Importance of Persistent Data Storage in Unity
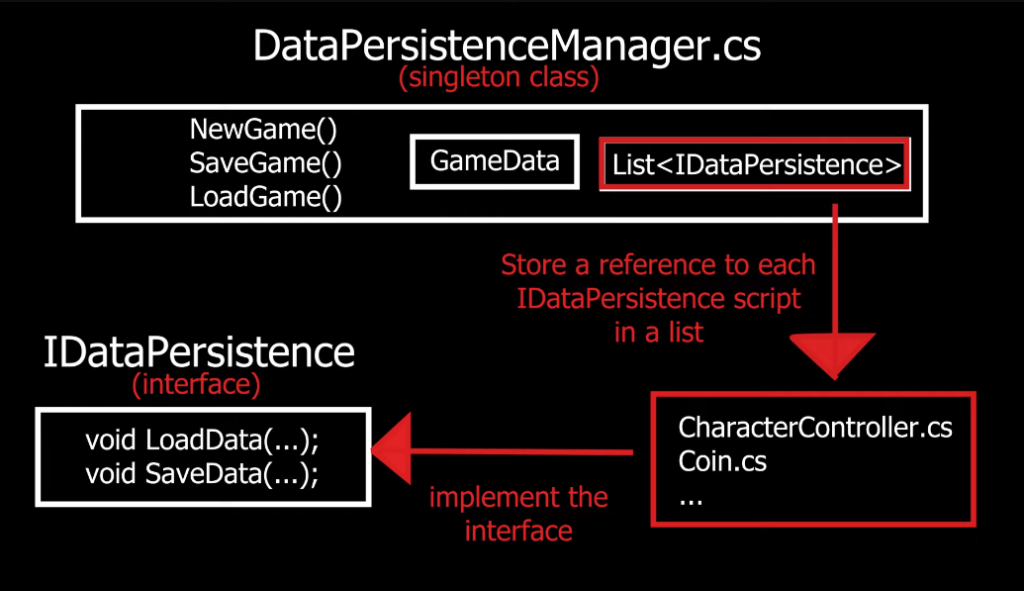
Persistent data storage is crucial in Unity game development as it allows the game to save and load important information such as player progress, game settings, and other data that needs to be retained even after the game is closed or restarted. Without persistent data storage, players would lose their progress and settings every time they exit the game, which can be frustrating and discouraging. Unity offers several ways to implement persistent data storage, including PlayerPrefs, which allows developers to store simple data such as integers and strings, and serialization.
Need For Secure And Protected Storage Mechanisms
The need for secure and protected storage mechanisms is crucial for any application that deals with sensitive user data. In the case of games, this can include personal information such as usernames, passwords, and payment details. Unity provides several options for secure data storage, including encryption and decryption methods that can be used to protect sensitive data. One popular method for secure data storage in Unity is to use the Unity Encryption Library, which provides a simple way to encrypt and decrypt data using a key.
Understanding Persistent Data
Persistent data refers to data that is saved and stored on a device even after the application or game has been closed. This data can include user preferences, game progress, and other important information that needs to be retained for future use. In Unity, persistent data is typically stored in a file or database on the device’s storage system. To access and manipulate persistent data in Unity, developers can use the PlayerPrefs class, which provides a simple way to save and load data.
Types of Data That Require Persistent Storage
Various types of data require persistent storage in Unity, including:
1. User preferences: User preferences such as sound settings, language preferences, and other customization options need to be saved and retrieved every time the application or game is launched.
2. Game progress: Game progress data such as high scores, completed levels, and unlocked achievements need to be saved and retrieved to ensure that the player can resume the game from where they left off.
Importance of Data Integrity And Confidentiality
Data integrity and confidentiality are crucial in any application or game that requires persistent storage. Data integrity ensures that the data stored is accurate and consistent and that it is not corrupted or lost due to system failures or other issues. Confidentiality ensures that sensitive data such as user information, passwords, and financial information is protected from unauthorized access or disclosure. Failure to maintain data integrity and confidentiality can result in loss of user trust, legal liabilities, and reputational damage.
Security Risks in Persistent Data Storage

Persistent data storage presents several security risks that organizations must address to maintain data integrity and confidentiality. Some of these risks include:
1. Malware and viruses: Malware and viruses can infect the storage system and corrupt or steal data.
2. Insider threats: Employees or contractors with access to the storage system may intentionally or unintentionally compromise data security.
3. Data breaches: Hackers may gain unauthorized access to the storage system and steal sensitive data.
4. Physical theft or damage.
Risks of Data Breaches And Unauthorized Access

Data breaches and unauthorized access are significant risks that can lead to severe consequences for individuals and organizations. Some of these risks include:
1. Identity theft: Cybercriminals can steal personal information, such as social security numbers, credit card numbers, and other sensitive data, to commit identity theft.
