Cryptography is the science of encoding and decoding information to ensure data security. When data is encrypted, it is transformed into an unreadable format. Recovering the original data from this encrypted format requires decryption, achieved by applying the appropriate decryption key to the ciphertext.
Cryptography is the method used to recover original data that has been encrypted. I will explore the data encryption process and the challenges involved in recovering encrypted data. I will also discuss the role of cryptography in ensuring data security and the key concepts essential to understanding this field.
Understanding Cryptography: A Brief Overview
Data security is of chief importance in today’s digital landscape. With the increasing amount of sensitive information being conducted and stored online, it is crucial to have robust mechanisms to protect this data from unauthorized access. Cryptography, the science of secure communication, is vital in safeguarding sensitive information from prying eyes.
At its core, cryptography involves encoding data to become unreadable to anyone without the correct decryption keys. This ensures that even if the encrypted data is intercepted, it remains useless to the unauthorized entity. Cryptography encompasses various techniques and algorithms to protect data integrity, confidentiality, and authenticity. Encryption algorithms transform data into ciphertext, making it indecipherable to anyone without the corresponding decryption keys.
The role of cryptography in data security cannot be overstated. It provides a secure framework for transmitting information across networks, preventing unauthorized access or tampering. By encrypting data, cryptography ensures that sensitive information, such as personal or financial data, remains confidential and protected from cyberattacks.
Cryptography also enables secure communication between parties by establishing trust and verifying the authenticity of the transmitted data. Through techniques like digital signatures and certificates, cryptography verifies the integrity of the data, ensuring it has not been altered or tampered with during transmission.
The Role of Cryptography in Data Security
Cryptography forms the foundation of data security. It provides a secure framework for transmitting information across networks, preventing unauthorized access or tampering. By encrypting data, cryptography ensures that sensitive information, such as personal or financial data, remains confidential and protected from cyberattacks.
Cryptography also enables secure communication between parties by establishing trust and verifying the authenticity of the transmitted data. Through techniques like digital signatures and certificates, cryptography verifies the integrity of the data, ensuring it has not been altered or tampered with during transmission.
Furthermore, cryptography plays a crucial role in ensuring data privacy. With the increasing number of data breaches and cyber threats, protecting sensitive information from falling into the wrong hands is essential. By encrypting data, cryptography ensures that even if an unauthorized entity gains access to the encrypted data, it cannot decipher it without the correct decryption keys.
In addition to data confidentiality, cryptography also focuses on data integrity. It ensures that the data remains intact and unaltered during transmission. Through techniques like hash functions, which generate fixed-length values for data, cryptography can verify the integrity of the transmitted information. If any changes or tampering occur during transmission, the hash value will differ, indicating that the data has been compromised.
Key Concepts in Cryptography
Before delving into the data encryption and recovery process, it is important to understand some key concepts in cryptography. These concepts include:
- Symmetric Encryption: This encryption technique practices the same key for both the encryption and decryption procedures. It is faster but requires a secure method to exchange the key between the cooperating parties. Symmetric encryption is widely used in scenarios where speed and efficiency are crucial.
- Asymmetric Encryption: Also known as civic-key cryptography, this technique uses a pair of keys – one for encryption and another for decryption. The keys are mathematically linked but cannot be derived from one another. Asymmetric encryption offers higher security but is computationally more intensive than symmetric encryption. It is commonly used when secure communication and key exchange are essential.
- Hash Functions: These are one-way mathematical functions that convert data of any size into fixed-length values. Hash functions are usually used to verify the integrity of data and ensure it has not been tampered with. Cryptography can detect any changes or alterations in the data by generating a unique hash value for each piece of data.
- Digital Signatures: Digital signatures are cryptographic mechanisms that confirm the authenticity and integrity of digital documents or messages. They provide a way to ensure that the message’s sender is who they claim to be and that the message has not been tampered with during transmission. Digital signatures use asymmetric encryption techniques to bind the sender’s identity to the message securely.
- Certificates: Certificates are digital documents that bind a public key to an entity, such as an individual, organization, or website. They are used to establish trust in the authenticity of the public key and the entity’s identity. Certificates are issued by trusted third-party entities known as Certificate Authorities (CAs) and play a crucial role in secure communication and online transactions.
