Introduction
As more businesses continue to embrace digital transformation, data security is becoming an increasingly important issue. Protecting sensitive data has always been a top priority for businesses, but with the rise in remote work and the use of cloud-based services, it has become even more critical. One area of data security that businesses need to pay close attention to is PPA (payment processing application) data security.
To ensure proper PPA data security, businesses need to take a proactive approach by implementing a range of security measures across their payment systems. This can include encrypting sensitive customer information during transmission, using secure servers to store this information, regularly monitoring access logs for suspicious activity, and ensuring staff members are trained on proper handling procedures.
What is PPA Data Security?
Definition of PPA

PPA, or Personal Privacy Act, is legislation that aims to protect and preserve the privacy of individuals. More specifically, it requires businesses and organizations to obtain explicit consent from customers before collecting, using, and disclosing their personal information. PPA also mandates these entities to provide notice to customers about their data collection practices and how they intend to use the collected information.
Explanation Of PPA Data Security
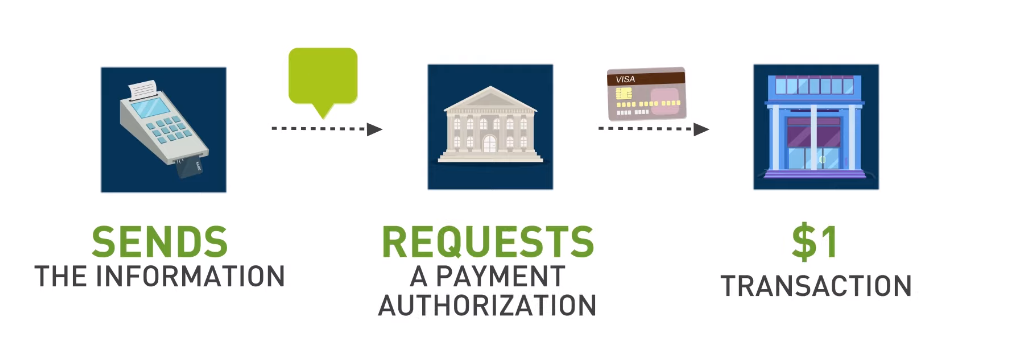
PPA data security refers to the measures and protocols put in place to protect sensitive information collected by Pay-Per-Action (PPA) networks. These networks are commonly used in affiliate marketing, where advertisers pay a commission for each action taken by a customer, such as filling out a form or making a purchase. PPA data typically includes personal and financial information, making it vulnerable to cyberattacks and fraud.
To ensure the secure handling of PPA data, network administrators employ various techniques such as encryption, access controls, and fraud detection systems. Encryption is used to scramble sensitive data during transmission and storage so that it can only be read by authorized parties with the proper decryption key. Access controls are put in place to limit who can access PPA data based on their role within the network. Fraud detection systems use machine learning algorithms to identify unusual activity patterns that could indicate fraudulent behavior.
How It Differs From Other Data Security Measures?
One of the most important things that set PPA data security apart from other types of data security measures is that it involves a highly specialized approach to encryption. With PPA, data is encrypted at rest and in transit using a complex algorithm that makes it virtually impossible for unauthorized individuals to access or manipulate the data. This level of encryption goes far beyond what you would typically find with standard security protocols like SSL or TLS.
Another key difference between PPA and other forms of data security is its focus on providing end-to-end protection for sensitive information. This means that not only is your data encrypted while it’s stored on servers or in transit, but also during any interactions with API calls, webhooks, or other integrations. Essentially, PPA provides a comprehensive layer of protection around every aspect of your business’s sensitive information.
PPA also differs from other types of data security measures due to its compatibility with various regulatory requirements. Whether you’re bound by GDPR in Europe or HIPAA regulations in the US healthcare industry, the advanced encryption standards used by PPA can help ensure compliance and protect against costly fines resulting from breaches or mishandling of sensitive information.
