Introduction
Securing employee laptops is critical for any organization that wishes to protect its data and intellectual property. Employee laptops are often used outside of the company’s network, making them vulnerable to various security threats. These risks include cyber-attacks, viruses, malware, phishing scams, theft, or physical damage to the device.
To ensure data security and prevent unauthorized access, it is essential to implement stringent measures for securing employee laptops. This guide will take you through steps that your organization can take to protect your data and minimize the risk of a data breach.
The guide will provide detailed information on securing employee laptops using a combination of software solutions and best practices. It covers topics such as installing antivirus software, encrypting sensitive information stored on the laptop, implementing robust password policies and educating employees on safe computing habits. By following these steps diligently, your organization can create a culture of cybersecurity awareness that helps safeguard vital company assets while reducing the likelihood of costly breaches or hacks.
Guide on Securing Employee Laptops
-
Create a Comprehensive Security Policy
A comprehensive security policy should specify the rules and guidelines that employees must follow when using company-owned laptops, including password management, software installation, and internet usage. A well-written security policy can help prevent data breaches and other security incidents by ensuring that employees are aware of their responsibilities in keeping confidential information safe.
When creating a security policy, it’s important to involve all stakeholders, including IT personnel and legal experts. The policy should be clear and easy to understand so that employees can comply with its provisions easily. It’s also essential to regularly review the policy to ensure that it remains up-to-date with changing technology trends and new threats.
-
Implement Password Protocols
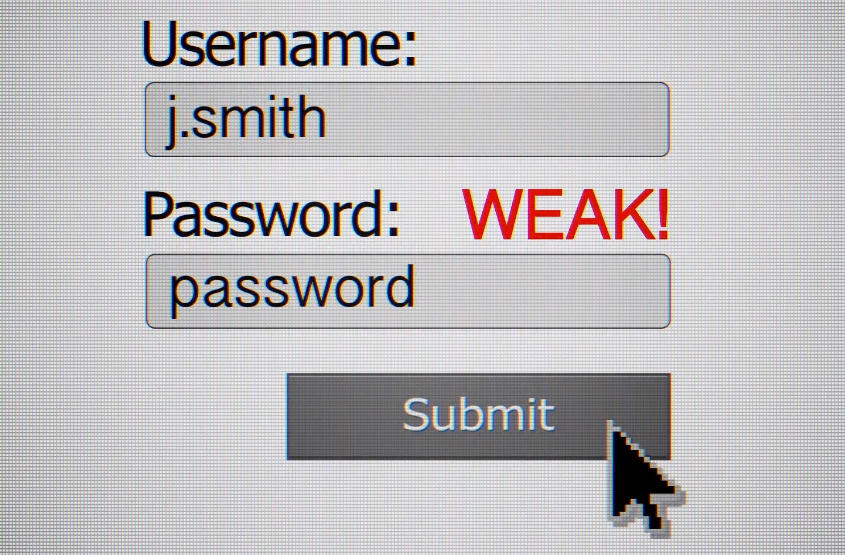
Passwords are the first line of defense against cyber attackers, and it’s important that employees create strong passwords that cannot be easily guessed or cracked. Companies should establish password policies that require employees to create passwords with a minimum length and complexity, including a combination of uppercase and lowercase letters, numbers, and symbols.
In addition to creating strong passwords, companies should also enforce periodic password changes to ensure continued security. It’s recommended that employees change their passwords every 90 days as an added measure of protection. Additionally, companies can implement multi-factor authentication (MFA) for added security. MFA requires users to provide additional verification beyond a password, such as a fingerprint or text message code.
-
Install Antivirus Software

Antivirus software helps to protect against malware, viruses, and other forms of cyber threats that can compromise the security of your laptop. Ensure that you install the latest version of antivirus software on all employee laptops and set up automatic updates to keep it current. It is also essential to configure the settings correctly, such as setting up real-time scanning and scheduling regular scans.
Moreover, some antivirus software comes with additional features such as firewalls, spam filters, and parental controls. Take advantage of these features to enhance your laptop’s protection from external threats further. Also, educate your employees on the importance of using antivirus software and how they can avoid downloading malicious files by only downloading from trusted sources or avoiding suspicious websites.
