Introduction
Wireshark is a powerful network protocol analyzer that allows you to capture and analyze network traffic in real time. One of the most important features of Wireshark is the ability to identify encrypted traffic. Encrypted traffic is data that has been scrambled to prevent unauthorized access. In this guide, we will show you how to tell if data is encrypted on Wireshark.
Understanding Data Encryption On Wireshark
Before we dive into how to tell if data is encrypted on Wireshark, it’s important to understand how data encryption works. Encryption is the process of converting plain text into cipher text that is unreadable without a key. The key is used to decrypt the cipher text back into plain text. Several encryption algorithms are commonly used, such as AES, DES, and RSA. These algorithms use different methods to encrypt and decrypt data.
When data is encrypted, it appears as random characters and symbols in the network traffic. This makes it difficult for anyone who intercepts the traffic to read the data without the key.
Wireshark: An Overview
Wireshark is a network protocol analyzer that allows users to capture and analyze network traffic in real time. It is an open-source tool that is used for troubleshooting network issues, analyzing network performance, and identifying security threats. Wireshark supports a wide range of protocols and can be used on multiple platforms, including Windows, Linux, and macOS. Its user-friendly interface makes it easy to use, and it provides detailed information about network traffic, including packet headers, payloads, and protocol-specific information. Wireshark is a powerful tool that is used by network administrators, security professionals, and developers to gain insight into network behavior and troubleshoot issues.
How To Tell If Data Is Encrypted On Wireshark?
Now that we understand how data encryption works, let’s take a look at how to tell if data is encrypted on Wireshark.
1. Look for the “Encrypted” Label
When you capture network traffic on Wireshark, you will see a list of packets in the main window. If a packet contains encrypted data, you will see an “Encrypted” label in the “Info” column. This label indicates that the data in the packet has been encrypted.
2. Look for the Protocol Used
Another way to determine if data is encrypted on Wireshark is to look at the protocol used. Some protocols, such as HTTPS, use encryption by default. If you see HTTPS in the protocol column, you can assume that the data is encrypted.
3. Look for the Cipher Suite
If the protocol used is SSL or TLS, you can look for the cipher suite used to encrypt the data. Wireshark will display the cipher suite in the “Secure Sockets Layer” or “Transport Layer Security” sections of the packet details. If the cipher suite is listed as “NULL,” the data is not encrypted.
4. Look for the Key Exchange
If the protocol used is SSL or TLS, you can also look for the key exchange used to establish the encryption. Wireshark will display the key exchange in the “Secure Sockets Layer” or “Transport Layer Security” sections of the packet details. If the key exchange is listed as “NULL,” the data is not encrypted.
How To See Encrypted Data In Wireshark?
Wireshark is not able to decrypt encrypted data as it requires the encryption key to do so. However, you can still see the encrypted data in Wireshark. To do this, you will need to have the encryption key or the pre-shared key (PSK) used to encrypt the data. Once you have the key, you can go to the “Edit” menu, select “Preferences”, and then select “Protocols”. From there, you can select the protocol used to encrypt the data and enter the encryption key or PSK.
After entering the key, Wireshark will be able to decrypt the data and display it in plain text. If you do not have the encryption key or PSK, you will not be able to see the encrypted data in Wireshark.
Capturing Network Traffic With Wireshark
To capture network traffic with Wireshark, you can start by selecting the network interface you want to capture traffic on. Then, click on the “Capture” button to start the capture process. Once the capture is initiated, you can filter the traffic using various filter expressions to narrow down the results. You can also save the capture file for later analysis.
During the capture process, Wireshark will display real-time statistics about the captured traffic, including the number of packets captured, the amount of data captured, and the capture rate.
After the capture is complete, you can analyze the captured traffic using various tools and features provided by Wireshark, such as the packet details view, the packet list view, and the protocol hierarchy view. These tools allow you to drill down into the captured traffic and analyze it in detail.
Identifying Encrypted Data In Wireshark
To identify encrypted data in Wireshark, you can look for packets that use encryption protocols such as SSL/TLS, SSH, or IPsec. These protocols encrypt the data payload of the packets, making it unreadable to anyone who intercepts the traffic. To filter for encrypted traffic in Wireshark, you can use the display filter “SSL” or “TLS” for SSL/TLS traffic, “ssh” for SSH traffic, or “IPsec” for IPsec traffic. You can also use the “Follow SSL Stream” feature in Wireshark to view the decrypted data of an SSL/TLS session.
It’s important to note that while encrypted data may be more secure, it can also make it more difficult to analyze network traffic for troubleshooting or security purposes.
