The encryption cipher that rearranges characters or bits of data is called a transposition cipher.
Understanding Encryption Ciphers
In the world of data security, encryption plays a crucial role. It is the process of converting plain text into a secret code, making it unreadable to unauthorized users. One type of encryption cipher that is employed to accomplish this is known as a transposition cipher.
A transposition cipher is a method of encryption that rearranges the letters of a message to create a secret code. Instead of substituting letters with other characters, like in a substitution cipher, a transposition cipher focuses on changing the order of the letters. This makes it more difficult for unauthorized individuals to decipher the message without the proper key.
Transposition ciphers have a long history and have been used for centuries to protect sensitive information. They were particularly popular during times of war, where secure communication was essential. Military strategists and leaders would use transposition ciphers to send coded messages that only their intended recipients could understand.
The Role of Encryption in Data Security
Data security is paramount in today’s digital age, where sensitive information is constantly at risk of falling into the wrong hands. Encryption serves as a powerful tool to protect data confidentiality. Organizations and individuals can safeguard valuable information and maintain privacy using encryption ciphers, such as transposition ciphers.
Encryption guarantees that even if data is captured, it stays indecipherable and of no value to unauthorized parties. This is particularly vital when sending confidential data online, a space prone to hacker interceptions. Personal details, monetary data, and other private information would be exposed to potential theft and exploitation without encryption.
Moreover, encryption’s role isn’t just restricted to safeguarding data in transit. It’s equally significant in protecting stationary data, like that on servers or databases. When data at rest is encrypted, entities can be confident that even with physical access to the storage device, the data stays locked and unreachable without the correct decryption key.
Key Elements of an Encryption Cipher
An encryption cipher typically consists of several key elements. Firstly, there is the algorithm, which determines how the cipher operates. The algorithm defines the steps and calculations performed to encrypt and decrypt the data. Different encryption algorithms have varying levels of complexity and security.
Secondly, there is the key, which the algorithm uses to encrypt and decrypt data. The key is a secret parameter determining the specific transformation applied to the plaintext. Without the correct key, it is nearly impossible to decipher the encrypted message, adding an extra layer of security.
Lastly, there is the plaintext, the original message to be encrypted, and the ciphertext, the encrypted result. The plaintext can be any form of data, such as text, numbers, or files, that needs to be protected. Encryption transforms the plaintext into ciphertext, which appears as a random sequence of characters.
When the recipient wants to access the original message, they use the decryption process, which involves applying the same algorithm and the correct key to the ciphertext. This reverses the encryption process and converts the ciphertext back into the original plaintext, allowing the recipient to read the message.
Overall, encryption ciphers are essential tools in the field of data security. They provide a means to protect sensitive information from unauthorized access and ensure the confidentiality and integrity of data. As technology advances and new threats emerge, encryption techniques evolve to meet the ever-growing data protection challenges.
The Concept of Data Rearrangement in Encryption
As the name suggests, transposition ciphers involve rearranging characters or bits of data to create the ciphertext. Unlike substitution ciphers that replace characters with other characters, transposition ciphers focus on altering the order of the data without altering the actual characters themselves.
Let’s delve deeper into data rearrangement in encryption and explore how it enhances the security of encrypted messages.
How Data Rearrangement Enhances Security?
Data rearrangement is a technique that enhances the security of encryption. By rearranging the characters or bits in a message, the transposition cipher introduces complexity and adds an extra layer of confusion for potential attackers. This makes it more difficult for unauthorized users to decipher the message without the appropriate key.
Imagine a scenario where a message is encrypted using a substitution cipher alone. An attacker who intercepts the ciphertext may be able to analyze the frequency of characters and deduce the substitution pattern, ultimately cracking the encryption. However, with transposition ciphers, the rearranged order of characters or bits makes it significantly harder for attackers to discern any patterns or gain insights into the original message.
Furthermore, data rearrangement in encryption can also thwart known plaintext attacks. In a known plaintext attack, an attacker possesses both the original plaintext and its corresponding ciphertext. The attacker attempts to deduce the encryption algorithm or key by analyzing the relationship between the two. However, transposition ciphers with data rearrangement make this task more challenging, as the rearranged order of characters or bits obscures any direct correlation between the plaintext and ciphertext.