2. Financial loss: Data breaches can result in financial loss for individuals and organizations, including the cost of repairing systems, lost revenue, and legal fees.
Impact of Compromised Data on User Experience
Compromised data can have a significant impact on user experience. When personal information is stolen, it can lead to identity theft and financial loss, which can cause stress and anxiety for individuals. In addition, data breaches can result in the loss of trust in organizations that handle sensitive data, leading to a negative user experience. Users may also experience inconvenience and frustration if they are required to change passwords or monitor their financial accounts due to a data breach.
Implementing Secure Data Storage in Unity
To implement secure data storage in Unity, you can use the Unity PlayerPrefs system to store sensitive data locally on the user’s device. However, this method is not completely secure as the data can be easily accessed and manipulated by experienced users. A more secure approach is to use encryption to protect the data. You can use the Advanced Encryption Standard (AES) algorithm to encrypt the data before storing it in PlayerPrefs. This will make it difficult for anyone to access or manipulate the data without the encryption key.
Player prefs: Storing Data Securely in Player Preferences
When it comes to storing sensitive data in player preferences, it’s important to take security seriously. One way to do this is by using encryption to protect the data. The Advanced Encryption Standard (AES) algorithm is a popular choice for encrypting data, as it is widely used and considered to be secure. To use AES encryption with PlayerPrefs, you can use the built-in encryption functions provided by Unity.
Secure File Storage: Saving Data in Encrypted Files
When it comes to storing sensitive data in files, it’s important to ensure that the data is encrypted to prevent unauthorized access. One way to do this is by using encryption libraries such as OpenSSL or Crypto++. These libraries provide a range of encryption algorithms that can be used to secure your files. To use encryption with your files, you can first generate a key using a secure random number generator. This key can then be used to encrypt your data using one of the encryption algorithms provided by the library.
Cloud-Based Solutions: Ensuring Security With Remote Storage
Cloud-based solutions can provide an added layer of security for your data by storing it remotely on secure servers. These servers are often maintained by third-party providers who specialize in cloud storage and security. To ensure the security of your data, cloud providers typically use encryption to protect your files. This encryption can be applied both during the transmission of your data to the cloud server and while it is stored on the server.
Best Practices for Secure Data Storage
Here are some best practices for secure data storage:
1. Use strong passwords: Create strong and unique passwords for all your accounts and change them regularly.
2. Enable two-factor authentication: This adds an extra layer of security by requiring a second form of authentication, such as a code sent to your phone, in addition to your password.
3. Regularly back up your data: Make sure to back up your data regularly to avoid data loss in case of a security breach or system failure.
Access Control Mechanisms And User Authentication
Access control mechanisms and user authentication are crucial for ensuring the security of data storage. Access control mechanisms limit access to data based on the user’s role and permissions. User authentication verifies the identity of the user before granting access to the data. Some common access control mechanisms include role-based access control (RBAC), attribute-based access control (ABAC), and mandatory access control (MAC).
Implementing Data Encryption And Decryption Routines
Implementing data encryption and decryption routines is another important aspect of ensuring data security. Encryption is the process of converting plain text into a coded message that can only be deciphered with a key. Decryption is the process of converting the coded message back into plain text using the same key. This helps to prevent unauthorized access to sensitive data by making it unreadable to anyone who does not have the key to decrypt it.
Ensuring Data Integrity And Validation
Ensuring data integrity and validation is crucial to maintaining the accuracy and reliability of data. Data integrity refers to the accuracy and consistency of data throughout its life cycle, from creation to deletion. Validation is the process of verifying that data is accurate, complete, and consistent. To ensure data integrity, it is important to implement data validation checks at various stages of the data life cycle. This can include input validation to ensure that data is entered correctly, as well as checks for data consistency and completeness.
Checking Data Integrity During Read-And-Write Operations
Data integrity is crucial for ensuring the reliability and usefulness of data. It is important to perform data validation checks during read-and-write operations to ensure that the data being added, modified, or deleted is accurate and consistent. This can include checking for data type, length, and format, as well as ensuring that the data being added or modified does not violate any business rules or constraints.
Preventing Data Corruption And Tampering
Preventing data corruption and tampering is also essential for maintaining data integrity. This can be achieved through various measures such as implementing access controls, encryption, and backups. Access controls limit who can access and modify data, while encryption protects data from unauthorized access and tampering. Backups ensure that data can be restored in case of data loss or corruption. Regular testing and auditing can also help identify and address any potential vulnerabilities in the system.
