To encrypt large amounts of data, one should utilize encryption techniques based on the data’s size, required security level, and available resources. Symmetric encryption is most suitable due to its speed and efficiency for large datasets. However, the choice between specific encryption tools, open-source or commercial, should align with individual needs, technical expertise, and budget.
In today’s digital age, the security of our data is of utmost importance. Effective encryption methods have become crucial with the ever-increasing amount of data being generated and transmitted. But what is the best way to encrypt large amounts of data? I will explore the various methods and factors to consider when choosing an encryption technique to protect your valuable data.
Understanding Data Encryption
Before delving into the different data encryption methods, it is essential to understand the significance of data encryption. Data encryption is the process of encoding information, making it unreadable to anyone who does not possess the decryption key. This ensures that even if unauthorized individuals can access the data, they cannot decipher its contents.
Data encryption is vital in safeguarding sensitive information such as personal details, financial data, and trade secrets. Without encryption, this information is vulnerable to interception and exploitation. Encryption provides protection, ensuring that only authorized individuals can access and understand the data.
But how does data encryption work? Let’s explore the basic principles behind it.
The Importance of Data Encryption
Data encryption protects sensitive info from unauthorized access and helps organizations comply with various data protection guidelines. For example, the General Data Protection Regulation requires businesses to implement suitable technical and organizational measures to protect personal data. Encryption is a recommended measure to achieve compliance with GDPR and other similar regulations.
Moreover, data encryption can prevent data breaches from causing severe damage. Even if a hacker manages to infiltrate a system and steal encrypted data, they cannot make sense of it without the decryption key. This buys organizations valuable time to detect and respond to the breach before harm is done.
Basic Principles of Data Encryption
Data encryption operates on two fundamental principles – algorithms and cryptographic keys. Encryption algorithms determine how the data will be transformed, while cryptographic keys encrypt and decrypt the data. The strength of encryption lies in the algorithm’s complexity and the keys’ secrecy.
Various encryption algorithms are available, each with its strengths and weaknesses. Some common encryption algorithms include Advanced Encryption Standard, Data Encryption Standard (DES), and Rivest Cipher (RC4). These algorithms use mathematical functions to scramble the data, making it unintelligible to unauthorized individuals.
Cryptographic keys, however, are like the secret codes that unlock the encrypted data. Without the correct key, the encrypted data remains unreadable. Keys can be of different lengths and generated using various methods, such as password-based key derivation or public-key cryptography.
It is important to note that the strength of encryption depends on both the algorithm’s complexity and the keys’ secrecy. If either of these components is compromised, the encrypted data becomes vulnerable to decryption.
In conclusion, data encryption is a crucial aspect of data security. It protects sensitive information from unauthorized access, helps organizations comply with data protection regulations, and mitigates the impact of data breaches. Understanding the importance and basic principles of data encryption is essential for individuals and organizations in today’s digital world.
Different Methods of Data Encryption
There are several methods of data encryption, each with its strengths and weaknesses. Understanding these approaches can help you choose the most suitable approach for encrypting large data.
Symmetric Encryption
Symmetric encryption, known as secret key encryption, uses a single key to encrypt and decrypt the data. This key needs to be securely shared between the sender and the recipient. Symmetric encryption is fast and efficient, making it suitable for encrypting large amounts of data. However, the challenge lies in securely distributing the encryption key.
The Advanced Encryption Standard (AES) is the most commonly used symmetric encryption algorithm. AES is widely adopted due to its security and efficiency. It operates on fixed-size data blocks & supports key sizes of 128, 192, and 256 bits. The strength of AES lies in its ability to resist various types of attacks, including brute force and known-plaintext attacks.
Another popular symmetric encryption algorithm is the Data Encryption Standard (DES). DES was widely used in the past but has been replaced by AES due to its vulnerability to brute force attacks. DES operates on 64-bit blocks of data and supports a 56-bit key size. Despite its vulnerabilities, DES is still used in some legacy systems.
