A hash is a function that converts an input (or ‘message’) into a fixed-size string of bytes, primarily used to verify data integrity.
Hashing is a fundamental concept in securing data. It plays a crucial role in numerous aspects of data security, including password storage, data integrity checks, and encryption. Together, we will determine the basics of hashing, different types of hash functions, the process of hashing in data security, the advantages and disadvantages of hashing, and common applications in data security.
Understanding the Basics of Hashing
Hashing is altering data into a fixed-size string of characters, usually represented as a hexadecimal value. The resulting string is called a hash value or hash code. Hash functions, which are mathematical algorithms, are responsible for generating the hash values.
When understanding the basics of hashing, it is important to delve into how it works and its various applications. Hashing can be seen as a technique that plays a fundamental role in data security and integrity. By converting data into a fixed-size string of characters, hashing ensures that any changes in the input data will produce a different hash value.
Definition of Hashing
Hashing can be defined as a technique that converts input data of any size into a fixed-size string of characters using a specific algorithm. This algorithm ensures that any change in the input data will produce a different hash value.
Let’s take a closer look at how this process works. When inputting data into a hash function, the algorithm processes the data and generates a unique hash value. This hash value is typically a fixed length, irrespective of the input data size. The resulting hash value can represent the original data in a condensed form.
One important aspect of hashing is that it is a one-way function. It is practically impossible to reverse-engineer the original data from the hash value. In other words, given a hash value, it is extremely difficult to determine the original input data that produced it. This property of hashing makes it an invaluable tool in various applications, particularly in data security.
The Role of Hashing in Data Security
Hashing is widely used in data security because it provides several essential features. First, it is a one-way function, meaning it is practically impossible to reverse-engineer the original data from the hash value. This property ensures that sensitive information, such as passwords, cannot be easily obtained from their hash values.
Second, even a tiny change in the input data will result in a meaningfully different hash value. This property makes hashing useful for data integrity checks. By comparing the hash values of two data sets, one can quickly determine if any modifications have been made to the original data. This feature is particularly important when data integrity is crucial, such as in financial transactions or critical systems.
Finally, hashing is also used to store and verify passwords securely. Instead of storing passwords in basic text, which is highly vulnerable to unauthorized access, websites, and applications often store the hash values of passwords. When an operator enters their password, it is hashed and related to the stored hash value. If the hash values match, the password is considered valid. This method adds a layer of security, as even if the hash values are compromised, the original passwords remain hidden.
In conclusion, hashing is a powerful technique that converts data into a fixed-size string of characters using specific algorithms. It plays a crucial role in data security, providing features like one-way functions, data integrity checks, and secure password storage. Understanding the basics of hashing is essential for anyone involved in data security and integrity.
Different Types of Hash Functions

Regarding data security, hash functions play a vital role in maintaining the integrity and confidentiality of information. Different types of hash functions are available, each serving specific purposes and offering varying levels of security.
Cryptographic Hash Functions
Cryptographic hash functions are designed to be highly secure and resistant to various attacks. They are widely used in applications that require data integrity and authentication. These functions generate unique hash values regardless of the input size.
One of the most commonly used cryptographic hash functions is SHA-256 (Secure Hash Algorithm 256-bit). It is a widely adopted standard that produces a 256-bit hash value, making it extremely difficult for attackers to reverse-engineer the original data. Another example is MD5 (Message Digest Algorithm 5), although it is considered less secure nowadays due to vulnerabilities that have been discovered.
These cryptographic hash functions have a few key properties that make them suitable for secure applications:
- Collision Resistance: Finding two different inputs that produce the same hash value is computationally unworkable.
- Preimage Resistance: Given a hash value, it is computationally infeasible to determine the original input.
- Small Input Changes Result in Large Output Changes: A slight modification in the input data will produce a completely different hash value.
Non-cryptographic Hash Functions
On the other hand, non-cryptographic hash functions are primarily used for indexing, data retrieval, and checksums. These functions are generally faster than cryptographic hash functions but may lack the same level of security.
