To secure the contents of a folder, one should use data encryption. This involves converting the plaintext data into unreadable ciphertext using encryption algorithms and keys. Only those with the right decryption key can access the original data.
Data security has become more important than ever in today’s digital age. With the rise of cyberattacks and the potential for sensitive information to be compromised, it is crucial to protect your data. One effective way to safeguard your data is through encryption. By encrypting the contents of a folder, you can confirm that only authorized individuals can access the information within it. Together, we will discover the importance of data encryption, discuss the basics, and provide step-by-step instructions on encrypting folder contents. We will also cover tips for maintaining encrypted folders and troubleshooting common encryption issues.
Understanding the Importance of Data Encryption
Data encryption plays a vital role in data security. It involves transforming data into an unreadable ciphertext format using encryption algorithms. The only way to reverse this process and access the original data is by using a decryption key. By encrypting complex information, you can protect it from unauthorized access ensuring the confidentiality and integrity of your data.
Data encryption is not a new concept. Its origins can be traced back to early times when people used various techniques to conceal messages. For example, the ancient Greeks used a method called the “scytale,” where a message written on a strip of parchment was wrapped around a cylinder of a specific diameter. The recipient would need a cylinder of the same diameter to decipher the message correctly. This early form of encryption demonstrates the fundamental principle behind data encryption – transforming information into an unreadable form that can only be understood by those with the right “key.
The Role of Encryption in Data Security
Encryption serves as a critical component of data security strategies. It provides an additional layer of protection, making it extremely difficult for cybercriminals to decipher sensitive information. By encrypting your data, you can mitigate the risks related with data breaches and unauthorized access, minimizing potential damage and safeguarding the privacy of your data.
Modern encryption algorithms are complex and mathematically secure. They use advanced mathematical operations and cryptographic keys to scramble data, making it virtually impossible to decrypt without the correct key. This level of security is essential in today’s digital landscape, where cyber threats are continually evolving.
One widely used encryption algorithm is the Advanced Encryption Standard (AES). AES operates as a symmetric encryption algorithm, which implies that it utilizes the same key for both encryption and decryption processes. It has become the de facto standard for securing sensitive data used by governments, organizations, and individuals worldwide.
Risks of Unencrypted Data
Leaving your data unprotected presents significant risks. If your data ends up in the wrong hands, it can be exploited for malicious purposes such as identity theft or financial fraud. Furthermore, failing to secure your data can lead to violations of data protection regulations, resulting in both legal and financial repercussions.
A prominent example illustrating the consequences of data being left unsecured is the Equifax data breach of 2017. This breach exposed the personal information of approximately 147 million individuals, including sensitive details like social security numbers, birthdates, and addresses. This incident underscored the critical importance of data encryption and the severe consequences of inadequately safeguarding sensitive information.
Moreover, various data protection regulations, such as the General Data Protection Regulation (GDPR) in the European Union, mandate that organizations implement appropriate security measures, including data encryption, to safeguard personal data. Failing to comply with these regulations can result in substantial fines and damage to an organization’s reputation.
In summary, data encryption plays a pivotal role in data security, offering a robust defense against unauthorized access and data breaches. It ensures the confidentiality and integrity of sensitive information. By comprehending the significance of encryption and the risks associated with leaving data unsecured, individuals and organizations can proactively protect their data and uphold compliance with data protection regulations.
Basics of Data Encryption
Before we delve into the process of encrypting folder contents, let’s first understand the fundamentals of data encryption.
Data encryption is a crucial aspect of current cybersecurity. It is the process of converting plaintext data into ciphertext to protect its confidentiality. Encryption involves using complex algorithms and keys to scramble the data in a way that can only be deciphered by authorized individuals with the correct decryption key.
By encrypting data, organizations and individuals can ensure that sensitive information remains secure, even if it falls into the wrong hands. Encryption is vital in safeguarding personal data, financial transactions, and sensitive business information.
What is Data Encryption?
Data encryption is a complex process that involves mathematical algorithms and cryptographic keys. When data is encrypted, it is transformed into an unreadable format known as ciphertext. This ciphertext can only be converted back into its original form, known as plaintext, using the correct decryption key.
