Introduction
Sending secure data to the front end is crucial in protecting sensitive information from unauthorized access or interception. Without secure data transmission, data can be easily compromised, leading to severe consequences such as identity theft, financial fraud, and data breaches. Therefore, it is crucial to implement robust security measures to ensure that data is transmitted securely between the backend and the front end.
Understanding Secure Data Transmission
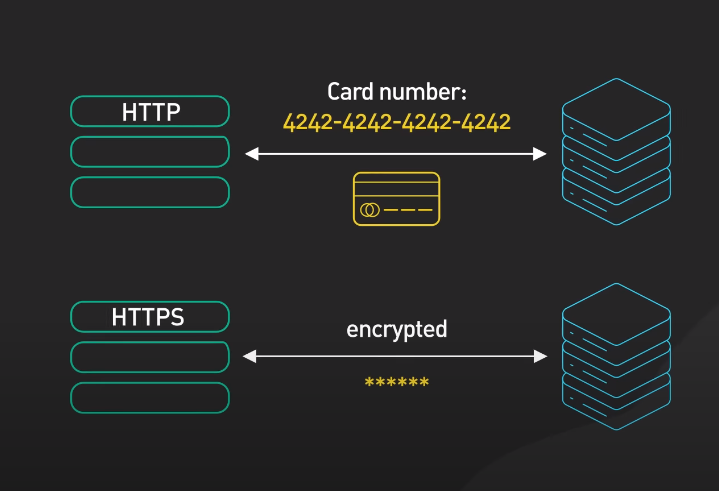
A. Encryption
Encryption is the process of converting plaintext data into ciphertext, which can only be deciphered using a secret key. This technique is used to protect data from unauthorized access and interception during transmission. There are two primary encryption techniques: symmetric encryption and asymmetric encryption.
B. SSL/TLS
Secure Socket Layer (SSL) and Transport Layer Security (TLS) are protocols used to provide secure communication over the internet. These protocols establish a secure connection between the client and server, encrypting all data transmitted between them.
Best Practices For Secure Data Transmission

A. Use HTTPS
HTTPS is a secure version of the HTTP protocol that uses SSL/TLS to encrypt data transmitted between the client and server. It is essential to use HTTPS to protect sensitive data such as login credentials, payment information, and personal data.
B. Challenges In Sending Secure Data To The Frontend
To ensure secure data transmission to the front end, several challenges need to be addressed. One of the main challenges is ensuring that the data is encrypted during transmission. This can be achieved by using the HTTPS protocol, as mentioned earlier. Another challenge is to prevent unauthorized access to the data. This can be done by implementing access control mechanisms, such as authentication and authorization. Authentication ensures that only authorized users can access the data, while authorization ensures that users can only access the data they are authorized to access.
It is also important to ensure that the data is not tampered with during transmission. This can be achieved by using digital signatures and message authentication codes (MACs) to verify the integrity of the data.
Finally, it is important to ensure that the data is not intercepted by attackers during transmission. This can be achieved by implementing network security measures, such as firewalls and intrusion detection systems.
By addressing these challenges, you can ensure that data is transmitted securely to the front end, protecting sensitive information from unauthorized access and interception.
C. Implementing Secure Data Transfer Protocols
To ensure secure data transfer, it’s important to implement protocols that are designed to protect against cyber threats. One such protocol is the Secure Sockets Layer (SSL), which encrypts data during transmission between a client and a server. Another protocol is Transport Layer Security (TLS), which is an updated version of SSL and provides even stronger encryption. In addition to using SSL or TLS, it’s important to ensure that your data transfer protocols are up-to-date and secure. This means regularly updating software and firmware and implementing best practices for network security.
Overall, implementing secure data transfer protocols is essential for protecting sensitive information from cyber threats. By using strong encryption and staying up-to-date with the latest security measures, you can ensure that your data is safe during transmission.
D. Secure Authentication And Authorization
Secure authentication and authorization are crucial for protecting sensitive information. Authentication is the process of verifying the identity of a user or device, while authorization is the process of granting or denying access to specific resources or data based on the user’s identity and permissions. To ensure secure authentication, it’s important to use strong passwords or multi-factor authentication methods, such as biometric identification or smart cards. Additionally, regularly auditing and monitoring user activity can help detect and prevent unauthorized access.
Authorization can be achieved through access control policies, which define who has access to what resources and data. These policies should be regularly reviewed and updated to ensure that only authorized users have access to sensitive information.