It is essential to monitor your antivirus software continuously for any alerts or notifications about potential threats. Invest in a reliable monitoring system or outsource this task to an IT professional who can handle potential security breaches before they cause damage.
-
Enable Firewall Protection
A firewall is a network security system that monitors and controls incoming and outgoing traffic based on predetermined security rules. It acts as the first line of defense against unauthorized access to your laptop or company network. Firewalls can be either hardware or software-based, and they are easy to install and configure.
A properly configured firewall reduces the risk of cyber-attacks by blocking malicious traffic while allowing legitimate traffic to pass through. By enabling firewalls on all employee laptops, you can protect your sensitive data from hacks, viruses, worms, and other cyber threats that could compromise your organization’s IT infrastructure. Firewalls also provide real-time monitoring capabilities that detect any suspicious activity on the network.
-
Update Software and Operating Systems
Software updates often include patches for security vulnerabilities that hackers may use to gain access to your system. Operating system updates also improve the performance and stability of your computer, ensuring that it runs smoothly and efficiently.
One important thing to note is that many operating systems have automatic update settings enabled by default. However, it’s still crucial to check regularly for any missed or failed updates manually. This way, you can ensure that all critical patches are installed on time.
Additionally, some outdated applications might still be present on the laptop even after updating the OS. These apps could pose a risk as they are no longer supported by their developers or have unpatched vulnerabilities; thus, removing them is recommended.
-
Encrypt Hard Drives
Encryption involves converting data into a secret code that can only be read with the correct decryption key. This means that even if someone gains unauthorized access to the laptop, they won’t be able to read any of the data without the encryption key.
Encrypting hard drives can be done through various software tools such as BitLocker, VeraCrypt, or Apple’s FileVault. These tools are easy to use and provide an added layer of security against data breaches and thefts. Additionally, encrypted hard drives also protect sensitive information from falling into the wrong hands in case an employee loses their laptop or it gets stolen.
However, it is important to note that encryption alone does not guarantee complete security for laptops. It should only be one part of a comprehensive security plan that includes other measures such as strong passwords, two-factor authentication, and regular software updates.
-
Limit Administrative Access
Administrative access grants users elevated privileges, which can be used to install software or make changes to the system settings. This level of access could also allow users to disable security settings or bypass security protocols, making it easier for cybercriminals to infiltrate your systems.
To mitigate this risk, consider limiting administrative access only to certain employees who require it for their job functions. Regular users should not have administrative privileges on their laptops. Additionally, ensure that all accounts with administrative privileges have strong passwords and are regularly updated.
-
Use Virtual Private Networks (VPNs)
VPNs create a secure and private connection between an employee’s laptop and the internet, which helps to protect sensitive data from hackers and other cyber threats.
VPNs work by encrypting all internet traffic that passes between an employee’s laptop and the VPN server. This means that even if a hacker intercepts this traffic, they will not be able to see any of the information contained within it. Additionally, because VPNs mask IP addresses, they can also help prevent tracking by third-party advertisers or malicious organizations.
In order to use VPNs for securing employee laptops effectively, it is important to choose a reputable provider with strong encryption protocols and strict privacy policies. It is also essential to educate employees about how to use this technology properly since some may inadvertently disable their VPN or fail to connect when accessing public Wi-Fi networks outside of the office.
-
Disable Automatic Login
This is especially important for devices that may be used in public places or shared among multiple users. With automatic login, anyone who gains access to the laptop can easily log in and gain access to sensitive information.
Disabling automatic login requires users to enter a password every time they want to use the laptop. This provides an additional layer of security that can prevent unauthorized access and protect sensitive data. It also forces employees to be more mindful of their passwords and encourages them to choose strong, unique passwords that are difficult for hackers to guess.
To disable automatic login on Windows laptops, go to Settings > Accounts > Sign-in options and turn off “Use my sign-in info…” For Mac laptops, go to System Preferences > Users & Groups > Login Options and select “Display Login Window as: Name and Password.” These simple steps can go a long way in securing employee laptops and protecting your company’s valuable data.