By understanding these key concepts in cryptography, one can gain a deeper obligation for the intricate mechanisms that underpin data security and privacy in the digital age.
The Process of Data Encryption
Data encryption converts plain text into ciphertext using an encryption algorithm and a key. Let’s explore some different types of data encryption techniques.
Different Types of Data Encryption
There are various types of data encryption techniques, including:
- Advanced Encryption Standard (AES): AES is a widely used symmetric encryption algorithm that provides strong security. It operates on fixed block sizes and helps key lengths of 128, 192, or 256 bits.
- Rivest Cipher (RC) Series: The RC series includes algorithms like RC4 and RC5. These stream ciphers are commonly used in wireless communication and are known for their simplicity and efficiency.
- RSA Encryption: RSA is an asymmetric encoding algorithm that uses a pair of keys – a free key for encryption and a private key for decoding. RSA encryption is widely used in secure communication and digital signatures.
How Does Data Encryption Work?
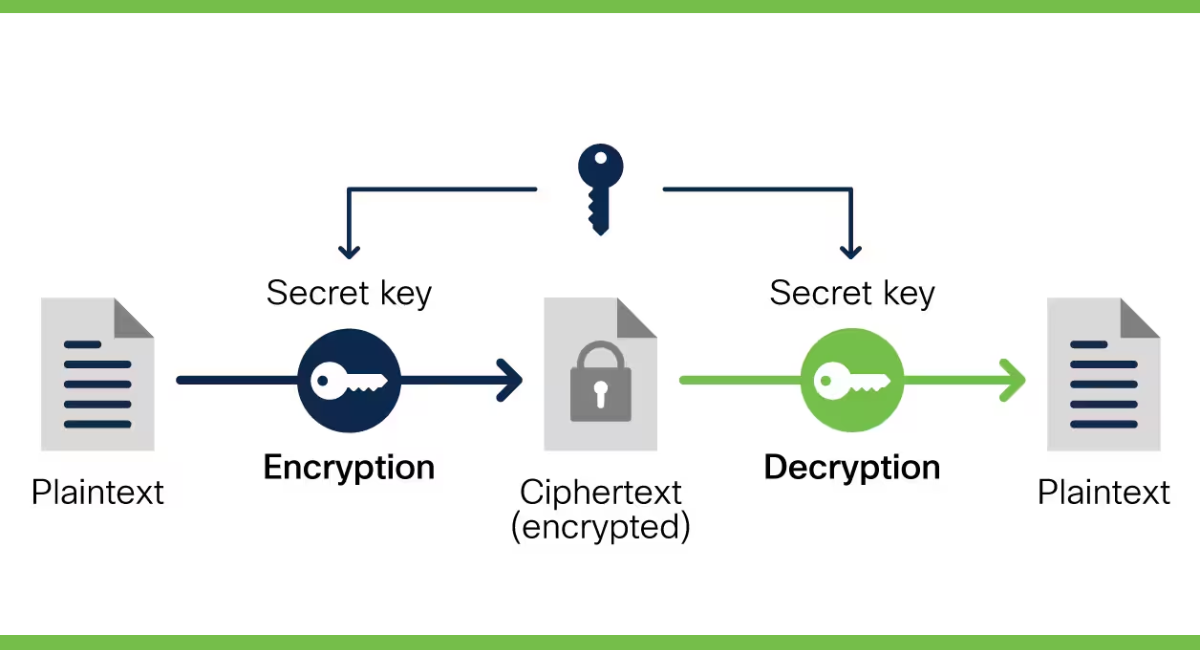
Data encryption applies mathematical operations to the plaintext using an encoding algorithm and a password. Encryption transforms the data into ciphertext, rendering it unreadable to unauthorized parties. The encrypted data can only be decrypted through the matching decryption key.
During encryption, the data is divided into fixed-size blocks, and each block is processed using the encryption algorithm. The resulting ciphertext is a scrambled version of the original data, ensuring that even if an invader gains access to the encrypted data, they cannot decipher its contents without the decryption key.