Types of PPA Data
Explanation Of The Types Of PPA Data
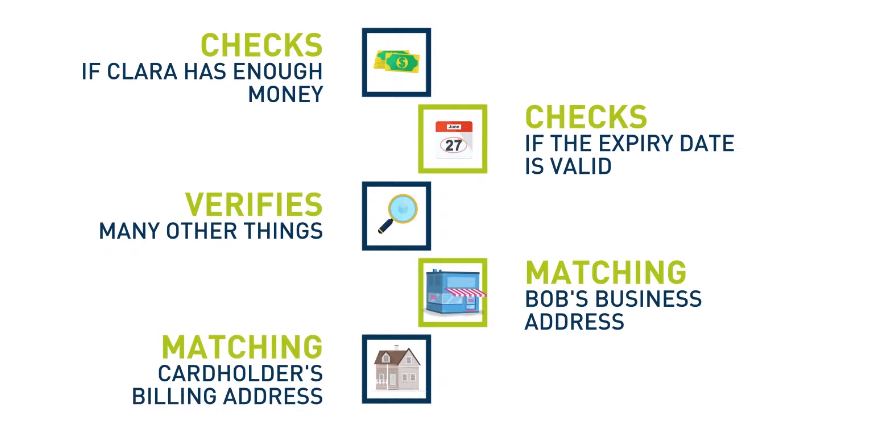
There are several types of PPA (Power Purchase Agreement) data that companies need to be aware of when dealing with energy contracts. The first type is the customer information, which includes names, addresses, and contact details. This data should be treated with utmost care as it contains sensitive information that can lead to identity theft if mishandled.
The second type of PPA data is financial information such as payment history, credit scores, and bank account numbers. These details are critical for both parties involved in the contract as they facilitate smooth transactions. However, this data should be kept secure to prevent fraud or unauthorized access.
Lastly, there are operational data consisting of power usage trends and other metrics related to energy consumption. This data helps companies understand how much energy they’re using and find ways to improve efficiency. It’s essential to protect this data from leaks or hacks as it can give competitors an advantage over a business.
How Each Type Of PPA Data Is Secured?
Data security for PPA agreements involves a variety of measures such as encryption, multi-factor authentication, firewalls, intrusion detection systems, and regular testing for vulnerabilities.
For instance, encrypted communication protocols are often used in transmitting client data between parties involved in a PPA contract. This ensures that the information being shared remains confidential while also protecting it against unauthorized access. Multi-factor authentication is another layer of security that can be applied when logging into systems or accessing critical data files.
Meanwhile, firewalls act as barriers that prevent unauthorized access to company networks and systems while intrusion detection systems monitor all traffic on a network for any suspicious activity or attacks. Lastly, regular testing for vulnerabilities is conducted to identify potential weaknesses before they become exploited by cybercriminals who might gain access to sensitive information through hacking or malware attacks.
Risks Associated with PPA Data
Explanation Of The Potential Risks Associated With PPA Data
One of the main problems with PPA data is that it can be vulnerable to cyber-attacks. As such, companies must take stringent security measures to ensure that their data remains secure at all times.
Another significant risk associated with PPA data is related to privacy concerns. As more and more sensitive information is shared through digital channels, there are increasing chances of that information being leaked or stolen by malicious actors. Companies need to take specific steps to safeguard their customers’ personal information and other confidential business data.
There are also compliance issues associated with PPA data usage. Businesses need to ensure that they are fully complying with all relevant regulations when collecting and storing this type of information. In particular, they must protect themselves against legal liability for any misuse or mishandling of customer data.
Consequences Of PPA Data Breaches
The consequences of PPA data breaches can be severe and long-lasting. One of the most significant impacts is reputational damage, as customers may lose trust in the company’s ability to protect their sensitive information. This could lead to a loss of business and revenue, as well as potential legal action from affected parties. Additionally, companies may face regulatory fines or sanctions for failing to adequately safeguard PPA data.
In addition to financial and legal consequences, PPA data breaches can also have operational implications. Companies may need to devote significant time and resources to investigating the breach, notifying affected parties, and implementing security measures to prevent future incidents. This can disrupt normal business operations and lead to lost productivity.
PPA Data Security Measures
Overview Of PPA Data Security Measures
PPA data security measures are the safeguards put in place to protect sensitive information. These measures include various physical, administrative, and technical controls that work together to prevent unauthorized access, disclosure, or modification of data. Physical security measures involve controlling access to PPA facilities and equipment through the use of keys or other electronic credentials. Administrative controls restrict who can access sensitive data by establishing policies and procedures for handling it.
Technical security measures include encryption, firewalls, intrusion detection systems (IDS), and antivirus software. Encryption protects data in transit by converting it into a code that only authorized users can decipher. Firewalls prevent unauthorized network traffic from entering an organization’s network while IDS detects any suspicious activity on the system. Antivirus software protects against malware that can compromise PPA systems.
Implementing PPA Data Security
Overview Of The Steps Involved In Implementing PPA Data Security Measures
Identify the potential risks and vulnerabilities that exist within the system. This requires a comprehensive understanding of the various components involved in energy generation, transmission, and distribution. Once these risks have been identified, appropriate security measures should be put in place to mitigate them.
