Yes, RAID (Redundant Array of Independent Disks) improves the security of your data by providing redundancy, which protects against data loss due to disk failures. However, it is not a substitute for backups or protection against other types of threats like malware or ransomware.
In today’s digitally-driven world, data security is of utmost importance. With increasingly sophisticated cyber threats, individuals and businesses must adopt robust measures to protect their valuable data. One such measure is RAID, which stands for Redundant Array of Independent Disks. RAID is a technology that can significantly enhance the security and reliability of data storage systems. We will delve into the concept of RAID, its role in data security, and the steps to implement it effectively.
Understanding the Concept of RAID
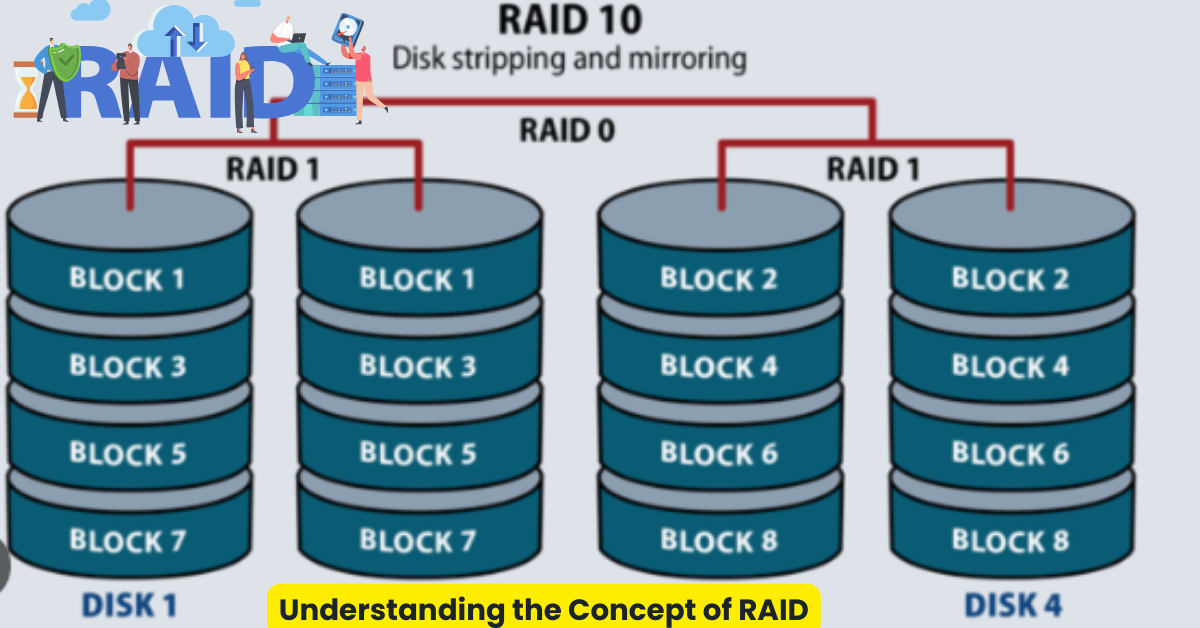
RAID, which positions for Redundant Array of Independent Disks, combines multiple physical hard drives into a single logical unit. By doing so, RAID provides several advantages over traditional single-drive systems. It improves data redundancy, performance, and error tolerance, ultimately enhancing data security.
When understanding RAID, it is important to familiarize yourself with the different types of RAID levels. Each RAID level offers a different data storage and protection approach, catering to different needs and requirements.
Different Types of RAID Levels
There are various RAID levels, each offering unique features and benefits. Let’s explore some of the most popular RAID levels:
1. RAID 0
RAID 0, or striping, is a RAID level that strips data across multiple drives. This enhances performance by allowing data to be read and written simultaneously across multiple drives. However, RAID 0 offers no redundancy, meaning all data is lost if one drive fails. It is commonly used when high performance is the primary concern and data redundancy is not a critical factor.
For example, in a gaming setup where fast loading times are essential, RAID 0 can significantly improve performance by distributing the load across multiple drives.
2. RAID 1
RAID 1, or mirroring, is a RAID level that mirrors data across two drives. This provides redundancy and improved read performance. In RAID 1, data is written to both drives simultaneously, ensuring that if one drive fails, the data remains intact on the other drive. The read performance is enhanced as the system can read data from both drives simultaneously.
RAID 1 is commonly used in scenarios where data redundancy and reliability are paramount. For example, in critical systems where data integrity is crucial, such as financial institutions or database servers, RAID 1 provides an added layer of protection against data loss.
