Introduction
A data security analyst is an IT professional who specializes in protecting sensitive information from unauthorized access, use, disclosure, and destruction. In today’s digital age, businesses rely on data to make informed decisions, increase efficiency and productivity, and deliver better services to their customers. However, this also puts them at risk of cyber-attacks and data breaches that can lead to financial losses, legal liabilities, reputational damage or even business closure.
To minimize these risks and ensure compliance with regulatory requirements such as GDPR or HIPAA, organizations need skilled professionals who can assess their security posture, identify vulnerabilities and threats, design effective security controls and protocols, monitor security events in real-time using advanced technologies such as SIEM (Security Information and Event Management), respond to incidents promptly with incident response plans (IRP) or business continuity plans (BCP), educate employees on best practices for data protection awareness training.
Qualifications For Becoming A Data Security Analyst
Data security analysts need to have certain qualifications to become effective in their roles.
A bachelor’s degree in computer science or information technology is essential. This provides the foundational knowledge of programming languages and operating systems that are necessary for conducting vulnerability assessments and penetration testing.
Experience with network systems and protocols is necessary to understand how cybercriminals can exploit vulnerabilities within an organization’s infrastructure. Additionally, certifications such as Certified Information Systems Security Professional (CISSP) or Certified Ethical Hacker (CEH) demonstrate expertise in ethical hacking and security analysis.
Data security analysts must also have strong technical skills in areas such as network architecture basics like TCP/IP protocols or firewall configurations; database administration concepts like SQL queries or backup strategies; operating systems knowledge like Windows Server 2016/2019 features versus Linux equivalents; cryptography understanding including encryption types available in SSL/TLS certificates. They need to possess soft skills such as communication proficiency for interacting with stakeholders across departments within the organization or external partners/vendors involved in cybersecurity programs.
Responsibilities Of A Data Security Analyst
Protecting Sensitive Data

A data security analyst plays a crucial role in ensuring the protection of sensitive data. These professionals are responsible for identifying, analyzing and addressing any potential security threats that may arise in an organization’s computer systems or networks. They work closely with other IT professionals to implement measures such as firewalls, encryption protocols, and access controls to safeguard data from unauthorized access.
Identifying And Addressing Potential Security Threats
As a data security analyst, one needs to be vigilant in monitoring the network for any suspicious activities that may indicate an attempted breach or hack. One key approach to identifying potential threats is by analyzing the logs generated by various devices on the network, including servers, routers, and firewalls. By closely examining these logs, you can detect anomalies such as unusual login attempts or unauthorized access attempts.
Developing And Implementing Security Measures
Once potential risks have been identified, data security analysts must develop strategies to mitigate these risks effectively. This involves implementing various controls such as firewalls, intrusion detection systems, encryption tools, access controls, and authentication mechanisms. The goal is to create multiple layers of defence that can prevent or detect any unauthorized access attempts.
Conducting Security Audits
Conducting security audits involves evaluating existing security measures in place to detect vulnerabilities that could potentially be exploited by hackers or other malicious actors. There are several steps involved in conducting a comprehensive security audit, including assessing the current state of security measures, identifying areas of potential risk, and developing an action plan to address any issues that are identified.
One important aspect of conducting a successful security audit is ensuring that all relevant stakeholders are involved in the process. This may include IT personnel, company executives, and other members of the organization who have access to sensitive data or systems. Additionally, it’s important to stay up-to-date with current best practices in data security and use that knowledge to inform your approach.
Tools And Techniques Used By Data Security Analysts
Penetration Testing
Penetration testing involves simulating a cyber-attack on an organization’s software, network, or application to identify vulnerabilities that hackers could exploit. Penetration testing helps organizations understand their potential weaknesses and assess the effectiveness of their security measures in protecting sensitive data from unauthorized access.
A penetration tester uses various techniques, including social engineering and exploitation of system vulnerabilities, to gain access to an organization’s assets. Once they have gained access, they test how far they can go without being detected by the security system. The goal of penetration testing is not only to identify weak points but also to provide recommendations for improving security posture.
Vulnerability Scanning
Vulnerability scanning involves identifying, monitoring, and analyzing potential weaknesses in computer systems and networks that could be exploited by attackers to gain unauthorized access or manipulate information. This process helps data security analysts identify vulnerabilities before they can be exploited by cybercriminals.
