Organizations are built on ideas, and as we all know, ideas are hard to come by. Every organization has a secret, it could be their award winning software, their marketing secrets and tactics, their financial strategy or some other secret information, which, if leaked, could spell financial disaster for the organization. A surprising statistic from Ponemon institute states that in 2015, 43 percent of organization have experienced data leaks. Some organizations have spent millions of dollars in an attempt to keep out hackers from infiltrating their servers. However, the greatest threat to data security doesn’t come from hackers outside the organization, it comes from within.
Organizations, in an attempt to make quick money by offering lower wages are unknowingly demotivating employees. Also, there are some employees that will always want more. For example, employees who might be paid well will may still be dissatisfied with their jobs. Whether they want better benefits, a promotion, something they hate about their boss or any of the slightest factor leading towards demotivation, could potentially motivate employees to steal company data. Let’s look at some practical examples of why and how employees steal sensitive data.
Mike works for a ABC pharmaceutical company as a senior marketing officer. He’s been working for the past 5 years in the same position. He feels that his life is going nowhere, after repeatedly applying for a senior position for the past 1 year. To no avail, he fails to land that position, accordingly he decides to take matters into his own hands. One day he gets a call from recruiter who is looking for someone with a senior level position for a XYZ pharmaceuticals, a competing firm. It seems mike has the right skill set with the preferred mindset for the job. However, to be considered for the position, Mike will need to share some detailed marketing strategies with the competing firm. Likewise, mike decides to copy some sensitive information onto a USB drive, given that he had unrestricted access to corporate marketing data, he was able to copy it all into an external drive. After appearing for the interview, mike shares some impressive details to the competing firm and is offered the job on the spot – without hesitation – he accepts the job offer.
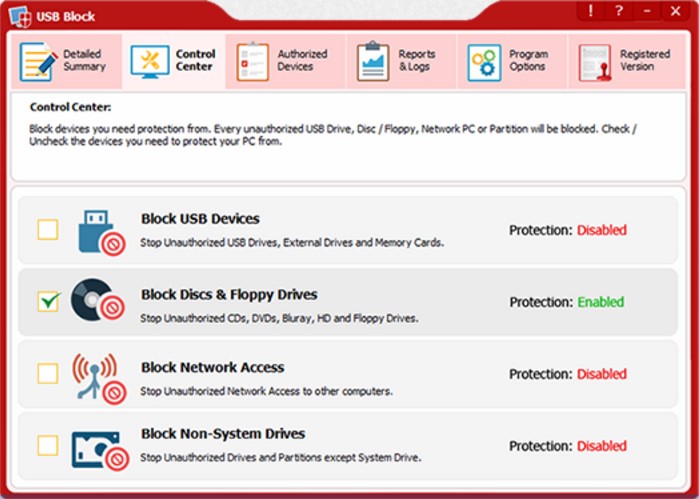
Ways to prevent data theft:
Accordingly, as the above example shows, organization that carelessly manage their secret data risk losing it at the hands of demotivated and rogue employees. The only solution that can prevent theft of corporate data is to block USB port, which can restrict people from copying certain files and folders onto external drives such as USB flash drives, external hard drives or prevent rogue employees from uploading this information to an online server, i.e. the cloud. One exceptional software which works quite effectively in preventing data leaks at the workplace is USB Block. It has been around for several years and restrict copying of data from all sources, whether it is USB ports, CD drives, WIFI connection or some other source of data leaks, USB Block will keep your corporate data safe.
Ways To Prevent Data Leakage
Data leakage can be prevented by implementing a variety of security measures, such as:
1. Establishing secure networks and firewalls to protect against unauthorized access.
2. Encrypting data to prevent unauthorized access to sensitive information.
3. Implementing access control measures to limit access to sensitive data.
4. Utilizing data monitoring and auditing tools to detect any suspicious activities or data leakage.
How Companies Prevent Data Breaches?