3. RAID 5
RAID 5 is a RAID level that uses data striping with distributed parity. It combines performance, redundancy, and efficient space usage. In RAID 5, data is striped across multiple drives, and parity information is distributed across all drives. This allows for both improved performance and data redundancy.
RAID 5 is commonly used in environments where a balance between performance and data redundancy is desired. It offers a good compromise between performance and fault tolerance. For example, in small to medium-sized businesses where cost-effectiveness and data protection are important, RAID 5 is often implemented.
4. RAID 10
RAID 10, also known as RAID 1+0, is a RAID level that combines mirroring and striping. It offers both redundancy and performance benefits. In RAID 10, data is mirrored across multiple pairs of drives, and then these pairs are striped. This provides both the redundancy of RAID 1 and the performance of RAID 0.
RAID 10 is commonly used in environments where both high performance and data redundancy are critical. It is often implemented in enterprise-level systems where data integrity and availability are top priorities, such as large-scale databases or virtualization environments.
Understanding the different RAID levels allows you to choose the right configuration based on your specific needs, whether prioritizing performance, data redundancy, or a balance between the two.
The Role of RAID in Data Security
The protection of data is a critical concern for individuals and organizations alike. In today’s digital age, where information is stored and accessed electronically, robust data security measures are paramount. RAID (Redundant Array of Independent Disks) is one such measure that has gained prominence. RAID technology offers a reliable and efficient way to safeguard data from potential loss or corruption.
How RAID Protects Data
One of the primary ways RAID enhances data security is through redundancy. Having multiple drives store duplicate copies of data, RAID can protect against data loss in case of drive failures. Imagine a hard drive suddenly fails, rendering the stored data inaccessible. This could be catastrophic for businesses, leading to significant financial losses and potential reputational damage. However, with RAID, this risk is mitigated.
RAID employs mirroring, where data is duplicated across multiple drives. If one drive fails, the redundant data stored on other drives allows for seamless data recovery without significant downtime or loss. The failed drive can be exchanged, and the data reconstructed using the redundant information, ensuring that the user’s valuable data remains intact and accessible.
RAID Redundancy: A Key to Data Security
Furthermore, RAID redundancy makes data accessible during drive rebuilds or rebuild failures. When a failed drive is substituted, the RAID system initiates a process called rebuilding, where the data from the remaining drives is used to reconstruct the information on the new drive. This ensures that users can continue accessing their data without experiencing any disruption.
During the rebuild process, RAID technology ensures that the system remains fully operational, allowing users to perform tasks without noticeable impact. This redundancy eliminates the risk of data loss and maximizes uptime, both crucial aspects of data security. Organizations can be assured that their critical data will always be available, even during hardware failures or maintenance operations.
Moreover, RAID configurations offer various levels of redundancy, each with its benefits and trade-offs. These levels, such as RAID 0, RAID 1, RAID 5, and RAID 6, provide different combinations of data striping, mirroring, and parity. This flexibility allows organizations to choose the RAID configuration that best suits their requirements, balancing performance, capacity, and data protection.
In conclusion, RAID plays a vital role in data security by providing redundancy and resilience to protect against drive failures and ensure continuous data availability. By implementing RAID technology, organizations can safeguard their valuable data, minimize the risk of data loss, and maintain uninterrupted operations. As the digital landscape evolves, RAID remains a cornerstone of data security, offering peace of mind and reliability in an increasingly data-driven world.
Implementing RAID for Enhanced Data Security
Implementing RAID (Redundant Array of Independent Disks) involves a series of steps to confirm a successful setup. Using many hard drives in a RAID configuration can enhance data security, improve performance, and increase storage capacity.
Steps to Set Up a RAID System

Setting up a RAID system requires careful planning and execution. Here are the key steps involved:
- Identify The Type Of Raid System That Best Suits Your Needs: There are different RAID levels to select from, each offering unique benefits and trade-offs. Some common RAID levels include RAID 0, RAID 1, RAID 5, RAID 6, and RAID 10. When deciding, consider factors such as data redundancy, performance requirements, and available storage space.
- Select The Appropriate Hard Drives And Hardware Required For The Raid Setup: Depending on the RAID level, you may need a specific number of hard drives with matching capacities. It’s important to ensure that the hard drives are compatible with your RAID controller and have sufficient storage capacity to meet your needs.