Decrypting SSL/TLS Traffic
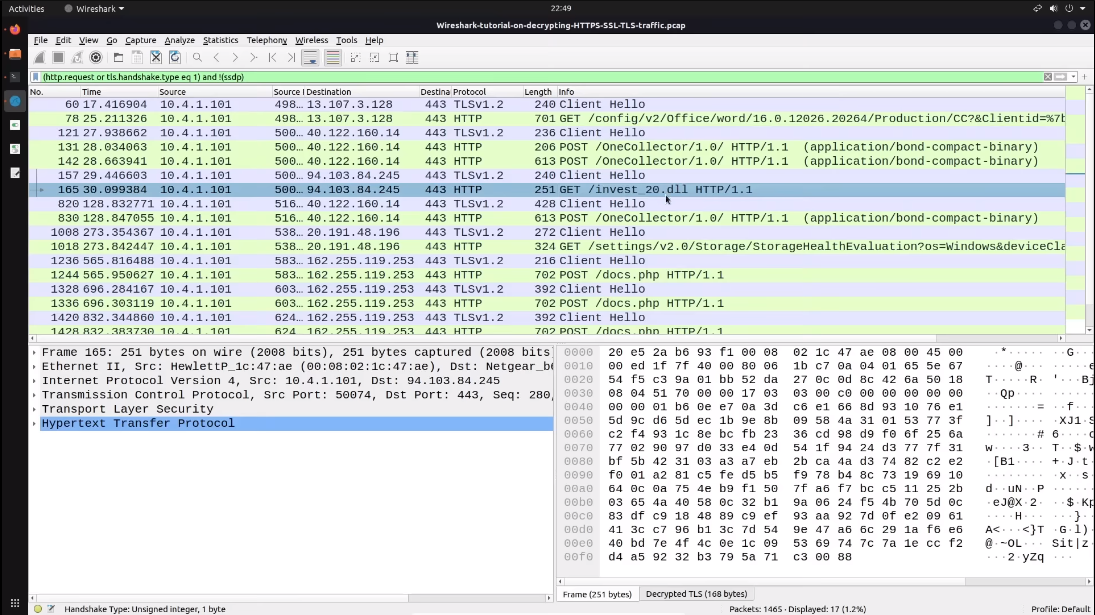
Decrypting SSL/TLS traffic can be a useful tool for analyzing network traffic, especially for troubleshooting or security purposes. However, it’s important to note that decrypting encrypted traffic without proper authorization can be illegal and unethical. To decrypt SSL/TLS traffic in Wireshark, you will need the private key used to encrypt the traffic. If you have access to the private key, you can configure Wireshark to use it to decrypt the traffic. This can be done by going to the “Edit” menu, selecting “Preferences”, and then navigating to the “Protocols” section. From there, select “SSL” or “TLS” and enter the path to the private key file.
Once the private key is configured, Wireshark will automatically decrypt SSL/TLS traffic that uses that key. This will allow you to view the decrypted data in the Wireshark capture, making it easier to analyze and troubleshoot network issues.
It’s important to note that decrypting SSL/TLS traffic should only be done with proper authorization and for legitimate purposes. Decrypting traffic without authorization can be illegal and unethical, and can also compromise the security of the network.
Analyzing Encrypted Traffic Without Decryption
If you don’t have the proper authorization to decrypt SSL/TLS traffic, there are still ways to analyze the encrypted traffic. One option is to look at the metadata of the traffic, such as the source and destination IP addresses, ports, and protocol. This can give you some insight into the nature of the traffic and the endpoints involved. Another option is to use statistical analysis techniques to identify patterns and anomalies in the encrypted traffic. For example, you can look for patterns in the size and timing of packets, or use machine learning algorithms to identify unusual behavior.
While these techniques may not give you the same level of insight as decrypting the traffic, they can still be useful for troubleshooting and identifying potential security threats. It’s important to remember, however, that analyzing encrypted traffic without decryption is not always reliable and may not provide a complete picture of what’s happening on the network.
Additional Techniques For Identifying Encryption
In addition to the techniques mentioned above, there are a few other ways to identify encryption on a network. One way is to look for traffic patterns that are commonly associated with encrypted traffic. For example, HTTPS traffic typically uses TCP port 443, while VPN traffic may use UDP port 500 or 4500. Another technique is to look for the use of encryption protocols or algorithms in network traffic. Common encryption protocols include SSL/TLS, IPsec, and SSH. These protocols can often be identified by examining the headers of network packets.
Finally, network administrators can use specialized tools and software to detect and analyze encrypted traffic. These tools may include network analyzers, intrusion detection systems, and security information and event management (SIEM) systems.
