Importance of Phone Data Encryption
In today’s digital age, our phones contain many sensitive information, including personal photos, financial information, and private messages. With the increasing risk of data breaches and cyber attacks, it is crucial to take measures to protect our phone data from unauthorized access. Encryption is one of the most effective ways to secure your phone data. Encryption is converting your data into a code that can only be deciphered with the correct key or password.
How to Encrypt Phone Data
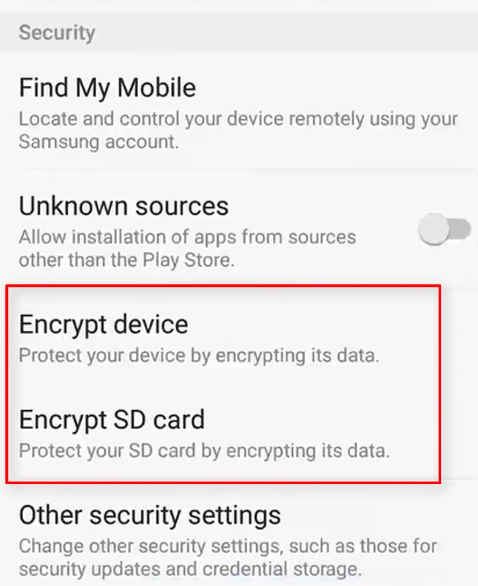
Encrypting your phone data is an important step in protecting your sensitive information. Here are the steps to encrypt your phone data:
1. Go to your phone’s settings.
2. Look for the “Security” or “Privacy” option.
3. Find the “Encryption” option and select it.
4. Follow the instructions on the screen to set a password or PIN.
5. Wait for the encryption process to complete. This may take several minutes, depending on the amount of data on your phone
Encryption on iOS devices
-
- Enabling encryption on iPhones
- Using iCloud Keychain
- Using third-party apps
Encryption on Android devices
- Enabling encryption on Android phones
- Using Google Drive
- Using third-party apps
Best Practices for Phone Data Encryption
- Creating strong passwords
- Two-factor authentication
- Updating software regularly
- Disabling automatic backups
- Disabling unnecessary features
Encryption for Specific Phone Data
Phone data encryption is the process of converting data into a secret code to prevent unauthorized access. Encryption is particularly important for mobile devices as they are easily lost or stolen. Both iOS and Android devices offer various encryption options.
On iOS devices, encryption can be enabled by setting a passcode and activating the “Data Protection” feature.
Encrypting Text Messages
To encrypt text messages, there are several options available. One option is to use a third-party messaging app that offers end-to-end encryption, such as Signal or WhatsApp. Another option is to use the built-in encryption feature on your device, such as iMessage on iOS devices. It’s important to note that both the sender and recipient must have the same encryption method enabled for the messages to be encrypted.
Encrypting Photos And Videos
To encrypt photos and videos, you can use a file encryption app such as VeraCrypt or AxCrypt. These apps allow you to create encrypted containers where you can store your sensitive files. You can also use the built-in encryption feature on your device, such as FileVault on Mac or BitLocker on Windows. It’s important to use a strong password or passphrase to secure your encrypted files.
Encrypting Files And Documents
To encrypt files and documents, you can use a file encryption app such as VeraCrypt, AxCrypt, or 7-Zip. These apps allow you to encrypt individual files or entire folders. You can also use the built-in encryption feature on your device, such as BitLocker on Windows or FileVault on Mac. It’s important to use a strong password or passphrase to secure your encrypted files, and to keep a backup of the password in a secure location.
Common Encryption Mistakes to Avoid
- Not encrypting all sensitive data
- Using weak passwords
- Not updating software
- Not backing up encrypted data
How to Resolve Encryption Issues
If you encounter encryption issues, there are a few steps you can take to resolve them:
1. Check that you are using the correct password or passphrase to access your encrypted files. If you have forgotten your password, see if you have a backup of it in a secure location.