The Process of Data Rearrangement in Encryption
The process of data rearrangement in transposition ciphers involves several steps. Firstly, the plaintext is divided into blocks or rows, depending on the specific transposition cipher. This division helps in organizing the data for subsequent rearrangement.
Next, the order of the characters or bits in each block or row is rearranged according to the predetermined rules set by the encryption algorithm. These rules dictate how the rearrangement should occur, ensuring consistency and allowing for decryption using the appropriate key.
Lastly, the rearranged blocks or rows are combined to create the ciphertext. The resulting ciphertext appears as a scrambled version of the original plaintext, with the characters or bits rearranged in a manner that is difficult to decipher without knowledge of the specific transposition algorithm and key.
It is worth noting that the complexity of the data rearrangement process can vary depending on the encryption algorithm employed. Some algorithms may employ simple rearrangement techniques, while others may utilize more intricate and sophisticated methods to enhance the encrypted message’s security further.
In conclusion, data rearrangement plays a crucial role in encryption by introducing complexity and confusion, making it challenging for unauthorized users to decipher the message. By understanding the concept and process of data rearrangement in transposition ciphers, we gain insight into how encryption techniques can enhance the security of sensitive information.
Introduction to Transposition Ciphers
Transposition ciphers have a rich history and have evolved to become an integral part of encryption methods. These ciphers provide a different approach to encryption than substitution ciphers, which replace characters with other characters.
The History and Evolution of Transposition Ciphers
Transposition ciphers have been used throughout history to protect important messages and military secrets. One notable example is the ancient Roman scytale, a cylinder-shaped device that encrypts transposition. The scytale consisted of a long strip of parchment or leather around which a message was wrapped. The recipient would then unwind the strip from the same diameter cylinder, revealing the hidden message. This method ensured that only those with the correct cylinder could decipher the message, adding an extra layer of security.
Over the years, transposition ciphers have been refined and adapted to incorporate more complex algorithms, keeping pace with technological advancements. In the 19th century, the rail fence cipher emerged as a popular transposition cipher. This cipher involved writing the message in a zigzag pattern along a set number of “rails” and then reading off the letters in a specific order to reveal the encrypted message. The rail fence cipher was widely used during the American Civil War and World War I, demonstrating its effectiveness in military communications.
The Mechanism Behind Transposition Ciphers
The mechanism behind transposition ciphers lies in the rearrangement of characters or bits. Instead of substituting each character, as seen in substitution ciphers like the Caesar cipher, transposition ciphers focus on changing the order of the characters or bits in the message. This structural alteration adds an extra layer of complexity to the encryption process.
There are various techniques used in transposition ciphers to rearrange the characters or bits. One common method is columnar transposition, where the message is written in rows and then read in columns. The order of the columns is determined by a specific key, which guides the rearranging of the characters. Another technique is the route cipher, which involves writing the message in a grid and then reading it off in a specific pattern, such as spiraling inward or following a predetermined path.
Transposition ciphers can also be combined with other encryption methods, such as substitution ciphers, to create even more secure algorithms. By layering different encryption techniques, the cipher’s complexity increases, making it more challenging for unauthorized individuals to decipher the message.
Different Types of Transposition Ciphers
Transposition ciphers come in various forms, each with its unique characteristics. Two commonly known transposition ciphers are the Columnar Transposition Cipher and the Rail Fence Transposition Cipher.
