The Tor Browser indeed encrypts data to ensure your online activities remain private and secure. When you use the Tor Browser, it automatically encrypts the data you send and receive over the internet.
In the era of digital communication and online activities, ensuring the privacy and security of our data has become increasingly important. With the growing concerns about surveillance and data breaches, many individuals are turning to tools and technologies that provide enhanced privacy protection. One such tool is the Tor Browser, renowned for its ability to anonymize online activities. But does Tor Browser encrypt data? Let’s delve deeper into this topic and understand how Tor Browser works to secure your information.
Understanding Tor Browser

Tor Browser is a web browser that allows users to browse the internet anonymously. It is based on the Tor network, which is a decentralized network of volunteer-operated servers. The primary goal of Tor Browser is to protect the user’s privacy and maintain their anonymity while accessing online content. By using the Tor network, users can prevent their online activities from being traced back to their real IP address.
How Tor Browser Works?
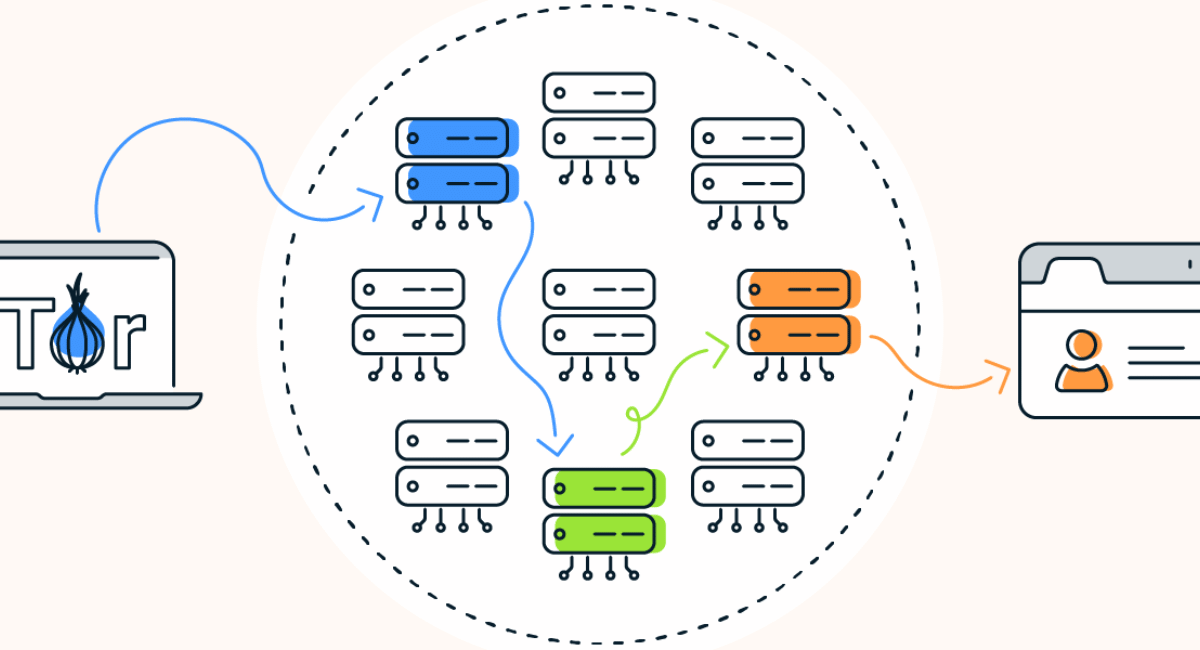
The Tor Browser operates on the principle of onion routing. When you use Tor Browser, your web traffic is routed through a series of random nodes within the Tor network. Each node peels off a layer of encryption, hence the term “onion routing.” This process makes it extremely difficult for anyone monitoring the network to determine the origin and destination of the data.
Multiple Layers of Encryption
To ensure the privacy and security of your data, Tor Browser employs multiple layers of encryption. As your web traffic passes through each node in the Tor network, a layer of encryption is removed. However, it’s important to note that Tor Browser does not encrypt the data itself. Instead, it relies on the encryption provided by the websites you visit. Therefore, websites that use HTTPS (Hypertext Transfer Protocol Secure) encryption provide an additional layer of security when accessed through Tor Browser.
