Introduction
Data encryption is a critical aspect of data protection, and businesses today need to be more vigilant than ever before in safeguarding their sensitive information. Zerto Data Encryption is designed to provide enhanced security for businesses that rely on virtual replication solutions. With this technology, data can be encrypted both in transit and at rest, ensuring that it remains safe from unauthorized access or theft.
However, implementing Zerto Data Encryption requires a clear understanding of the technology and its capabilities. This guide will explore everything you need to know about Zerto Data Encryption, from the benefits it offers to how it should be implemented. It will also delve into some of the most common questions regarding this technology and provide answers that can help businesses make informed decisions about how best to use it for their needs.
Part 1: Understanding Zerto
What is Zerto?
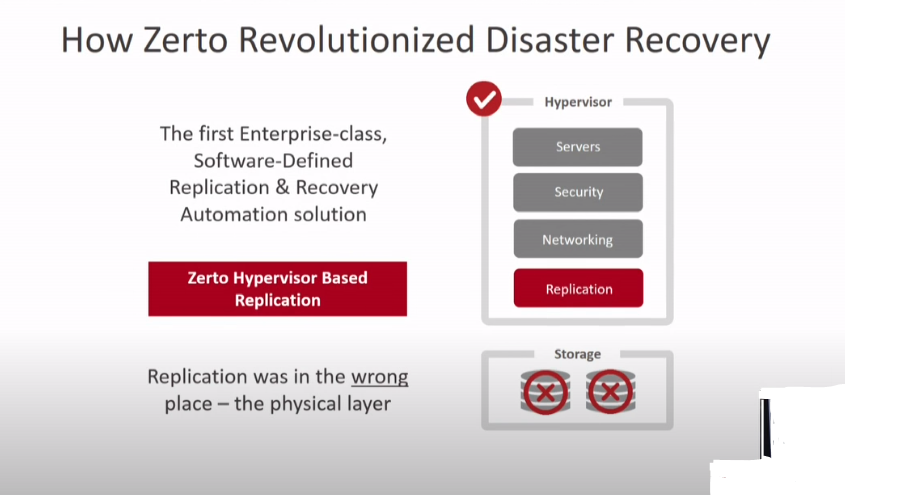
Zerto is a software company that provides disaster recovery and business continuity solutions to organizations of all sizes. The platform allows businesses to replicate their critical infrastructure and data in real time, ensuring minimal downtime in the event of an outage or disaster. Zerto’s technology enables businesses to recover quickly from data loss incidents by creating virtual copies of their production environment.
Zerto’s solution is designed for use across private, public, and hybrid cloud environments. It supports various hypervisors like VMware vSphere, Microsoft Hyper-V, Linux KVM, Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), IBM Cloud, and more. The platform uses continuous data protection (CDP) technology to provide better recovery point objectives (RPOs) than traditional backup solutions.
Businesses can leverage Zerto for multiple use cases such as disaster recovery testing, migration between clouds, or even on-premises systems without any downtime or risk and for long-term retention of archived data.
How Does Zerto Work?

Zerto is a disaster recovery solution that works by continuously replicating data from production servers to a secondary location, such as a cloud-based environment or remote data center. Whenever there’s a disruption in the primary site, Zerto can easily switch over to the secondary site with minimal downtime.
Zerto stands out because it’s hypervisor-based and hardware agnostic, allowing users to replicate across different storage systems without any compatibility issues. It also enables point-in-time recovery so that organizations can restore their data to specific moments before an outage occurred. Additionally, Zerto’s journaling technology tracks all changes made within the system in real time, making it possible to rewind transactions if necessary.
Part 2: What is Data Encryption?
Definition And Explanation Of Data Encryption
Data encryption is a process of converting plain text into an unreadable format that can only be deciphered using a secret key or password. It is a crucial security measure used to protect sensitive data from unauthorized access, theft, and manipulation. Encryption algorithms use complex mathematical formulas to scramble the original message into an unintelligible code.
Encryption can be applied to various types of data such as emails, files, databases, and even entire hard drives. The encrypted data can only be decrypted by someone who has access to the corresponding key or password. This means that even if hackers manage to intercept the encrypted data, they won’t be able to read it without the proper decryption tools.
Data encryption is particularly important in industries that handle sensitive information such as healthcare, finance, and government agencies. It ensures compliance with privacy regulations and reduces the risk of data breaches.
Types Of Data Encryption
There are several types of data encryption techniques that can be used to protect sensitive information from unauthorized access. One popular method is symmetric-key encryption, where the same key is used for both encryption and decryption. This type of encryption is commonly used in secure messaging applications and file-sharing services.
Another widely-used technique is asymmetric-key encryption, which involves two keys – a public key for encrypting data and a private key for decrypting it. This type of encryption is often used in online transactions, such as banking websites or e-commerce platforms.
A third approach to data encryption that has gained popularity in recent years is homomorphic encryption. This technology allows computations to be performed on encrypted data without having to decrypt it first, making it ideal for scenarios where privacy and security are critical concerns. Homomorphic encryption has numerous potential applications in fields such as healthcare, finance, and government agencies where sensitive data needs to be analyzed without being exposed.