Addressing Cross-Platform Compatibility
Cross-platform compatibility is an important consideration when it comes to software development. It refers to the ability of a software application to run on different operating systems and hardware platforms without any compatibility issues. To ensure cross-platform compatibility, developers need to use standard programming languages and frameworks that are compatible with multiple platforms. Additionally, developers should test their software on different platforms to identify and address any compatibility issues. They should also consider using virtualization technology to simulate different operating environments and test their software on them.
Challenges of Persistent Data Storage Across Platforms
Persistent data storage across platforms can be challenging due to differences in file systems, data structures, and storage technologies. Developers need to ensure that their software can handle different file formats and storage devices, such as hard drives, solid-state drives, and cloud storage. They should also consider using standardized data formats and serialization techniques to make it easier to transfer data between different platforms.
Adapting Storage Mechanisms for Different Operating Systems
Adapting storage mechanisms for different operating systems can be a complex task for developers. This is because each operating system has its own file system and storage architecture. For example, Windows uses NTFS or FAT file systems, while macOS uses HFS+ or APFS. Therefore, developers need to ensure that their software can handle different file systems and storage technologies. To address this challenge, developers can use cross-platform libraries or APIs that abstract the underlying storage architecture.
Ensuring Consistent Security Measures on All Platforms
Ensuring consistent security measures on all platforms can be a challenging task for developers. This is because each operating system has its security model and architecture. For example, Windows uses a different set of security features than macOS or Linux. Therefore, developers need to ensure that their software can handle different security models and technologies. To address this challenge, developers can use cross-platform security libraries or APIs that abstract the underlying security architecture.
Performance Considerations for Secure Storage
When it comes to secure storage, performance considerations are crucial. Encryption and decryption processes can be resource-intensive and can slow down the performance of the software or application. Therefore, developers need to carefully choose the encryption algorithms and key sizes that they use. They also need to consider the hardware capabilities of the devices that their software will run on. One way to improve performance is to use hardware-based encryption.
Optimizing Data Storage And Retrieval Processes
Developers can optimize data storage and retrieval processes by implementing efficient data structures and algorithms. They can also consider using compression techniques to reduce the size of the data being stored. Additionally, developers can use caching mechanisms to improve the speed of data retrieval by storing frequently accessed data in memory. It’s important to consider the scalability of the storage solution as well, ensuring that it can handle increasing amounts of data over time. Finally, developers should regularly monitor and optimize the storage and retrieval processes to ensure optimal performance.
Minimizing Impact on Application Performance
To minimize the impact on application performance, developers can implement various strategies. One approach is to use asynchronous processing, which allows the application to continue running while data is being retrieved or stored in the background. This can help prevent the application from becoming unresponsive or slowing down. Another strategy is to use indexing, which can improve the speed of data retrieval by allowing the database to quickly locate specific records.
XVII. Frequently Asked Questions (FAQs)
Why is secure data storage important in Unity?
Secure data storage is important in Unity to protect sensitive information such as user credentials, payment details, and other personal data. If this information is not securely stored, it can be easily accessed by unauthorized individuals, leading to identity theft, financial fraud, and other security breaches. Additionally, secure data storage is often a legal requirement for applications that handle sensitive data, so failing to implement it can result in legal consequences.
How can encryption techniques enhance data security in Unity?
Encryption techniques can enhance data security in Unity by encrypting sensitive data, such as user credentials and payment details, before storing them in the database or transmitting them over the network. This makes it difficult for unauthorized individuals to access the data even if they manage to gain access to the system. Unity provides built-in encryption features that developers can use to encrypt data. For example, Unity’s PlayerPrefs class provides a way to securely store player preferences using AES encryption.
What are the best practices for implementing secure data storage?
There are several best practices for implementing secure data storage:
1. Use encryption: As mentioned earlier, encryption is a crucial aspect of secure data storage. Always use encryption algorithms that are considered secure and strong, such as AES.
2. Use secure protocols: When transmitting data over the network, ensure that you use secure protocols such as HTTPS, SSL, or TLS.
3. Use secure storage mechanisms: Use secure storage mechanisms such as password-protected databases or encrypted file systems.
How can I ensure data integrity and validation in Unity?
To ensure data integrity and validation in Unity, you can follow these best practices:
1. Use data validation: Implement data validation techniques to ensure that the data entered into your game/application is correct and free from errors or malicious code.
2. Use data serialization: Use Unity’s built-in serialization features to save and load data securely and efficiently.
3. Use encryption: Use encryption algorithms to encrypt sensitive data such as passwords, credit card information, and user data.
