
How to Extract a Password-Protected Zip File in Android?
Extracting password protected zip files in Android requires using dedicated extraction tools that can handle encryption algorithms and prompt for ...
Read More
Extracting password protected zip files in Android requires using dedicated extraction tools that can handle encryption algorithms and prompt for ...
Read More
Extracting pages from password protected PDFs is possible with the right tools and proper authorization. It allows for targeted editing ...
Read More
To connect to a password-protected WiFi network: Identify the desired network in your device’s WiFi settings. Enter the correct password ...
Read More
To compress files with password protection in Windows 7, select the files, right-click, choose “Send to,” then “Compressed (zipped) folder.” ...
Read More
In today’s digital age, data protection has become a top priority for individuals and organizations alike. Whether you are managing ...
Read More
Yes, you can unlock and edit locked Excel files by following specific procedures depending on the level of protection applied, ...
Read More
Yes, it’s possible to edit locked Word documents without a password using built-in Word tools or third-party software designed for ...
Read More
Unlocking or editing password protected PDFs is possible using various tools and methods. Identify the protection level, choose the right ...
Read More
You can remove Secure Folder Locked Notifications from your device by following simple steps outlined in this article. Secure Folder ...
Read More
To combine locked PDF files, use dedicated software like Adobe Acrobat, PDFsam, or Nitro Pro, which offer encryption options and ...
Read More
To check if a PDF is password protected, you can look for visual indicators like a lock icon or prompts ...
Read More
Unlocking Access: Editing Password Protected Word Documents offers a comprehensive guide on navigating password protection, utilizing recovery tools, and addressing ...
Read More
Factory resetting a password-protected laptop erases all data and settings, providing a fresh start. Prepare by backing up data, disconnecting ...
Read More
To factory reset a locked iPhone without an Apple ID password use the methods such as using iTunes or utilizing ...
Read More
Changing your lock password on the iPhone is a vital step in enhancing your device’s security. Follow the simple steps ...
Read More
To change the lock password on your iPad, go to Settings, then select Face ID & Passcode or Touch ID ...
Read More
To change the password for a locked folder, access the folder’s settings or security options, locate the password change feature, ...
Read More
To lock a folder on Windows 11, you can utilize built-in features like encryption and password protection or opt for ...
Read More
To download password protected PDFs, first, ensure you have the necessary permissions. Identify the source, obtain the password if required, ...
Read More
To download password protected Vimeo videos, you need proper authorization and the right tools. Understand the legal implications and follow ...
Read More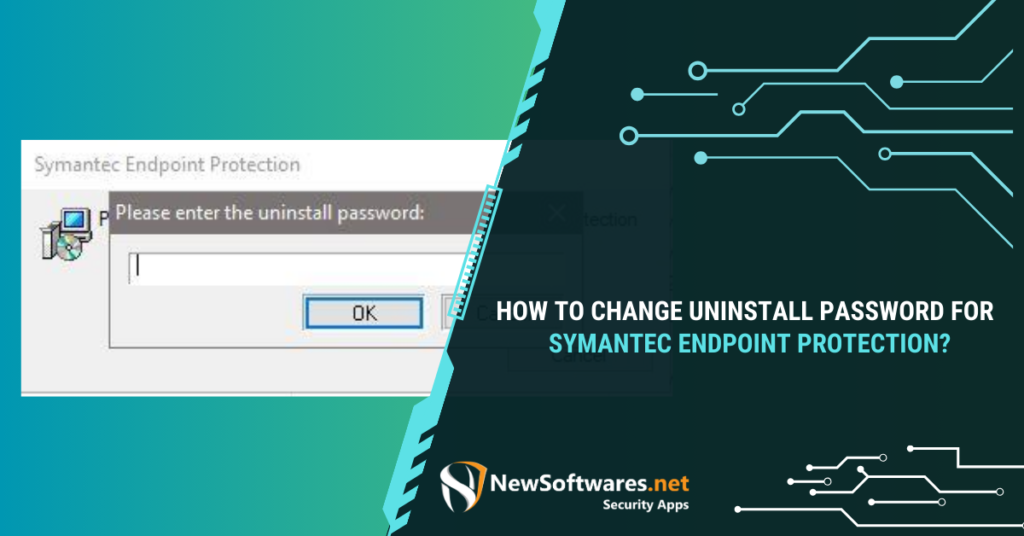
Changing the uninstall password for Symantec Endpoint Protection is crucial for maintaining system security. Uninstall passwords prevent unauthorized individuals from ...
Read More
Changing the password on a locked computer is achievable by following specific procedures tailored to your operating system. This task ...