Overall, implementing secure authentication and authorization protocols is essential for protecting sensitive information from unauthorized access and ensuring that only authorized users can access the data they need to do their jobs.
Understanding Data Security
Definition Of Data Security
Data security refers to the protection of sensitive and confidential information from unauthorized access, use, disclosure, modification, or destruction. It involves implementing measures and protocols to ensure that data is kept safe and secure throughout its lifecycle, from creation to disposal. Data security is crucial in today’s digital age, where data breaches and cyberattacks are becoming increasingly common. By implementing effective data security measures, organizations can protect their sensitive information and maintain the trust of their customers and stakeholders.
Risks Of Insecure Data Transmission
Insecure data transmission can lead to a variety of risks, including:
1. Data breaches: When data is transmitted insecurely, it can be intercepted by unauthorized parties, leading to data breaches.
2. Data theft: Cybercriminals can steal sensitive information, such as credit card details, login credentials, and personal information, by intercepting insecure data transmissions.
3. Malware infections: Insecure data transmissions can also lead to malware infections, where malicious software is installed on the recipient’s device, allowing cybercriminals to gain access to sensitive information.
4. Reputation damage: Insecure data transmissions can damage an organization’s reputation, leading to a loss of trust and credibility among customers and stakeholders.
Common Attack Vectors
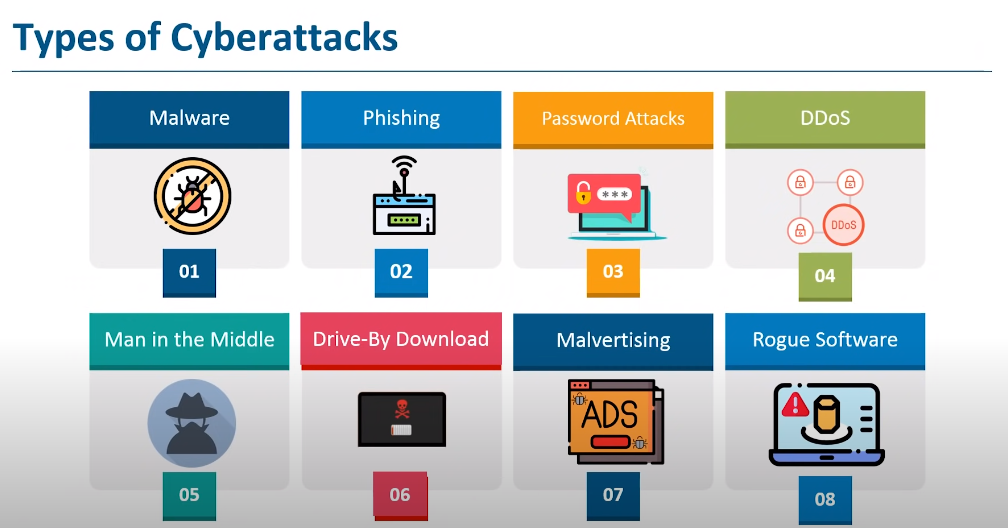
There are several common attack vectors that cybercriminals use to intercept insecure data transmissions, including:
1. Man-in-the-middle attacks: Cybercriminals intercept data transmissions between two parties, allowing them to steal sensitive information.
2. Phishing attacks: Cybercriminals use fake emails, websites, or social media accounts to trick users into sharing sensitive information.
3. Malware attacks: Cybercriminals use malware to infect devices and steal sensitive information or gain unauthorized access to systems.
4. Password attacks: Cybercriminals use various techniques to guess or obtain passwords, such as brute force attacks or phishing.
5. Denial-of-service attacks: Cybercriminals flood a network or website with traffic, causing it to crash or become unavailable.
6. SQL injection attacks: Cybercriminals exploit vulnerabilities in web applications to gain access to sensitive data stored in databases.
Individuals and organizations need to be aware of these attack vectors and take steps to protect themselves, such as using strong passwords, keeping software up-to-date, and being cautious of suspicious emails or websites.
Encrypting Data For Secure Transmission
Encrypting data for secure transmission is an essential step in protecting sensitive information from cyber threats. There are several encryption techniques that you can use to secure your data, including symmetric encryption, asymmetric encryption, and hashing. Symmetric encryption involves using the same key to both encrypt and decrypt data. This technique is commonly used for encrypting large amounts of data, such as files or databases. Asymmetric encryption, on the other hand, uses different keys for encryption and decryption. This technique is commonly used for securing communication channels, such as email or messaging apps.
Hashing involves converting data into a fixed-length string of characters, which cannot be reversed to obtain the original data. This technique is commonly used for securing passwords and other sensitive data.