Asymmetric Encryption
Asymmetric encryption, known as public-key encryption, utilizes a pair of keys – a public key for encoding and a private key for decryption. The public key is easily shared, while the private key is kept secret. Asymmetric encryption provides a more secure solution, as the private key remains hidden from unauthorized individuals. However, it is slower than symmetric encryption and less efficient for large-scale data encryption.
RSA (Rivest-Shamir-Adleman) is one of the most widely used asymmetric encryption algorithms. It is based on the mathematical problem of factoring large prime numbers. RSA supports key sizes ranging from 1024 to 4096 bits, with larger key sizes providing stronger security. Despite its popularity, RSA is computationally expensive and unsuitable for encrypting large amounts of data.
Another commonly used asymmetric encryption algorithm is Elliptic Curve Cryptography (ECC). ECC is based on the mathematics of elliptic curves and then offers the same level of security as RSA with much smaller key sizes. This makes ECC more efficient and suitable for resource-constrained environments such as mobile devices and embedded systems.
Hash Functions
Hash functions are cryptographic algorithms that convert data into fixed-length values known as hash codes. These hash codes are unique to the input data, ensuring its integrity. Hash functions are commonly used for password storage and data verification but are unsuitable for encrypting large amounts of data as they are irreversible.
One widely used hash function is the Secure Hash Algorithm (SHA). SHA-256, a variant of SHA, generates a 256-bit hash code and is commonly used for data integrity checks. It is widely adopted and considered secure for most applications. However, SHA-3, a newer variant of SHA, offers improved security and performance compared to SHA-256.
Another commonly used hash function is the Message Digest Algorithm (MD). MD5, a widely known variant of MD, generates a 128-bit hash code. However, MD5 is considered weak and vulnerable to collision attacks. Secure alternatives such as MD5, SHA-256, and SHA-3 should be used instead.
In conclusion, understanding the different data encryption methods is crucial for securing sensitive information. Symmetric encryption offers speed and efficiency, while asymmetric encryption provides stronger security. Hash functions ensure data integrity but are unsuitable for encrypting large amounts of data. Choosing the right encryption method protects your data from unauthorized access and ensures its confidentiality and integrity.
Factors to Consider When Encrypting Large Data
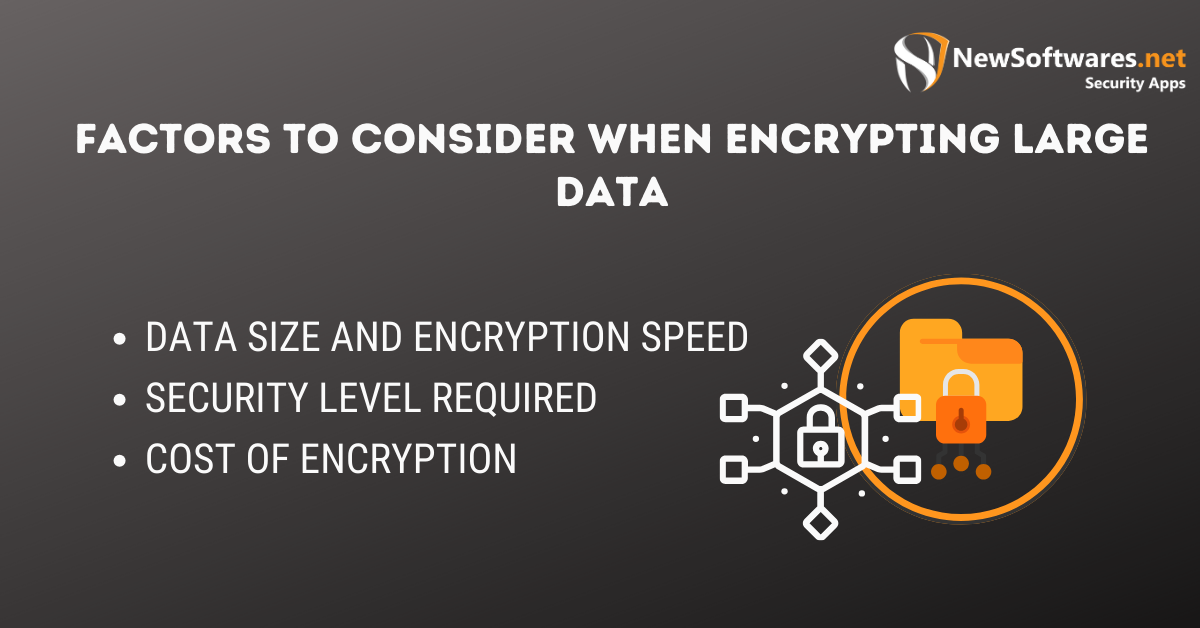
Certain factors need to be considered when deciding on the best encryption method for large amounts of data.