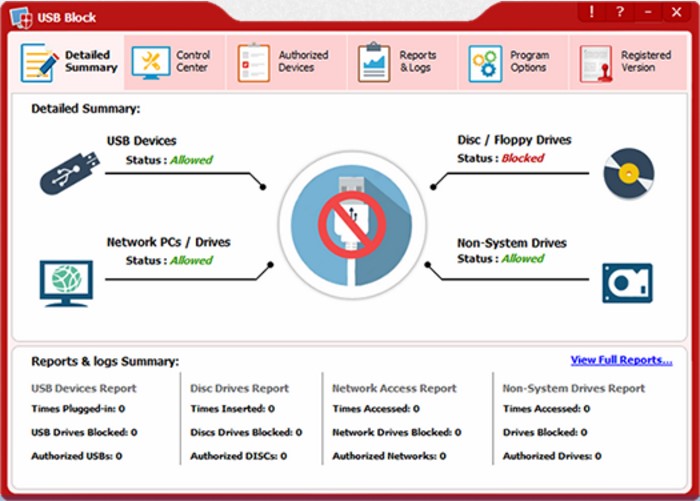
Companies can prevent data breaches by implementing a comprehensive security program that includes the following measures:
1. Establishing secure networks and firewalls to protect against unauthorized access.
2. Encrypting data and utilizing access control measures to limit access to sensitive information.
3. Regularly monitoring and auditing data to detect any suspicious activities or data breaches.
4. Training staff on security best practices and policies.
What Is Data Leakage And Why Should We Avoid It?
Data leakage is the unauthorized access or transmission of sensitive or confidential information. It can occur due to poor security measures or malicious intent. Data leakage can lead to identity theft, financial loss, and damage to a company’s reputation. To avoid data leakage, organizations should implement robust security measures such as encryption, access control, and regular monitoring and auditing.
Steps To Managing A Data Breach
1. Identify the breach: It is important to identify the source of the breach, the type of information that was compromised, and the extent of the breach.2. Notify affected parties: Once the breach is identified, affected parties should be notified as soon as possible.
3. Contain the breach: Organizations should take steps to contain the breach and prevent further damage.
4. Analyze and learn from the breach
Steps Of The Data Breach Response Plan
1. Pre-Incident Planning: Organizations should develop a plan of action to be taken in the event of a data breach.
2. Identify the Breach: It is important to identify the source of the breach, the type of information that was compromised, and the extent of the breach.
3. Notify Affected Parties: Once the breach is identified, affected parties should be notified as soon as possible.
Handle Breach Confidentiality In The Workplace
1. Establish a clear policy: Organizations should establish a clear policy on confidentiality that outlines what information is to be kept confidential and the consequences for breaching confidentiality.
2. Monitor employee access: Organizations should monitor employee access to confidential information to ensure that it is not being accessed without authorization.
3. Investigate breaches: Organizations should investigate any suspected breaches of confidentiality and take appropriate action to address the breach.
4. Educate employees: Organizations should educate employees on the importance of maintaining confidentiality
Methods Of Data Leakage
1. Unencrypted data transmission: Sending data over an unencrypted connection is one of the most common methods of data leakage.
2. Unsecured cloud storage: Cloud storage solutions that are not properly secured can be a source of data leakage.
3. Malware: Malicious software can be used to access confidential data.
4. Social engineering: Social engineering techniques such as phishing can be used to gain access to confidential data.
Major Reasons Of Data Leak
1. Human Error: This is the most common cause of data leaks. It could be due to lack of security awareness, negligence, or accidental data exposure.