Encrypting Data with Tor Browser
While Tor Browser does not encrypt the data itself, it plays a crucial role in encrypting web traffic between your device and the websites you visit. When you use Tor Browser, your internet service provider (ISP) can only see that you are using Tor, but they cannot monitor your specific online activities. This encryption prevents anyone from intercepting and deciphering your web traffic, thus safeguarding your privacy.
End-to-End Encryption
In addition to the encryption provided by Tor Browser, it’s essential to ensure that the websites you visit also utilize end-to-end encryption. End-to-end encryption protects your data throughout its journey, from your device to the destination server. Popular protocols such as HTTPS and SSL/TLS (Secure Sockets Layer/Transport Layer Security) are examples of encryption methods that secure your data from potential eavesdroppers.
Encrypting Data with Tor Browser
While we have discussed how Tor Browser encrypts web traffic and protects your privacy, it’s important to highlight the encryption mechanisms involved in the process.
- Entry Node Encryption: When you initiate a connection to the Tor network, your data is encrypted from your device to the entry node. This encryption ensures that your initial communication is protected and prevents your ISP or other network observers from intercepting or understanding the data.
- Layered Encryption: As your encrypted data passes through each node in the Tor network, a layer of encryption is removed at each step. This layered approach prevents any single node from having complete visibility into both the source and destination of the data, making it difficult for anyone to trace your online activities.
- Destination Encryption: While Tor Browser encrypts data within the network, it’s important to note that the final connection between the exit node and the destination website may not be encrypted by default. This means that if you’re visiting a website that does not use HTTPS encryption, the data transmitted between the exit node and the website’s server may not be fully encrypted. To address this, it is recommended to look for websites that support HTTPS to ensure end-to-end encryption throughout your browsing session.
The Role of Encryption in Tor Browser
Encryption is a fundamental component of Tor Browser’s privacy and security features. Here are some key aspects of Tor Browser’s encryption that further emphasize its importance:
- Anonymity and Privacy: The encryption provided by Tor Browser helps maintain your anonymity and privacy by preventing third parties from monitoring and understanding your online activities. It protects your browsing history, personal information, and communication, allowing you to explore the internet without leaving a digital trail.
- Protection against Surveillance: With increasing concerns about surveillance and data monitoring, encryption plays a vital role in safeguarding your information. Tor Browser’s encryption helps protect your data from being intercepted or monitored by government agencies, ISPs, or other potential eavesdroppers.
- Securing Data Transmission: Encryption is essential for securing data transmission between your device and the websites you visit. By encrypting your web traffic, Tor Browser mitigates the risk of unauthorized access, data interception, or tampering, ensuring the confidentiality and integrity of your online communication.
Understanding Encryption Levels in Tor Browser

It’s important to note that the encryption in Tor Browser operates at different levels:
- Network-Level Encryption: The encryption at the network level ensures that your data is protected as it traverses through the nodes in the Tor network. Each node removes a layer of encryption, making it challenging for anyone to trace the origin and destination of your data.
- Website-Level Encryption: Tor Browser relies on websites that use HTTPS encryption to provide an additional layer of security. When you visit websites that utilize HTTPS, your connection is further encrypted between your device and the website’s server, providing end-to-end encryption for the data transmitted.
By incorporating both network-level and website-level encryption, Tor Browser maximizes the protection of your data while maintaining your anonymity and privacy.
Limitations of Tor Browser
While Tor Browser provides valuable privacy and security features, it’s essential to be aware of its limitations.
Malicious Exit Nodes
One of the potential vulnerabilities of Tor Browser is the presence of malicious exit nodes. Exit nodes are the final points in the Tor network where your encrypted traffic leaves the network and reaches its destination. In some cases, malicious actors can set up these exit nodes to capture unencrypted data or inject malicious code into the transmitted data. However, such instances are relatively rare and can be mitigated by using websites with HTTPS encryption.
Vulnerabilities in Websites
Tor Browser can only encrypt data between your device and the websites you visit. If a website itself has vulnerabilities or lacks proper encryption, your data may still be at risk. It’s crucial to exercise caution while accessing websites and ensure they have appropriate security measures in place.
Is Tor Browser Safe to Use?