The encryption process typically involves three main components: the plaintext data, the encryption algorithm, and the encryption key. The encryption algorithm determines how the data will be scrambled, while the encryption key is the secret code that allows authorized individuals to decrypt the data.
Without the correct decryption key, the ciphertext appears as a jumble of random characters, making it virtually incredible for unauthorized individuals to access the original information.
Different Types of Data Encryption
Various types of data encryption methods are available, each with its strengths and vulnerabilities. Understanding the different types of encryption can help organizations choose the most suitable method for their needs.
- Symmetric Encryption: This technique uses a single key to encrypt and decrypt the data. It is a fast and efficient encryption technique commonly used to secure large data volumes. However, symmetric encryption requires securely sharing the encryption key between the sender and the recipient. The encrypted data becomes vulnerable if the key falls into the wrong hands.
- Asymmetric Encryption: Also known as public-key encryption, this method uses a pair of public and private keys. The public key encrypts the data, while the private key is used for decryption. Asymmetric encryption provides a more secure solution as the private key remains confidential and is not disclosed. However, it is slower than symmetric encryption and is typically used for secure communication and digital signatures.
- Hashing: Hashing is a one-way encryption method that changes data into a fixed-length string of characters. Unlike symmetric and asymmetric encryption, hashing is not used for confidentiality purposes. Instead, it is commonly used for data integrity verification. A hash function takes an input (data) and produces a unique fixed-size string of characters, known as a hash value. Even a small change in the input data will produce a significantly different hash value, making it useful for verifying data integrity.
Each type of encryption method has its advantages and disadvantages, and the choice of encryption technique depends on the specific necessities of the protected data.
Steps to Encrypt Folder Contents
Now that we have a solid understanding of data encryption let’s walk through the steps involved in encrypting the contents of a folder.
Choosing the Right Encryption Software
The first step in encrypting a folder is selecting suitable encryption software. There are numerous options available, ranging from free tools to commercial solutions. Consider factors such as encryption strength, user-friendliness, and compatibility with your operating system before deciding.
Process of Encrypting a Folder
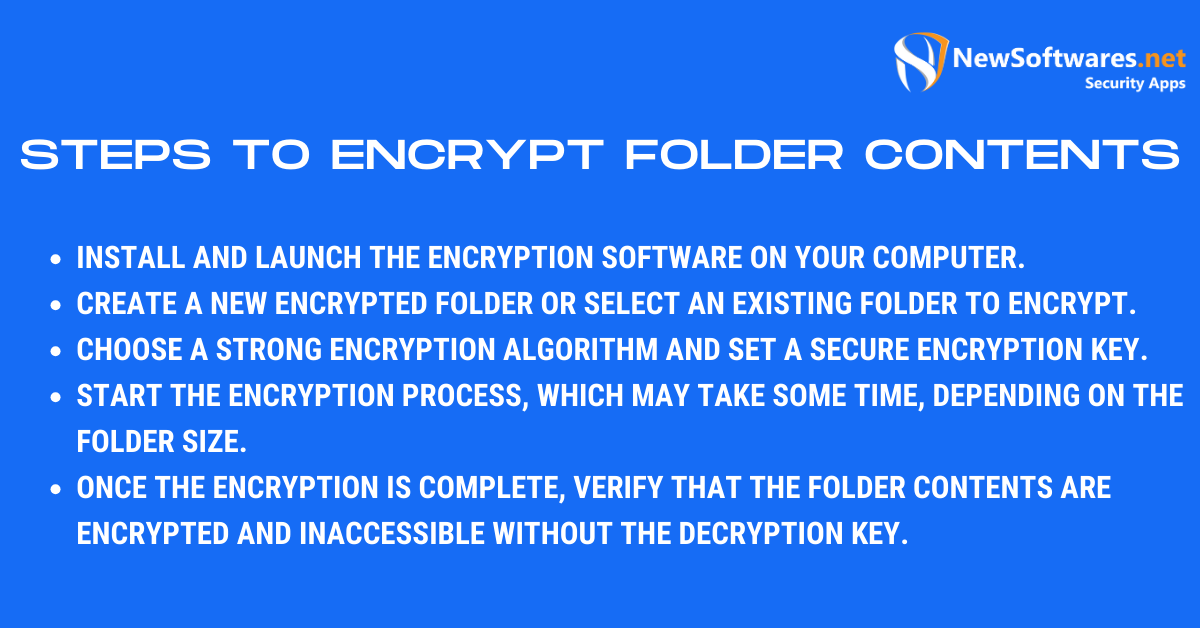
Once you have selected the encryption software, follow these steps to encrypt your folder contents:
- Install and launch the encryption software on your computer.
