In today’s digital age, the protection of personal information and secure communication has become a top priority. With rising concerns about data breaches, hacking, and unauthorized access to sensitive data, it is crucial to employ robust security measures. End-to-end encryption has emerged as a powerful solution to safeguard data during transmission. I will provide a comprehensive understanding of end-to-end encrypted data, including its working mechanism, benefits, applications, and potential future developments.
What is End-to-End Encryption?
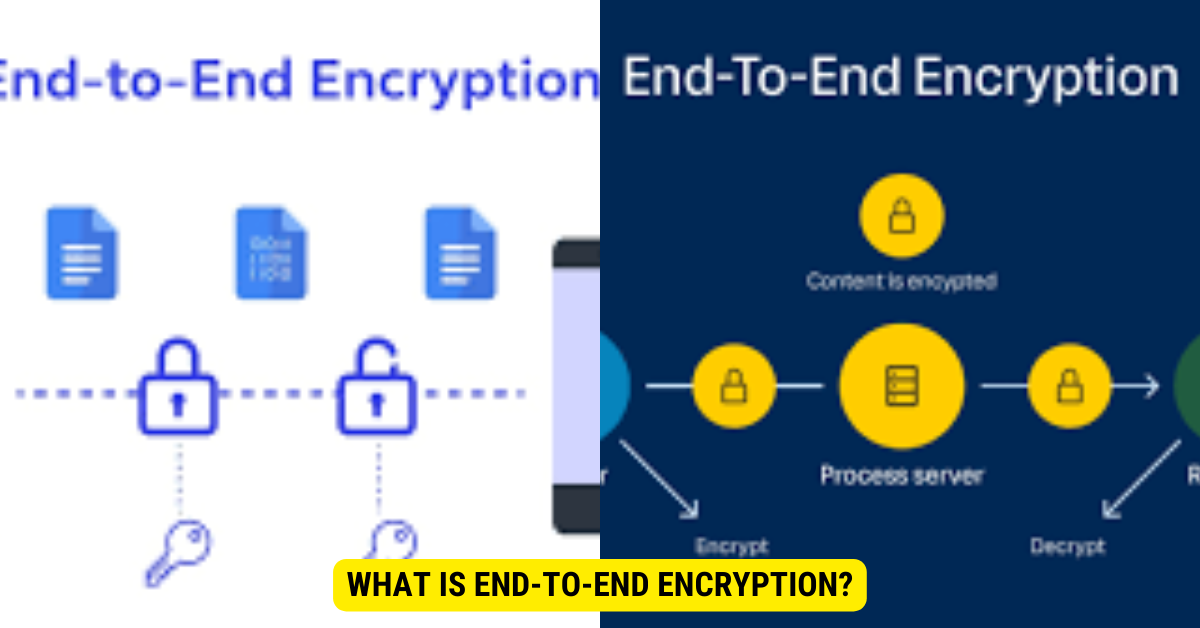
End-to-end encryption is the gold standard for communication security. It ensures that only the sender and the intended recipient(s) have access to the data, while preventing any unauthorized parties, including hackers and third-party entities, from intercepting or accessing the encrypted information.
The Meaning of Encryption
Encryption is the process of converting human-readable plain text into incomprehensible text, known as ciphertext, through the use of cryptographic keys. It transforms data into a secure form that can only be decrypted and understood by those possessing the correct decryption key. Encryption adds an essential layer of protection to sensitive information, both when stored and when transmitted.
The Rise of End-to-End Encryption
The growing concern over data security vulnerabilities on social media platforms and messaging applications has fueled the adoption of end-to-end encryption. Platforms such as WhatsApp, Signal, and others have embraced this technology to safeguard user data. However, many users are still unaware of the intricacies of end-to-end encryption, how it differs from other security measures, and the level of data security it provides.
Understanding How End-to-End Encryption Works

End-to-end encryption ensures that messages and files are encrypted before leaving the sender’s device and remain encrypted until they reach the intended recipient’s device. This encryption process takes place at the device level, making it challenging for unauthorized entities to access the data. The security of end-to-end encryption relies on the generation of a public-private key pair, where the public key encrypts the message, while the private key, known only to the recipient, decrypts the message.
Can The System Be Hacked?
While no system is entirely impervious to hacking attempts, end-to-end encryption significantly reduces the risk. The encryption of data stored on servers makes it indecipherable, even if hackers gain access to them. Furthermore, brute force attacks, where attackers attempt to guess the encryption key through millions or billions of guesses, are highly unlikely to succeed due to the complexity and strength of modern encryption algorithms.
