Definition of Encryption And Its Role in Data Security
Encryption is a process of converting plain text into a coded form that can only be decoded and read by someone who has the key to unlock it. Encryption plays a crucial role in data security as it protects sensitive information from unauthorized access and theft. In today’s digital age, where data breaches and cyber-attacks are becoming increasingly common, encryption has become a necessity for businesses and individuals alike.
Types of Encryption And How They Work
There are several types of encryption, including symmetric encryption, asymmetric encryption, and hashing. Symmetric encryption involves using the same key to both encrypt and decrypt data. This means that both the sender and receiver of the data must have access to the same key. While symmetric encryption is relatively fast and efficient, it can be less secure than other types of encryption if the key is compromised.
Symmetric Encryption
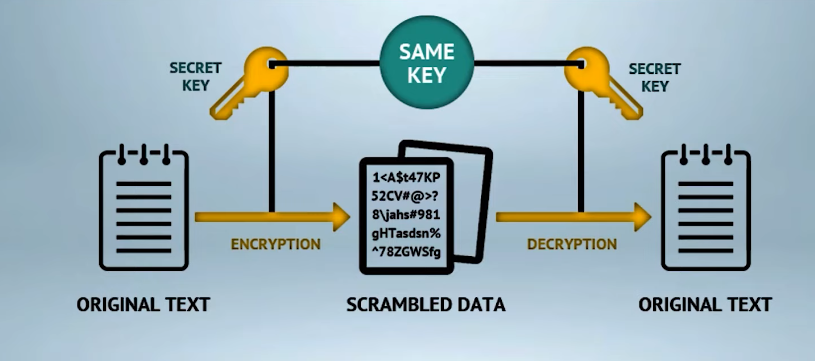
Symmetric encryption is a type of encryption where the same key is used to encrypt and decrypt data. Both the sender and receiver of the data must have access to the same key. This type of encryption is relatively fast and efficient, but it can be less secure than other types of encryption if the key is compromised. Examples of symmetric encryption algorithms include Advanced Encryption Standard (AES) and Data Encryption Standard (DES).Asymmetric encryption
Asymmetric Encryption
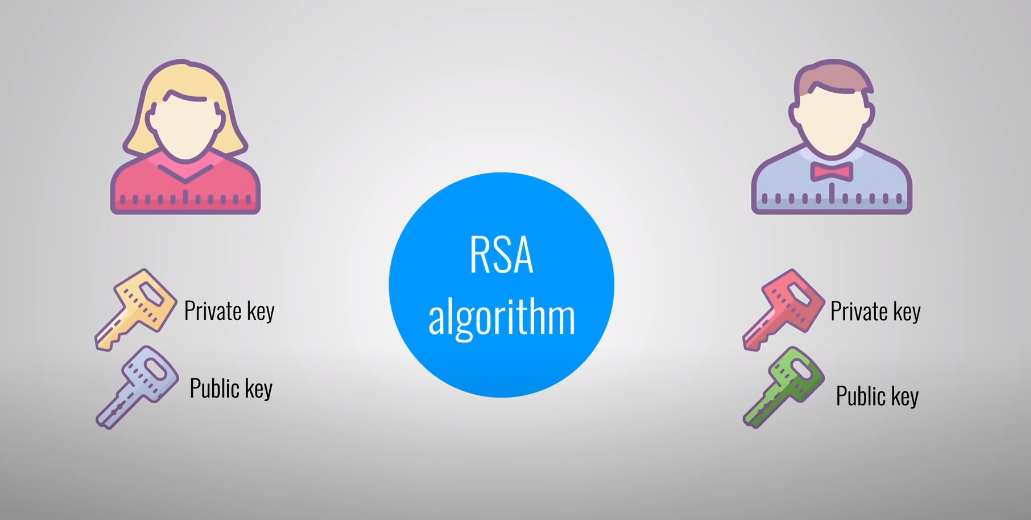
It is a type of encryption where two different keys are used to encrypt and decrypt data. These keys are mathematically related, but one key is kept private (the private key) and the other is shared publicly (the public key). The sender of the data uses the recipient’s public key to encrypt the data, and the recipient uses their private key to decrypt it. This type of encryption is more secure than symmetric encryption, but it can be slower and less efficient. Examples of asymmetric encryption algorithms include
Hash Functions
Hash functions are one-way mathematical functions that take input data and produce a fixed-size output called a hash value or digest. Hash functions are used for data integrity and digital signature verification, but they do not involve keys or encryption. Examples of asymmetric encryption algorithms include RSA (Rivest-Shamir-Adleman), Diffie-Hellman, and Elliptic Curve Cryptography (ECC).