Establish policies and procedures for managing access to data and information related to PPA transactions. This includes defining roles and responsibilities for different stakeholders involved in the process, as well as outlining protocols for monitoring and reporting any suspicious activities or incidents.
To ensure that these security measures are effective, regular testing and evaluation should be conducted. This can include penetration testing, vulnerability assessments, and audits of security controls. Any issues identified during these tests should be addressed promptly to minimize the risk of data breaches or other security incidents.
Explanation Of Risk Assessments And Analysis
Risk assessments and analysis involve identifying, analyzing, and evaluating potential risks to the confidentiality, integrity, and availability of sensitive data. The purpose of risk assessments is to help organizations identify areas that may be vulnerable to attack or unauthorized access so that they can take appropriate measures to mitigate those risks.
Risk analysis involves examining the likelihood and impact of a security breach occurring within an organization’s PPA system. It entails assessing the potential threats that could compromise the system’s security, such as human error, software vulnerabilities, or physical threats like natural disasters. Once these risks have been identified and analyzed appropriately, organizations can design strategies for minimizing their exposure.
Training and Education on PPA Data Security
When it comes to PPA data security, training, and education is essential for organizations to provide regular training sessions to employees on how best to handle and safeguard personal information.
The training should cover topics such as password management, phishing attacks, social engineering tactics, and the importance of physical security measures such as locking cabinets and shredding documents. Education on PPA data security should also be extended beyond just employees who directly handle personal information. All staff members need to understand the consequences of mishandling sensitive data.
Moreover, organizations should regularly review their policies and procedures related to PPA data security to ensure they are up-to-date with current regulations and industry best practices. Periodic assessments can identify any gaps in existing protocols and help reinforce good habits among employees when handling confidential information. By investing in training and education initiatives around PPA data security, organizations can minimize the risk of a costly breach while building a culture of awareness around protecting personal information.
Outsourcing PPA Data Security
Overview Of Outsourcing PPA Data Security
Outsourcing PPA data security is a wise move for companies seeking to protect their customers’ personal and financial information. The Payment Card Industry Data Security Standard (PCI DSS) mandates strict requirements for merchants to ensure the secure handling of cardholder data, and outsourcing data security can help companies meet those requirements while freeing up internal resources.
When outsourcing PPA data security, it’s important to choose a reputable vendor with experience in the field. The vendor should be able to provide customized solutions based on the specific needs of your business, as well as ongoing support and monitoring. Additionally, any vendor you work with should be compliant with PCI DSS regulations themselves.
Explanation Of The Benefits And Risks Associated With Outsourcing PPA Data Security
Outsourcing PPA data security can offer several benefits to companies. It allows businesses to focus on their core competencies, leaving data security management in the hands of experts who have specialized skills and experience. Outsourcing also enables firms to save money by reducing the overhead costs associated with hiring and training personnel.
However, outsourcing PPA data security comes with risks. For one, it can result in a loss of control over sensitive business information. Moreover, if a third-party vendor fails to implement proper cybersecurity measures or becomes negligent in handling data breaches effectively, it could lead to massive financial losses for companies.
Another risk associated with outsourcing PPA data security is the potential for hacking attacks or cybercrime resulting from weak links within the supply chain.
Things To Consider When Outsourcing PPA Data Security
Assess the level of experience and expertise that your potential service provider has in handling sensitive information. It would be best if you worked with a company that has a proven track record in safeguarding PPA data.
Consider the measures put in place to ensure secure transmission and storage of information. Your service provider should have robust encryption protocols to protect against breaches and unauthorized access.
Check if your potential outsourcing partner adheres to industry regulations concerning data protection. You may require them to comply with specific standards such as ISO 27001 or the General Data Protection Regulation (GDPR).
PPA Data Security Best Practices
Overview Of PPA Data Security Best Practices
Use encryption: One of the key PPA data security best practices is to use encryption for all sensitive information. This includes passwords, credit card numbers, and other personal details that are collected or transmitted via online platforms.
Limit access to data: Another important practice is to limit access to PPA data only to authorized personnel who have a legitimate need for it. This can be achieved by implementing strong user authentication mechanisms, such as two-factor authentication or biometric verification.
Regularly update software and security protocols: Keeping software and security protocols up-to-date is another crucial aspect of PPA data security best practices. This ensures that any known vulnerabilities or weaknesses are patched promptly, minimizing the risk of data breaches.
