File encryption is a crucial method for safeguarding sensitive data in today’s digital landscape. It involves converting file contents into a code that can only be decrypted with the correct key, ensuring data remains confidential even if unauthorized parties gain access. Common methods include symmetric, asymmetric, and hybrid encryption, each with its strengths. Key terms like public and private keys, passphrases, and key length are fundamental. Various encryption algorithms, such as AES and RSA, offer different levels of security.
What is File Encryption?

File encryption is the process of converting the contents of a file into a code that can only be deciphered by individuals or systems possessing the correct decryption key. This method ensures that even if unauthorized parties gain access to your files, they will be unable to decipher the information without the necessary credentials.
Importance of File Encryption
The primary importance of file encryption is its ability to protect sensitive data. Whether it’s personal financial records, confidential business documents, or sensitive personal information, encrypting files ensures that even if unauthorized individuals gain access to your device or network, they cannot decipher the content without the encryption key.
Secure Communication
File encryption plays a pivotal role in ensuring secure messaging, email exchanges, and voice calls. It prevents eavesdropping and data interception during transmission, making it an essential tool for businesses, governments, and individuals alike. Secure communication is not only vital for privacy but also for protecting intellectual property and trade secrets.
File encryption safeguards these files, making it extremely challenging for cybercriminals to gain access to confidential information. This is particularly critical for businesses that store financial records, customer data, and proprietary information.
File encryption ensures that even employees with access to sensitive data cannot view or steal information without the necessary decryption keys, reducing the risk of insider threats.
Common File Encryption Methods:
Symmetric Encryption
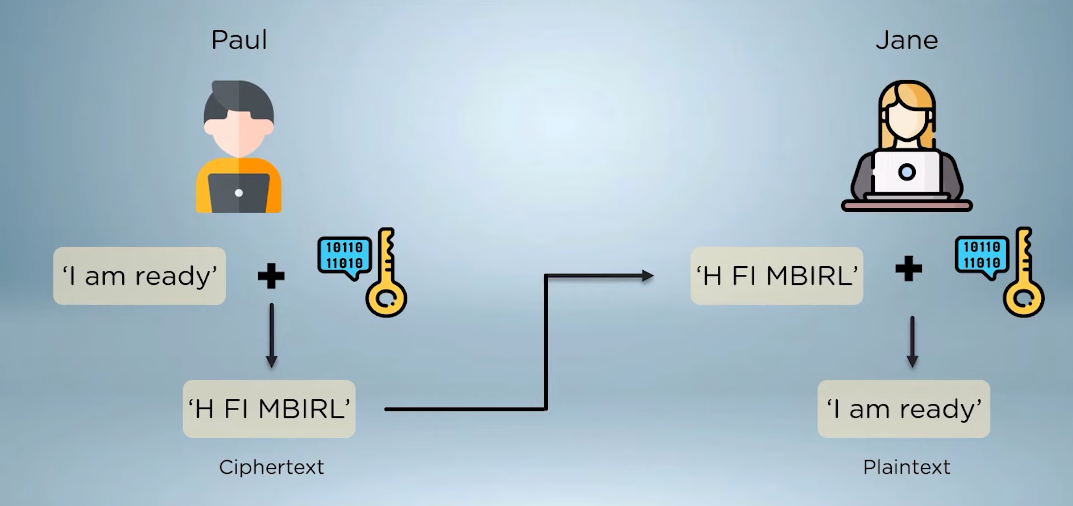
Symmetric encryption, also known as private-key encryption, is a method where the same key is used for both encryption and decryption. This means that whoever encrypts the file can also decrypt it. While it’s fast and efficient, the challenge lies in securely sharing the encryption key between the sender and receiver.
Asymmetric Encryption
Asymmetric encryption, also referred to as public-key encryption, utilizes two different keys: a public key for encryption and a private key for decryption. This method ensures better security since the public key can be freely shared, but the private key must remain confidential. Asymmetric encryption is often used for secure communication and digital signatures.
Hybrid Encryption
Hybrid encryption combines the strengths of both symmetric and asymmetric encryption. In this method, a symmetric key is used to encrypt the actual data, while the recipient’s public key is used to encrypt and securely transfer the symmetric key. This approach strikes a balance between efficiency and security.
Encryption Key Terminologies:

Public Keys and Private Keys
In asymmetric encryption, public keys are used for encrypting data, while private keys are used for decryption. Public keys are openly shared, while private keys must be kept confidential. This duality ensures secure communication and data protection.
Passphrases and Passwords
Passphrases and passwords are strings of characters used to authenticate users and access encrypted files. Passphrases are generally longer and more complex than passwords, enhancing security. Users should choose strong passphrases and passwords and avoid sharing them.
Key Length and Strength
The strength of an encryption key depends on its length. Longer keys are exponentially more secure than shorter ones. For example, a 256-bit key is far stronger than a 128-bit key. Choosing an appropriate key length is crucial to protect your data effectively.
