The data encryption process involves converting plain text into scrambled data that can only be read by the intended recipient with the decryption key. Here are the steps involved in an encryption process:
- Select a suitable encryption algorithm: The first step is to choose an appropriate algorithm, such as AES or RSA, based on your security needs.
- Generate a key: A random string of bits will be generated to determine how the plaintext is encrypted.
- Convert plaintext to ciphertext: To encrypt data, you must convert it from plain text into ciphertext using the chosen algorithm and encryption key.
- Store or transmit encrypted data: After encrypting, store or transmit this encrypted data so no unauthorized person can access it.
- Decrypt ciphertext back to plaintext: When you want to access the original message again, use your decryption key to decrypt it back into readable format.
- Verify the integrity of decrypted message: Finally, ensure there has been no tampering with your decrypted message by verifying its integrity through hashing algorithms like SHA-256.
Decryption Process Step-By-Step
The decryption process involves converting ciphertext back into plaintext using a secret key or password. Different methods for decrypting data depend on the encryption algorithm used.
To decrypt data, you need access to the same key used during the encryption process. The first step is to enter the key into a decryption program or software. This will allow you to generate an output representing the original message before encryption.
The next step involves running this output through a decryption algorithm that reverses the mathematical operations carried out during encryption. The result should be readable in plaintext that can be understood by anyone who has access to it. It’s important to note that decryption won’t be possible if you don’t have access to the same key used for encryption.
Mathematical Principles Behind Data Encryption
One of the most important mathematical principles behind data encryption is using prime numbers. Prime numbers are unique integers that can only be divided by 1 and themselves without leaving a remainder. This property makes them ideal for use in cryptographic algorithms.
Another mathematical principle used in data encryption is modular arithmetic. Modular arithmetic involves computing remainders after division, usually by a predefined number called the modulus. In cryptography, modular arithmetic performs various operations on large numbers, such as multiplying or exponentiating them.
The RSA algorithm is one of the most widely-used encryption methods today. This algorithm relies on two important concepts: public-key cryptography and prime factorization.
Encryption Standards And Technologies
AES Encryption
AES, or Advanced Encryption Standard, is a commonly used encryption algorithm that provides high levels of security for data communication. This symmetric key block cypher operates on fixed-length plaintexts and transforms them into ciphertexts using a secret key. It works by dividing the input data into blocks of 128 bits and then applying a series of substitution and permutation operations to each block.
RSA Encryption
The security of RSA encryption relies on the fact that it is extremely difficult to factorize large numbers into their prime factors. The larger the number used in RSA encryption, the more secure it becomes. Some experts believe that with a large enough number, RSA encryption could be unbreakable.
Diffie-Hellman Key Exchange
Diffie-Hellman key exchange is a cryptographic protocol used in secure communication. It is a method of exchanging cryptographic keys over a public channel, such as the internet, without sharing any secret information.
The basic principle of the Diffie-Hellman key exchange is that two parties who want to communicate securely can agree on a shared secret without revealing it to anyone else. The shared secret can then be used as the basis for the encryption and decryption of messages between the two parties.
ECC Encryption
ECC (Elliptic Curve Cryptography) relies on the mathematical properties of elliptic curves to generate keys and encrypt data, making it more difficult for attackers to break the encryption.
One advantage of ECC over other encryption techniques is its smaller key size. A 256-bit ECC key provides the same level of security as a 3072-bit RSA key, which means that ECC can provide stronger protection with less overhead.
Common Uses Of Data Encryption
Protecting Confidential Information In Businesses
Confidential data can be anything from trade secrets, customer information, financial records, etc. With cybercrime on the rise, it’s essential to take proactive measures to secure your company’s data. Data encryption is one of the best ways to protect confidential information.
Securing Online Transactions And Banking

One of the most common encryption methods used in online banking is the Secure Sockets Layer (SSL). It encrypts data as it travels between a user’s device and the bank’s server. Another method banks use is Transport Layer Security (TLS), which provides a more secure connection than SSL.
Encrypted Messaging And Communication
Encrypted messaging services like Signal, Telegram, and WhatsApp allow users to send messages protected by encryption algorithms, making them virtually impossible to intercept or read by unauthorized third parties.
Securing Cloud Storage And Data Backups
Encryption plays a vital role in safeguarding data, which involves converting plain text into a coded form that can only be deciphered with the correct decryption key. When it comes to cloud storage, businesses should opt for providers that implement robust encryption methods to ensure the confidentiality of their data.
Encryption In Government And Military
Various types of encryption methods are available for government and military use, including symmetric-key encryption, public-key encryption, and hash functions. Symmetric-key encryption involves using one secret key to encrypt and decrypt data. Public-key encryption uses two keys – a public key for encrypting data and a private key for decrypting it. Hash functions create fixed-length outputs that represent an entire set of data.
Advantages Of Data Encryption
Protection Against Data Theft And Cyber Attacks
Data encryption is crucial in protecting sensitive information against theft and cyber attacks. Encryption scrambles data, making it unreadable to anyone without the proper decryption key. The use of encryption can be as simple as encrypting individual files or as complex as encrypting entire databases or networks.