-
Educate Employees on Security Best Practices
It is vital to provide training sessions that cover the basics of cybersecurity, such as phishing scams, password management, and software updates. Employees should be educated on how to identify suspicious emails, links, and attachments. They must also understand the importance of creating strong passwords and changing them regularly.
Moreover, it is crucial to emphasize the significance of keeping software up-to-date on their laptops. Outdated applications are vulnerable to malware attacks that can compromise sensitive data. Providing guidelines for safe file sharing practices is also essential to prevent accidental sharing of confidential files with unauthorized parties.
-
Monitor Laptop Usage
This involves keeping track of which applications are being used, how long they are being used for, and whether any unauthorized or suspicious activity is taking place. By closely monitoring laptop usage, employers can identify potential security threats and take appropriate action before any damage is done.
There are various tools and software programs available that can help with laptop monitoring. These include keystroke logging software, website tracking tools, and network traffic analysis tools. Employers should also set up regular audits to review laptop usage logs and assess the effectiveness of their security measures.
In addition to enhancing security, monitoring laptop usage can also help improve productivity by identifying areas where employees may need additional training or resources. It also ensures that company resources are being used appropriately and not being misused for personal purposes during work hours.
-
Limit the Use of Personal Devices
It is essential for companies to limit the use of personal devices in the workplace. Employees should be discouraged from using their personal laptops, tablets or smartphones for work purposes, especially when handling company data.
To reduce the risk of data breaches stemming from personal devices, companies should ensure that all employees have access to secure and encrypted company-owned devices. This will help keep sensitive information confidential and prevent unauthorized access.
In addition to limiting the use of personal devices, companies must also implement strict security policies governing device usage within the workplace. These policies should include guidelines on password protection, software updates, and safe browsing practices.
-
Implement Remote Wiping
Implementing remote wiping allows you to erase sensitive data from a device that has been lost or stolen, regardless of its physical location. This feature ensures that your company’s confidential information remains protected, even if the laptop falls into the wrong hands.
Remote wiping can be implemented through various software tools and mobile device management (MDM) systems. These solutions allow you to remotely wipe all data or specific files from a device with just a few clicks. Moreover, some MDMs provide real-time tracking features that enable you to locate the stolen device’s whereabouts and take prompt action.
It’s important to note that remote wiping should only be used as a last resort when all other measures have failed. Before initiating remote wiping, ensure that you have exhausted all attempts at locating the missing laptop and have taken steps to secure any other devices or accounts associated with the employee in question. Additionally, inform your employees about this policy beforehand so they understand what happens in case their laptop is lost or stolen.
-
Back Up Data Regularly
Backing up your data ensures that you have a copy of all your critical files and documents in case something happens to your computer. There are several ways to back up data, including cloud storage, external hard drives, and network-attached storage (NAS) devices.
Cloud storage services like Dropbox, Google Drive, and Microsoft OneDrive provide an easy way to store and access files from anywhere with an internet connection. These services also offer automatic syncing features that ensure your files are always up-to-date. External hard drives can be used for local backups of large amounts of data. They offer faster backup speeds than cloud storage but require physical access to the drive.
Network-attached storage (NAS) devices are ideal for businesses with multiple employees who need access to shared files. NAS devices allow you to create a centralized location for storing and accessing data on a local network.
-
Use Cloud-Based Solutions
Cloud-based solutions are becoming increasingly popular in the business world, especially when it comes to securing employee laptops. Cloud storage allows you to store your data on a remote server that can be accessed from anywhere with an internet connection. This means that if an employee’s laptop is lost or stolen, their data can still be protected and accessed from another device.
In addition to cloud storage, there are also cloud-based security solutions available. These include antivirus and anti-malware software that can be centrally managed and updated by IT administrators. This makes it easier to ensure that all employee laptops have the latest security measures in place.
One of the biggest benefits of using cloud-based solutions for laptop security is scalability. As your business grows and you onboard more employees, it becomes increasingly difficult to manage individual laptops and ensure they are all adequately secured. With cloud-based solutions, however, you can easily scale up your security measures as needed without having to manually install new software on each individual device.