The Methodology of Recovering Encrypted Data
Recovering encrypted data involves decrypting the ciphertext using the correct decryption key. However, this process can be challenging and requires careful management of the encryption keys.
The Importance of Key Management in Data Recovery
Key management is crucial in data recovery. Without the correct decryption key, recovering encrypted data is virtually impossible. Organizations must establish robust key management practices to ensure the security and availability of encryption keys.
Proper key management includes secure generation, storage, distribution, and revocation of encryption keys. It also involves implementing key backup and recovery mechanisms to prevent data loss in case of key compromise or system failures.
Steps Involved in Decrypting Data
The process of decrypting data involves the following steps:
- Obtain the decryption key: The correct key must be acquired from a secure source or trusted party.
- Validate the decryption key: Ensure that the obtained decryption key is valid and corresponds to the encrypted data.
- Apply the decryption algorithm: Use the decryption key and algorithm to reverse the encryption process and convert the ciphertext back into plaintext.
- Verify the integrity of the decrypted data: Validate the decrypted data to ensure its integrity and that it has not been tampered with during the decryption process.
Challenges in Recovering Encrypted Data
While cryptography provides a vital layer of security for data, recovering encrypted data can present significant challenges.
Potential Risks and Threats in Data Recovery
One of the key risks in data recovery is the loss or compromise of decryption keys. It becomes extremely difficult to recover encrypted data without the correct encryption keys. Malicious actors and advanced cyber threats pose a constant risk to key security, making it crucial to implement proper key management practices and protect keys from unauthorized access.
Overcoming Obstacles in Data Decryption
Various obstacles, including the use of strong encryption algorithms and longer key lengths, can hinder data decryption. As technology advances, encryption techniques become more sophisticated, making it increasingly challenging to break the encryption without the correct decryption keys. This emphasizes the importance of implementing strong encryption algorithms and key management practices.
Future Trends in Cryptography and Data Recovery

The field of cryptography and data recovery is continually evolving. Let’s explore some future trends that could shape the industry.
The Impact of Quantum Computing on Cryptography
Quantum computation has the potential to revolutionize cryptography. Quantum computers practice quantum bits, or qubits, to process multiple states simultaneously. This computational power can potentially break many traditional encryption algorithms, rendering them ineffective. To counter this, researchers are exploring quantum-resistant encryption algorithms that can endure the power of quantum computers.
Innovations in Secure Data Recovery
As data security becomes more critical, advancements in secure data recovery are being developed. Techniques such as homomorphic encryption, which allows computations to be performed on encrypted data without decrypting it, are gaining prominence. These innovations provide secure and efficient methods for recovering encrypted data while preserving data confidentiality and integrity.
Key Takeaways
- Cryptography involves encoding data to ensure its confidentiality and integrity.
- Proper key management is essential in data recovery and overall data security.
- There are various encryption techniques, with symmetric and asymmetric being the most common.
- Data decryption converts ciphertext to its original plaintext form using a decryption key.
- The advent of quantum computing challenges traditional cryptographic methods, prompting the exploration of quantum-resistant algorithms.
FAQs
What is cryptography?
Cryptography is the science and practice of securely communicating information by encoding (encryption) and decoding (decryption) data.
What’s the importance of key management in cryptography?
Key management is vital as encrypted data security relies on the encryption keys’ secrecy and integrity. Proper key management ensures secure generation, storage, distribution, and revocation of these keys.
How does data encryption work?
Data encryption transforms plain data (plaintext) into an unreadable format (ciphertext) using specific algorithms and encryption keys.
Are there different types of encryption?
Yes, there are primarily two types: symmetric encryption, which uses a single key for both encryption and decryption and asymmetric encryption, which uses a pair of keys – a public key for encryption and a private key for decryption.
How does quantum computing impact cryptography?
Quantum computing, with its immense computational power, has the potential to break many traditional encryption algorithms, necessitating the development of quantum-resistant encryption techniques.
Conclusion
In conclusion, cryptography is a crucial method for recovering original data that has been encrypted. By understanding the data encryption process, the challenges in recovering encrypted data, and future trends in this field, we can appreciate the importance of cryptography in maintaining data security and privacy.