One popular form of encryption is end-to-end encryption (E2EE), which provides an extra layer of protection by ensuring that only the sender and recipient can access the data being exchanged. This type of encryption is commonly used in messaging apps like WhatsApp and Signal.
Ensuring Compliance With Data Protection Regulations
Organizations must implement robust encryption protocols throughout their systems and networks to ensure compliance with data protection regulations. This includes encrypting all sensitive information during transmission and storage, regularly monitoring and updating encryption tools, and providing secure access controls to prevent unauthorized access. Companies also need to train employees on properly handling sensitive information, including following strict security protocols when accessing protected files or transferring them internally.
Building Trust With Customers And Stakeholders
When businesses implement encryption in their data protection strategy, they commit to protecting their customers’ information. This conveys that they take cybersecurity seriously and are willing to invest in the necessary tools and resources to safeguard sensitive data.
Preventing Data Breaches And Reputation Damage
Data breaches can cause irreparable damage to an organization’s reputation, leading to significant financial losses and customer distrust. To prevent data breaches, organizations must prioritize data encryption. Encryption converts plain text or data into a code that can only be deciphered with a specific key or password. By encrypting sensitive information like customer data, payment details, and intellectual property, companies can make it nearly impossible for hackers to access their valuable assets.
Disadvantages Of Data Encryption
Performance And Speed Issues
While encryption is necessary for securing sensitive information, it can also slow down systems and cause performance issues. Encryption algorithms use complex mathematical calculations that demand significant computing power, leading to slower systems. However, this problem can be mitigated by implementing efficient algorithms or optimizing existing ones.
Complexity And Difficulty In Implementation
Implementing data encryption can be difficult as it requires companies to invest time and resources into selecting the right encryption technology for their needs. It also often requires specialized knowledge that may not be present within an organization’s IT department.
Compatibility And Interoperability Issues
Data encryption tools must work seamlessly with existing systems and be compatible with all the software applications in an organization. Incompatibility can lead to data loss, corruption, or even security breaches. The key to addressing compatibility issues is ensuring the encryption solution integrates well with existing systems without causing disruptions.
Conclusion
Data encryption is a powerful tool for protecting digital information from malicious actors. With the right knowledge and resources, it can be easy to implement encryption strategies to keep your data safe. Whether you’re an individual looking to protect your online banking or a business seeking to secure customer data, encryption technology is an invaluable resource. Familiarizing yourself with its applications and how it works will pay off in the end by providing more secure protection of your valuable data.
FAQs
What Is Key Management?
Key management refers to properly generating, storing, distributing and disposing of cryptographic keys in an organization. Cryptographic keys are crucial to data encryption because they determine who can access the encrypted data. Without proper key management protocols, unauthorized users can obtain these keys and gain access to sensitive information.
What Are The Best Practices For Encryption?
- Use a strong encryption algorithm such as AES-256 or RSA-4096. These algorithms provide high levels of security and are widely accepted in the industry.
- Use a unique key for each piece of data that needs to be encrypted. This ensures that even if an attacker manages to decrypt one piece of data, they cannot access other pieces of information.
- Organizations should regularly update their encryption protocols and keys. As technology advances, new vulnerabilities can be discovered and exploited. Regular updates ensure that the organization stays ahead of potential threats.
- Keys must be securely stored and only accessible by authorized personnel. In addition, regular audits and monitoring can help detect any unauthorized access attempts.
What Are Encryption Standards?
Encryption standards are a set of guidelines and protocols that ensure data security. These standards define how data should be encrypted, decrypted, stored and transmitted securely between the sender and receiver. Advanced Encryption Standard (AES) is the most commonly used encryption standard, which uses a symmetric key algorithm to encrypt data. This means the same key is used for encryption and decryption, ensuring secure communication.
What Are The Real-World Applications Of Encryption?
One of the most common applications is in online banking transactions. Encryption ensures that sensitive information such as credit card numbers or bank account details is transmitted securely between the customer and the financial institution.
Another application of encryption is in email communication. Email encryption protects important information from being intercepted by hackers or unauthorized third-party entities during transmission. This also applies to messaging apps like WhatsApp or Signal, which use end-to-end encryption to secure user messages.
What Is The Length Of The Cryptographic Key Used In The Data Encryption Standard (DES) Cryptosystem?
The length of the cryptographic key used in the DES cryptosystem is 56 bits, which provides many possible keys.
While once considered secure, technological advances have made it vulnerable to brute force attacks. To address this issue, triple DES (3DES) was developed to improve over standard DES by using three keys to encrypt data. This increased the effective key size to 168 bits, making 3DES significantly more secure than its predecessor.
Nowadays, AES (Advanced Encryption Standard) has replaced both DES and 3DES as the preferred standard for encryption due to its stronger security features and longer key lengths. AES offers multiple key sizes ranging from 128-bit to 256-bit, which makes it highly resistant against brute force attacks while still being fast enough for practical use in modern systems.