- Create a new encrypted folder or select an existing folder to encrypt.
- Choose a strong encryption algorithm and set a secure encryption key.
- Start the encryption process, which may take some time, depending on the folder size.
- Once the encryption is complete, verify that the folder contents are encrypted and inaccessible without the decryption key.
Maintaining Encrypted Folders
Encrypting your folders is only the first step in securing your data. It is essential to frequently maintain and update your encrypted folders to ensure maximum protection.
Regularly Updating Encryption Software
Encryption algorithms and software can become vulnerable over time due to technological advancements or the discovery of security vulnerabilities. It is crucial to keep your encryption software up to date by installing regular updates or patches provided by the software vendor. This ensures that you use the latest encryption technologies and benefit from improved security features.
Best Practices for Password Protection
When encrypting folders, paying close attention to password protection is essential. Select a strong and unique password that is tough to guess. Avoid using easily obtainable personal information such as birthdates or pet names. Additionally, consider changing your encryption password periodically to enhance security.
Troubleshooting Common Encryption Issues
While encrypting folder contents is generally straightforward, you may encounter certain issues along the way. Here are some common problems and their possible solutions.
Dealing with Lost Encryption Keys
If you misplace or forget your encryption key, it can be challenging to improve your encrypted data. To avoid such situations, make sure to store your encryption keys in a secure position, such as a password executive or a physical safe.
Resolving Encryption Software Errors
If you encounter errors or difficulties while encrypting your folders, refer to the software’s user manual or online documentation for troubleshooting steps. If the issue persists, seek assistance from the software’s support team or online communities.
Key Takeaways
- Data encryption transforms sensitive data into an unreadable format, ensuring it remains secure from unauthorized access.
- Modern encryption methods like the Advanced Encryption Standard (AES) provide a robust defense against cyber threats.
- Unencrypted data poses risks like identity theft, financial fraud, and non-compliance with data protection regulations.
- Symmetric Encryption employs a single key for both the encryption and decryption of data, whereas Asymmetric Encryption involves the utilization of a public key for encryption and a private key for decryption.
- Regularly maintaining encrypted folders, including updating software and ensuring strong password protection, is crucial for sustained data security.
FAQs
What is data encryption?
Data encryption converts plaintext data into an unreadable format called ciphertext using mathematical algorithms and cryptographic keys.
Why is data encryption important?
Data encryption safeguards data’s confidentiality and integrity, shielding it from unauthorized entree and potential cyber threats..
What are the main types of data encryption?
The primary types are Symmetric Encryption, Asymmetric Encryption, and Hashing.
How do you encrypt the contents of a folder?
To encrypt a folder, one should select appropriate encryption software, install it, create or select a folder, set a secure encryption key, and initiate the encryption process.
What should one do if they lose their encryption key?
It’s vital to store encryption keys securely, like in a password manager or physical safe. If lost, recovering encrypted data might be challenging, so precautions are necessary.
Conclusion
In conclusion, encrypting the contents of a folder is an essential step in securing your data. You can protect your sensitive info from unauthorized access by understanding the importance of data encryption, learning the basics of data encryption, and following the steps outlined in this article. Remember to maintain your encrypted folders by updating encryption software regularly and implementing best practices for password protection. If you encounter any issues, troubleshoot them promptly to ensure the integrity of your encrypted data. Stay vigilant and proactive in safeguarding your data through encryption, as it is crucial in today’s data-driven world.
