Blocking and restricting unknown USB drives is crucial in safeguarding your digital world. These seemingly harmless devices can pose a significant threat, introducing malware and compromising your data. You can enhance your data security using methods like Group Policies, third-party software, password protection, and encryption. The benefits are clear: simplified data management, increased productivity, and the priceless peace of mind that comes from knowing your digital fortress is secure. In a world filled with cybersecurity risks, taking these steps can make your life considerably easier and your digital presence much safer.
Understanding the USB Threat
USB drives have become ubiquitous in our daily lives. They are incredibly convenient for transferring files but can also be a vector for cyberattacks. Here’s a closer look at the USB threat landscape:
1. Malware Distribution
Unknown USB drives can carry malware that can infect your computer as soon as you plug them in. Malicious software can spread like wildfire, causing extensive damage to your system and data.
2. Data Theft and Leakage
Connecting an unknown USB drive to your computer risks unauthorized access to sensitive data. This could lead to data theft and leakage, potentially compromising your personal or business information.
Benefits of Blocking and Restricting Unknown USB Drives

Blocking and restricting unknown USB drives can provide several benefits, particularly in environments where security and data integrity are paramount. Here’s how doing so can make your life easier and more secure:
Prevent Malware and Viruses

One of the most common reasons to block and restrict unknown USB drives is the prevention of malware and viruses. USB drives have been a common vector for spreading malicious software. Implementing these security measures significantly reduces the risk of introducing harmful software into your computer or network. This is particularly crucial in an era where cyber threats are becoming increasingly sophisticated.
Data Loss Prevention (DLP)
Data loss prevention is paramount in environments where sensitive data is handled, such as businesses and organizations. By controlling which USB devices can connect to your systems, you minimize the risk of data theft or leaks, whether intentional or unintentional. This proactive approach to data security is fundamental to safeguarding proprietary information and maintaining data integrity.
Standardized IT Environment
Restricting unknown USB drives also contributes to a standardized IT environment. Organizations can streamline IT management, troubleshooting, and system maintenance by allowing only vetted and approved hardware. This consistency in hardware reduces compatibility issues and simplifies the IT department’s workload, resulting in more efficient operations.
Avoid Unwanted Software Installations
Some USB drives come with auto-run software or applications that can be automatically installed when the drive is connected to a computer. By restricting unknown USB drives, you can prevent these unwanted software installations. This safeguards your system’s integrity and prevents bloatware or unnecessary applications from cluttering your computer.
Protection Against Physical Damage
Beyond the digital threats, blocking and restricting unknown USB drives can protect against physical damage. Poorly made or malfunctioning USB devices have the potential to cause harm to computer ports or internal electronics. By allowing only known and trusted devices, you reduce the risk of damage, ensuring the longevity of your hardware.
Reduced IT Support Tickets
Implementing these security measures can lead to a reduction in IT support tickets. Fewer external USB drives mean fewer issues related to malware infections, data transfer problems, or conflicts with software. This translates to less disruption for users and improved productivity across the organization.
Easier Auditing
Tracking and auditing data transfers become more manageable when only specific USB drives are permitted. This feature is particularly vital for businesses that must maintain detailed logs of data movements for compliance or security reasons. With a controlled USB drive environment, auditing processes are streamlined, ensuring data is handled securely and by regulations.