Yes, the Tor Browser is generally considered safe to use. It was created to help protect people’s privacy and keep them safe while browsing the internet. However, it’s important to remember that no tool is 100% perfect, and there may still be some risks involved. It’s always a good idea to use additional security measures and be cautious about the websites you visit and the information you share online.
How Can I Start Using Tor Browser?
Getting started with Tor Browser is relatively simple. Here’s a step-by-step guide on how to begin using Tor Browser:
- Download Tor Browser: Visit the official Tor Project website at https://www.torproject.org and navigate to the Tor Browser download page. Choose the appropriate version for your operating system (Windows, macOS, or Linux) and click on the download link.
- Verify the Download: After the download is complete, it’s essential to verify the integrity of the downloaded file. The Tor Project provides instructions on how to verify the signature of the downloaded file to ensure its authenticity. Verification helps protect against the risk of tampered or malicious downloads.
- Install Tor Browser: Once the download is verified, proceed with the installation process. Run the installer file and follow the on-screen instructions. Tor Browser installation is similar to installing any other software on your computer. Choose the desired installation directory and complete the installation.
- Launch Tor Browser: After installation, locate the Tor Browser icon on your desktop or in the designated installation folder. Double-click the icon to launch Tor Browser.
- Configure Tor Network: When you first launch Tor Browser, you’ll be prompted to configure your Tor network connection. You can choose to connect directly or configure a proxy if necessary. Most users can select the default configuration and click “Connect” to establish a connection to the Tor network.
- Wait for Connection: Tor Browser will establish a connection to the Tor network, which may take a few moments. Once the connection is established, Tor Browser will open with a modified version of the Mozilla Firefox web browser.
- Browse Anonymously: You are now ready to start browsing the internet with Tor Browser. Tor Browser automatically routes your web traffic through the Tor network, providing anonymity and privacy. Use the address bar to enter URLs or search queries as you would with any other web browser.
- Configure Security Settings: Tor Browser includes built-in security features that help protect your privacy. It is recommended to review and adjust the security settings according to your preferences. Click on the shield icon located in the address bar to access the security settings menu.
- Keep Tor Browser Updated: It is crucial to keep Tor Browser updated with the latest version to benefit from security patches and improvements. Tor Browser will automatically check for updates and notify you when a new version is available. Ensure that you regularly update the browser to maintain optimal security.
- Exercise Caution: While Tor Browser provides anonymity and privacy, it’s essential to exercise caution while browsing the internet. Be mindful of the websites you visit, avoid downloading files from untrusted sources, and follow best practices for online security.
By following these steps, you can start using Tor Browser to browse the internet anonymously and enhance your online privacy.
Precautions While Using Tor Browser
To stay safe while using the Tor Browser, here are a few tips:
- Always keep your Tor Browser up to date by installing the latest updates.
- Be cautious about the websites you visit and avoid clicking on suspicious links.
- Avoid downloading files or opening attachments from unknown sources.
- Use strong and unique passwords for your accounts.
- Consider using additional security measures, such as antivirus software and a virtual private network (VPN).
FAQs
Q: Can Tor Browser be trusted?
A: Tor Browser has been extensively tested and is trusted by millions of users worldwide. However, it’s important to note that no tool can guarantee 100% security, and users should always exercise caution while browsing the internet.
Q: Is Tor Browser legal?
A: Tor Browser itself is legal to use in most countries. However, certain activities conducted while using Tor Browser may be subject to legal regulations. It is essential to understand and comply with the laws of your jurisdiction.
Q: Can Tor Browser be used for illegal activities?
A: While Tor Browser provides anonymity, it does not condone or promote illegal activities. Users are responsible for their actions and should use Tor Browser within the boundaries of the law.
Q: How can I enhance my security while using Tor Browser?
A: To enhance security while using Tor Browser, ensure you are using the latest version, regularly update your operating system and antivirus software, and exercise caution while accessing websites or downloading files.
Conclusion
In conclusion, the Tor Browser is like a magical cloak that helps keep your online activities private and your information safe. It encrypts your data, making it harder for others to understand, and allows you to access websites that might otherwise be blocked. While it’s not a guarantee of complete anonymity, it’s a valuable tool for protecting your privacy on the internet.
Remember, it’s always important to use the internet responsibly, be cautious about the websites you visit, and keep your personal information safe. By using tools like the Tor Browser and following best practices for online safety, you can enjoy a safer and more private browsing experience.
