Understanding USB Block
Data theft and unauthorized access to confidential information have become increasingly perplexing problems, hindering creativity and productivity. USB Block is designed to counteract this trend by restricting access to your system, PC, or other devices, thwarting unauthorized USB connections
1. Password Protection
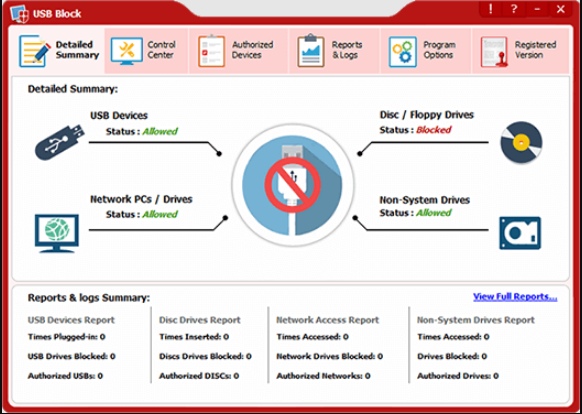
USB Block prompts you to enter a password whenever an unauthorized device tries to connect to your system. This password requirement ensures that your data remains secure and only accessible to those you trust. Trusted devices can be added to the ‘list of trusted devices,’ exempting them from the password prompt.
2. Blocking USB Devices
To begin using USB Block, follow these simple steps:
- Download and Install: Start by downloading and installing USB Block on your device.
- Launch the Software: Once installed, launch the software.
- Set Password: Set and confirm your password, then click ‘OK.’
- Control Center: Switch to the ‘Control Center’ tab, where you can manage the devices you do not trust.
- Default Port/USB Blocking: USB devices are blocked by default, but you can deactivate this feature from the ‘Control Center’ tab.
- Custom Blocking: To block specific types of devices, simply check the relevant boxes as directed.
Once blocked, all devices of the selected type will be denied access to your computer.
3. Trusted Device Exemption
USB Block ensures that the software will prompt for a password whenever an unauthorized device, such as a USB drive, is connected. However, trusted devices in the ‘authorized list’ won’t be subjected to this password request. Adding a device to the authorized list is as easy as checking the box that says ‘Remember (add to Authorized List)’ whenever a password prompt window appears.
Beyond USB Drives
USB Block goes beyond merely safeguarding against USB drives. It is also renowned as the best data leak prevention software, reducing the risk of data exposure to untrusted individuals. Here are some additional features of USB Block:
- Port and Device Blocking: USB Block can block not only USB drives but also ports and devices on your local PC.
- Restriction of Unauthorized Use: It prevents unauthorized use of USB drives, media, Blu-ray discs, and non-system drives on your computer.
Blocking Non-System Drives
USB Block allows you to extend its protective capabilities to non-system drives on your PC. Here’s how to do it:
- Launch USB Block: Start USB Block and enter your password.
- Control Center: Switch to the ‘Control Center’ tab, where you can manage drives and devices that you do not trust. By default, only USB drives are blocked, but you can deactivate this feature if needed.
- Block Non-System Drives: Check the ‘Block Non-system Drives’ box to prevent unauthorized access to non-system drives on your computer.
Hence, whenever an unauthorized device attempts to access your non-system drives, they will be prompted to enter the correct password. Drives on the ‘Authorize List’ won’t require a password when accessed. You can add devices to this trusted list by checking the ‘Remember (add to Authorize List)’ box whenever a password prompt window appears.
Conclusion
In a world where data security is paramount, USB Block is a powerful tool that ensures your valuable information remains protected. By effectively blocking unauthorized USB devices and providing password protection, it offers peace of mind for both personal and professional use. With USB Block, you can work without fear of data theft, allowing your creativity to flourish unencumbered.
FAQs
1. Is USB Block compatible with all operating systems?
USB Block is compatible with various Windows operating systems, including Windows 10, Windows 8, Windows 7, and more.
2. Can USB Block be used in corporate environments?
Yes, USB Block is an excellent choice for corporate settings where data security is a priority. It helps prevent data breaches and unauthorized data transfers.
3. What types of devices can USB Block block?
USB Block can block a wide range of devices, including USB drives, external hard drives, media devices, and Blu-ray discs, among others.
4. Is it easy to add trusted devices to USB Block’s ‘authorized list’?
Yes, adding trusted devices to the authorized list is straightforward. You can do it with a simple checkbox whenever a password prompt window appears.
5. Does USB Block offer any trial version for testing?
Yes, USB Block often provides a trial version that allows users to test its features before purchasing the full version. This is a great way to ensure it meets your security needs.