Encryption Algorithm
An encryption algorithm is a set of mathematical rules and operations used to transform data into an unreadable format. The choice of encryption algorithm impacts the security of the encryption process. Some well-known encryption algorithms include AES, RSA, and DES.
Cryptographic Hash Functions
Cryptographic hash functions are one-way mathematical functions that generate a fixed-size output (hash) based on input data. Hash functions are used in various encryption processes, including password storage and data integrity verification.
Salt
A salt is a random value added to data before it’s hashed or encrypted. Salting is commonly used in password storage to prevent attackers from using precomputed tables (rainbow tables) to crack passwords.
Initialization Vector (IV)
In symmetric encryption, an initialization vector is a random value used as an additional input to the encryption algorithm. The IV ensures that even if the same plaintext is encrypted multiple times, the ciphertext will be different, enhancing security.
Key Management
Key management refers to the secure generation, distribution, storage, and disposal of encryption keys. Effective key management is crucial for maintaining the security of encrypted data.
Digital Certificate
A digital certificate is a cryptographic document that verifies the identity of an entity, such as a website or an individual, in a secure manner. It is often used in public key infrastructure (PKI) for secure communication and authentication.
Decryption
Decryption is the process of converting encrypted data back into its original, readable form using the appropriate decryption key. It is the reverse of encryption and allows authorized parties to access protected information.
Brute Force Attack
A brute force attack is a method of trying every possible combination of keys or passwords to gain access to encrypted data. Longer and stronger keys make brute force attacks computationally infeasible.
File Encryption Algorithms:
AES (Advanced Encryption Standard)
AES is a widely used symmetric encryption algorithm. It offers strong security and is used in various applications, from securing Wi-Fi networks to encrypting files and data at rest.
RSA (Rivest–Shamir–Adleman)
RSA is a popular asymmetric encryption algorithm. It plays a crucial role in secure communications and digital signatures. RSA’s strength lies in its reliance on the difficulty of factoring large prime numbers.
DES (Data Encryption Standard)
DES was one of the earliest encryption standards. While it’s now considered obsolete due to its vulnerability to brute force attacks, it paved the way for modern encryption methods.
Blowfish
Blowfish is a symmetric key block cipher known for its simplicity and speed. Although it’s not as widely used as AES, it remains a respected encryption option.
ChaCha20
ChaCha20 is a symmetric encryption algorithm known for its speed and security. It’s gaining popularity as an alternative to AES, especially in mobile and lightweight applications.
Use Cases of File Encryption
Data Protection in Transit
Encrypting data during transmission ensures that even if intercepted, the information remains secure. This is essential for online banking, e-commerce transactions, and secure messaging apps.
Data Protection at Rest
When files are stored on devices or in the cloud, encryption protects them from unauthorized access. This is crucial for safeguarding sensitive documents, financial records, and personal information.
Secure Communication
Encryption ensures that emails, instant messages, and voice calls remain confidential. It’s a critical component of secure communication, particularly for businesses and individuals sharing sensitive information.
Compliance Requirements
Many industries and organizations are subject to regulatory compliance standards that mandate data encryption. Failing to adhere to these standards can result in severe legal consequences.
Challenges and Best Practices
Key Management
Managing encryption keys is a critical aspect of file security. Ensure that keys are stored securely, regularly updated, and only accessible to authorized personnel.
Choosing the Right Encryption Algorithm
Selecting the appropriate encryption algorithm depends on your specific needs and security requirements. Conduct a risk assessment to determine the best fit for your organization.
Regularly Updating Encryption Protocols
Cyber threats evolve constantly, so it’s crucial to keep your encryption protocols up to date. This includes updating software, algorithms, and encryption key lengths as needed.
Educating Employees
Your organization’s security is only as strong as its weakest link. Provide comprehensive training to employees on the importance of encryption, password hygiene, and data protection best practices.
Conclusion:
File encryption is a fundamental tool in today’s digital landscape, serving as a shield against the ever-present threats to data privacy and security. Whether it’s safeguarding data in transit, at rest, or facilitating secure communication, encryption plays a pivotal role. It is imperative to stay vigilant, update encryption protocols, and educate employees to stay one step ahead of cyber adversaries.
FAQs:
What is the difference between passphrases and passwords?
Passphrases and passwords are both used for authentication and access control. Passphrases are typically longer and more complex than passwords, offering greater security. Users should choose strong passphrases and passwords and avoid sharing them.
How do I choose the right encryption algorithm for my needs?
The choice of encryption algorithm depends on your specific security requirements. Conduct a risk assessment to determine the best fit for your organization. Common algorithms include AES, RSA, Blowfish, and ChaCha20.
Is file encryption necessary for individuals or only for businesses?
File encryption is essential for both individuals and businesses. It protects sensitive personal information and confidential business data from cyber threats, making it a crucial security measure for everyone.
Can file encryption be cracked or hacked?
While no encryption is entirely immune to attacks, modern encryption methods are highly secure and require significant computational power and time to crack. Regularly updating encryption protocols and key management practices helps maintain security.