To conduct vulnerability scanning, data security analysts use various tools and techniques to scan the system for loopholes. The results provide insights into areas that need improvement, such as outdated software versions, unsecured passwords, or weak firewalls. Analysts then provide recommendations on how to fix these vulnerabilities or mitigate their impact.
Firewall Management
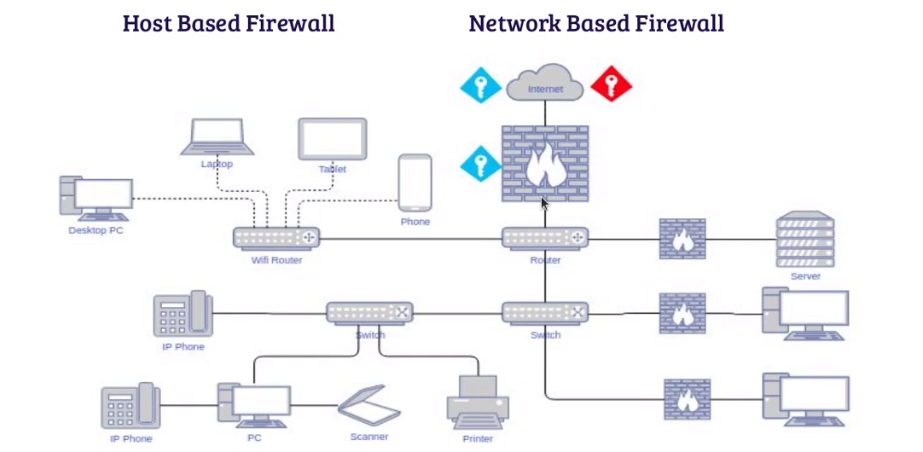
Firewall management acts as a barrier between the internet and an organization’s internal network. The role of a data security analyst is to ensure that firewalls are properly configured and maintained. A firewall management strategy should include regular updates to the firewall software, monitoring for intrusion attempts, and ensuring that all ports are secured.
Intrusion detection is another important aspect of firewall management. This involves monitoring network traffic and identifying any attempts to breach the firewall. Data security analysts must also be aware of emerging threats on the internet landscape and update their firewalls accordingly.
Encryption
Data security analysts are responsible for implementing encryption techniques to protect an organization’s confidential data from cyber threats. They must stay updated on emerging trends in encryption technology and ensure that all essential data is encrypted. They also work closely with other IT teams to ensure proper handling and storage of encrypted data.
Intrusion Detection And Prevention
Intrusion detection involves monitoring networks, systems, and applications to identify any suspicious activity indicative of a possible security threat. These activities can range from unauthorized access attempts or malicious code injections to unusual network traffic patterns.
Once an intrusion has been detected, the next step is to take measures that prevent further damage. This is where intrusion prevention comes in. Intrusion prevention solutions use various techniques such as firewalls, access control lists, and intrusion prevention systems (IPS) to block or quarantine the source of the attack.
Different Types Of Data Security Analysts
Network Security Analyst
A network security analyst is responsible for protecting a company’s computer networks from cyber-attacks and other potential threats. They work to ensure that a company’s data, hardware, and software are all secure and protected against unauthorized access. In order to perform their job effectively, they must stay up-to-date on the latest trends in cybercrime and use various tools and techniques to identify vulnerabilities in a network.
Risk Management Analyst
Risk management analysts are responsible for identifying potential risks and vulnerabilities within a company’s IT infrastructure, as well as developing strategies to mitigate these risks. This involves analyzing data from various sources, such as network logs and security reports, to identify potential threats.
Industries That Employ Data Security Analysts
Financial institutions deal with large volumes of confidential information such as bank account details, credit card numbers, and social security numbers on a daily basis. A single breach could result in significant financial losses and damage to their reputation. Therefore, they employ data security analysts who specialize in financial cybersecurity strategies.
Another industry that requires the expertise of data security analysts is healthcare. With the digitization of medical records and the increasing use of telemedicine platforms, patient privacy has become a major concern for healthcare organizations. Data breaches can lead to severe consequences such as identity theft or exposure of personal health information leading to discrimination or embarrassment; hence,data security analysts help prevent such risks by implementing effective measures to safeguard health records from unauthorized access or cyber threats.
Challenges Faced By Data Security Analysts
Data security analysts play a crucial role in safeguarding sensitive information from cyber threats. However, their job is not without challenges. One of the biggest challenges faced by data security analysts is keeping up with rapidly evolving technology and identifying new vulnerabilities as they emerge.