Importance Of Data Encryption
Data encryption helps in maintaining compliance with regulations like HIPAA or GDPR that require organizations to keep private customer information secure. It also provides protection against internal threats such as unauthorized employee access to sensitive data. In addition, encrypted data is less vulnerable during transmission over networks since any interception would only yield meaningless code.
Investing in robust encryption solutions can provide peace of mind knowing that your organization’s confidential information is secure even if it falls into the wrong hands. Properly encrypting your data can go a long way in preventing costly breaches and legal consequences associated with non-compliance with regulatory requirements.
Part 3: Zerto Data Encryption Features
What Kind Of Data Encryption Does Zerto Use?
Zerto, a leading disaster recovery, and business continuity software provider, uses AES 256-bit encryption to encrypt data at rest and in transit. This is the same encryption standard used by financial institutions, government agencies, and military organizations worldwide. With AES 256-bit encryption, Zerto ensures that data remains safe and secure even if it falls into the wrong hands.
In addition to AES 256-bit encryption, Zerto also implements Secure Sockets Layer (SSL) technology for secure communication between servers. SSL is a protocol that encrypts all communication between servers using public key cryptography. This ensures that all data transmitted between servers cannot be intercepted or modified by unauthorized parties.
Benefits Of Zerto Data Encryption
Zerto data encryption offers several benefits for organizations, including enhanced security, regulatory compliance, and improved business continuity. By encrypting data both in transit and at rest, Zerto can help prevent unauthorized access to sensitive information. This is especially important for businesses that handle confidential customer or financial data.
Furthermore, Zerto’s encryption capabilities enable organizations to comply with various regulations such as HIPAA, GDPR, and PCI DSS. Compliance with these standards is crucial as non-compliance can result in significant fines and reputational damage. With Zerto’s data encryption solution, organizations can ensure they meet these requirements while also protecting their critical business operations.
Zerto’s data encryption also helps improve business continuity by ensuring that mission-critical applications and services remain available even during a cybersecurity incident or breach. With encrypted data backups stored securely offsite, businesses can quickly recover from any disaster without worrying about the loss of sensitive information or downtime due to cyberattacks.
Part 4: Implementation of Zerto Data Encryption
Steps To Implement Zerto Data Encryption
- Understand the importance of data encryption: Before implementing Zerto data encryption, it is important to understand why it is necessary. Data encryption helps protect sensitive information from unauthorized access and ensures confidentiality. It also helps companies comply with various regulations such as HIPAA, GDPR, and PCI DSS.
- Determine the scope of encryption: Once you have decided to implement Zerto data encryption, determine the scope of what needs to be encrypted. This includes identifying which applications and databases need to be encrypted, what type of data needs to be protected (e.g., personal information or financial records), and who should have access to the encrypted information.
- Configure Zerto Virtual Replication: To enable Zerto data encryption, you will need to configure your virtual replication environment accordingly. This involves setting up a secure connection between source and target sites using Secure Sockets Layer (SSL) certificates, configuring network settings for communication between sites, and enabling encryption in your replication policies.
- Test your implementation: After implementing Zerto data encryption, it is important to test its effectiveness regularly. Conduct regular vulnerability assessments or penetration tests on your environment to identify any potential security gaps or weaknesses in your implementation.
- Monitor and maintain security: Finally, once you have implemented Zerto data encryption successfully, continue monitoring your environment for potential threats or vulnerabilities while ensuring that all updates are applied promptly for optimal security maintenance over time.
Configuring Zerto Data Encryption
To configure Zerto data encryption using software-based encryption methods, you’ll need to first choose your preferred method of encryption – either Advanced Encryption Standard (AES) or TwoFish. Once you’ve made this decision, you can begin configuring your VMs to encrypt their respective volumes using these methods. This can be done either manually or through automation tools like PowerShell scripts.
Another important consideration when configuring Zerto data encryption is key management. It’s critical that you have a clear understanding of who has access to your keys and how they are managed over time. One option is to use a third-party key management solution that integrates with Zerto for added security and ease of use.
Part 5: Ensuring Compliance with Zerto Data Encryption
Regulatory Compliance Requirements
Zerto’s data encryption solution provides compliance with many regulatory requirements by using industry-standard encryption algorithms to secure data at rest and in motion. The solution allows organizations to encrypt their sensitive information while maintaining its accessibility for authorized users. This ensures that the organization remains compliant with the stringent regulations set forth by governing bodies while also enabling them to conduct business operations smoothly.
Compliance Best Practices With Zerto Data Encryption
Implement role-based access control for keys and passwords, ensuring that only authorized personnel can access encrypted data.
Regularly review the encryption policy and make changes as necessary to ensure it remains in line with changing compliance regulations. Additionally, performing regular audits of the system can also be beneficial in identifying potential vulnerabilities or gaps in security protocols. By following these best practices, companies can ensure that their encrypted data meet their industry’s compliance requirements while minimizing risk and maintaining strong security measures.