Columnar Transposition Cipher
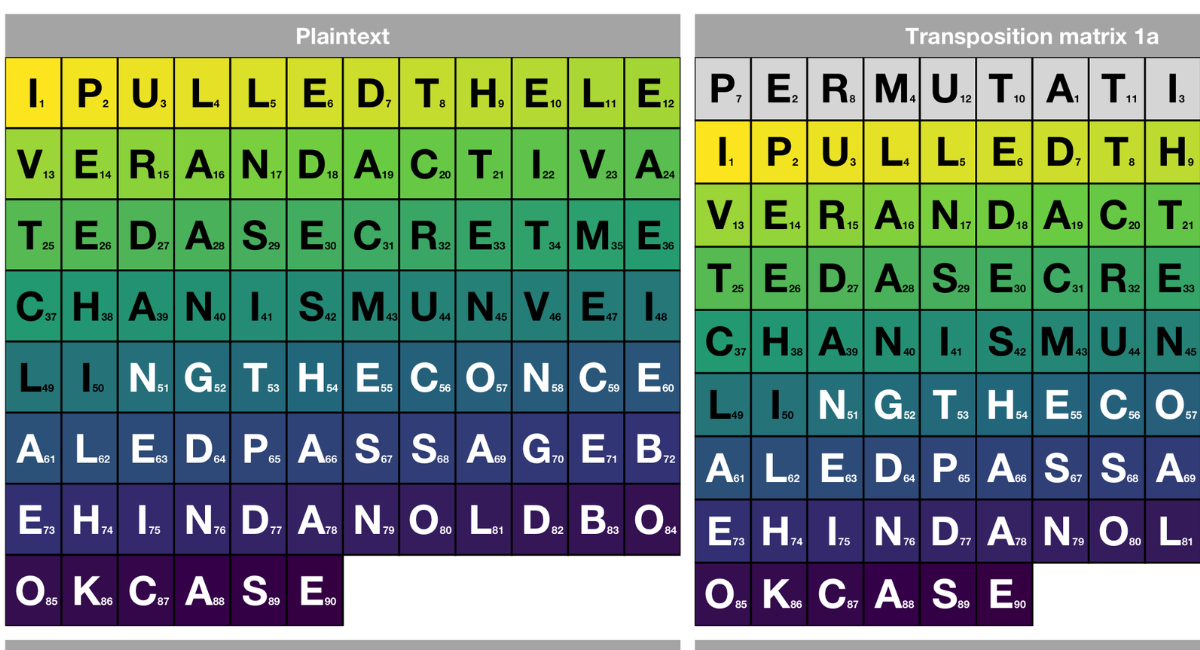
In a Columnar Transposition Cipher, the message is written in a grid with a specific number of columns. The ciphertext is then obtained by reading the columns in a specific order, determined by the key. This cipher type is known for its adaptability and can accommodate messages of different lengths.
Rail Fence Transposition Cipher
The Rail Fence Transposition Cipher operates by arranging the characters or bits of the message in a zigzag pattern on multiple lines. The ciphertext is then obtained by reading the characters in a specific order along the rails. This cipher is relatively simple and provides a basic level of security.
The Application of Transposition Ciphers in Modern Technology

Transposition ciphers continue to find applications in modern technology, particularly digital communication and cybersecurity.
Transposition Ciphers in Digital Communication
In the digital era, secure communication is crucial to prevent unauthorized access to sensitive information. Transposition ciphers can encrypt messages transmitted over various communication channels, such as email or instant messaging. By utilizing transposition ciphers, individuals and organizations can maintain the confidentiality of their digital conversations.
The Future of Transposition Ciphers in Cybersecurity
Cybersecurity is an ongoing battle, and as technology advances, so do the threats. Transposition ciphers, with their ability to rearrange data, hold promise for the future of encryption. As encryption algorithms become more sophisticated, transposition ciphers may provide an essential defense against emerging cyber threats.
FAQs
What is a transposition cipher?
A transposition cipher is an encryption method that rearranges the letters or bits of a message to create encrypted text.
How does a transposition cipher differ from a substitution cipher?
Unlike a substitution cipher that replaces letters with other characters, a transposition cipher changes the order of the letters or bits without altering the characters themselves.
Why are transposition ciphers important in data security?
Transposition ciphers add an extra layer of complexity, making it harder for unauthorized individuals to decipher the message without the appropriate key.
How has the use of transposition ciphers evolved?
From ancient tools like the Roman scytale to modern algorithms, transposition ciphers have been refined to address changing security needs.
What are some common types of transposition ciphers?
Some popular types include the Columnar Transposition Cipher and the Rail Fence Transposition Cipher.
Key Takeaways
- A transposition cipher rearranges characters or bits, altering their order to encrypt data.
- It offers a unique approach to encryption by focusing on structure alteration rather than character substitution.
- Historically, transposition ciphers have been essential for secure communication, especially during wartime.
- Transposition ciphers can be layered with other encryption methods for added security.
- Modern digital communication and cybersecurity often employ transposition ciphers for data protection.
Conclusion
Transposition ciphers offer a unique encryption approach, focusing on rearranging characters or bits. Their ability to add complexity by altering data structure rather than substituting characters makes them invaluable in ensuring data security, historically and in modern digital contexts.