One example of a non-cryptographic function is the Jenkins hash, widely used in hash tables and hash-based data structures. It is known for its simplicity and good distribution properties, making it suitable for applications where security is not the primary concern.
Another popular non-cryptographic hash function is MurmurHash, known for its speed and low collision rates. It is commonly used in applications that require fast hash computation, such as hash-based look-up tables and hash-based checksums.
While non-cryptographic hash functions may not offer the same level of security as their cryptographic counterparts, they are still valuable in various applications where speed and efficiency are more important.
In conclusion, hash functions are essential tools in data security, with different types serving specific purposes. Cryptographic hash functions provide high security and are used in applications where data integrity and authentication are critical. On the other hand, non-cryptographic hash functions are faster and more efficient, making them suitable for indexing, data retrieval, and checksums.
The Process of Hashing in Data Security
The process of hashing involves several steps to ensure the integrity and security of data.
Hashing is fundamental in data security to protect sensitive info from unauthorized access or tampering. It is a process that transforms data into a fixed-size hash value, which serves as a unique identifier for the input data. This hash value remains the same regardless of the input size, making it a reliable method for data integrity checks.
How Hashing Works
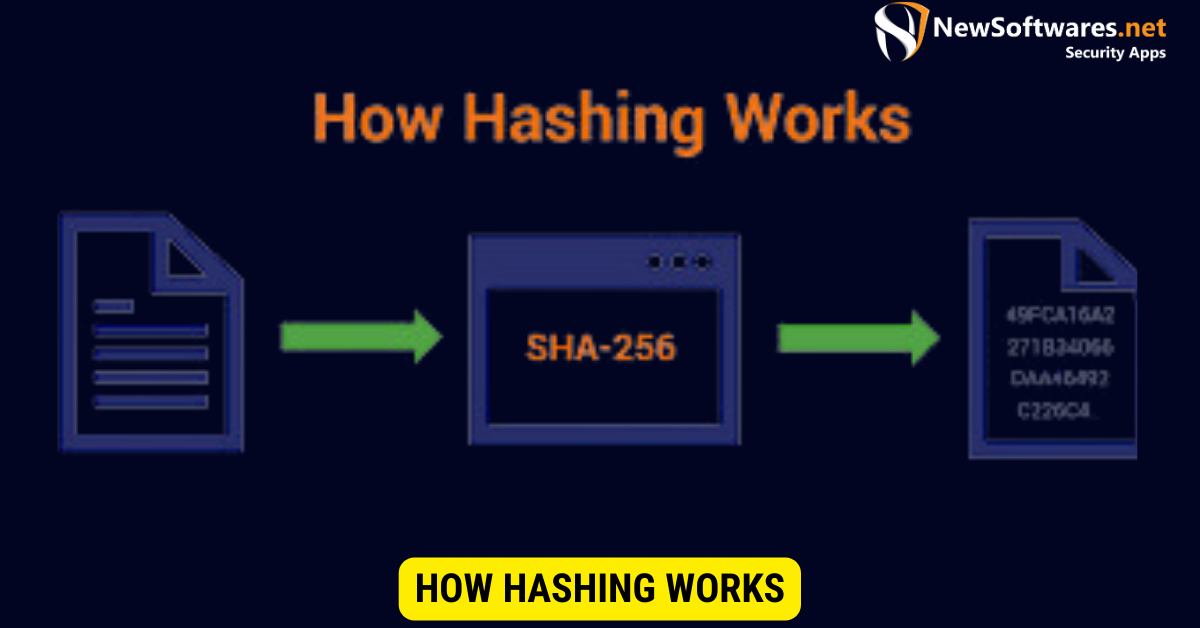
When data is put through a hash function, the algorithm processes it and generates a fixed-size hash value. This value is unique to the input data and remains unchanged regardless of the input size.