Auditing And Monitoring Zerto Data Encryption
To audit Zerto data encryption, you need to understand how it works. Zerto uses AES-256 encryption to secure both data in transit and at rest. The encryption keys are stored securely in a key vault to prevent unauthorized access. You can monitor the status of the encryption process through the management console, which provides real-time visibility into all activities related to data protection.
Regular audits should be conducted to ensure that all sensitive information is properly encrypted at all times. Monitoring should also include analyzing logs for suspicious activity or attempted breaches of security protocols.
Part 6: Best Practices for Zerto Data Encryption
Tips And Recommendations For Data Encryption
- Use strong passwords and encryption keys: It is important to use strong passwords and encryption keys when encrypting data. This ensures that the data is protected from unauthorized access and cannot be easily decrypted.
- Implement multi-factor authentication: Multi-factor authentication adds an extra layer of security by requiring users to provide additional information besides their username and password before accessing the encrypted data.
- Regularly update encryption software: Encryption software must be regularly updated to ensure that vulnerabilities are patched, reducing the risk of being exploited by cybercriminals.
- Encrypt all types of sensitive data: All types of sensitive data, including customer information, intellectual property, and financial records should be encrypted to prevent it from falling into the wrong hands.
- Properly manage encryption keys: The encryption key used for protecting the encrypted data must be properly managed to avoid loss or compromise by malicious actors.
- Test your encryption strategy regularly: Regular testing helps identify any weaknesses in your current system’s configuration before they can be exploited by attackers.
- Consider using third-party solutions for added protection: Organizations can consider using third-party solutions as an added layer of protection against potential attacks on their encrypted data.
- Train employees on proper handling of sensitive information: Employee training is essential in ensuring that all personnel with access to sensitive information understand how to handle it securely and avoid accidental exposure or loss through human error.
Ensuring Optimal Data Security With Zerto
Zerto is a data protection and disaster recovery software that ensures optimal data security. It offers encryption of data both in transit and at rest to ensure the confidentiality, integrity, and availability of information. The software provides a continuous replication process that enables quick restoration of systems and applications in case of any disruption or failure. Zerto also offers multiple layers of security with features such as multi-factor authentication, role-based access control, audit trails, and real-time alerting.
With Zerto’s encryption capabilities, organizations can be confident that their sensitive information is protected from unauthorized access or cyber-attacks. The software uses Advanced Encryption Standard (AES) 256-bit encryption to secure data while it’s transmitted over the network or stored on disks. AES 256-bit encryption is considered one of the most secure algorithms available today.
FAQs
What Is Zerto’S Stance On Quantum Computing And Encryption?
Zerto is a leading provider of disaster recovery and business continuity solutions, and they have been monitoring the developments in quantum computing and encryption. They believe that quantum computers will eventually become powerful enough to break current encryption methods, which could pose a significant threat to data security. To address this concern, Zerto has been working on developing post-quantum cryptography algorithms that can resist attacks from quantum computers.
Zerto is committed to staying ahead of the curve when it comes to data security, and its approach to quantum computing and encryption reflects this ethos. While many companies may be caught off guard by the rapid pace of technological change in this field, Zerto is taking proactive steps to prepare for the future. By investing in research and development, as well as collaborating with experts in cryptography and quantum computing, Zerto aims to ensure that their client’s data remains secure even as new threats emerge.
Does Zerto’S Encryption Techniques Affect Performance?
Zerto has designed its encryption technology to have minimal impact on storage performance. The platform also allows users to choose from several different levels of encryption based on their specific needs. While higher levels of encryption do require more processing power, they can provide an additional layer of protection against potential threats.
Can I Use My Own Encryption Keys With Zerto?
Yes, you can use your own encryption keys with Zerto. By default, Zerto uses industry-standard AES-256 encryption to protect your data both in transit and at rest. However, some organizations may have specific compliance requirements that necessitate the use of their own encryption keys.
To use your own encryption keys with Zerto, you can leverage the Key Management Interoperability Protocol (KMIP). KMIP is a standardized protocol for communication between key management servers and clients, allowing you to manage and distribute your own encryption keys across different platforms and vendors. With KMIP integration, you can easily configure Zerto to encrypt data using your organization’s preferred key management solution.
Conclusion
Zerto data encryption is a crucial aspect of maintaining security in today’s digital landscape. By encrypting data at rest and in transit, businesses can ensure that their sensitive information remains protected from cyber threats such as theft or hacking attempts. Zerto’s encryption capabilities offer an added layer of protection for businesses looking to safeguard their data and maintain compliance with industry regulations.
Moreover, the implementation of Zerto data encryption is a relatively straightforward process that can be easily integrated into existing systems. With its user-friendly interface and customizable settings, businesses can tailor Zerto’s encryption features to meet their specific needs and requirements. Ultimately, investing in a robust encryption solution like Zerto can provide peace of mind knowing that your critical business data is secure from potential breaches or attacks.