The Importance And Advantages Of End-To-End Encryption
End-to-end encryption offers several crucial benefits:
- Privacy: Encryption ensures that only authorized recipients can read messages or access data, protecting it from interception by attackers, ad networks, ISPs, and, in certain cases, government surveillance.
- Security: Encryption helps prevent data breaches, whether the data is in transit or at rest. Even if a device is lost or stolen, encrypted data remains secure.
- Data Integrity: Encryption, coupled with additional integrity safeguards, ensures that data sent over the internet remains unaltered and tamper-proof during transmission.
- Authentication: Public key encryption enables verification of the website owner’s authenticity, enhancing trust and preventing fraudulent activities.
- Regulatory Compliance: Various industry and government standards require organizations to encrypt user data, making end-to-end encryption crucial for compliance.
Applications of End-to-End Encryption
End-to-end encryption finds applications in various areas, including:
- Messaging Apps: Secure messaging apps employ end-to-end encryption to protect users’ conversations and ensure that only the intended recipients can read the messages.
- Email Services: Some email providers offer end-to-end encryption options, allowing users to send and receive encrypted emails for added security.
- File Sharing: End-to-end encryption can be used to secure the transfer of files, ensuring that they remain protected throughout the process.
Challenges and Limitations
While end-to-end encryption offers robust security, it is not without challenges and limitations. Some of these include:
- Key Management: The secure distribution and management of encryption keys can be complex, especially in large-scale deployments.
- Metadata Vulnerability: While the content of the data is protected, metadata such as sender and recipient information may still be accessible.
- User Experience: Implementing end-to-end encryption can sometimes introduce complexities and impact the user experience, leading to trade-offs between security and convenience.
The Future of End-to-End Encryption
The future of end-to-end encryption looks promising as more individuals and organizations recognize the importance of securing their data and communication. Technological advancements, improved key management systems, and user-friendly implementations are expected to address some of the current limitations, making end-to-end encryption more accessible and widespread.
FAQs
What platforms offer end-to-end encryption?
Several messaging platforms provide end-to-end encryption, including WhatsApp, Signal, iMessage, and more. However, it’s important to note that not all platforms have end-to-end encryption enabled by default.
Can end-to-end encryption be overridden by service providers?
In genuine end-to-end encryption systems, service providers do not possess the decryption keys, ensuring that they cannot access the encrypted data. However, some platforms may have certain exceptions or variations in their encryption policies, particularly for business chats or third-party integrations.
Is end-to-end encryption the most secure form of data protection?
End-to-end encryption is currently considered the most robust and reliable method to protect data during transmission. However, it’s essential to follow best practices such as using strong passwords and keeping devices secure to enhance overall data security.
Is end-to-end encryption completely secure?
End-to-end encryption provides a high level of security, but it’s important to implement it correctly and use strong encryption algorithms. However, it’s essential to understand that no security measure is entirely foolproof.
Can end-to-end encryption be hacked?
End-to-end encryption is designed to be extremely difficult to hack. However, it’s important to keep your devices and applications updated with the latest security patches to minimize vulnerabilities.
Can end-to-end encryption be used for voice and video calls?
Yes, end-to-end encryption can be applied to voice and video calls, ensuring that the content of the calls remains private and inaccessible to unauthorized parties.
Can end-to-end encryption protect against phishing attacks?
While end-to-end encryption protects the content of the communication, it does not directly protect against phishing attacks. Users should still exercise caution and be vigilant while interacting with unknown or suspicious sources.
Is end-to-end encryption legal?
End-to-end encryption is legal in many jurisdictions, as it serves as an essential tool for privacy and data protection. However, specific regulations may vary by country, so it’s advisable to consult local laws and regulations.
Key Takeaways:
- Encryption is the process of encoding information to make it unreadable without the appropriate decryption key.
- End-to-end encryption ensures that only the intended recipients can access decrypted data.
- Unique encryption keys are used to encrypt and decrypt the data.
- Benefits of end-to-end encryption include enhanced privacy, protection from intermediaries, and secure communication.
- Applications of end-to-end encryption include messaging apps, email services, and file sharing.
- Challenges and limitations include key management complexities and potential metadata vulnerabilities.
- The future of end-to-end encryption holds promise with technological advancements and improved user-friendly implementations.
- End-to-end encryption provides a powerful solution for securing data and communication in the digital landscape.
Conclusion
End-to-end encryption is a vital technology that ensures secure communication and protects data from unauthorized access. By encrypting data at the device level and employing strong encryption algorithms, end-to-end encryption provides privacy, security, data integrity, authentication, and regulatory compliance. While no system is entirely hack-proof, end-to-end encryption significantly reduces the risk of data breaches. Its adoption by popular messaging platforms highlights its importance in safeguarding sensitive information.