- Connect The Drives To The Raid Controller: Once you have the required hard drives, you must connect them to the RAID controller. This can be done by installing the drives internally in your computer or using external enclosures. Ensure that the connections are secure and that all cables are properly connected.
- Configure The Raid Controller Software Or Access The System BIOS: To configure the RAID settings and create the logical unit, you need to access the RAID controller software or the system BIOS. This allows you to define the RAID level, set up data striping or mirroring, and configure other parameters specific to your RAID setup.
- Initialize And Format The RAID Array: After configuring the RAID settings, you need to initialize and format the RAID array. This prepares the array for data storage by creating a file system and organizing the available storage space. Depending on your operating system, you can choose from various file system formats such as NTFS, FAT32, or ext4.
Choosing the Right RAID Level for Your Needs
When selecting the appropriate RAID level, it’s crucial to consider your specific requirements and priorities. Here are some factors to keep in mind:
- Redundancy: If data redundancy is a top priority, RAID levels like RAID 1, RAID 5, RAID 6, or RAID 10 are suitable options. These levels provide various degrees of fault tolerance, ensuring that your data remains intact even if one or more drives fail.
- Performance: If you require high performance and faster data access, RAID levels like RAID 0 or RAID 10 are worth considering. These levels offer improved read and write speeds by striping data across multiple drives.
- Storage Efficiency: RAID levels like RAID 5 or RAID 6 balance storage capacity and data redundancy well. They efficiently use storage space by distributing parity data across the drives.
- Available Storage Space: Certain RAID levels may be more suitable depending on the number and capacity of the hard drives you have. RAID 0, for example, offers maximum storage capacity since it combines the drives without providing redundancy.
By carefully considering these factors and understanding the trade-offs between performance, redundancy, and storage efficiency, you can select the ideal RAID level that meets your data security requirements.
The Limitations and Risks of RAID
Common Misconceptions About RAID
Despite its numerous advantages, RAID is not a foolproof solution for data security. One common misconception is that RAID eliminates the need for regular backups. While RAID provides redundancy and protection against drive failures, it does not safeguard against other risks such as accidental file deletion, filesystem corruption, or catastrophic events like fires or floods. Regular backups remain crucial to cover these scenarios.
Potential Drawbacks of Using RAID
Implementing RAID can have its limitations and risks. One potential drawback is the cost of setting up and maintaining a RAID system. RAID may require additional hardware, controllers, and increased power consumption. Assessing the cost-benefit ratio based on your specific needs and budget is vital.
Case Studies of RAID in Data Security
Successful Implementations of RAID
Many organizations have successfully implemented RAID to bolster their data security. For example, a multinational financial institution implemented RAID 5 across its server infrastructure, ensuring continuous operation even during drive failures. This enhanced data availability, reduced downtime, and increased customer satisfaction.
Lessons Learned from RAID Failures
Despite its successes, RAID has faced failures in certain cases. For instance, a small e-commerce business relied on RAID 0 without considering the lack of redundancy. Unfortunately, when one drive failed, they lost all their data, including customer records and order details. This highlights the status of understanding the limitations and risks of each RAID level before implementation.
Key Takeaways
- RAID mainly aims to protect against data loss due to disk failures.
- RAID does not offer encryption or protect against cyber threats.
- Configurations like RAID 1 (mirroring) and RAID 5 (parity) provide data redundancy.
- Using RAID alone is not sufficient for a comprehensive data security strategy.
- Combining RAID with encryption and other security measures is advisable.
FAQs
Q: Is RAID a backup solution?
A: No, RAID provides redundancy against drive failures but is not a substitute for backups.
Q: Can RAID protect against ransomware?
A: No, RAID won’t protect against malware or ransomware attacks.
Q: Which RAID level is most secure?
A: RAID doesn’t primarily focus on security. However, RAID 6 offers two parity checks, providing better fault tolerance.
Q: If I use RAID, do I need to back up my data?
A: Yes, RAID protects against hardware failures, but backups guard against data corruption, accidental deletion, and other issues.
Q: Can I combine RAID with encryption?
A: Combining RAID with disk encryption enhances data availability and security.
Conclusion
In conclusion, RAID can improve your data’s security by offering redundancy, performance enhancements, and increased fault tolerance. However, it is crucial to understand the concept, choose the right RAID level, and consider its limitations and risks. By implementing RAID effectively, you can strengthen your data security measures and mitigate the risks associated with drive failures. Remember, RAID is just one piece of the puzzle, and regular backups and other security measures should also be a part of your comprehensive data protection strategy.