2. Make sure that your encryption software is up-to-date. Check for any available updates and install them if necessary.
3. If you are still unable to access your encrypted data, try decrypting it using your encryption software’s decryption feature. This will require you to enter your password or passphrase again.
4. If decryption does not work, you may need to seek the assistance of a professional data recovery service. These services specialize in recovering data from corrupted, damaged, or encrypted storage devices.
5. To prevent encryption issues in the future, make sure to regularly back up your encrypted data to a secure location.
Decrypting Encrypted Data
To decrypt encrypted data, you can follow the steps below:
1. Open your encryption software and locate the encrypted file or folder that you want to decrypt.
2. Select the file or folder and click on the “Decrypt” or “Decrypt File” option.
3. You will be prompted to enter your password or passphrase to decrypt the file or folder.
4. Once you enter the correct password or passphrase, the file or folder will be decrypted and you will be able to access its contents.
Recovering Lost Encrypted Data
To recover lost encrypted data, you can try the following methods:
1. Check your backups: If you have a backup of the encrypted data, you can restore it from there.
2. Use recovery software: There are many data recovery software programs available that can help you recover lost or deleted files, including encrypted ones. You can try using one of these programs to recover your lost data.
3. Contact a professional data recovery service: If you are unable to recover your lost data using the above methods.
Data Recovery Services
There specialized companies that can help you recover lost or encrypted data. They have the expertise and tools necessary to recover data from damaged or corrupted devices. You can search online for data recovery services in your area and choose one that has good reviews and a proven track record of success. Keep in mind that professional data recovery services can be expensive, so be sure to weigh the cost against the value of the data you are trying to recover.
Alternatives to Phone Data Encryption
- Virtual Private Networks (VPNs)
- Secure messaging apps
- Cloud storage options
Encryption in the Workplace
Encryption in the workplace is a crucial aspect of data security. It involves the use of encryption software to protect sensitive data from unauthorized access or theft. Encryption can be applied to various forms of data, including emails, files, and databases. There are several encryption software options available that can be used in the workplace, including BitLocker, Symantec Endpoint Encryption, and VeraCrypt. It is important to choose encryption software that is compatible with your system and meets your organization’s security needs.
Employer Responsibilities
Employers have a responsibility to ensure the security and privacy of their employees’ and customers’ sensitive data. This includes implementing encryption software to protect data from unauthorized access or theft. Employers should also provide training to employees on how to properly use encryption software and follow security protocols. Additionally, employers should regularly review and update their encryption software to ensure it is up-to-date and effective in protecting sensitive data.
Employee Responsibilities
Employees also have a responsibility to protect sensitive data by following security protocols and using encryption software properly. This includes using strong passwords and not sharing them with others, avoiding using public Wi-Fi networks to access sensitive data, and reporting any security breaches or suspicious activity to their employer immediately. Employees should also attend any training provided by their employer on data security and encryption software usage. By taking these steps, employees can help ensure the security and privacy of sensitive data.
Best Practices For Workplace Encryption
Encrypting sensitive data is an important step in protecting it from unauthorized access. Here are some best practices for workplace encryption:
1. Use strong encryption algorithms: Ensure that the encryption software being used employs strong encryption algorithms that are difficult to crack.
2. Use strong passwords: Use strong, unique passwords for encryption keys and avoid sharing them with others.
3. Keep encryption software up to date: Keep encryption software updated with the latest security patches to address any vulnerabilities.
Privacy Concerns Related To Encryption
Encryption is an important tool for protecting sensitive information and maintaining privacy in the workplace. However, some people have concerns about the potential misuse of encryption, such as by criminals or terrorists. One argument against encryption is that it can be used to hide illegal activities, such as drug trafficking or terrorism. However, it is important to note that encryption is not inherently illegal, and many legitimate businesses and individuals use encryption to protect their sensitive information.
Ethical Implications of Encryption
Encryption has several ethical implications, both positive and negative. On the positive side, encryption can help protect sensitive information and maintain privacy, which is a fundamental right of individuals. This can be particularly important for vulnerable populations, such as political dissidents, journalists, and whistleblowers who may face persecution or retaliation for their activities. On the negative side, encryption can also be used to conceal illegal activities, such as terrorism, money laundering, or child pornography.