Hash functions are designed to be one-way, meaning it is computationally infeasible to reverse-engineer the original data from the hash value. This property ensures that even if an attacker gains access to the hash value, they cannot retrieve the original data without significant computational resources.
Furthermore, hash functions have a fixed output size, regardless of the input size. This property allows for efficient storage and comparison of hash values, making them ideal for data integrity checks and password storage.
The Importance of Hash Values
Hash values are essential in data security because they serve as a unique identifier for specific data. Comparing hash values can determine if any alteration has occurred in the data, making them useful for data integrity checks.
For example, in a secure communication system, hash values can be used to verify the integrity of transmitted data. The sender can compute the hash value of the data before transmission and send it along with the data. The receiver can then compute the hash value of the received data and compare it with the transmitted hash value. If the hash values match, the data has not been tampered with during transmission.
Hash values are also widely used in password storage. Instead of storing actual passwords, systems store the hash values of passwords. When a user enters their password during authentication, the system computes the hash value of the entered password and compares it with the stored hash value. This way, even if an attacker gains access to the password database, they cannot retrieve the original passwords without significant computational effort.
Moreover, hash values are used in digital signatures, a cryptographic technique to ensure digital documents’ authenticity and integrity. By signing a document with a hash value, the signer can prove that the document has not been altered since the signature was applied.
In conclusion, hashing plays a crucial role in data security by providing a reliable method for data integrity checks and protecting sensitive information. The unique and fixed-size hash values generated through the hashing process serve as a powerful tool in various applications, including secure communication, password storage, and digital signatures.
Advantages and Disadvantages of Hashing
Like any other data security technique, hashing has its advantages and disadvantages.
Benefits of Using Hashing for Data Security
- Hashing is a one-way function, preventing the retrieval of original data from the hash value.
- It ensures data integrity by detecting changes in the data by comparing hash values.
- Passwords can be securely stored and verified using hash functions.
Potential Drawbacks of Hashing
- Hash functions can produce the same hash value for different inputs, known as a hash collision. While rare, this can potentially lead to vulnerabilities.
- Hash functions are susceptible to brute-force attacks, where adversaries attempt to guess the input data by computing various hash values.
Common Applications of Hashing in Data Security
Hashing is widely used in various areas of data security.
Password Storage and Verification
When storing passwords, it is crucial to avoid storing the actual text. Instead, a hash value of the password is stored. The entered password is hashed during the verification process, and the generated hash value is compared with the stored hash value. If they match, the password is considered correct.
Data Integrity Checks
Hashing ensures data integrity in various scenarios, including file transfers and database management. Any alterations or errors can be detected by comparing the hash value of the received data with the original hash value.
Key Takeaways
- Hash functions produce a unique output for a unique input.
- They are used in data verification, password storage, and digital signatures.
- A good hash function resists collisions (two different inputs producing the same output).
- Changing even one bit in the input produces a significantly different hash output.
- Hash functions are one-way, meaning you can’t derive the original input from the hash.
FAQs
Q: Can a hash be decrypted back to the original data?
A: No, hashing is one-way; you cannot retrieve the original data from its hash.
Q: Why is hashing used for password storage?
A: Hashing passwords ensures that even if a database is compromised, the attacker only sees the hash, not the actual password.
Q: Are all hash functions secure?
A: No, older or poorly designed hash functions can have vulnerabilities. Always use well-established, cryptographic hash functions.
Q: What’s a hash collision?
A: It’s when two different inputs produce the same hash output. Good hash functions minimize the chances of collisions.
Q: Can I use hashing for encryption?
A: No, hashing and encryption are different. Encryption is reversible (with a key), but hashing isn’t.
Conclusion
In conclusion, hashing is a vital technique in securing data. Converting data into fixed-size hash values provides features like one-way functions, data integrity checks, and secure password storage. Understanding the basics, different types of hash functions, and common applications can help strengthen data security and protect sensitive information.