Read More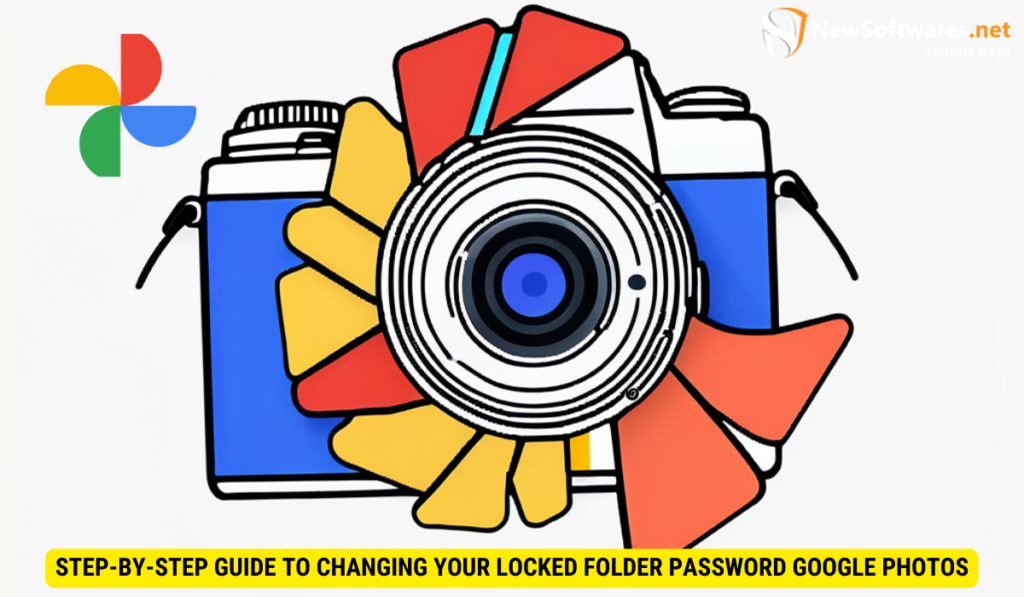
To change the password for a Locked Folder in Google Photos, first access your Google Photos account. Navigate to the ...
Read More
To download locked files from Google Drive, identify the files, request access from the owner if needed, or use Google’s ...
Read More
Learn about downloading password protected PDF files, including why they’re used, legal considerations, tools for downloading, safety tips, and file ...
Read More
Yes, password protected videos can be unlocked using various methods and techniques, but it’s important to consider legal and ethical ...
Read More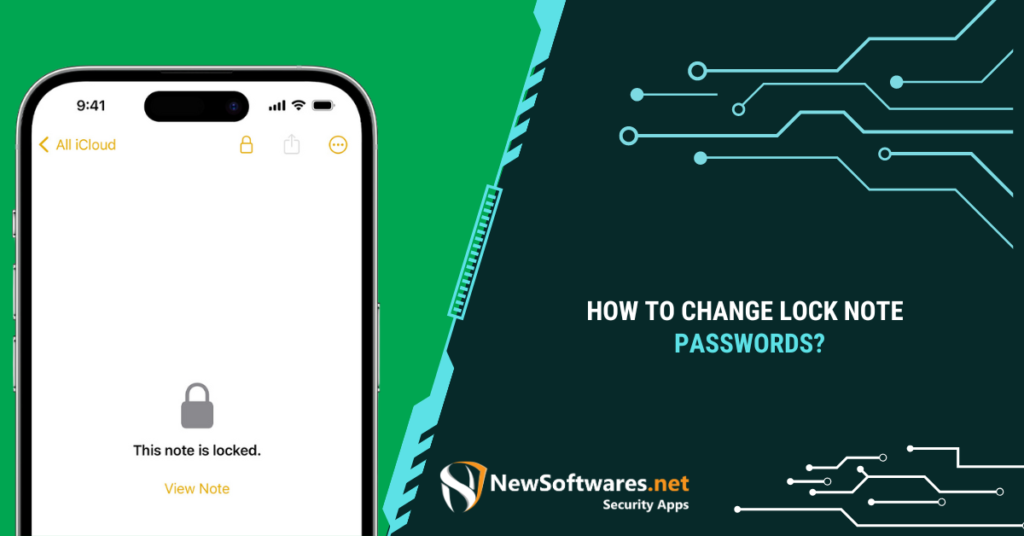
Regularly changing your Lock Note password is crucial for maintaining the security of your sensitive notes. By regularly updating your ...
Read More
To change your Google Smart Lock password, navigate to your Google account settings and select the “Security” tab. From there, ...