Data Size and Encryption Speed
The size of the data to be encrypted directly impacts the encryption speed. Symmetric encryption tends to be faster than asymmetric encryption for large data sets. It is essential to assess the encryption speed requirements and select a method to handle the data volume within acceptable time frames.
Security Level Required
The security level required for your data depends on its sensitivity. Assessing the potential threats and consequences of unauthorized access will help determine the appropriate encryption method. Asymmetric encryption provides higher security but may not be necessary for all types of data.
Cost of Encryption
Encryption methods vary in cost, both in terms of implementation and maintenance. Open-source encryption tools are often cost-effective as they are freely available, while commercial encryption tools may involve licensing fees. Consider the budget constraints and choose a method that aligns with your resources.
Comparing Popular Encryption Tools
When it comes to selecting an encryption tool, there are numerous options available.
Open-source Encryption Tools
Open-source encryption tools, such as GnuPG and OpenSSL, provide a transparent and community-driven approach to data encryption. They offer flexibility and customization options but may require more technical expertise for implementation and maintenance.
Commercial Encryption Tools
Commercial encryption tools, like Symantec Encryption and Bitdefender GravityZone, offer comprehensive encryption solutions with user-friendly interfaces. They often provide additional features, such as centralized management and customer support, but may come at a higher cost.
The Future of Data Encryption
As technology advances, so do the challenges and opportunities in data encryption.
Quantum Computing and Encryption
With the advent of quantum computing, the current encryption methods may become vulnerable to attacks. Researchers are actively developing quantum-resistant encryption algorithms to ensure data security in the post-quantum era.
AI in Data Encryption

Artificial intelligence (AI) is also employed in data encryption to enhance efficiency and effectiveness. AI algorithms can analyze patterns and identify potential vulnerabilities, thereby improving the overall security of encrypted data.
Key Takeaways
- Data encryption is essential to protect sensitive information and maintain data integrity and confidentiality.
- Symmetric encryption is recommended for encrypting large volumes of data due to its efficiency.
- Asymmetric encryption provides higher security levels but may be slower, making it less ideal for substantial data.
- The choice between open-source and commercial encryption tools depends on technical expertise, specific requirements, and budget.
- Emerging technologies, such as quantum computing and AI, pose challenges and opportunities in data encryption.
FAQs
What is data encryption?
Data encryption is the process of encoding information, rendering it unreadable without the proper decryption key, ensuring data confidentiality and integrity.
How does symmetric encryption differ from asymmetric encryption?
Symmetric encryption uses a single key for encryption and decryption, making it faster and more efficient for large data sets. Asymmetric encryption, on the other hand, employs a pair of keys (public and private) and offers higher security but is slower.
Are hash functions suitable for encrypting large data?
Hash functions convert data into fixed-length values to ensure data integrity. They’re not designed to encrypt large data sets, as their output is irreversible.
How might quantum computing impact encryption?
Quantum computing has the potential to break many current encryption algorithms, making it necessary to develop quantum-resistant encryption techniques.
Why might one choose open-source encryption tools over commercial ones?
Open-source tools offer transparency and flexibility and are generally cost-effective. In contrast, commercial tools often come with added features, user-friendly interfaces, and dedicated support but might be more expensive.
Conclusion
In conclusion, the best way to encrypt large amounts of data requires careful consideration of various factors such as the security level required, encryption speed, and cost. Symmetric encryption, asymmetric encryption, or hash functions can be utilized depending on these factors. The choice between open-source and commercial encryption tools should also be based on individual needs and resources. As technology evolves, staying informed about emerging technologies like quantum computing and AI will be essential to ensure the continued protection of our data.