Overall, identifying encrypted traffic on a network can be a challenging task. However, by using a combination of techniques and tools, network administrators can gain valuable insights into the security and performance of their networks.
Common Challenges And Limitations
When it comes to identifying encrypted traffic on a network, there are several common challenges and limitations that network administrators may face. Some of these challenges include:
1. Limited visibility: Encrypted traffic is designed to be private and secure, which means that it can be difficult to monitor and analyze.
2. Performance impact: Decrypting and analyzing encrypted traffic can be resource-intensive and may impact network performance.
3. False positives: Encrypted traffic can be used for both legitimate and malicious purposes, which means that identifying potential threats can be challenging.
4. Encrypted tunneling: Some applications use encrypted tunneling, which can make it difficult to identify the specific type of traffic being transmitted.
5. Compliance requirements: In some cases, network administrators may be required to monitor and analyze encrypted traffic for compliance purposes, which can be a complex and time-consuming process.
Despite these challenges, network administrators need to have a comprehensive understanding of the encrypted traffic on their networks to ensure the security and performance of their systems. By using a combination of techniques and tools, network administrators can overcome these limitations and gain valuable insights into their network traffic.
Ensuring Data Security In Encrypted Networks
Ensuring data security in encrypted networks is a critical task for network administrators. Encrypted traffic can be difficult to monitor and analyze, making it challenging to detect potential security threats. However, several techniques and tools can be used to ensure the security of encrypted data. One approach is to use SSL/TLS inspection, which involves intercepting and decrypting SSL/TLS traffic for inspection. This technique allows administrators to analyze the contents of encrypted traffic and detect any potential security threats. However, SSL/TLS inspection can be complex and may require additional hardware and software.
Another approach is to use network behavior analysis (NBA) tools, which can monitor network traffic and detect anomalies in behavior. NBA tools can detect unusual traffic patterns, such as a sudden increase in traffic or traffic from an unknown source. This can help administrators identify potential security threats and take appropriate action.
In addition to these techniques, network administrators can also use intrusion detection and prevention systems (IDPS) to detect and prevent security threats. IDPS can monitor network traffic and detect potential security threats, such as malware or unauthorized access attempts. IDPS can also take proactive measures to prevent these threats, such as blocking traffic from suspicious sources.
Conclusion
In conclusion, detecting and analyzing encrypted traffic is crucial in ensuring the security and privacy of sensitive information. While encryption can provide a layer of protection, it can also be used by malicious actors to conceal their activities. By implementing the best practices outlined above, organizations can better detect and analyze encrypted traffic, identify potential threats, and take appropriate measures to mitigate them. It is important to stay vigilant and proactive in the face of evolving security threats and to continue to adapt and improve encryption policies and practices.
Encouraging data security practices is crucial in protecting sensitive information and preventing data breaches. Organizations should educate their employees on the importance of proper data handling and provide training on data security best practices. This includes using strong passwords, avoiding phishing scams, and securely storing and transmitting data. Additionally, implementing security measures such as firewalls, intrusion detection systems, and access controls can help prevent unauthorized access to sensitive data. Regularly reviewing and updating security policies and procedures can also ensure that the organization is prepared to handle any security incidents that may arise. Wireshark is a powerful tool that can be used for network analysis and troubleshooting. However, it is important to keep in mind that encryption can render Wireshark ineffective in capturing and analyzing network traffic. As such, organizations must implement strong encryption protocols to protect their sensitive data. Additionally, organizations should also adopt a comprehensive approach to data security, which includes implementing firewalls, intrusion detection systems, and access controls, as well as regularly reviewing and updating security policies and procedures. By promoting a culture of data security and implementing robust security measures, organizations can effectively safeguard their sensitive information and prevent data breaches.
Frequently Asked Questions (FAQs)
A. How Does Wireshark Capture Encrypted Data?
Wireshark cannot capture encrypted data as it is designed to capture and analyze network traffic. Encrypted data is protected by encryption algorithms, which makes it unreadable to anyone without the proper decryption key. However, Wireshark can capture the metadata associated with encrypted traffic, such as the source and destination IP addresses and ports, which can provide valuable information for network analysis and troubleshooting. To capture encrypted data, you would need to use a tool specifically designed for decrypting and analyzing encrypted traffic, such as SSL decryption software.
B. Can Wireshark Decrypt All Types Of Encrypted Traffic?
No, Wireshark cannot decrypt all types of encrypted traffic. It can only capture the metadata associated with encrypted traffic, such as the source and destination IP addresses and ports. To decrypt encrypted traffic, you would need to use a tool specifically designed for decrypting and analyzing that type of encryption, such as SSL decryption software. Additionally, attempting to decrypt encrypted traffic without proper authorization may be illegal and unethical.