2. Poor Security Practices: Weak security practices and lack of security measures can also lead to data leaks.
3. Hacking: Hackers can gain access to confidential data by exploiting vulnerabilities in systems or networks.
4. Data Breaches: Data breaches occur when unauthorized individuals gain access to sensitive data.
Ways To Secure Data
1. Encryption: Encrypting data can help protect it from unauthorized access.
2. Access Control: Establishing access control policies and procedures can help prevent unauthorized access to data.
3. Firewalls: Firewalls can help protect data from malicious attacks.
4. Monitoring and Auditing: Regularly monitoring and auditing systems can help detect any unauthorized access to data.
5. Data Backup: Regularly backing up data can help ensure that data is not
Principles Of The Data Protection
1. Transparency: Data controllers must be open and transparent about how they process personal data.
2. Legitimate Purpose: Personal data must be processed for legitimate and specified purposes only.
3. Data Minimization: Data controllers must only collect and process the minimum amount of personal data necessary for the specified purpose.
4. Accuracy: Personal data must be accurate and kept up to date.
Essential Data Protection Methods
1. Encryption: Encrypting data to protect it from unauthorized access.
2. Access control: Restricting access to data to only authorized personnel.
3. Data backup: Backing up data regularly to protect against data loss.
4. Data disposal: Disposing of data securely when no longer needed.
5. Data monitoring: Monitoring data access and usage to detect unauthorized access.
6. Data security: Implementing security measures to protect data from unauthorized access.
Rules Of Data Protection
1. Keep personal data secure: Ensure that personal data is stored securely and is only accessed by authorized personnel.
2. Collect only necessary data: Only collect the data that is necessary for the purpose for which it is being used.
3. Process data lawfully: Ensure that data is used in a lawful manner and in accordance with relevant legislation.
4. Provide data accuracy: Ensure that personal data is accurate and up-to-date.
Respond To Data Breach In Workplace
The first step in responding to a data breach in the workplace is to assess the scope and severity of the breach. This includes identifying the source of the breach, the type of data that was compromised, and the potential impact of the breach. Once the scope and severity of the breach have been determined, the next step is to take immediate action to contain and mitigate the breach, such as by shutting down systems, revoking access, and notifying affected individuals.
Way Companies Protect Themselves From Data Loss
Companies can protect themselves from data loss by implementing security measures such as encrypting data, using two-factor authentication, and regularly monitoring networks and systems for suspicious activity. Companies should also have a data breach response plan in place to ensure that any data breach is quickly identified and addressed. Additionally, companies should regularly review their security policies and procedures to ensure that they remain up to date and effective.
Importance To Maintain Data Security In Workplace
Data security is essential in all workplaces in order to protect confidential and sensitive information. Data security helps to protect the company’s reputation, customer data, and financial information. It also helps to protect against cyber attacks and data breaches, which can have serious consequences for the business. Maintaining data security is important to ensure the safety and privacy of customers, employees, and other stakeholders. Additionally, it is important to maintain data security in order to comply with industry regulations and laws.
Types Of Data Loss Prevention
1. Technical Controls: These include measures such as encryption, firewalls, and antivirus software to protect data from unauthorized access.
2. Administrative Controls: Policies and procedures such as access control and user authentication can be used to limit access to sensitive data.
3. Physical Controls: Physical security measures such as locks, cameras, and alarms can be used to protect data from theft or damage.
Steps Of Data Loss Prevention
1. Identification: Identifying the sensitive data and assessing the risk of potential data loss.
2. Prevention: Establishing and implementing policies and procedures to protect data from unauthorized access.
3. Detection: Monitoring data access and activity to detect any unauthorized access or data loss.
Most Common Way For Data To Get Leaked
The most common way for data to get leaked is through unsecured networks or devices. This can include leaving devices or computers connected to unsecured networks, not using strong passwords, or not encrypting data.
Risk Of Data Leakage
The risk of data leakage can be significant, as it can lead to the loss of confidential information, financial losses, and damage to a company’s reputation. Data leakage can also result in legal action, as there are laws in place to protect personal data.
Example Of Employee Data Breach
An example of an employee data breach is when an employee’s personal information, such as Social Security numbers, bank account numbers, or passwords, is accessed without authorization.
Breach Of Data In The Workplace
The most common breaches of data in the workplace include unauthorized access to confidential information, unauthorized sharing or selling of confidential information, and unauthorized use of confidential information for personal gain.