Future of Encryption
The future of encryption is uncertain, as governments and law enforcement agencies continue to push for backdoors and weakened encryption standards in the name of national security. However, many experts argue that any such measures would ultimately weaken the security of all users and make everyone more vulnerable to cyber-attacks and data breaches. It remains to be seen how this debate will play out, but encryption will continue to play a crucial role in protecting sensitive information and preserving privacy in the digital age.
Conclusion
In conclusion, encryption is a vital tool in safeguarding sensitive information and preserving privacy in the digital age. While there are ongoing debates about the balance between national security and individual privacy, it is important to recognize that any attempts to weaken encryption standards could have far-reaching consequences for all users. As such, it is essential to continue to support and prioritize strong encryption practices to ensure the security and privacy of our digital lives.
FAQs
What is phone data encryption?
Phone data encryption is converting the data stored on a phone into a coded format that can only be accessed with a specific key or password. This helps to protect sensitive information such as personal messages, financial data, and login credentials from unauthorized access. Encryption is an important security measure that helps to safeguard the privacy of individuals in the digital age.
How does phone data encryption work?
Phone data encryption works by using complex algorithms to scramble the data stored on a phone. This scrambled data can only be read with a specific key or password. When the phone is locked, the encryption key is stored in a secure area of the phone’s memory, making it difficult for hackers to access the data even if they gain physical access to the device. When the phone is unlocked with the correct password or key, the data is decrypted and can be accessed by the user. This process helps to ensure
What should I do if I have encryption issues?
If you are experiencing encryption issues on your phone, the first step is to try restarting the device. If that does not resolve the issue, you may need to reset the encryption settings or contact the manufacturer for assistance. It is important to remember that encryption is a complex process and any changes made to the settings can have significant consequences for the security of your data. It is always best to seek professional advice before making any changes to encryption settings.
Can encrypted data be decrypted?
Encrypted data can be decrypted, but it requires the correct decryption key or password. Without the correct key or password, the encrypted data will remain unreadable and inaccessible. It is important to keep your encryption key or password secure and not share it with anyone who is not authorized to access your data. Additionally, it is important to use strong encryption methods to ensure that your data is as secure as possible.
Are there alternatives to phone data encryption?

Yes, there are alternatives to phone data encryption. One alternative is to use a virtual private network (VPN) to encrypt your internet traffic and protect your online privacy. Another alternative is to use secure messaging apps that offer end-to-end encryption, such as Signal or WhatsApp. Additionally, you can use strong passwords and two-factor authentication to protect your accounts and data. It is important to use a combination of these methods to ensure that your data is as secure as possible.
What legal considerations are there for phone data encryption?
There are several legal considerations for phone data encryption. In some countries, the use of encryption technologies may be restricted or even illegal. Therefore, it is important to research the laws and regulations in your country or region before using encryption on your phone. Additionally, if you are using encryption to protect sensitive information, such as medical records or financial data, you may be subject to additional legal requirements, such as complying with data protection laws or industry-specific regulations.
What are the ethical considerations related to encryption?
There are several ethical considerations related to encryption. Firstly, there is the question of privacy. Encryption allows individuals to protect their personal information from unauthorized access, which is a fundamental right. However, some argue that encryption can also be used to conceal illegal activities or to protect criminals from being caught.
Secondly, there is the issue of national security. Governments may argue that they need to access encrypted information to protect their citizens from terrorism or other threats.
What does the future of encryption look like?
The future of encryption is likely to be shaped by ongoing debates and discussions around privacy, security, and law enforcement. While encryption is a powerful tool for protecting personal information and ensuring privacy, it can also be used by criminals to hide their activities. As a result, there may be ongoing efforts by governments and law enforcement agencies to regulate or limit the use of encryption. At the same time, there will likely be continued innovation in the development of new encryption technologies that are even more secure and difficult to crack.