When encrypting data for secure transmission, it’s important to use strong encryption algorithms and keys. Additionally, you should ensure that your encryption keys are properly managed and stored securely.
By implementing these encryption techniques, you can ensure that your sensitive data is protected from cyber threats during transmission.
Preventing Common Security Vulnerabilities
Preventing common security vulnerabilities is crucial to ensure the safety and security of sensitive information. Some of the most common security vulnerabilities include:
1. Weak passwords: Weak passwords are easy to guess or crack, making it easy for attackers to gain unauthorized access to sensitive information. To prevent this, organizations should enforce strong password policies and encourage users to use complex passwords.
2. Unpatched software: Unpatched software can leave vulnerabilities that attackers can exploit. Organizations should ensure that all software is regularly updated with the latest security patches.
3. Phishing attacks: Phishing attacks are a common way for attackers to steal sensitive information. Organizations should educate their employees on how to identify and avoid phishing emails.
4. Malware: Malware can infect systems and steal or destroy sensitive information. Organizations should use anti-malware software and regularly scan for malware.
5. Social engineering: Social engineering is a tactic used by attackers to trick users into divulging sensitive information. Organizations should educate their employees on how to identify and avoid social engineering attacks.
By taking steps to prevent these common security vulnerabilities, organizations can significantly reduce the risk of a security breach and protect their sensitive information from unauthorized access.
Secure Data Storage And Retrieval
Secure data storage and retrieval is an essential aspect of information security. Organizations should implement appropriate measures to ensure that data is stored and retrieved securely. Here are some best practices for secure data storage and retrieval:
1. Encryption: Data should be encrypted both when it is stored and when it is transmitted. This ensures that even if the data is intercepted, it cannot be read by unauthorized individuals.
2. Access control: Access to data should be restricted based on the principle of least privilege. This means that users should only be given access to the data they need to perform their job functions.
3. Backup and recovery: Organizations should implement a robust backup and recovery strategy to ensure that data can be recovered in case of a disaster or data loss.
4. Physical security: Physical security measures should be implemented to protect the servers and storage devices that store the data. This includes measures such as access controls, surveillance cameras, and alarms.
5. Monitoring: Organizations should monitor their data storage and retrieval systems for suspicious activity. This can help detect and prevent unauthorized access to sensitive data.
By implementing these best practices, organizations can ensure that their data is stored and retrieved securely, reducing the risk of a security breach and protecting sensitive information from unauthorized access.
Best Practices For Secure Frontend Development
Frontend development is an essential part of creating a secure website or application. Here are some best practices for secure frontend development:
1. Input validation: Always validate user input to prevent malicious code injection and other attacks. Use client-side validation to provide immediate feedback to users, but also validate input on the server side to ensure that it meets security requirements.
2. Cross-site scripting (XSS) prevention: Use frameworks and libraries that automatically escape user input to prevent XSS attacks. Additionally, sanitize user input to remove any potentially harmful code.
3. Password security: Implement strong password policies, including password complexity requirements, password expiration, and password history. Store passwords securely using encryption and hashing.
4. Avoid client-side storage of sensitive data: Do not store sensitive data, such as passwords or credit card information, on the client side. Instead, use server-side storage and retrieval methods.
5. Secure communication: Use HTTPS to encrypt all communication between the client and server. Avoid using HTTP, which is vulnerable to interception and tampering.
By following these best practices, front-end developers can create secure websites and applications that protect user data from unauthorized access and attacks.
How To Send Secure Data To Frontend Nodejs?
To send secure data to the front end in Node.js, you can use encryption techniques such as SSL/TLS. Here are the steps to follow:
1. Install the SSL/TLS certificate on your server.
2. Use the HTTPS protocol instead of HTTP to send data between the server and the client.
3. Use encryption libraries such as Crypto to encrypt sensitive data before sending it to the client.
4. Use secure cookies to store session information and ensure that they are transmitted over HTTPS.
5. Use secure connection settings in your database configuration to prevent unauthorized access to your database.
By implementing these measures, you can ensure that the data sent between your server and the client is secure and protected from cyber-attacks.
Conclusion
It is important to take appropriate measures to ensure the security of the front end of a web application. Using HTTPS to encrypt communication between the front end and back end, implementing access controls, keeping software up-to-date, and using security testing tools are all effective ways to enhance the security of the front end. By following these best practices, you can help prevent data interception, tampering, and other security threats.