Methods for Blocking and Restricting USB Drives:
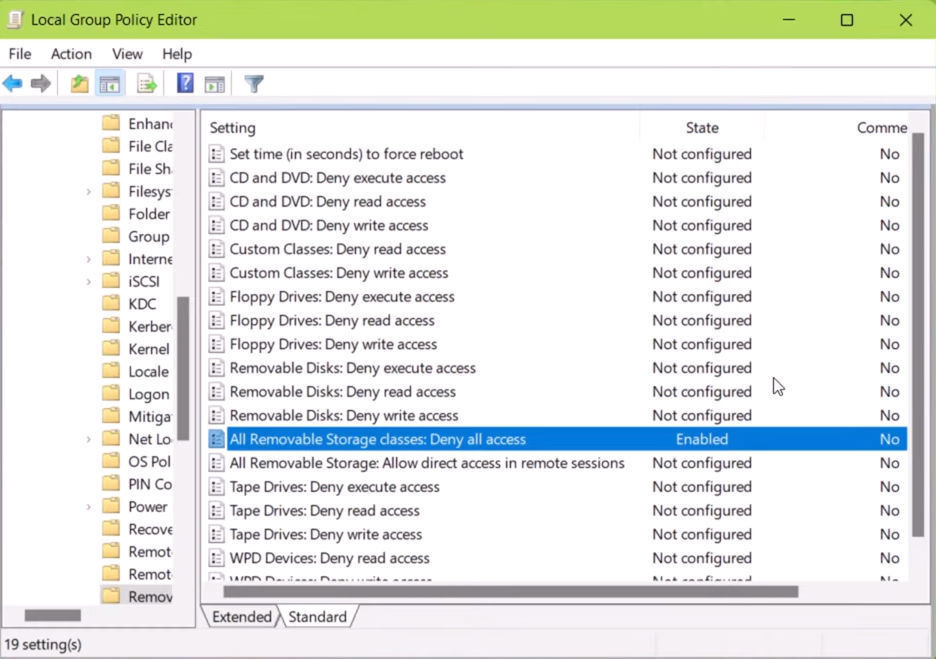
1. Group Policy Settings
Group Policy settings can be used on Windows-based systems to disable USB drive access for specific user groups. This method provides centralized control over USB drive permissions.
2. Third-Party Software Solutions
Numerous third-party software solutions are available for both Windows and macOS. These tools offer a range of features, including USB drive monitoring, blocking, and encryption.
3. Hardware Locks
For an added layer of security, physical hardware locks can be used to block USB ports on computers physically. This ensures that no USB drives can be connected without authorization.
Implementing USB Drive Policies
1. Assess Your Needs
Start by assessing the specific needs of your organization or personal computer use. Determine which level of USB drive access restriction is appropriate.
2. Choose the Right Method
Select the method that best suits your needs and resources. A software solution may suffice if you’re a small business, while larger organizations may prefer Group Policy settings.
3. Educate Users
Ensure that your employees or family members are educated about the USB drive policies in place. Teach them about the risks associated with unknown USB drives and why these measures are necessary.
4. Regularly Update and Monitor
Security threats evolve, so it’s crucial to update and monitor your USB drive policies regularly. Keep your software up to date, and review your policies periodically.
Frequently Asked Questions (FAQs)
Can all USB drives be blocked or restricted?
Yes, most USB drives can be blocked or restricted using the methods mentioned in this article. However, choosing the right method for your specific needs is essential.
Can USB drive policies be bypassed?
While USB drive policies provide strong security, determined attackers may still find ways to bypass them. Regular updates and monitoring are essential to stay protected.
Is there a risk of false positives with USB drive blocking?
There is a slight risk of false positives, where legitimate USB drives may be blocked. However, this can usually be addressed by configuring policies carefully.
Are there free software solutions for USB drive restriction?
Yes, free software solutions are available for USB drive restriction, although they may have limitations compared to paid options.
Are all USB drives potentially dangerous?
No, not all USB drives are dangerous. However, if infected or manipulated, any USB drive can threaten your data security. It’s essential to exercise caution with unknown drives.
Can I still use my trusted USB drives with these security measures?
Yes, you can use your trusted USB drives with these security measures. Blocking and restricting are typically designed to target unknown or unauthorized devices, allowing you to continue using your approved devices without issues.
Are there any free software options for USB drive security?
Yes, free software options are available for USB drive security, such as USB Disk Security and Bitdefender. These tools offer basic protection and can be a good starting point for securing your devices.
Conclusion:
Blocking and restricting unknown USB drives is crucial in enhancing data security and simplifying your life. By understanding the USB threat landscape and implementing the right policies and methods, you can significantly reduce the risks associated with these seemingly harmless devices. Stay vigilant, keep your systems updated, and educate your users to enjoy the benefits of a safer digital environment.