Another challenge is that the sheer volume of data generated by organizations can make it difficult to identify and prioritize potential risks. Data security analysts must be able to analyze large amounts of data quickly and accurately, often using specialized tools and software.
Data security analysts must also navigate regulatory frameworks that govern how organizations collect, store, and use data. Compliance regulations such as GDPR or HIPAA can vary widely depending on the industry or geography, making it incredibly challenging for analysts to stay up-to-date on all relevant regulations while maintaining effective cybersecurity practices.
Best Practices For Data Security Analysts
Stay up-to-date with the latest security trends and technologies. This includes regular training and certification programs, attending seminars and conferences, and following industry publications. It is also important to have a clear understanding of your company’s security policies and procedures.
Implement strong access control measures. This includes limiting user privileges, regularly updating passwords, implementing multi-factor authentication, and monitoring system logs for any suspicious activities. Additionally, implementing encryption techniques can help protect sensitive data both at rest and in transit.
Ultimately, successful data security analysts are those who are proactive in identifying potential vulnerabilities within their systems and taking action to mitigate them before they can be exploited by malicious actors.
Salary For Data Security Analysts
According to Glassdoor, the average salary for a senior-level data security analyst in the United States is around $108,000 per year. However, salaries can range from $80,000 to over $150,000 per year depending on factors such as years of experience and geographic location.
Due to the increasing importance of data security in today’s digital environment, the demand for skilled professionals in this field is high. This has led to increased competition among employers seeking qualified candidates and higher salaries being offered at senior levels in order to attract top talent.
FAQs
What Skills Do I Need To Become A Data Security Analyst?
To become a data security analyst, you need to have a strong foundation in computer science and related fields. A degree in computer science or cybersecurity is preferred, but not always necessary. You should be well-versed in programming languages such as Java, C++, Python and SQL.
Additionally, having a deep understanding of operating systems such as Windows and Linux is crucial. Knowledge of network security protocols like SSL/TLS, DNSSEC and VPNs is also important. As a data security analyst, you will be dealing with sensitive information; therefore you need to have good communication skills that can help explain complex technical issues to non-technical users.
You should also possess analytical skills that allow you to analyze large volumes of data quickly and accurately. Being able to identify potential threats through the analysis of system logs is essential for this role. Knowledge of compliance standards like GDPR and HIPAA are necessary since they provide the framework for how organizations manage personal data privacy globally.
What Are The Benefits Of Hiring A Data Security Analyst?
A data security analyst can bring significant benefits to an organization. One of the most important is the ability to manage and prevent cyber threats. A skilled analyst can identify potential vulnerabilities in a company’s network or systems and put measures in place to mitigate them. This includes installing firewalls, monitoring access controls, and creating policies for data handling.
Another benefit of hiring a data security analyst is that they can help ensure compliance with industry regulations such as HIPAA or GDPR. They are able to stay up-to-date on changing laws and regulations, ensuring that a company’s information management practices are aligned with legal requirements. This not only protects the organization from regulatory fines but also helps build customer trust.
A data security analyst can also help improve overall efficiency within an organization by streamlining processes related to data management. They can work with IT teams to develop automation tools that reduce manual labor involved in managing sensitive information while improving accuracy and reliability of data handling practices across different departments.
What Are The Most Common Data Security Threats Faced By Organizations?
Phishing attacks:
These types of attacks involve the use of fraudulent emails or websites to trick employees into providing sensitive information. Phishing attacks are becoming more sophisticated, making it difficult for even experienced employees to identify them.
Malware:
Malware can infect an organization’s systems through various channels such as malicious email attachments, infected software downloads, or compromised websites. Malware can cause significant damage to an organization’s data and systems and can be challenging to detect and remove.
Insider threats:
Insider threats also pose a considerable risk to organizations’ data security. Insider threats refer to incidents where current or former employees intentionally or unintentionally compromise sensitive information through actions such as stealing confidential data, mishandling it, or accidentally disclosing it outside the company network.
Conclusion
Being a data security analyst is a vital role in any organization that handles sensitive information. The responsibilities of this position range from analyzing and monitoring networks to identifying potential risks and implementing security measures to protect against them. They are also responsible for ensuring compliance with regulations, policies, and procedures related to data privacy.
A successful data security analyst must have excellent technical skills, including knowledge of computer systems, networks, and databases. They should be able to analyze complex information and identify patterns or anomalies that may indicate a potential security threat. Additionally, they must have strong communication skills to effectively communicate risks and vulnerabilities to key stakeholders within the organization.