Frequently Asked Questions (FAQs)
A. How Does Encryption Ensure Data Security?
Encryption is a process of converting plain text into a secret code, also known as ciphertext, using an encryption algorithm and a key. The ciphertext is then transmitted securely over the internet or stored in a database. Only authorized parties with the correct key can decrypt the ciphertext and access the original plain text. This ensures that if an attacker intercepts the data, they will not be able to read it without the key. Encryption is a crucial component of data security and is used to protect sensitive information such as passwords, credit card numbers, and personal data.
B. What Is The Difference Between Symmetric And Asymmetric Encryption?
Symmetric encryption and asymmetric encryption are two different methods of encrypting data. Symmetric encryption uses the same key for both encryption and decryption. This means that the sender and the receiver both have the same key and use it to encrypt and decrypt the data. The advantage of symmetric encryption is that it is fast and efficient, but the disadvantage is that the key must be exchanged between the sender and the receiver securely.
Asymmetric encryption, on the other hand, uses two different keys, a public key, and a private key. The sender uses the recipient’s public key to encrypt the data, and the recipient uses their private key to decrypt it. The advantage of asymmetric encryption is that the public key can be freely distributed, while the private key is kept secret. This makes it easier to exchange keys securely, but it is also slower and less efficient than symmetric encryption.
In summary, symmetric encryption uses the same key for encryption and decryption, while asymmetric encryption uses two different keys, a public key, and a private key.
C. What Are The Benefits Of Using HTTPS For Data Transmission?
Using HTTPS for data transmission provides several benefits, including:
1. Encryption: HTTPS encrypts the data being transmitted between the client and server, making it difficult for unauthorized parties to intercept and read the data.
2. Authentication: HTTPS provides authentication of the server, ensuring that the client is communicating with the intended server and not an imposter.
3. Integrity: HTTPS ensures that the data being transmitted between the client and server has not been tampered with or altered in any way.
4. Trust: HTTPS provides a level of trust and confidence to users, as it is a widely recognized and trusted protocol for secure communication.
Overall, HTTPS helps to ensure the confidentiality, integrity, and authenticity of data being transmitted over the internet.
D. How Can I Secure User Authentication On The Front End?
There are several ways to secure user authentication on the frontend:
1. Use HTTPS: As mentioned earlier, HTTPS provides a secure channel for data transmission between the client and server. This can help prevent unauthorized access to user credentials and other sensitive information.
2. Implement strong password policies: Encourage users to create strong passwords that include a mix of letters, numbers, and symbols. Additionally, consider implementing password requirements such as minimum length and complexity.
3. Use two-factor authentication: Two-factor authentication (2FA) adds an extra layer of security to user authentication by requiring users to provide two forms of identification, such as a password and a code sent via SMS or email.
4. Limit login attempts: To prevent brute-force attacks, limit the number of login attempts allowed per user. This can help prevent unauthorized access to user accounts.
5. Use a secure authentication framework: Consider using a secure authentication framework such as OAuth or OpenID Connect. These frameworks provide a standardized way to authenticate users and can help prevent common security vulnerabilities.
E. How Can I Protect Sensitive Data In Databases?
There are several ways to protect sensitive data in databases:
1. Encryption: Use encryption techniques to protect sensitive data in databases. This can be done by encrypting the data before storing it in the database and decrypting it when it is retrieved.
2. Access control: Implement access control mechanisms to restrict access to sensitive data in databases. This can be done by assigning different levels of access to different users based on their roles and responsibilities.
3. Regular backups: Regularly back up the database to ensure that the data can be restored in case of a security breach or data loss.
4. Secure communication: Use secure communication protocols, such as SSL or TLS, to protect data in transit between the database and the application.
5. Database security tools: Use database security tools, such as firewalls, intrusion detection systems, and antivirus software, to protect the database from external threats.
F. What Are The Best Practices For Secure Front-End Development?
Here are some best practices for secure frontend development:
1. Input validation: Validate all user input to prevent cross-site scripting (XSS) attacks and other vulnerabilities.
2. Use secure authentication: Implement secure authentication mechanisms, such as multi-factor authentication and password hashing, to protect user accounts.
3. Secure communication: Use HTTPS to encrypt communication between the front end and back end to prevent data interception and tampering.
4. Implement access controls: Limit access to sensitive data and functionality to authorized users only.
5. Keep software up-to-date: Regularly update frontend libraries and frameworks to ensure that security patches are applied promptly.
6. Use security testing tools: Use automated security testing tools to identify vulnerabilities and weaknesses in the frontend code.