C. What Are Some Indicators Of Encrypted Traffic In Wireshark?
There are a few indicators that can suggest the presence of encrypted traffic in Wireshark:
- The protocol column may display “TLS” or “SSL” instead of the usual protocol name.
- The packet details may show an “Encrypted Handshake Message” or a similar message.
- The packet length may be larger than expected, as encrypted traffic often includes additional padding to obscure the actual data size.
- The packet payload may appear as a series of seemingly random characters, rather than recognizable text or data.
However, it’s important to note that these indicators do not necessarily mean that the traffic is malicious or illegal. Encrypted traffic is commonly used to protect sensitive information, such as login credentials or financial transactions, from eavesdropping or interception.
D. How Can I Identify The Encryption Algorithm Used?
Identifying the encryption algorithm used in encrypted traffic can be a challenging task. However, there are a few methods that can be used to identify the encryption algorithm:
- Check the protocol: Some encryption algorithms are associated with specific protocols, such as SSL/TLS or SSH. By identifying the protocol used, you may be able to narrow down the possible encryption algorithms.
- Look for metadata: Some encrypted traffic may contain metadata that can provide clues about the encryption algorithm used. For example, the SSL/TLS handshake process includes information about the encryption algorithm and key length used.
- Analyze the packet size: Some encryption algorithms add additional padding to obscure the actual data size. By analyzing the packet size, you may be able to identify the encryption algorithm used.
- Use decryption tools: There are a variety of decryption tools available that can help identify the encryption algorithm used. These tools work by analyzing the encrypted traffic and attempting to decrypt it using various algorithms until a match is found.
It’s important to note that identifying the encryption algorithm used may not always be possible, especially if the traffic is well-encrypted and the encryption algorithm is not known.
E. Is It Possible To Analyze Encrypted Data Without Decryption?
It is possible to analyze encrypted data without decryption, but the analysis would be limited. Encrypted data can still provide information about the size and frequency of the data, as well as the source and destination of the traffic. However, the actual contents of the data would remain hidden unless the encryption is decrypted. Additionally, analyzing encrypted data without authorization may violate privacy laws and ethical considerations. It is important to obtain proper authorization and follow legal and ethical guidelines when analyzing encrypted data.
F. What Challenges Are Faced When Analyzing Encrypted Traffic?
Analyzing encrypted traffic can be challenging because the contents of the data are hidden and cannot be easily accessed without decryption. This means that important information about the data, such as its size and frequency, may be difficult to obtain. Additionally, analyzing encrypted data without proper authorization may violate privacy laws and ethical considerations. Decrypting encrypted data can also be time-consuming and resource-intensive, requiring specialized tools and expertise. Overall, the challenges of analyzing encrypted traffic highlight the importance of following proper legal and ethical guidelines when conducting such analysis.
G. How Can I Ensure Data Security In Encrypted Networks?
There are several steps you can take to ensure data security in encrypted networks:
- Use strong encryption algorithms: Ensure that your encryption algorithms are strong and up-to-date. Avoid using weak encryption methods that can be easily decrypted by attackers.
- Use secure key management: Properly manage your encryption keys to prevent unauthorized access. Use strong passwords and multi-factor authentication to protect your keys.
- Implement access controls: Limit access to encrypted data to authorized personnel only. Use role-based access control to ensure that only those who need access to the data can view it.
- Monitor network traffic: Regularly monitor your network traffic to detect any anomalies or suspicious activity. Use intrusion detection systems and firewalls to prevent unauthorized access.
- Regularly update software and hardware: Keep your software and hardware up-to-date with the latest security patches and updates to prevent vulnerabilities from being exploited.
By following these steps, you can help ensure the security of your encrypted network and protect your sensitive data from unauthorized access.
H. Are There Any Best Practices For Encryption Implementation?
Yes, there are several best practices for encryption implementation. Here are a few:
- Use strong encryption algorithms: Use encryption algorithms that are widely accepted and considered to be strong, such as AES or RSA.
- Use long and complex encryption keys: The longer and more complex the encryption key, the more difficult it is to crack. Aim for keys that are at least 128 bits long.
- Implement end-to-end encryption: End-to-end encryption ensures that data is encrypted at the source and can only be decrypted by the intended recipient.
- Use two-factor authentication: Two-factor authentication adds an extra layer of security by requiring users to provide two forms of authentication, such as a password and a fingerprint.
- Regularly review and update encryption policies: Keep your encryption policies up-to-date to ensure that they align with the latest security standards and best practices.
By following these best practices, you can help ensure that your encrypted data remains secure and protected from unauthorized access.