Weaknesses in Encryption
- Known vulnerabilities in encryption algorithms
- Brute-force attacks and their limitations
- Side-channel attacks
- Quantum computing and its impact on encryption
Overview of Encryption Standards
Encryption is a powerful tool for securing data, but it is not foolproof. There are several weaknesses in encryption that can be exploited by attackers. One weakness is known vulnerabilities in encryption algorithms. Cryptographic algorithms are designed to be secure, but they can have flaws that make them vulnerable to attack. These vulnerabilities can be exploited by attackers to gain access to encrypted data.
AES (Advanced Encryption Standard)
AES (Advanced Encryption Standard) is a widely used encryption standard that is considered to be very secure. It uses a symmetric key encryption algorithm, which means that the same key is used for both encryption and decryption. AES is used in a variety of applications, including online banking, email encryption, and file encryption.RSA encryption
RSA encryption is a type of asymmetric encryption, which means that it uses two different keys for encryption and decryption.
RSA (Rivest-Shamir-Adleman)
RSA encryption is a widely used encryption algorithm that is considered to be very secure. It uses a public key for encryption and a private key for decryption. The public key is shared with anyone who needs to send encrypted messages to the owner of the private key. RSA encryption is commonly used in digital signatures, secure email, and secure online transactions. It is named after its inventors Ron Rivest, Adi Shamir, and Leonard Adleman.
SHA (Secure Hash Algorithm)
SHA, or Secure Hash Algorithm, is a family of cryptographic hash functions that are widely used for data integrity verification, digital signatures, and password storage. It generates a fixed-length output, known as a hash, from any input data, which can be used to verify the integrity of the original data. SHA algorithms are designed to be secure against various attacks, including collision attacks, where two different inputs produce the same hash output. The most widely used SHA algorithms are SHA-1, SHA-2,
What It Means To “Crack” Encrypted Data
To “crack” encrypted data means to gain unauthorized access to the original data by breaking the encryption algorithm used to protect it. This can be done by using various techniques, such as brute-force attacks, where an attacker tries every possible key or password combination until the correct one is found, or by exploiting vulnerabilities in the encryption algorithm itself. Once the encryption is cracked, the attacker can access and potentially manipulate the original data, which can be a serious security threat.
Methods Used To Crack Encrypted Data
There are several methods used to crack encrypted data, including:
- Brute-force attacks: This involves trying every possible key or password combination until the correct one is found. This method can be effective, but it can also be time-consuming and resource-intensive.
- Dictionary attacks: This involves using a list of common passwords or phrases to try and guess the correct key. This method is often more efficient than brute-force attacks, but it may not work if the password is unique or complex.
Rainbow Tables
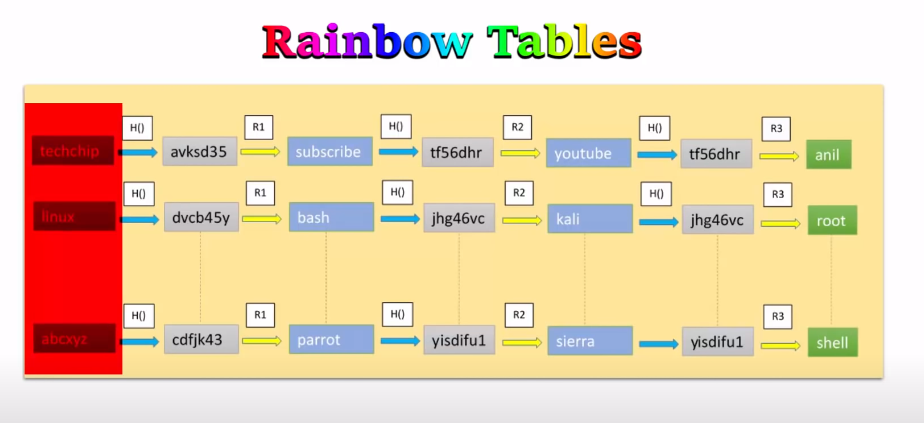
Rainbow tables are precomputed tables of encrypted passwords or keys that can be used to quickly crack encrypted data. These tables are created by hashing every possible password or key combination and storing the results in a table. When trying to crack an encrypted password, the attacker can look up the hash value in the table and quickly find the corresponding password or key. While rainbow tables can be effective, they require a lot of storage space and may not work if the password has been salted.
Social Engineering Attacks
Social engineering attacks are a type of cyber attack that involves manipulating individuals into divulging sensitive information or performing actions that they would not normally do. These attacks can take many forms, such as phishing emails, phone scams, or impersonating a trusted authority figure. The goal of social engineering attacks is to exploit human psychology to gain access to sensitive information or systems. To protect against social engineering attacks, it is important to be vigilant and cautious when receiving unsolicited requests for information or actions.