Read More
To change your Apple lock password, you can do so on your iPhone, iPad, or Mac. On your iOS device, ...
Read More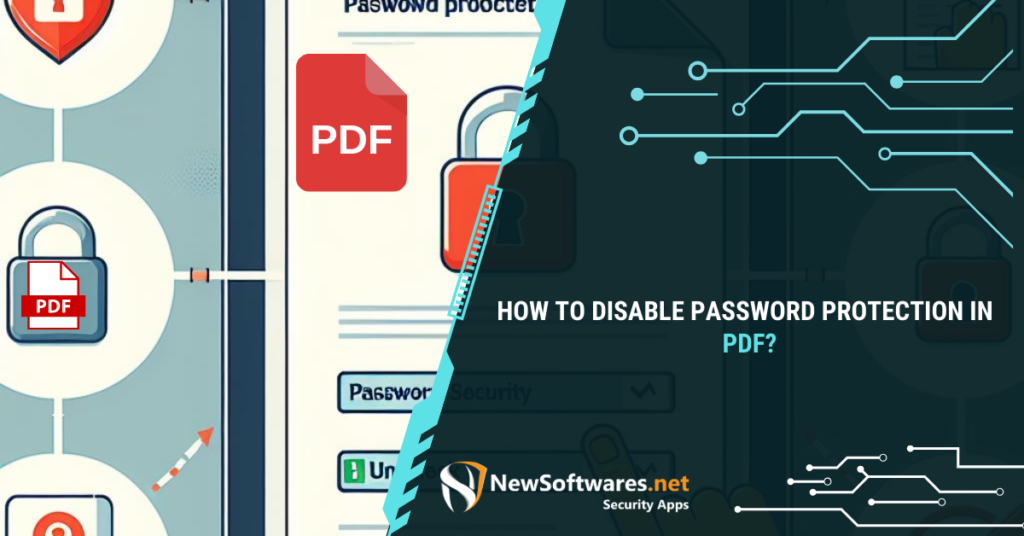
Disabling password protection in PDF files is possible but requires careful consideration of legal and ethical implications. It involves using ...
Read More
Disabling iPhone password locks can provide convenience but poses security risks. It’s crucial to weigh the trade-off between convenience and ...
Read More
Disabling drive lock passwords involves a systematic approach that includes ensuring alternative security measures are in place. Following this, the ...
Read More
Attempting to bypass privacy protection passwords without lawful authority is illegal and unethical. However, there may be certain circumstances where ...
Read More
To change password-protected Excel files, open the file, click on the “File” tab, select “Protect Workbook,” choose “Encrypt with Password,” ...
Read More
In today’s digital age, internet safety has become a paramount concern, especially when it comes to protecting our children from ...
Read More
Deleting locked notes on an iPhone without a password can be challenging. However, there are techniques you can try, such ...
Read More
To delete locked files on a Mac, use Finder to adjust file permissions or utilize Terminal commands. Prioritize backing up ...
Read More
To decrypt a password-protected zip file, gather necessary details, use decryption tools like John the Ripper or Hashcat, and ensure ...
Read More
A variety of tools and software are available to aid in bypassing password-protected websites. Understanding their capabilities and limitations is ...
Read More
To break password-protected RAR files, follow these steps: Use reputable RAR password cracker software, assess password complexity, and let the ...
Read More
If you find yourself unable to access a password-protected Word document, there are steps you can take to resolve the ...
Read More
Package-lock.json files are crucial for project security, ensuring consistency and stability by specifying dependency versions. In today’s digital landscape, security ...
Read More
Creating password protected files in Android programmatically involves understanding the importance of file security, grasping the basics of Android programming ...
Read More
Learn to safeguard sensitive data by creating password protected PDFs from Word docs. Explore encryption basics, conversion steps, and effective ...
Read More
To access password-protected WiFi, seek permission, use public hotspots, or employ legal methods. In today’s digital age, staying connected is ...
Read MoreAccessing a locked folder in Google Photos involves setting it up, managing its contents, and using authentication methods. Follow these ...
Read More
To access locked files on Windows 10, you can use built-in tools like Resource Monitor or third-party software solutions like ...
Read More
Learn how to enhance file security in Windows 10 by creating password protected zip files. Safeguard your sensitive information with ...
Read More
Decrypting password-protected PDF files is a crucial skill when it comes to accessing confidential information. By understanding the basics of ...
Read More
Customizing password protected pages in WordPress enhances website security, controls content access, and requires regular maintenance for optimum protection. In ...
Read More

Data Security and Encryption Softwares.