PPA Data Security for Small Businesses
Small businesses are often the target of cyberattacks due to their lack of proper security measures. This is why implementing Payment Card Industry Data Security Standard (PCI DSS) compliance is essential for any small business that accepts credit card payments. PPA data security measures help small businesses protect their customer’s financial data, which instills trust and loyalty in the minds of customers.
Implementing PPA data security measures can also safeguard against fraudulent activities, such as chargebacks and identity theft. Small businesses that fail to comply with PCI DSS regulations could face hefty fines and legal action if they fall victim to a breach or attack. Therefore, it is imperative for small business owners to take the necessary steps to ensure the safety of their customers’ financial information by implementing PPA data security measures.
PPA Data Security for Large Enterprises
Overview Of PPA Data Security For Large Enterprises
To achieve PPA data security compliance, large enterprises must implement a range of measures including encryption of sensitive data both in transit and at rest, multi-factor authentication for access controls to systems containing the sensitive data, and regular vulnerability assessments to identify potential weaknesses in the system. In addition to these technical measures, companies must also have policies and procedures in place to ensure employees are trained on the proper handling of sensitive data and understand their role in maintaining compliance.
Overall, PPA data security is critical for large enterprises that want to protect customer information while avoiding costly breaches or penalties for non-compliance with regulations such as PCI-DSS (Payment Card Industry Data Security Standard). By implementing robust technical measures combined with employee training programs on the proper handling of sensitive information, businesses can reduce their risk exposure while maintaining a secure environment for customers.
PPA Data Security and Mobile Devices
Overview Of PPA Data Security And Mobile Devices
Personal Protective Equipment (PPE) regulations require all PPA data, including PHI and PII, to be protected from unauthorized access. This means that mobile devices must be secured in the same way as desktop computers or laptops.
One of the most important steps in securing mobile devices is implementing strong authentication measures. This can include password-protected screensavers or biometric identification techniques such as fingerprint scanning or facial recognition technology. Additionally, remote wipe capabilities should also be enabled so that if a device is lost or stolen, all sensitive information can be erased remotely.
Another key consideration for PPA data security on mobile devices is ensuring that software and firmware are up-to-date with the latest security patches. Mobile operating systems regularly release new updates that address vulnerabilities and improve overall security, so it’s important to keep devices updated regularly.
Explanation Of The Risks Associated With Storing And Transmitting Ppa Data On Mobile Devices
Storing and transmitting PPA data on mobile devices can pose significant risks due to the potential for theft or loss of the device. Mobile devices are inherently less secure than desktop computers or servers as they are easily lost, stolen, or hacked. Hackers can use various techniques to steal PPA data from smartphones, such as malware designed specifically for mobile devices.
Another risk associated with storing and transmitting PPA data on mobile devices is the possibility of unauthorized access by third parties. Without proper encryption protocols in place, hackers can intercept transmissions containing personal information and use it for fraudulent activities like identity theft. Additionally, users who store PPA data on their phones without a password or PIN code increase the risk of unauthorized access should their phone fall into the wrong hands.
PPA Data Security and Social Engineering
Overview Of PPA Data Security And Social Engineering
Social engineering is a technique used by hackers to manipulate individuals into divulging sensitive information or performing actions that compromise security. Common methods include phishing emails, pretexting phone calls, and baiting via online ads or social media.
Implementing PPA data security measures such as firewalls, encryption, access controls, and employee training can help prevent unauthorized access to valuable customer information. Being aware of social engineering tactics and educating employees on how to identify and avoid scams can also significantly reduce the risk of a security breach.
Explanation Of The Risks Associated With Social Engineering Attacks
One of the main risks associated with social engineering attacks is identity theft. Attackers can use stolen personal information such as passwords, credit card numbers, and social security numbers for fraudulent purposes. Another risk is financial loss; attackers may use stolen credentials to transfer funds out of bank accounts or make unauthorized purchases.
Social engineering attacks can also result in reputational damage for both individuals and businesses. If sensitive information such as client data is compromised due to an attack, it could lead to legal problems, loss of customer trust, and even lawsuits.
Conclusion
Data security in PPA is a crucial factor for any business. It ensures that sensitive information stays safe from unauthorized access and prevents potential breaches that could lead to data loss or theft. Understanding the importance of securing your company’s data is essential in today’s digital era where cyberattacks are increasingly becoming prevalent.
Therefore, businesses must invest in robust security measures such as encryption, two-factor authentication, and regular software updates to safeguard their PPA systems against malicious attacks. Additionally, companies should educate their employees on the best practices for handling sensitive information to minimize the risk of human error leading to security incidents.