Keylogging
Keylogging is a type of malicious software that records every keystroke made on a computer or mobile device. This can include login credentials, credit card numbers, and other sensitive information. Keyloggers can be installed on a device through phishing emails, infected downloads, or physical access to the device. To protect against keylogging, it is important to use strong passwords, keep software up-to-date with the latest security patches, and avoid clicking on suspicious links or downloading unknown software.
Best Practices For Protecting Encrypted Data
Encrypting data is an important step in protecting sensitive information from unauthorized access. Here are some best practices for protecting encrypted data:
- Use strong encryption algorithms: Choose encryption algorithms that are considered secure and have not been compromised.
- Use strong encryption keys: Use long and complex encryption keys that are not easily guessable.
- Store encryption keys securely: Keep encryption keys in a secure location that is only accessible to authorized personnel.
- Use multi-factor authentication
Overview of the Future of Encryption
Encryption is expected to continue to play a critical role in protecting sensitive data in the future. As technology advances, encryption algorithms will need to become more complex to keep up with potential threats. Additionally, the use of quantum computing may require new encryption techniques to be developed. However, the need for secure communication and data protection will remain a priority, making encryption an essential tool for individuals and organizations alike.
Impact of Quantum Computing
Quantum computing has the potential to revolutionize the field of cryptography, which is the science of encoding and decoding information. Traditional encryption methods rely on the difficulty of factoring large numbers, but quantum computers can solve these problems much more efficiently than classical computers. This means that current encryption methods may become vulnerable to attacks from quantum computers in the future.To address this issue, researchers are developing new encryption techniques that are resistant to quantum attacks.
Myths And Misconceptions Surrounding Encryption
Encryption is a complex topic that is often misunderstood. Here are some common myths and misconceptions surrounding encryption:
- Encryption is only used by criminals: While it’s true that encryption can be used by criminals to hide their activities, it is also used by businesses, governments, and individuals to protect sensitive information.
- Encryption is unbreakable: While encryption can provide strong protection for data, it is not unbreakable. As mentioned earlier, quantum computers have the potential to break current encryption methods
How Encryption Protects Individual Privacy
Encryption is a powerful tool for protecting individual privacy. When data is encrypted, it is transformed into a code that can only be deciphered with the proper key. This means that even if someone gains access to the encrypted data, they will not be able to read it without the key.For example, when you use a messaging app like WhatsApp or Signal, your messages are encrypted so that only the intended recipient can read them. This prevents anyone else from intercepting and reading your messages.
Encryption And Government Surveillance
Encryption has been a topic of debate when it comes to government surveillance. Some governments argue that they need access to encrypted data in order to prevent terrorism and other criminal activities. However, privacy advocates argue that weakening encryption would make everyone’s data vulnerable to hackers and other malicious actors. In recent years, there have been several high-profile cases where tech companies have refused to comply with government requests to decrypt data.
Conclusion
In conclusion, the debate over encryption and government surveillance is complex and ongoing. While governments argue that access to encrypted data is necessary for national security, privacy advocates argue that weakening encryption would have serious consequences for individuals’ privacy and security. As technology continues to advance, it is likely that this debate will continue and evolve in new ways.
FAQs
Is it possible to hack encrypted data?
While it is technically possible to hack encrypted data, it is extremely difficult and time-consuming. Encryption is designed to make it nearly impossible for unauthorized parties to access or decipher the data. However, there have been cases where hackers have successfully breached encrypted systems, highlighting the importance of strong encryption and cybersecurity measures.
Can encrypted data be cracked?
As mentioned earlier, it is technically possible to crack encrypted data, but it is extremely difficult and time-consuming. The level of difficulty depends on the strength of the encryption algorithm and the length of the encryption key. A longer key using a strong encryption algorithm is much harder to crack than a shorter key using a weaker algorithm. However, with the advancement of technology, it is important to continuously update and improve encryption methods to stay ahead of potential hackers.
What is the strongest form of encryption?
Different encryption algorithms have different levels of strength and are suitable for different purposes. Some of the most commonly used encryption algorithms include Advanced Encryption Standard (AES), RSA, and Blowfish. It is important to choose an encryption method that is appropriate for the specific needs and level of security required for the data being encrypted.
What is the future of encryption?
The future of encryption is likely to involve the development of more advanced and sophisticated encryption algorithms that are even more secure than current methods. This may include the use of quantum encryption, which uses the principles of quantum mechanics to create unbreakable codes. Additionally, there may be a shift towards more decentralized encryption methods, such as blockchain-based encryption, which can provide greater security and privacy for users. As technology continues to evolve, encryption will remain an essential tool for protecting sensitive information and maintaining online security.