-
Enforce Laptop Registration
When laptops are registered, the IT department can keep track of who has been given a device and when it is returned. This helps to prevent the loss or theft of laptops as well as ensure that all devices have up-to-date security measures.
One way to enforce laptop registration is by requiring employees to sign a usage policy. This policy should outline the expectations for using company equipment, including proper care and handling of laptops, reporting lost or stolen devices and keeping software updated.
Another effective way to enforce laptop registration is by installing tracking software on all company devices. This software can help locate lost or stolen laptops and prevent unauthorized access to sensitive data in case a device falls into the wrong hands.
-
Conduct Regular Security Audits
These audits help you identify vulnerabilities in your system and address them before they can be exploited by hackers or other cyber threats. Conducting regular security audits also ensures that your employees are following all necessary protocols and guidelines for securing their laptops.
When conducting a security audit, it is important to take an inventory of all laptops used within the organization. This will help you identify which devices need updates or replacements to maintain optimal security levels. During these audits, it is also important to review access controls and privileges granted to employees as well as any third-party vendors who may have access to your network.
Overall, regular security audits should be an essential part of any organization’s cybersecurity strategy. They help identify weaknesses in your system that could lead to data breaches or theft, and allow for timely fixes before any damage can occur.
-
Develop an Incident Response Plan
An incident response plan outlines the steps that will be taken in case of a cybersecurity breach or data loss. It is essential for businesses of all sizes to have such a plan in place as the consequences of a cyber attack can be devastating.
The first step in developing an incident response plan is identifying potential risks and vulnerabilities. This involves assessing the security measures currently in place and pinpointing areas that need improvement. Once these risks have been identified, it is important to create an action plan with clear steps to mitigate them.
Another critical component of an incident response plan is establishing roles and responsibilities. This includes designating individuals who are responsible for managing the response process, communicating with stakeholders, and reporting on progress throughout the recovery period. By having clearly defined roles and responsibilities, businesses can ensure that everyone knows what they need to do in case of a cyber emergency.
-
Work with a Professional Security Firm
These firms have the expertise and experience needed to identify potential security threats and create effective solutions to mitigate them. They can also provide valuable guidance on best practices for protecting sensitive data.
One of the key advantages of working with a professional security firm is access to advanced technologies that may not be available in-house. This includes specialized software, hardware, and other tools designed specifically for cybersecurity purposes. Working with a third-party vendor also means that employees can benefit from ongoing training and support, ensuring that they are up-to-date on the latest security protocols.
In addition to technical expertise, professional security firms bring another important advantage: objectivity. Because they are not part of your organization’s internal structure, they can provide an unbiased perspective on potential vulnerabilities and recommend solutions without fear of conflict or politics getting in the way.
-
Continuously Update Security Measures
With the constant threat of cyberattacks, it’s essential to continuously update your software and hardware systems. Make sure you have the latest version of antivirus software installed on all employee laptops and that they are set to automatically update.
Additionally, implementing strong password policies can prevent unauthorized access to sensitive data. Encourage employees to use complex passwords that include a combination of upper and lowercase letters, numbers, and symbols. You can also require them to change their passwords every few months as an added layer of protection.
Ensure that all laptops are encrypted so that if they fall into the wrong hands, the data cannot be accessed without permission. Encryption should be done on both the device’s hard drive and any external storage devices used by employees.
FAQs
Are Laptops A Potential Data Security Risk?
Laptops have become an essential tool for modern-day work. However, they can also pose a potential data security risk. Laptop theft or loss is one of the most common ways that sensitive information falls into the wrong hands. Hackers can also exploit vulnerabilities in laptops to gain access to company networks and sensitive data.
Another risk factor is employee negligence or lack of awareness about proper security measures. For instance, employees may use weak passwords, leave their laptops unlocked and unattended in public places, or connect to unsecured Wi-Fi networks. These actions increase the likelihood that hackers could steal confidential information.
Conclusion
Securing employee laptops is a critical process that requires an organization-wide effort. It involves implementing security measures such as encryption and antivirus software, enforcing strong passwords, and ensuring regular updates of the operating system and applications. Additionally, organizations need to create policies and guidelines that govern the use of company-owned laptops.
